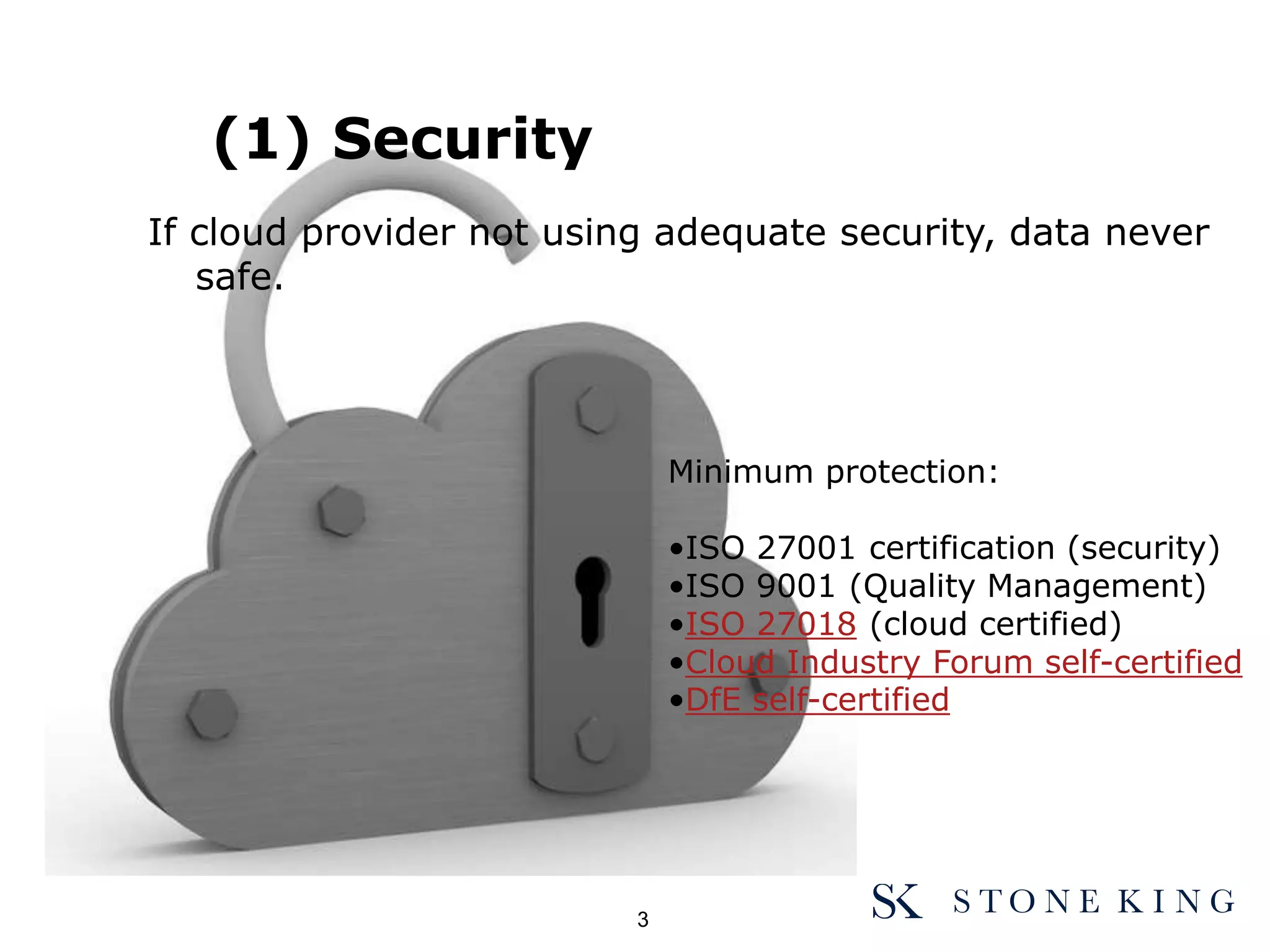
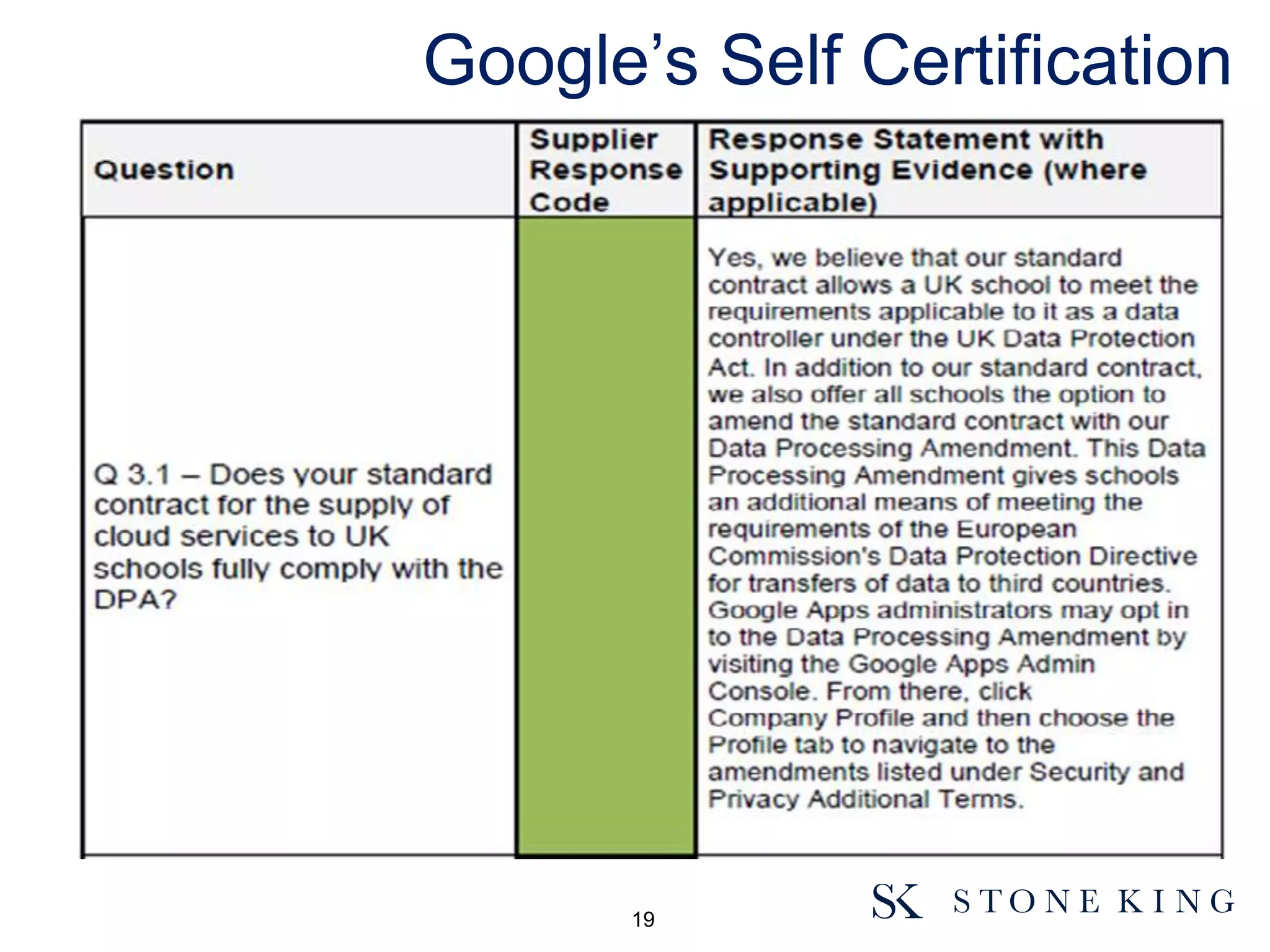
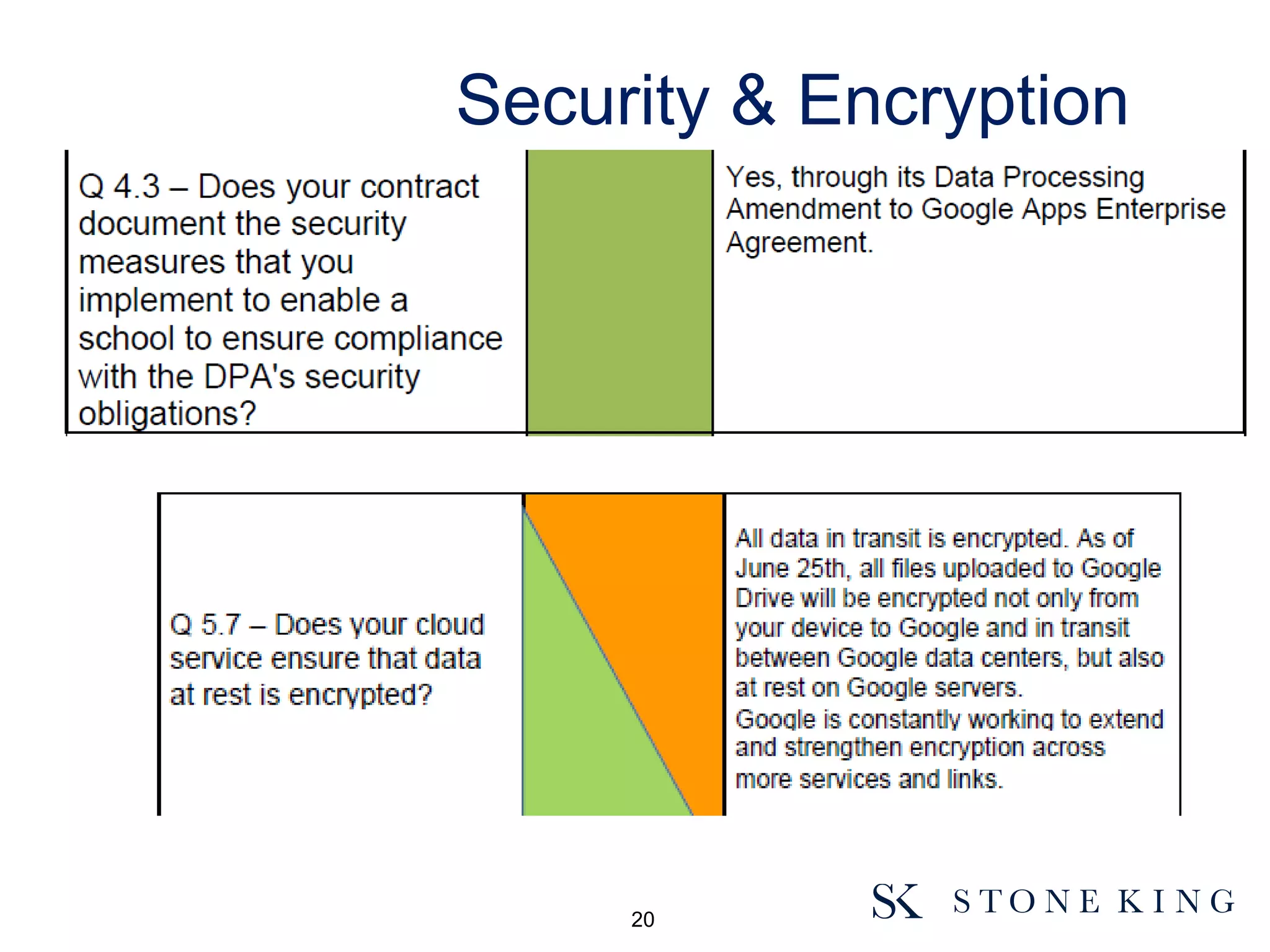
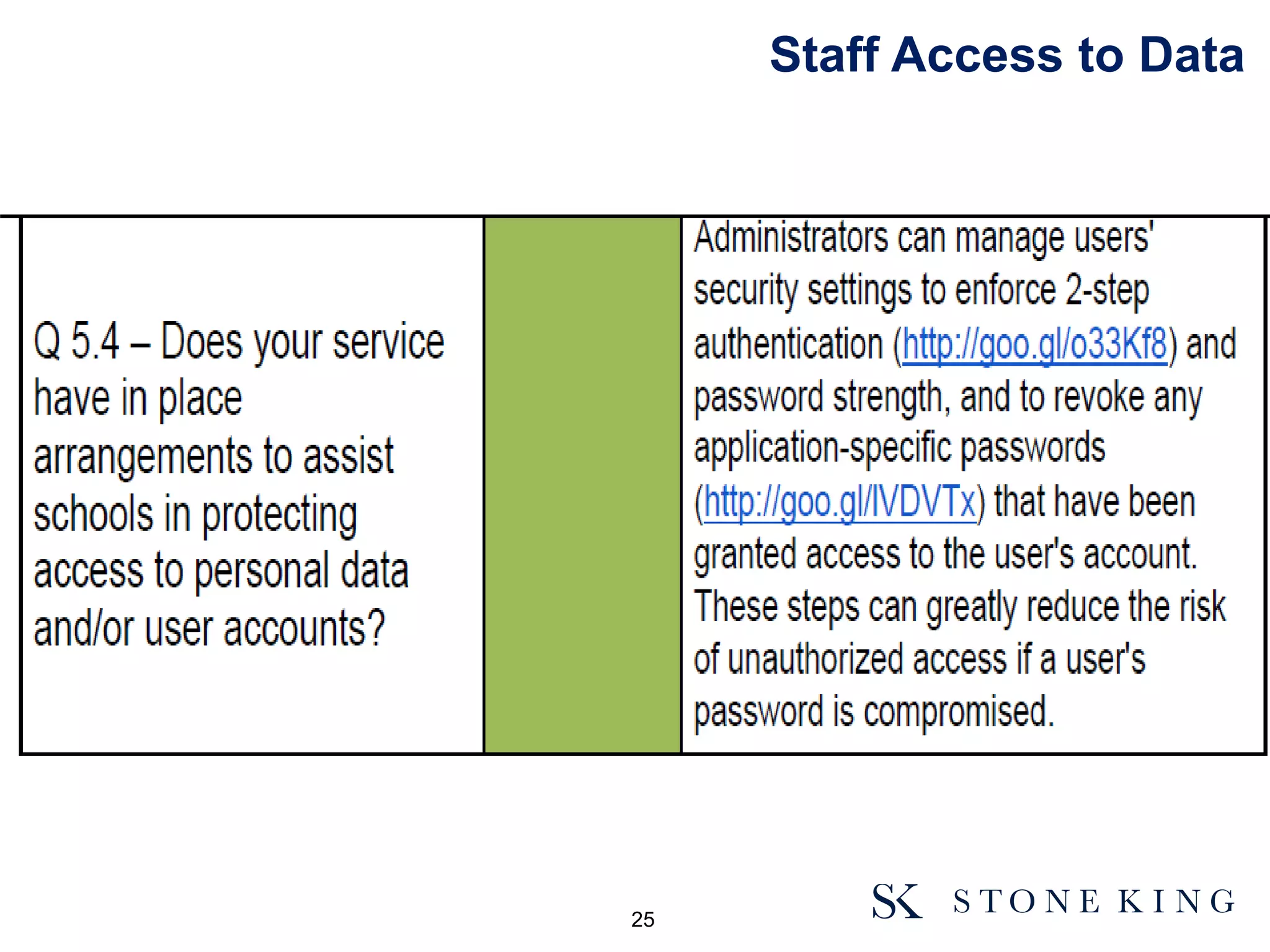
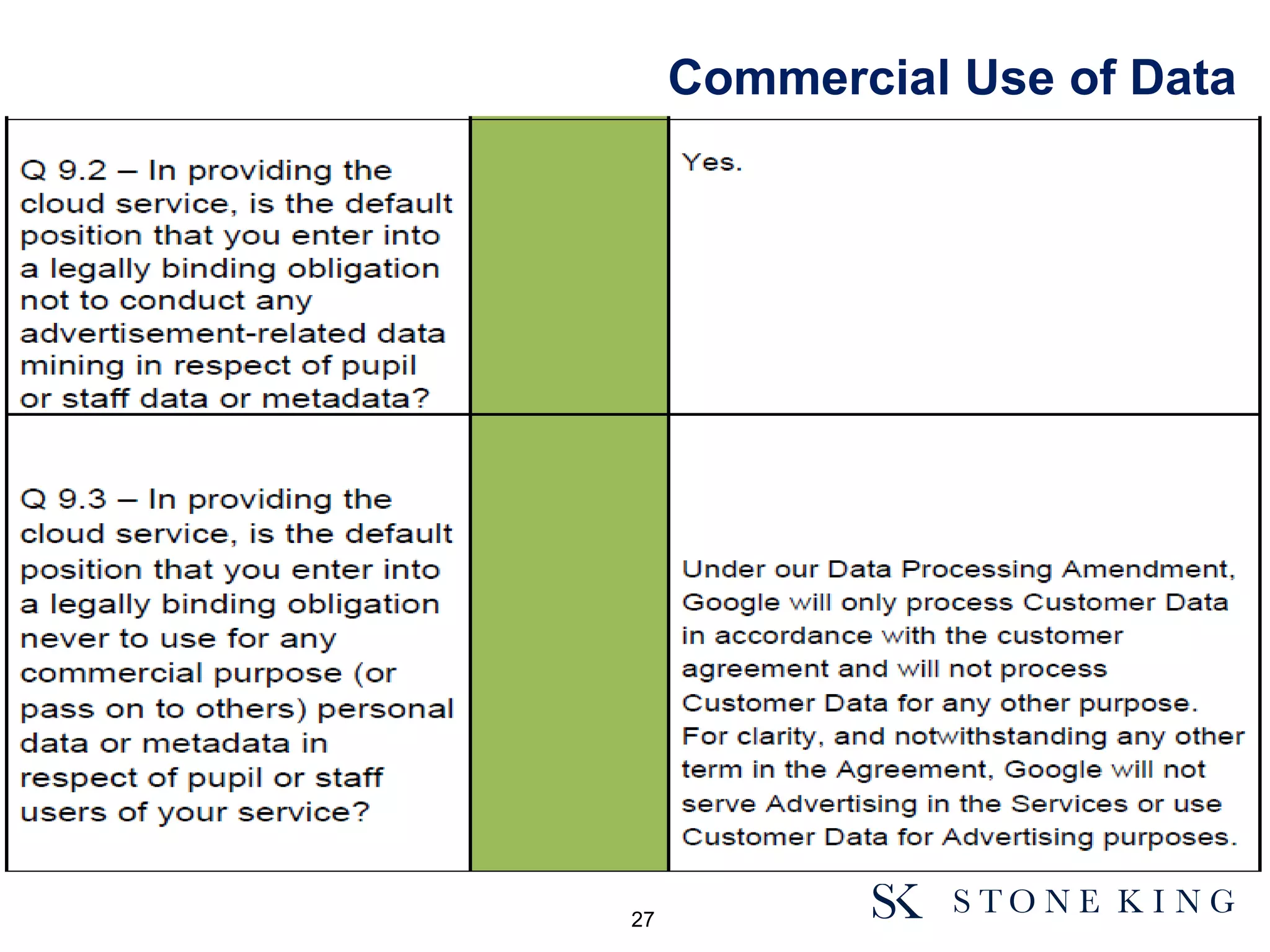
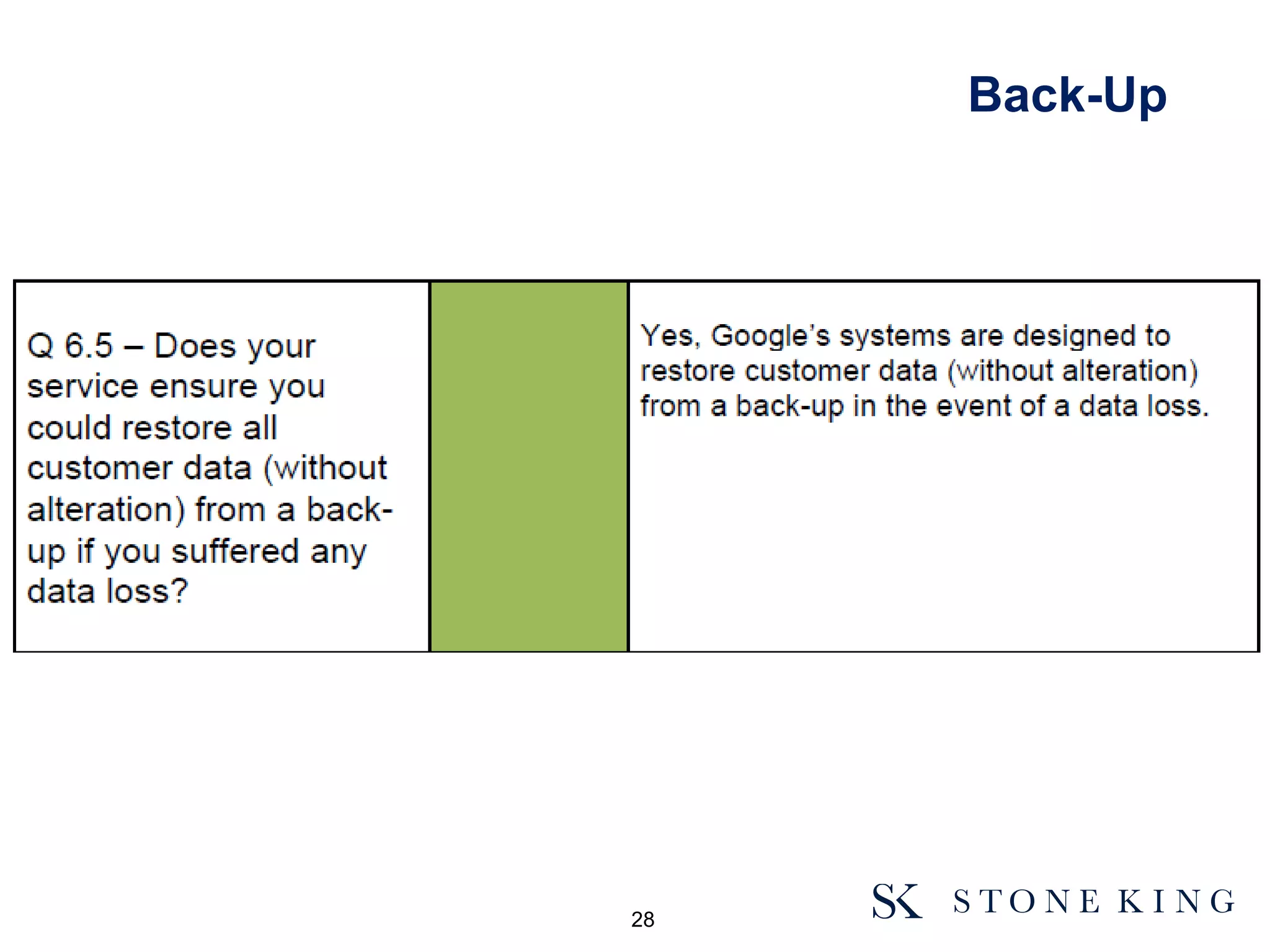
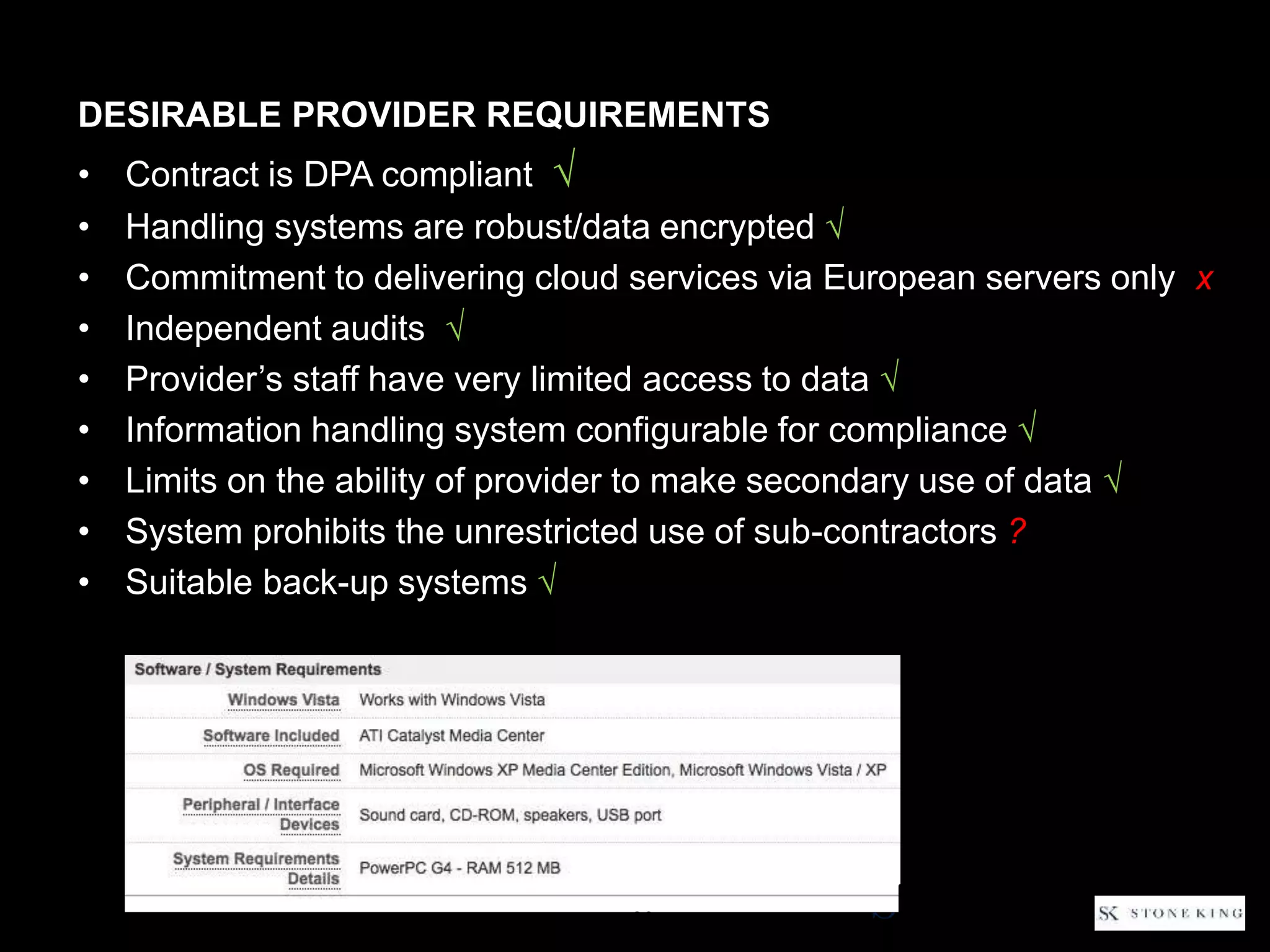
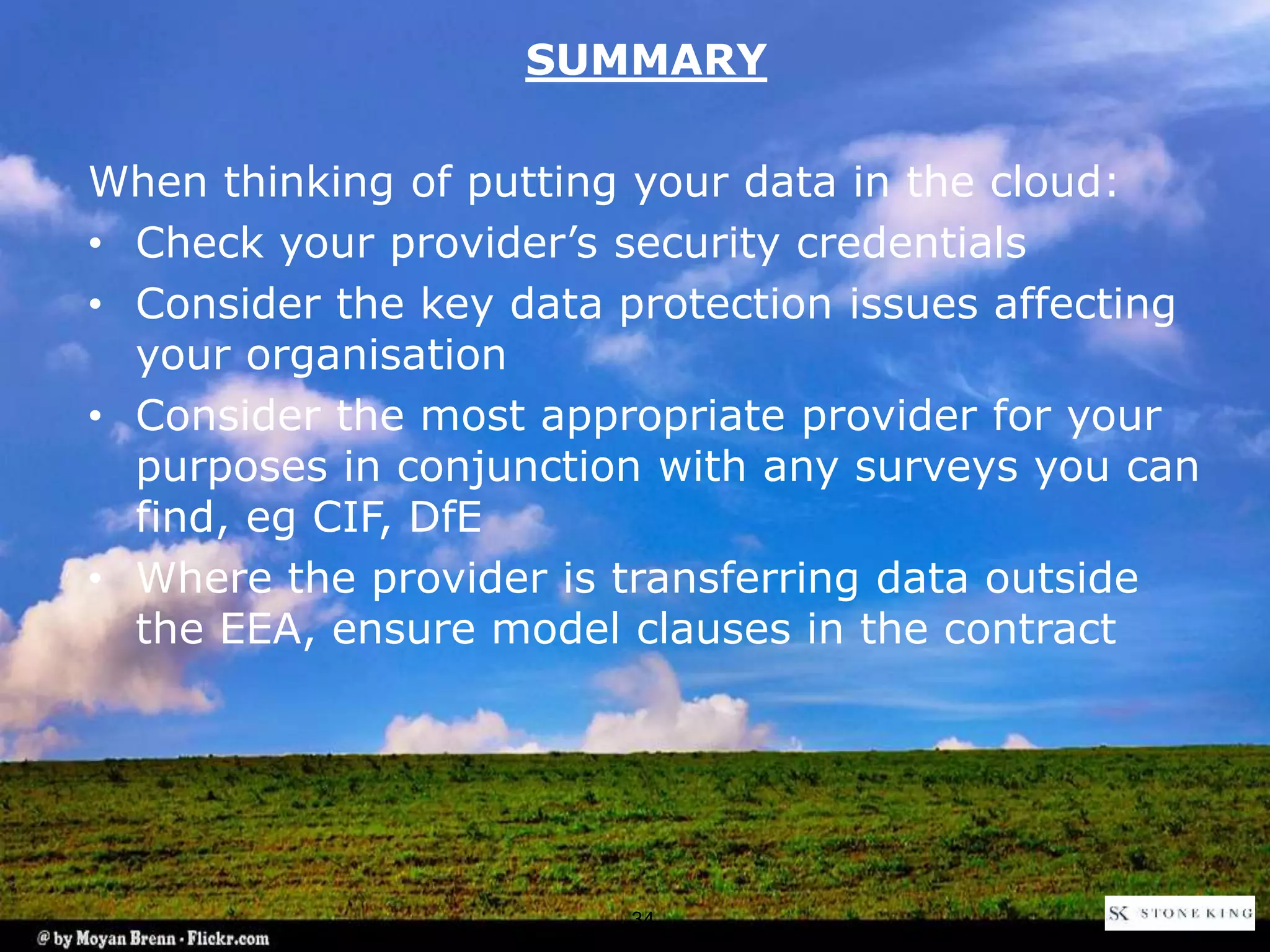
The document discusses essential aspects organizations need to consider regarding cloud computing and data protection, particularly highlighting compliance with data protection principles and EU regulations. It outlines key responsibilities for data controllers, security certifications for cloud providers, and the risks associated with cloud storage, including data breaches and compliance challenges. Additionally, it emphasizes the importance of conducting due diligence and maintaining an active management approach to ensure data protection compliance.




















![A.1.5 Third-Party Coverage Transparency
Statement about the extent to which the organization accepts indirect
responsibility for the organization's suppliers. [This covers e.g. the situation
of the organization's suppliers going out of business.] For example: for the
technical failure of vendors in the supply chain such as co-location where
services are taken off-line.
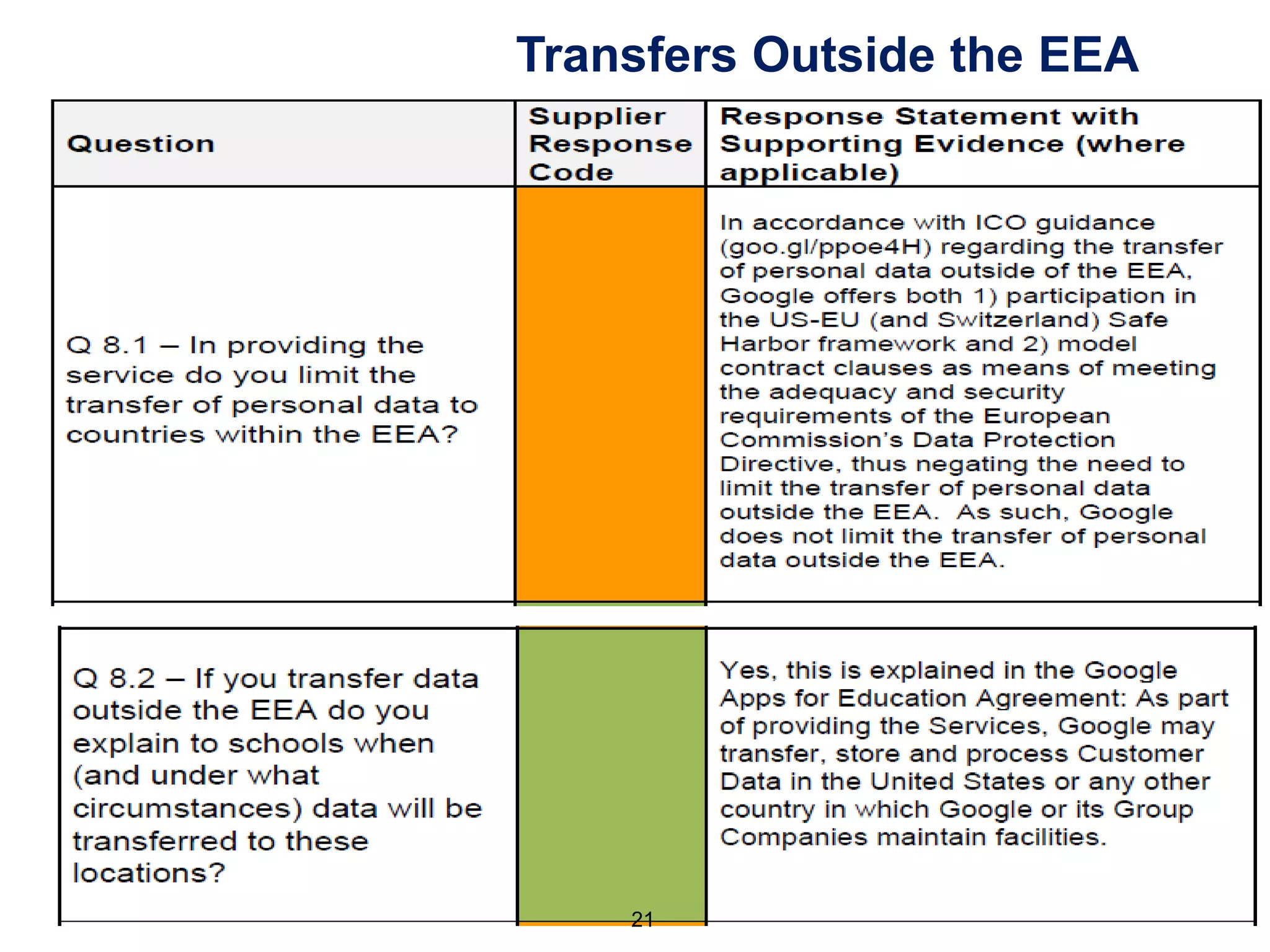
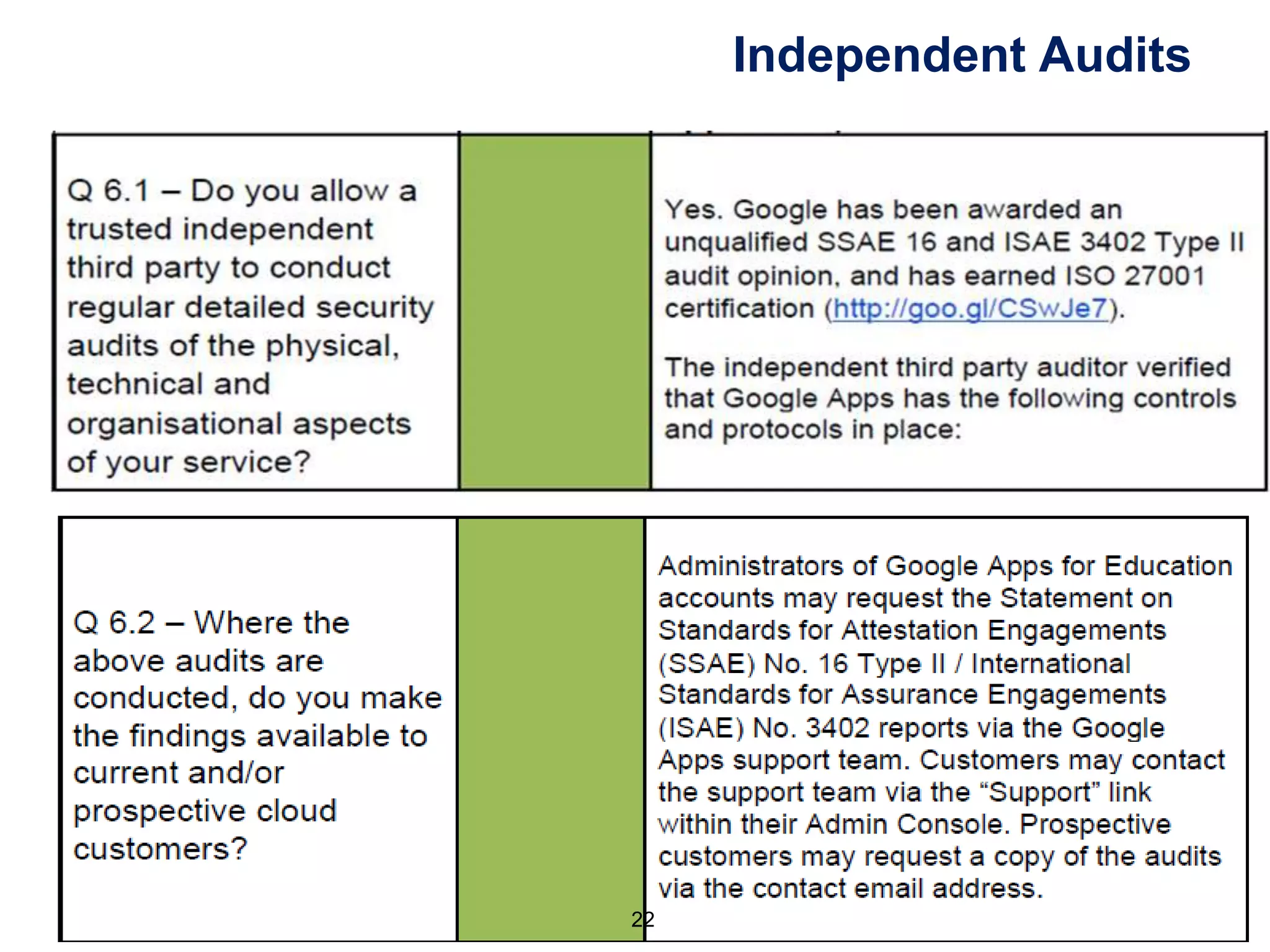
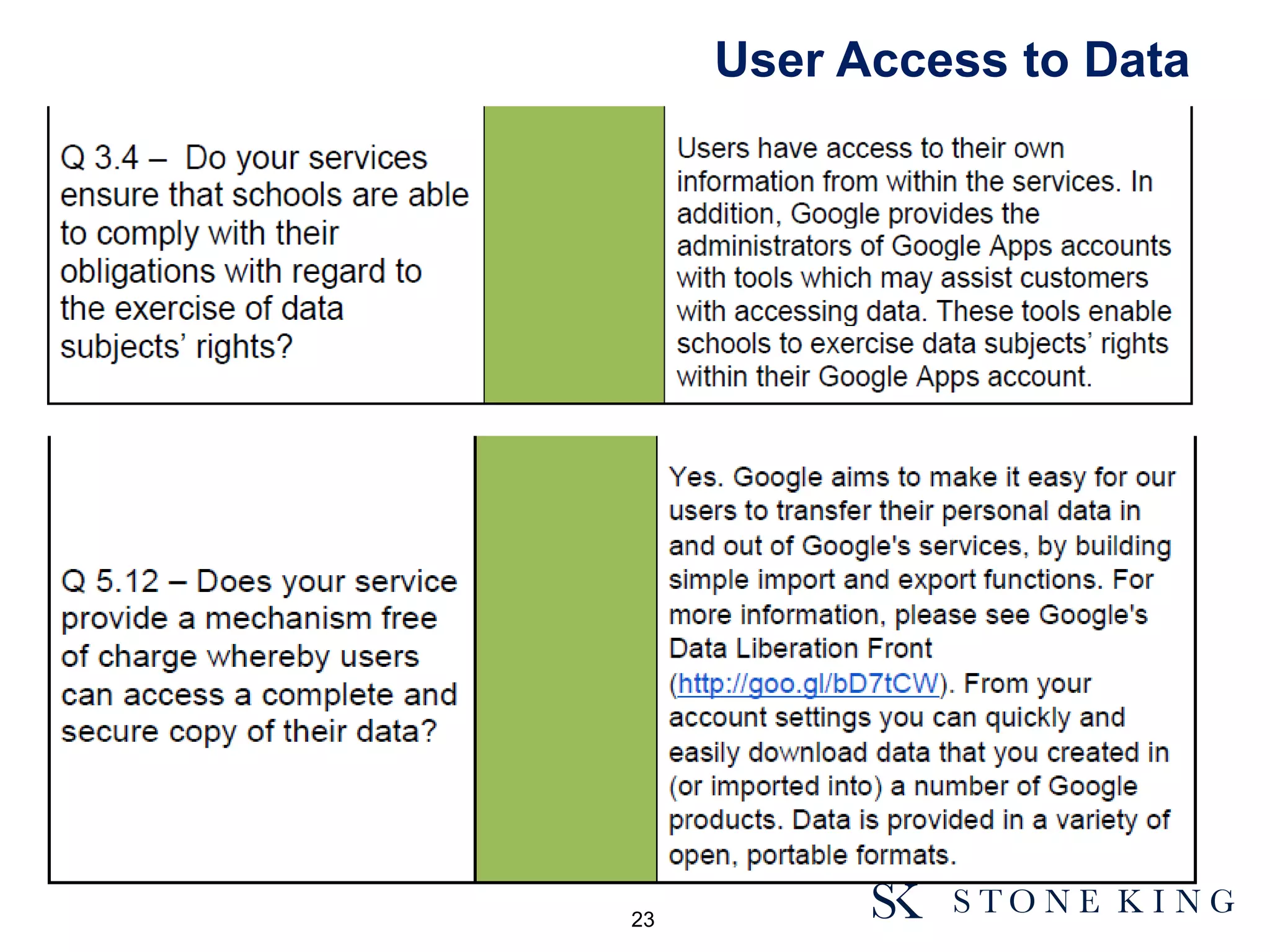
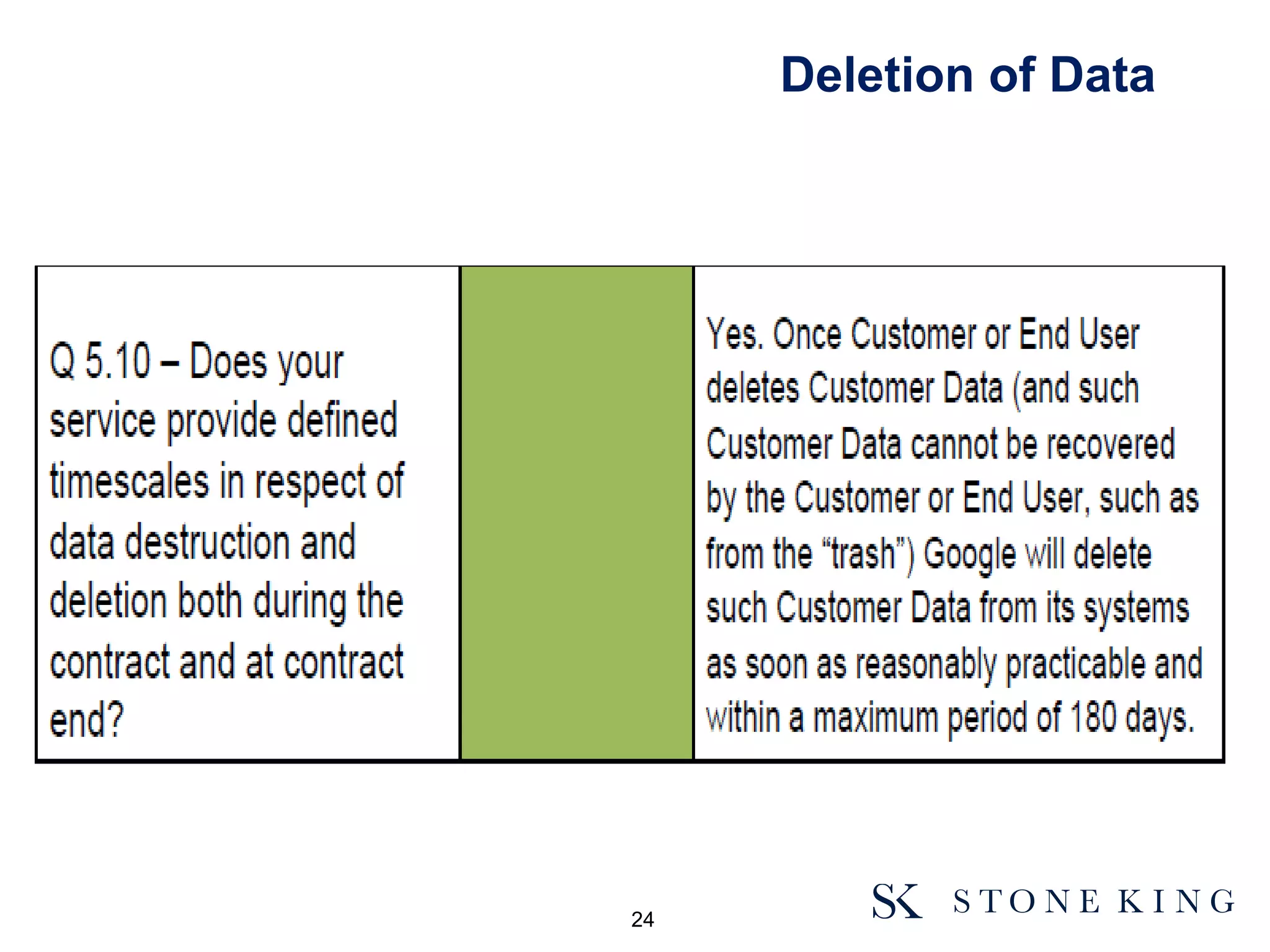
(1) customer can limit countries to which data is transferred to comply wth 8th
principle
(2) LawCloud and Rise accepts responsibility for the provision of its infrastructure
services, including any technical failures of third party vendors
(3) LawCloud and Rise's responsibility to direct Customers is subject to
contractual agreement and associated terms and conditions.
(4) In respect of contractual liability, such liability will be limited
(5) direct Customers are required to undertake their own areas of responsibility...
(6) the contractual relationship is between LawCloud and the direct customer.
LawCloud has a separate agreement with Rise and Microsoft who are under no
obligation or liability to direct customers. Any requests from a customer will
be reviewed on an individual basis and in association with LawCloud.
CLOUD INDUSTRY FORUM’S CERTIFICATION PROCESS
6](https://image.slidesharecdn.com/what-all-organisations-need-to-know-about-cloud-computing-part2-by-brian-miller-solicitor-150310084100-conversion-gate01/75/Data-Protection-and-the-Cloud-Part-2-by-Brian-Miller-Solicitor-and-Vicki-Bowles-Barrister-25-2048.jpg)












![Attributions
Slide 32 Some rights reserved by opensourceway
Slide 33 Some rights reserved by archer10 (Dennis)
Slide 34 Some rights reserved by storem
Slide 35 Some rights reserved by Moyan_Brenn
Slide 13 Some rights reserved by Intersection Consulting
Slide 14 All rights reserved by edbutowsky
Slide 15 Some rights reserved by kilokon.tw
Slide 16 Some rights reserved by Celso Flores
Slide 17 Some rights reserved by mediadeo
Slide 18 Some rights reserved by brionv
Slide 30 Some rights reserved by scott.tanis
Slide 31 Some rights reserved by CarbonNYC [in SF!]
37](https://image.slidesharecdn.com/what-all-organisations-need-to-know-about-cloud-computing-part2-by-brian-miller-solicitor-150310084100-conversion-gate01/75/Data-Protection-and-the-Cloud-Part-2-by-Brian-Miller-Solicitor-and-Vicki-Bowles-Barrister-56-2048.jpg)
