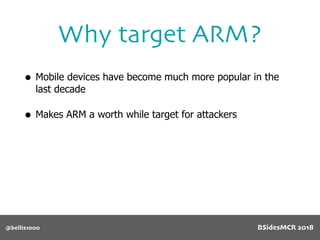
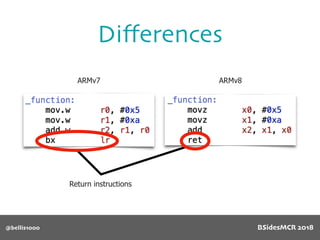
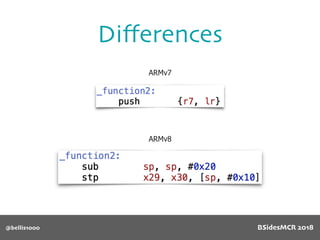
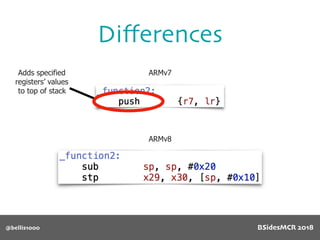
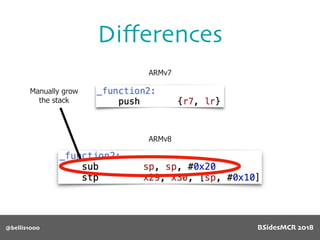
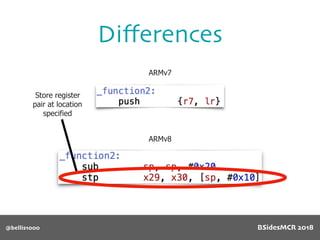
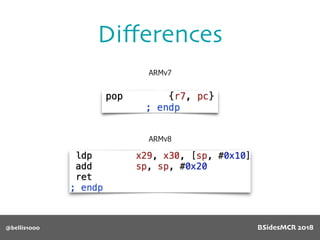
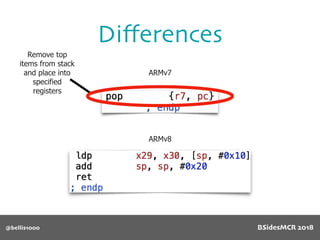
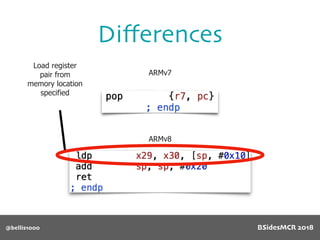
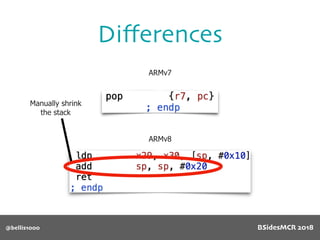
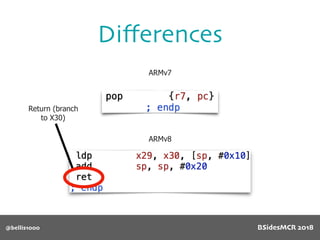
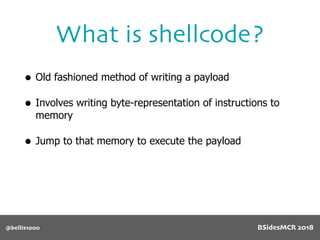
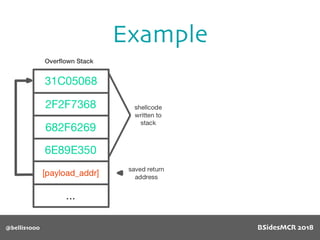
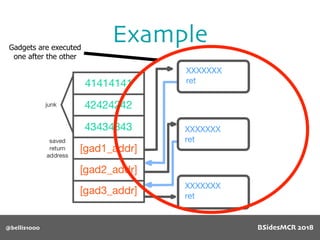
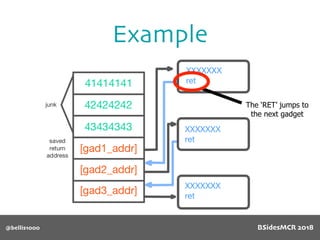
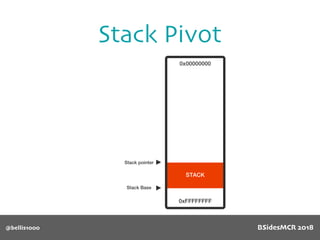
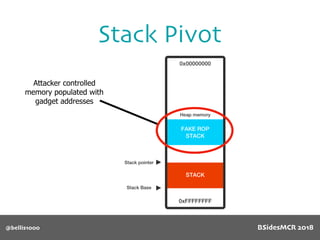
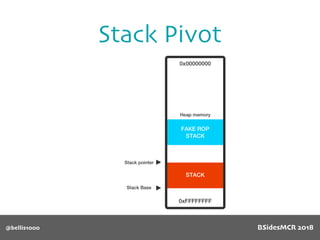
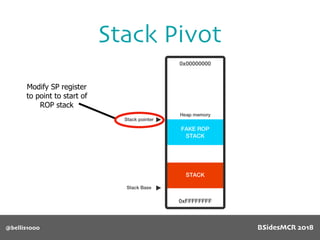
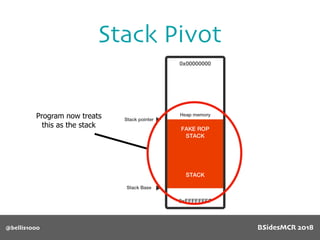
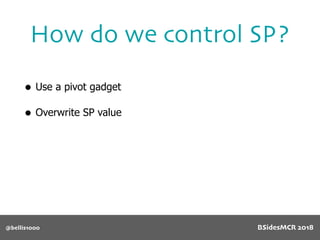
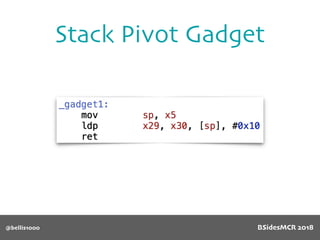
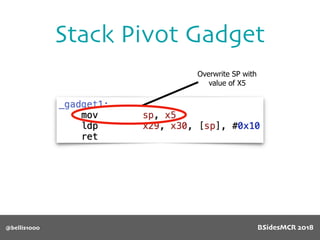
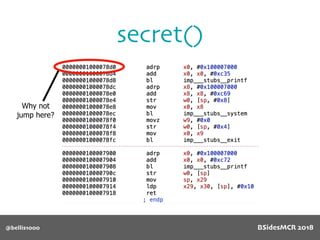
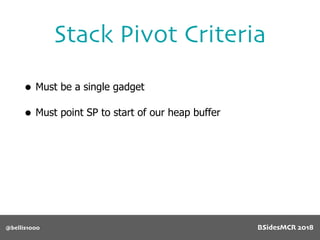
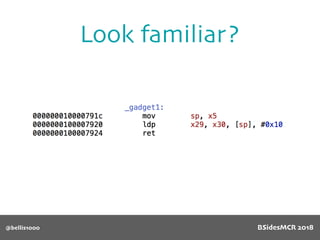
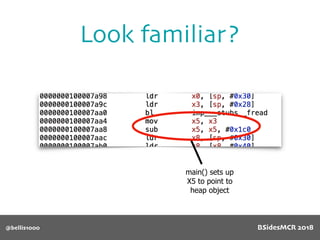
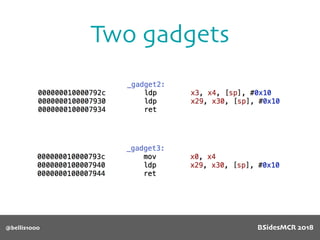
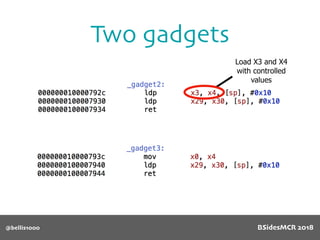
Billy Ellis presents an introduction to return-oriented programming (ROP) exploitation on ARM64 at BSidesMCR 2018, detailing the background and significance of targeting ARM architectures due to their prevalence in mobile devices. The talk covers the fundamentals of ARM architecture, differences between ARMv7 and ARMv8, and the mechanics of ROP, which involves chaining gadgets to perform code execution without traditional payloads. Ellis also outlines a practical example of an exploit leveraging a heap buffer overflow, demonstrating how to manipulate program control flow to execute a vulnerable function.




















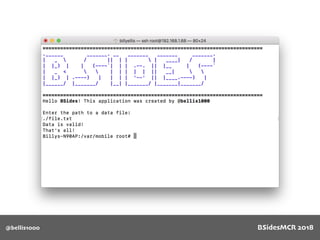

![@bellis1000
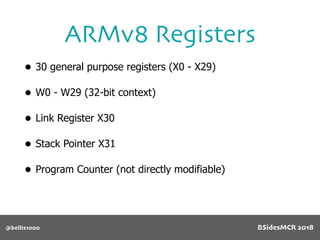
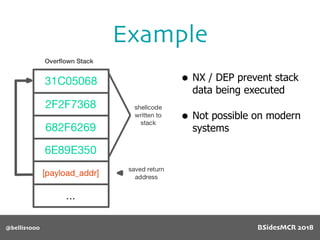
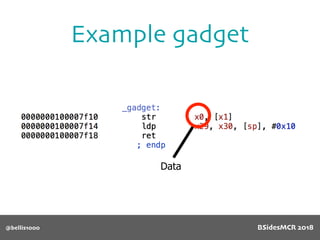
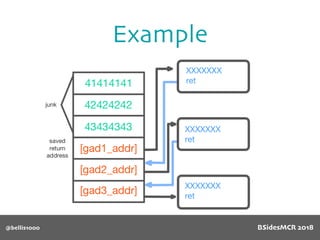
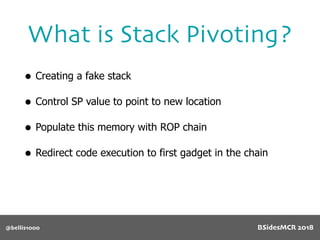
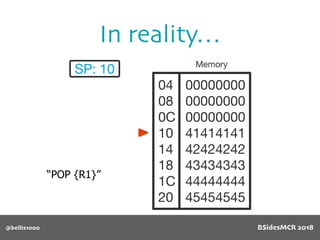
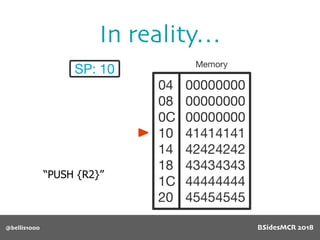
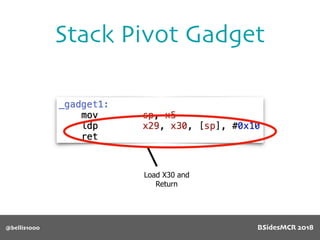
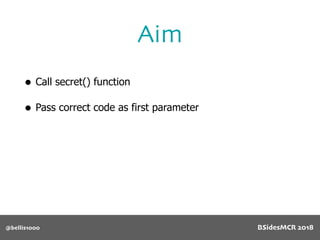
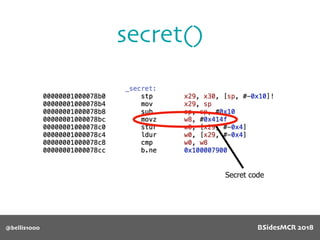
Vulnerability
512 byte copy into
object’s name[] char
array
BSidesMCR 2018](https://image.slidesharecdn.com/bsidestalkbillyellis-180816165818/85/Introduction-to-Return-Oriented-Exploitation-on-ARM64-Billy-Ellis-86-320.jpg)
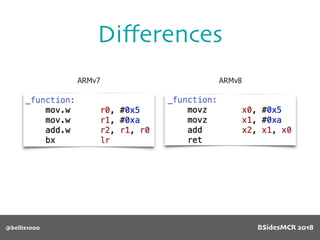
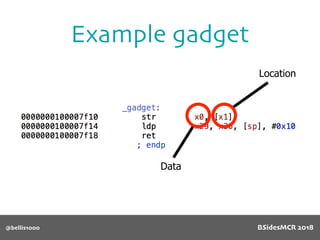
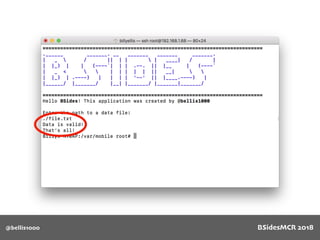
![@bellis1000
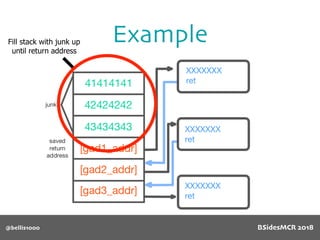
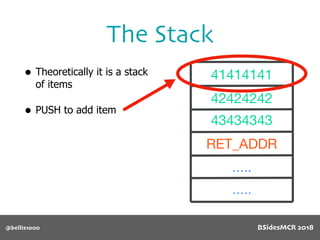
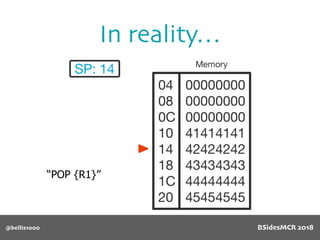
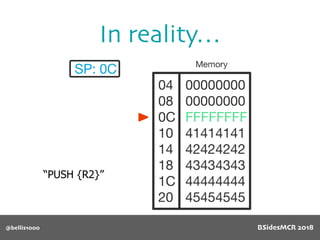
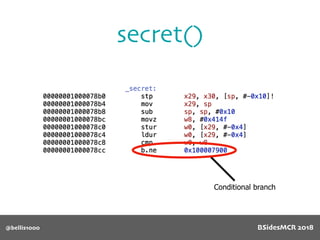
Vulnerability
name[] array is
only 64 bytes long
512 byte copy into
object’s name[] char
array
BSidesMCR 2018](https://image.slidesharecdn.com/bsidestalkbillyellis-180816165818/85/Introduction-to-Return-Oriented-Exploitation-on-ARM64-Billy-Ellis-87-320.jpg)
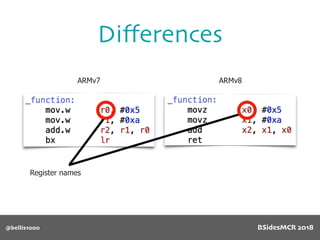
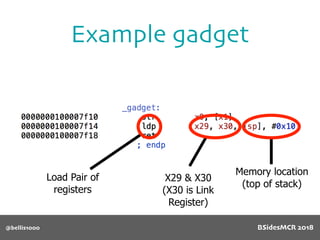
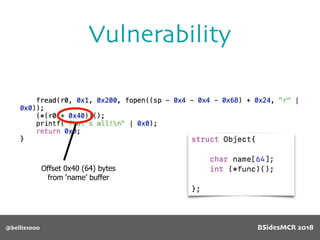
![@bellis1000
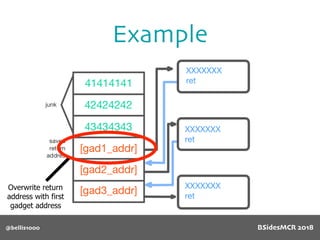
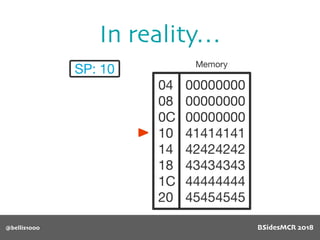
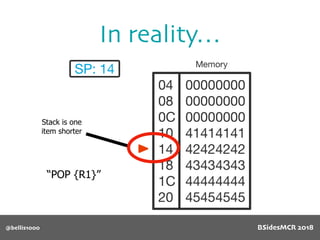
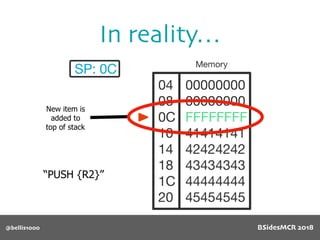
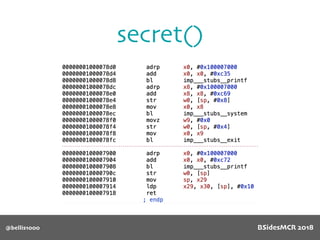
Vulnerability
Will overflow causing
function pointer to be
overwritten!
512 byte copy into
object’s name[] char
array
BSidesMCR 2018](https://image.slidesharecdn.com/bsidestalkbillyellis-180816165818/85/Introduction-to-Return-Oriented-Exploitation-on-ARM64-Billy-Ellis-88-320.jpg)

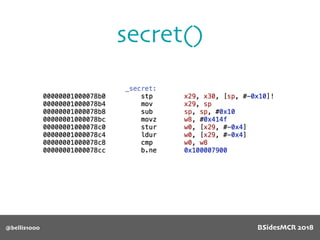






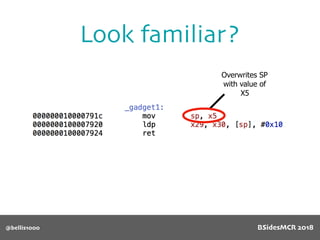

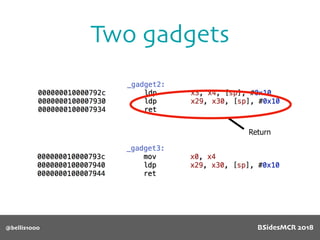



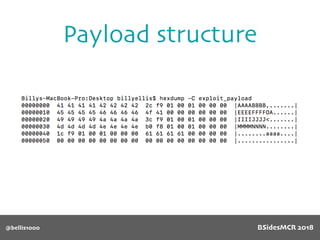
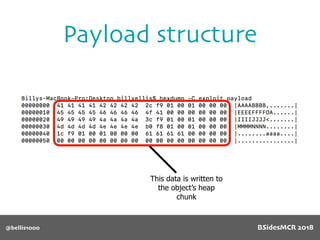
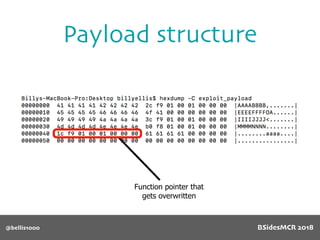
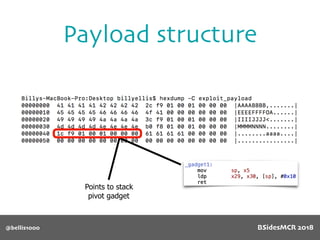
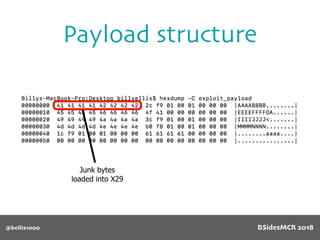
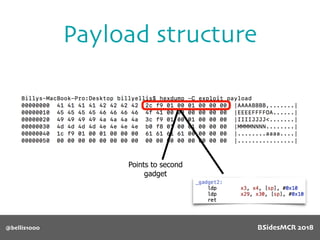
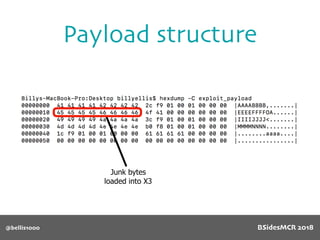
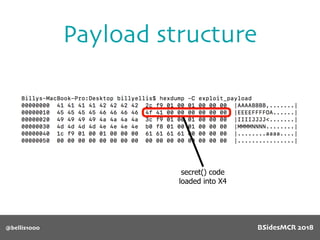
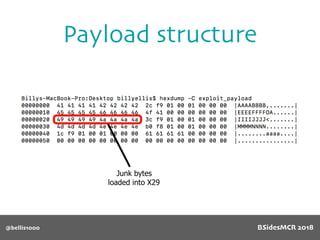
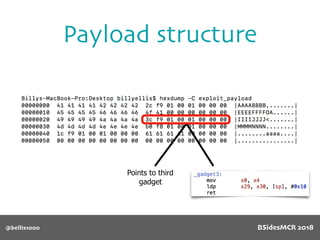
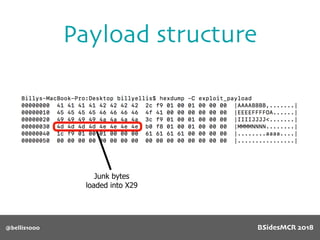
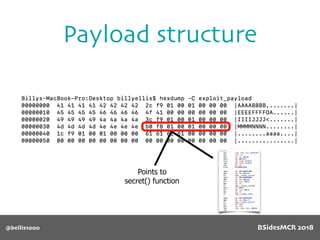
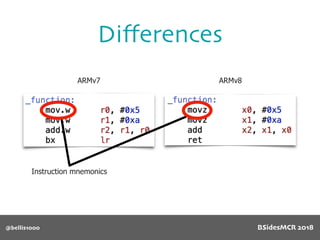
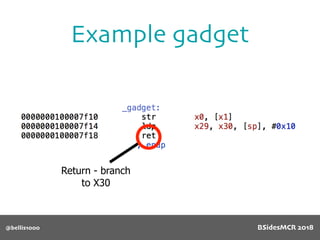
![@bellis1000
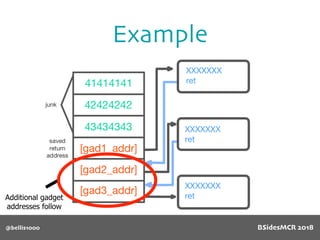
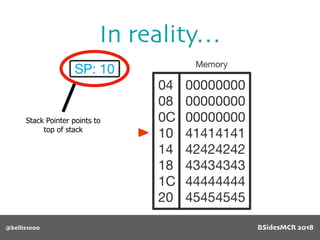
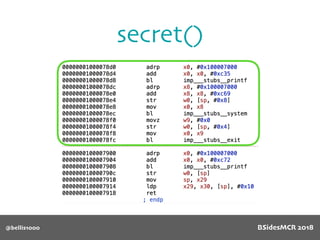
Payload structure
char name[64];
BSidesMCR 2018](https://image.slidesharecdn.com/bsidestalkbillyellis-180816165818/85/Introduction-to-Return-Oriented-Exploitation-on-ARM64-Billy-Ellis-118-320.jpg)