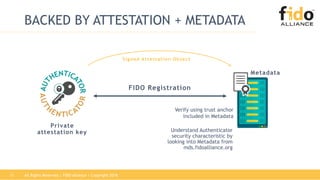
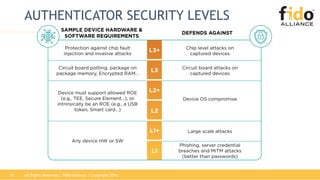
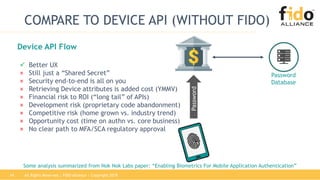
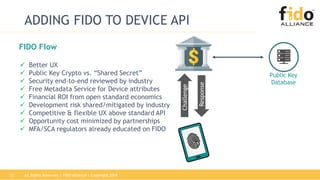
The document discusses the challenges and inefficiencies associated with traditional password-based authentication methods, highlighting the increasing costs of fraud and the security risks involved. It presents the FIDO (Fast Identity Online) framework as a solution that utilizes public key cryptography for secure authentication, thereby improving user experience and security. Additionally, it mentions the collaboration between FIDO Alliance and EMVCo to enhance payment authentication processes.