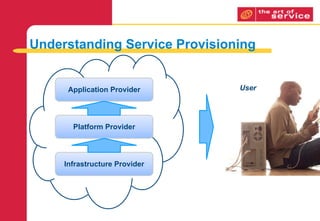
This document provides an overview of cloud computing, focusing on service provisioning and the various types of providers. It discusses the advantages and disadvantages of internal versus external provisioning and insourced versus outsourced solutions, highlighting the importance of managing risks and developing a comprehensive business case for cloud migration. Additionally, it addresses constraints organizations may face during the transition and outlines strategies for managing both the cultural and organizational changes involved.