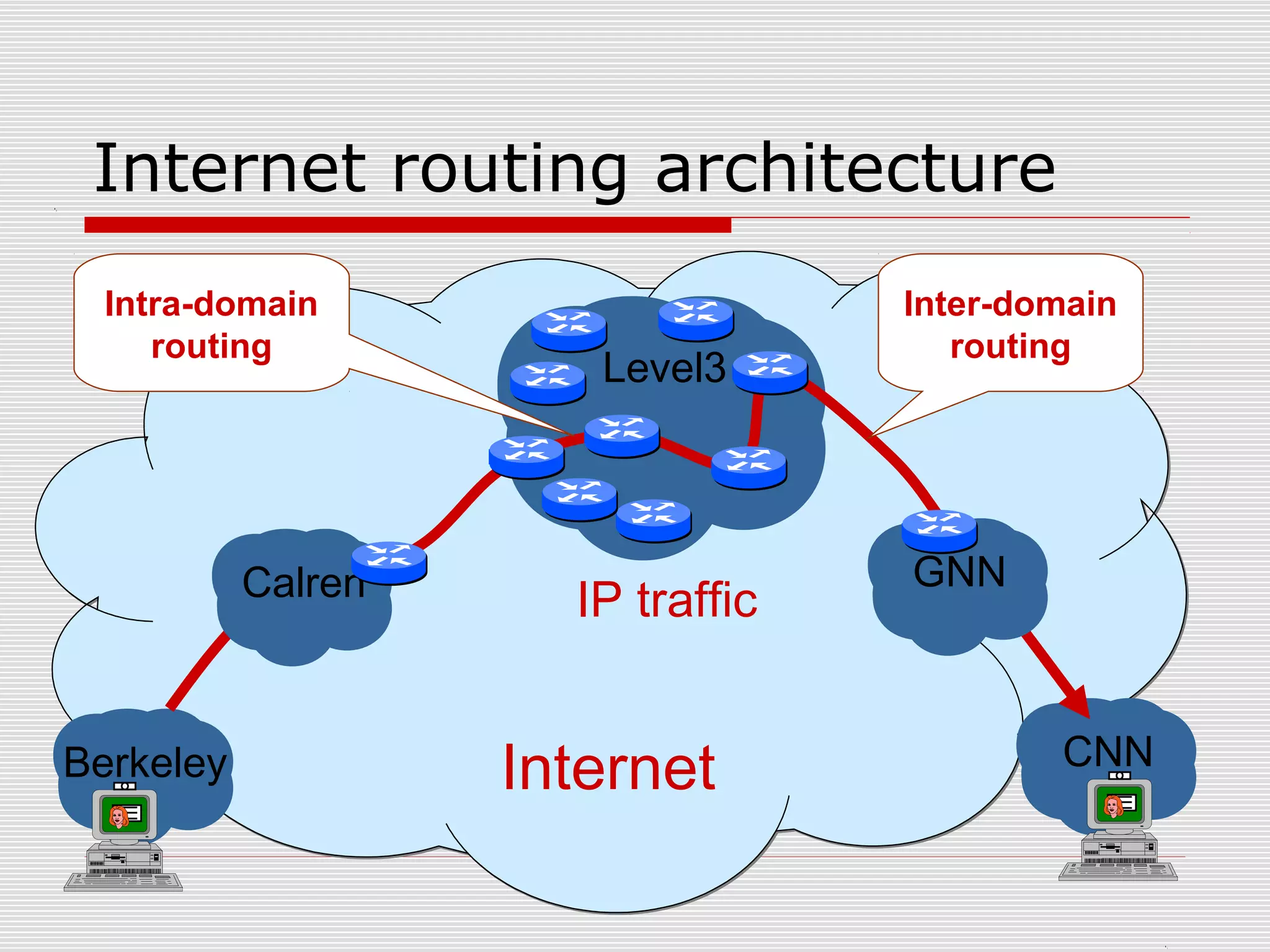
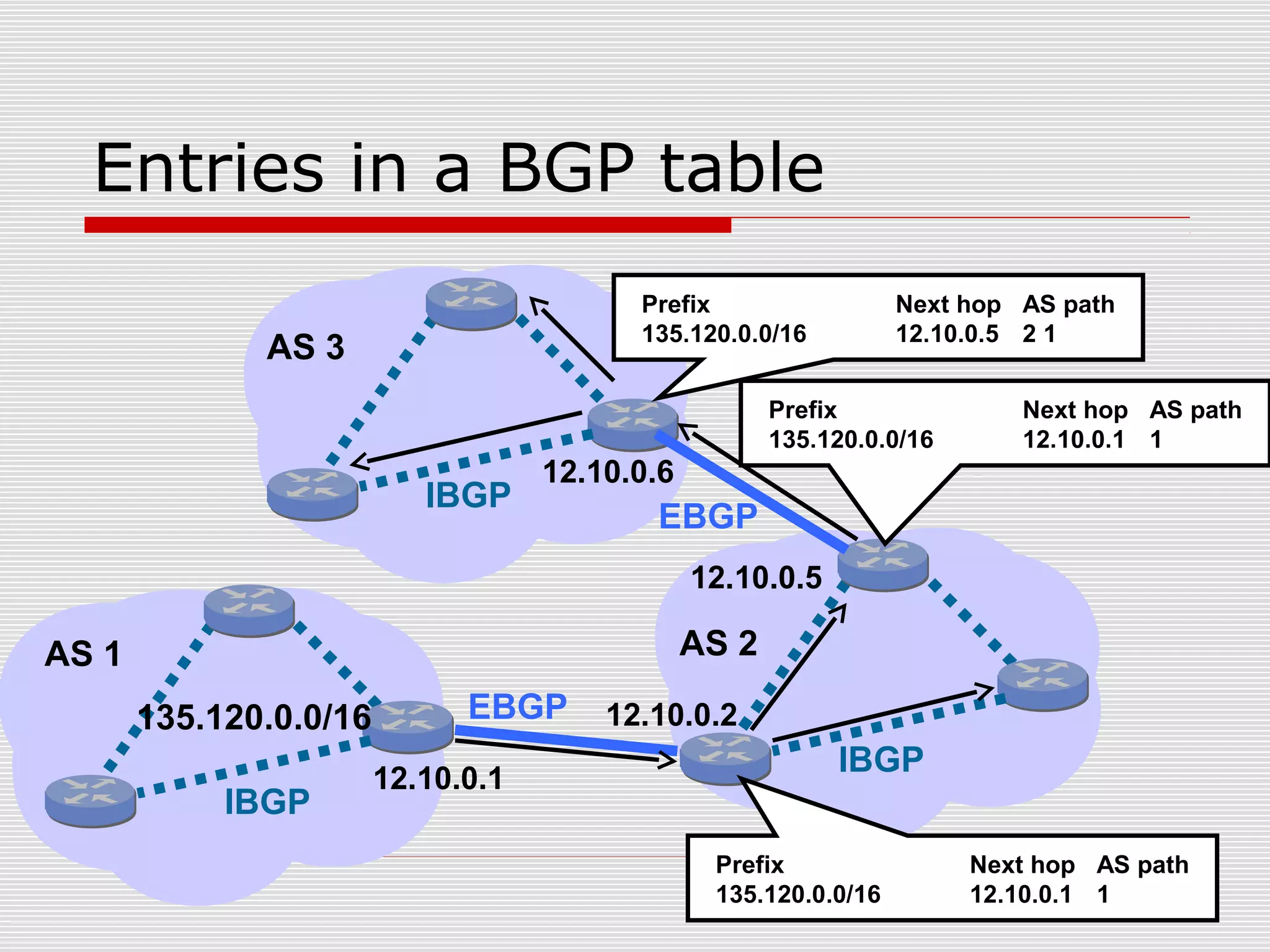
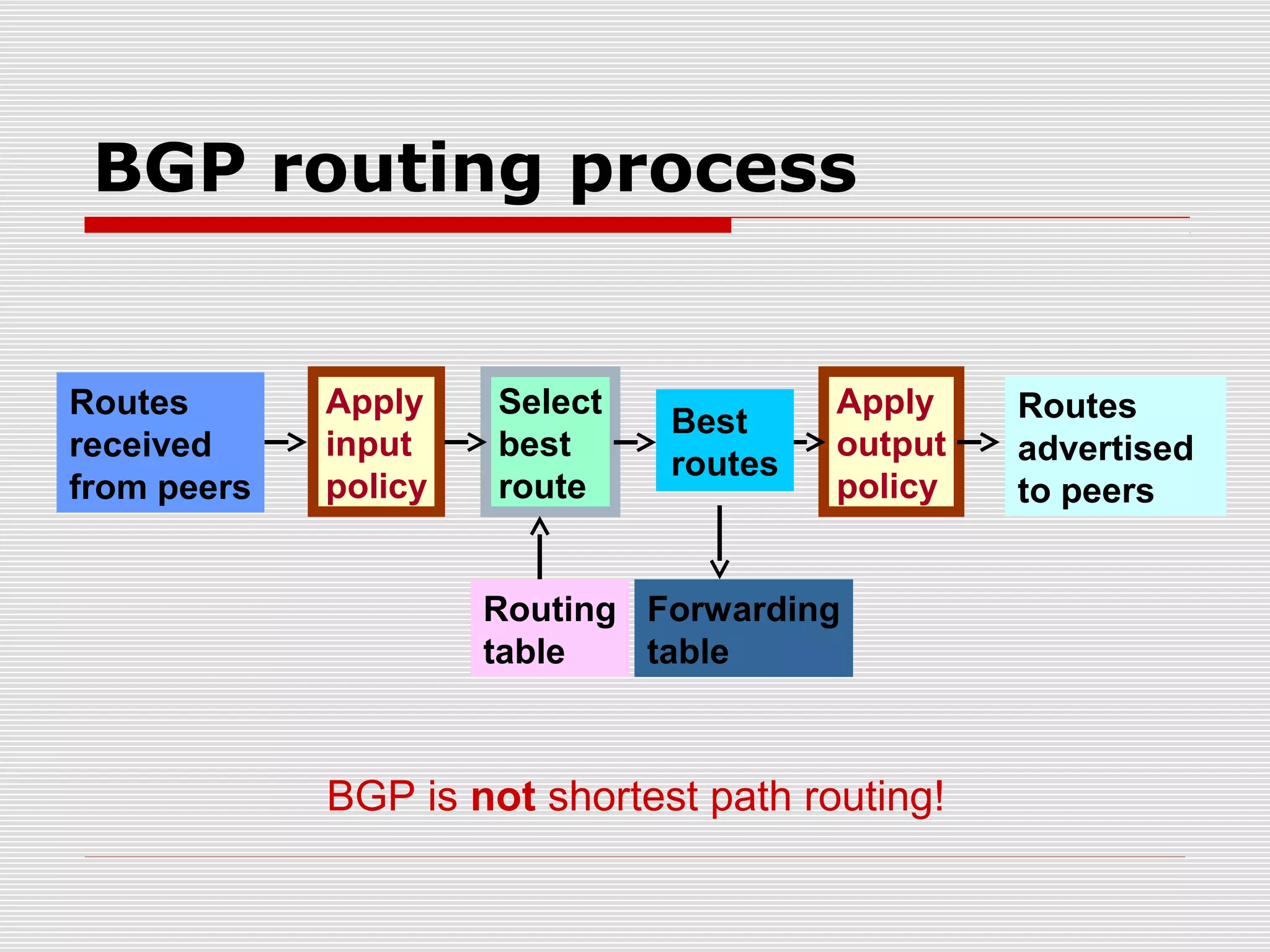
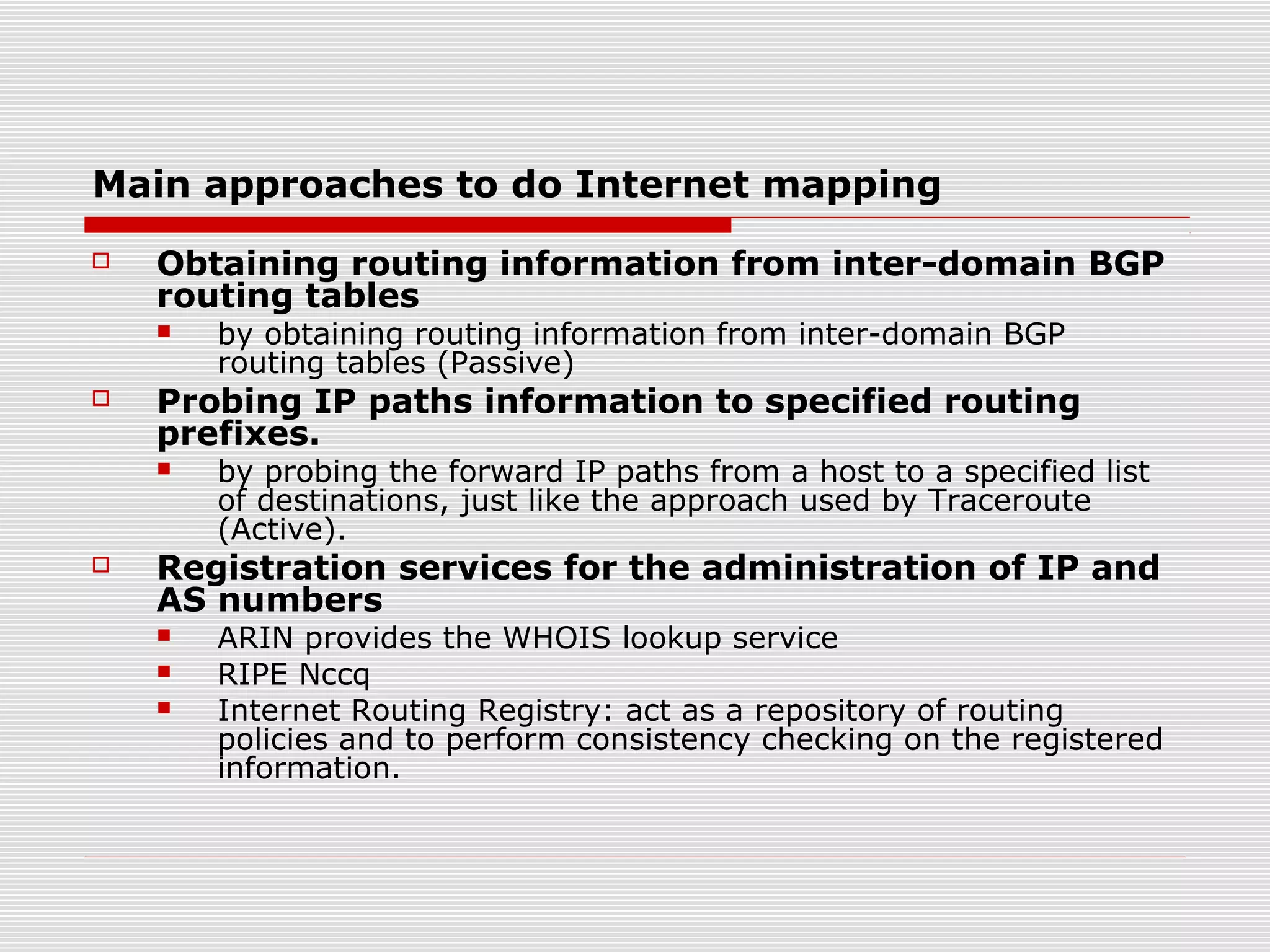
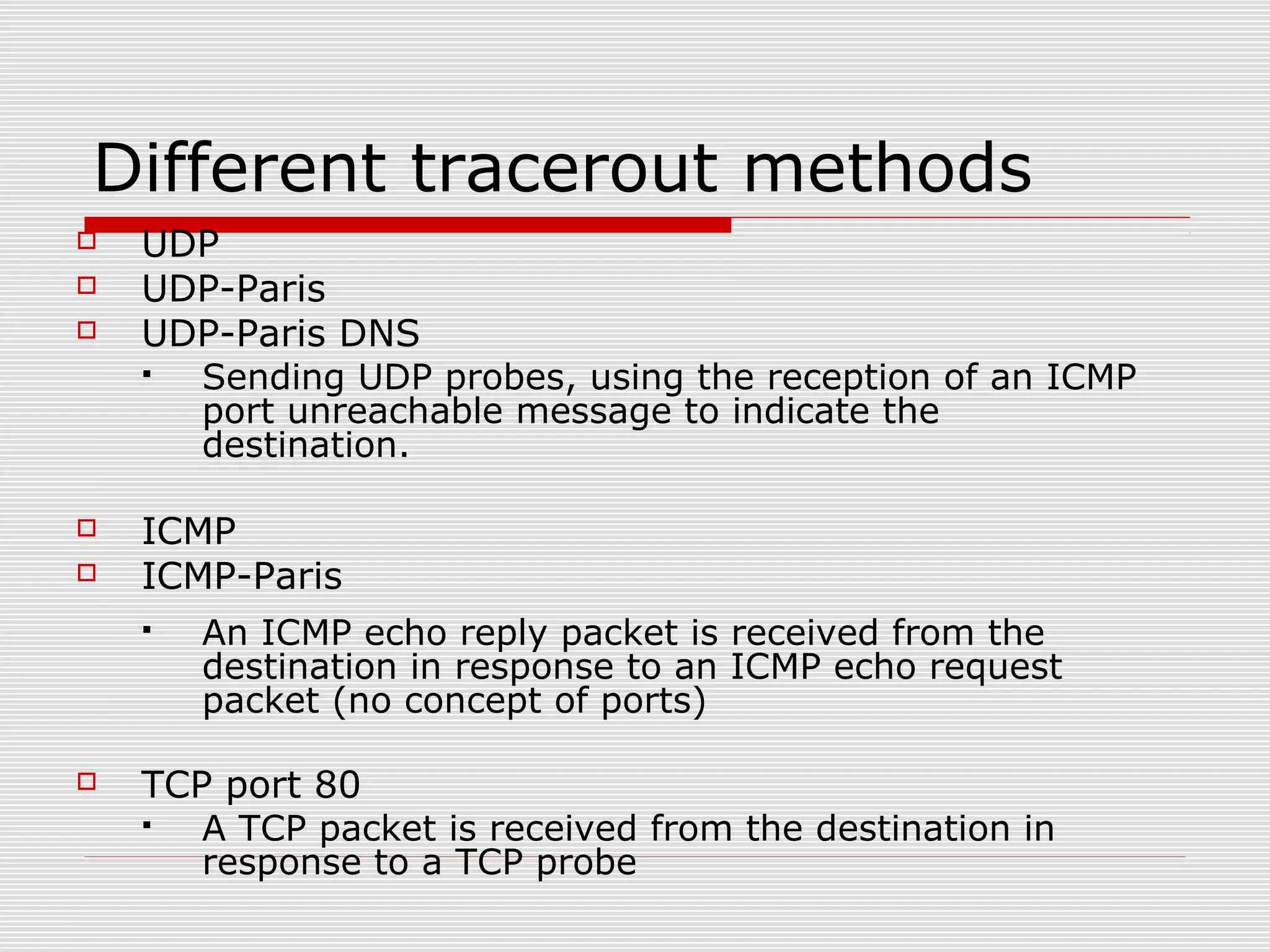
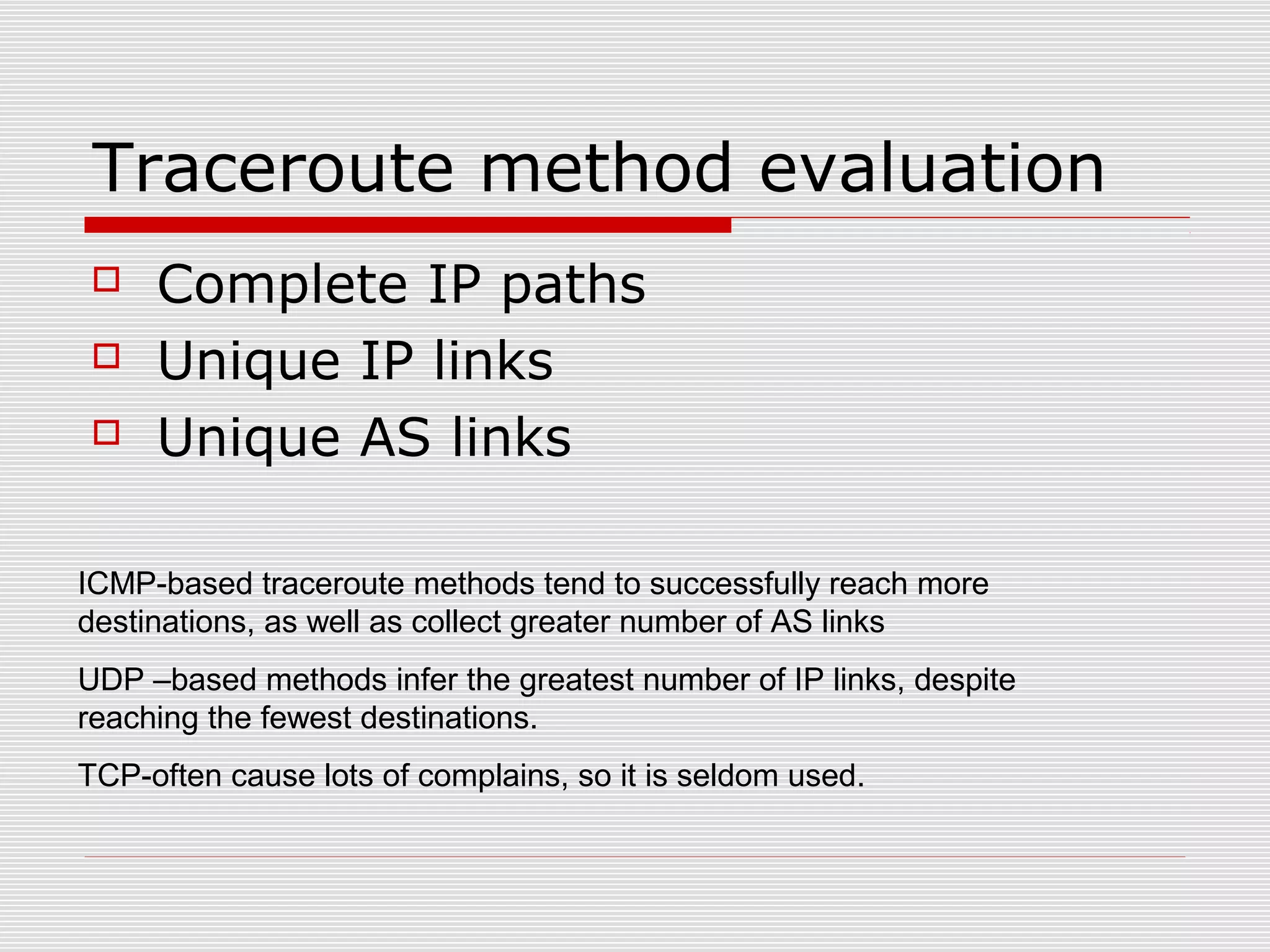
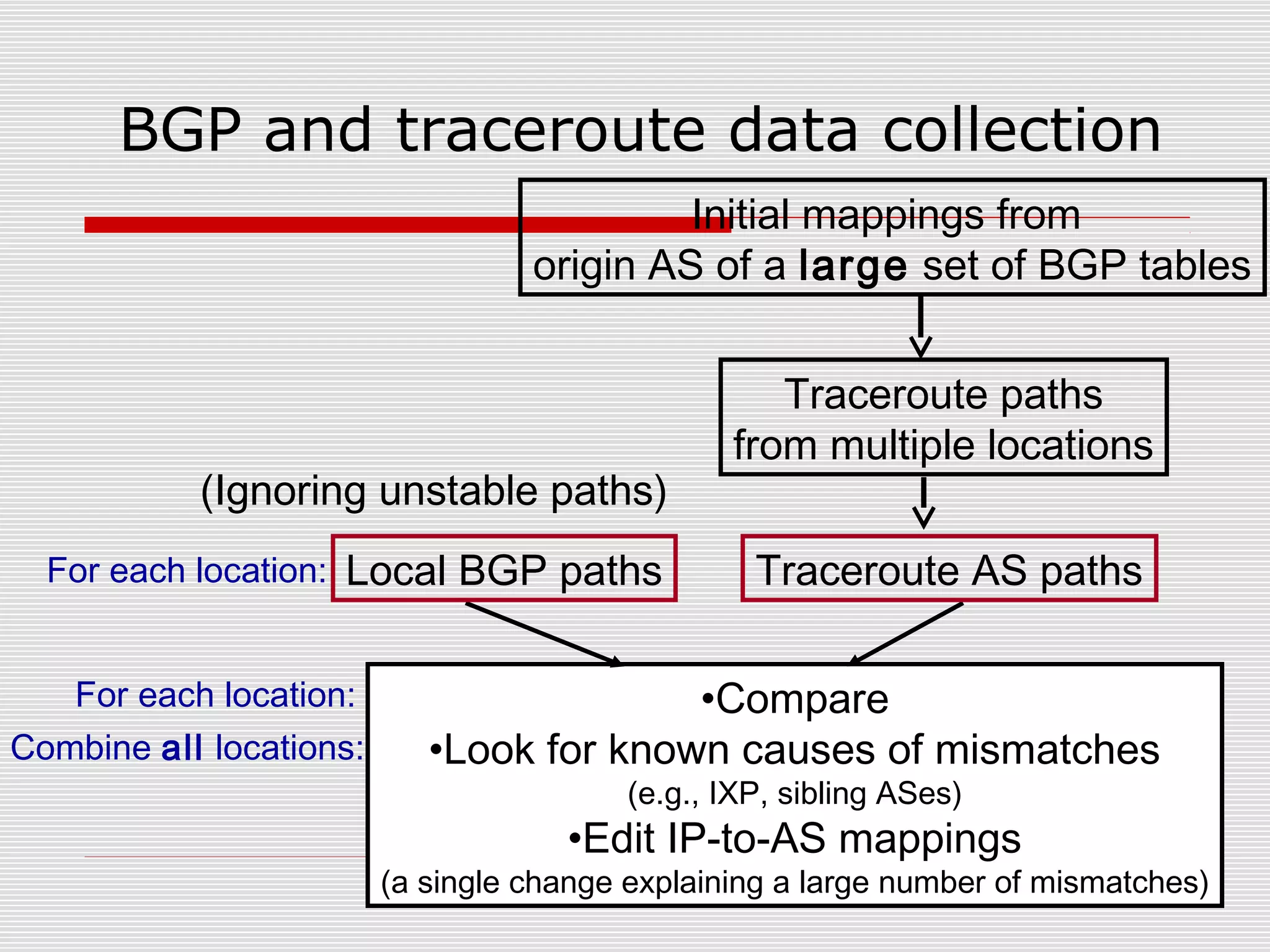
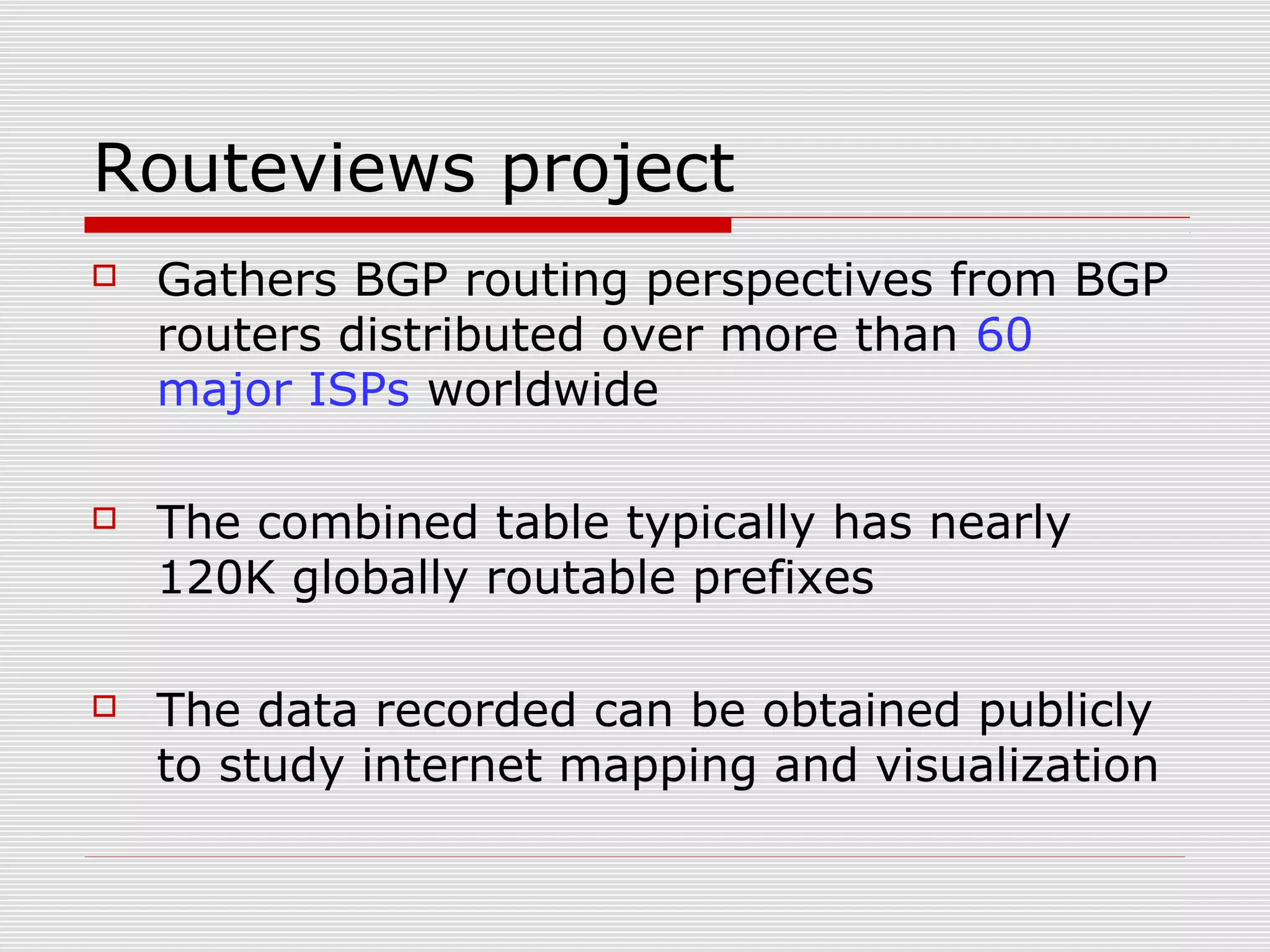
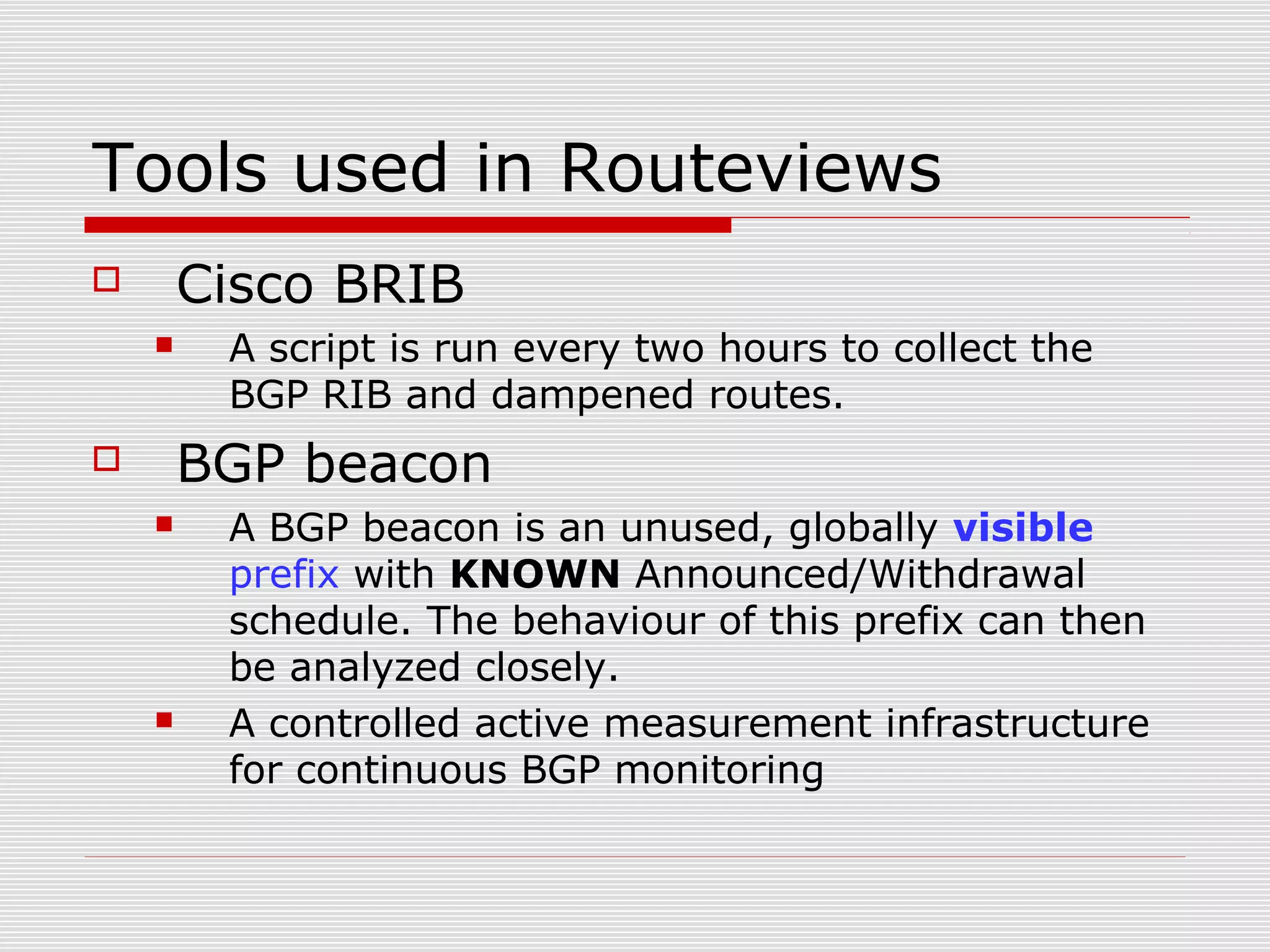
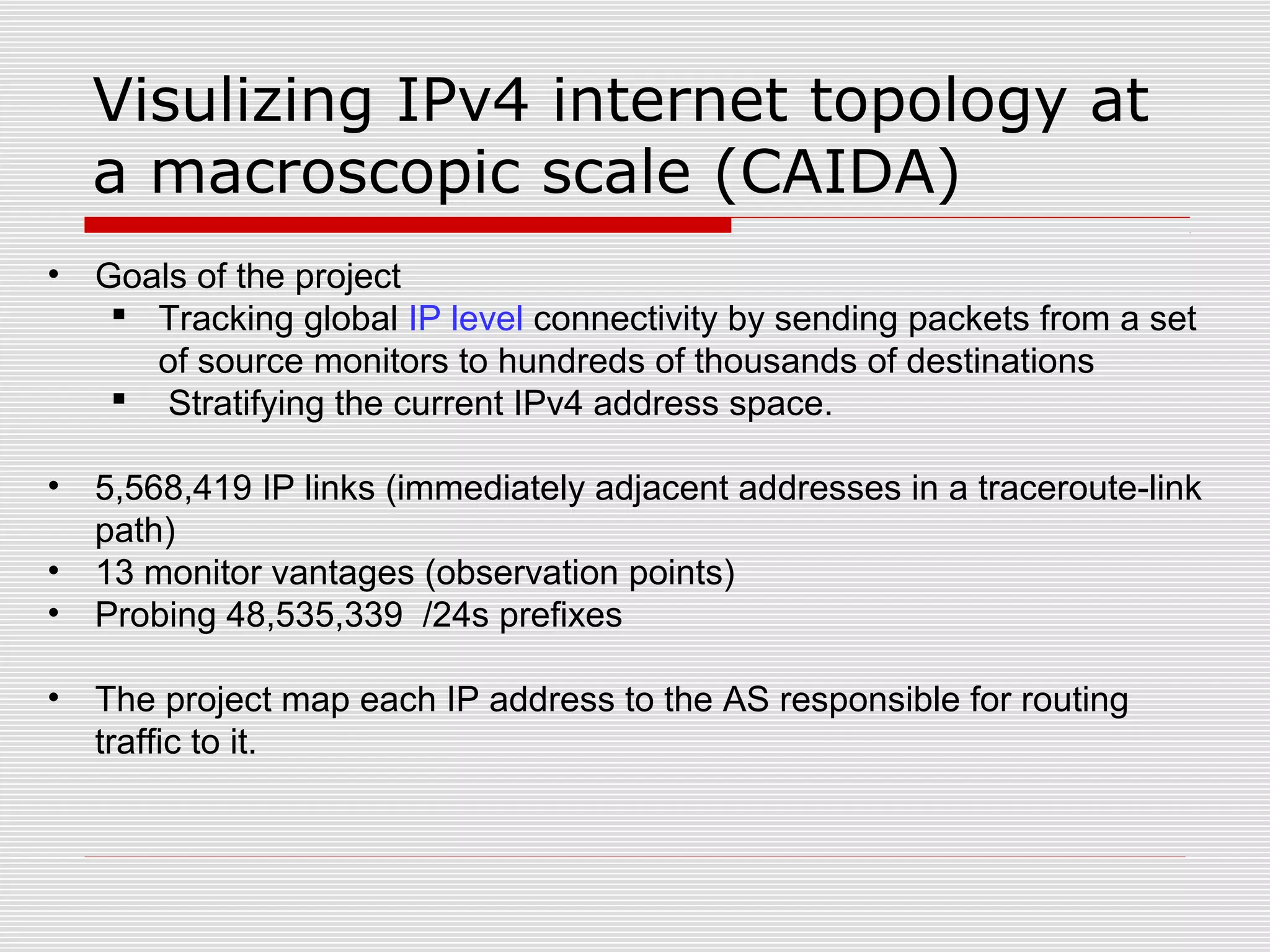
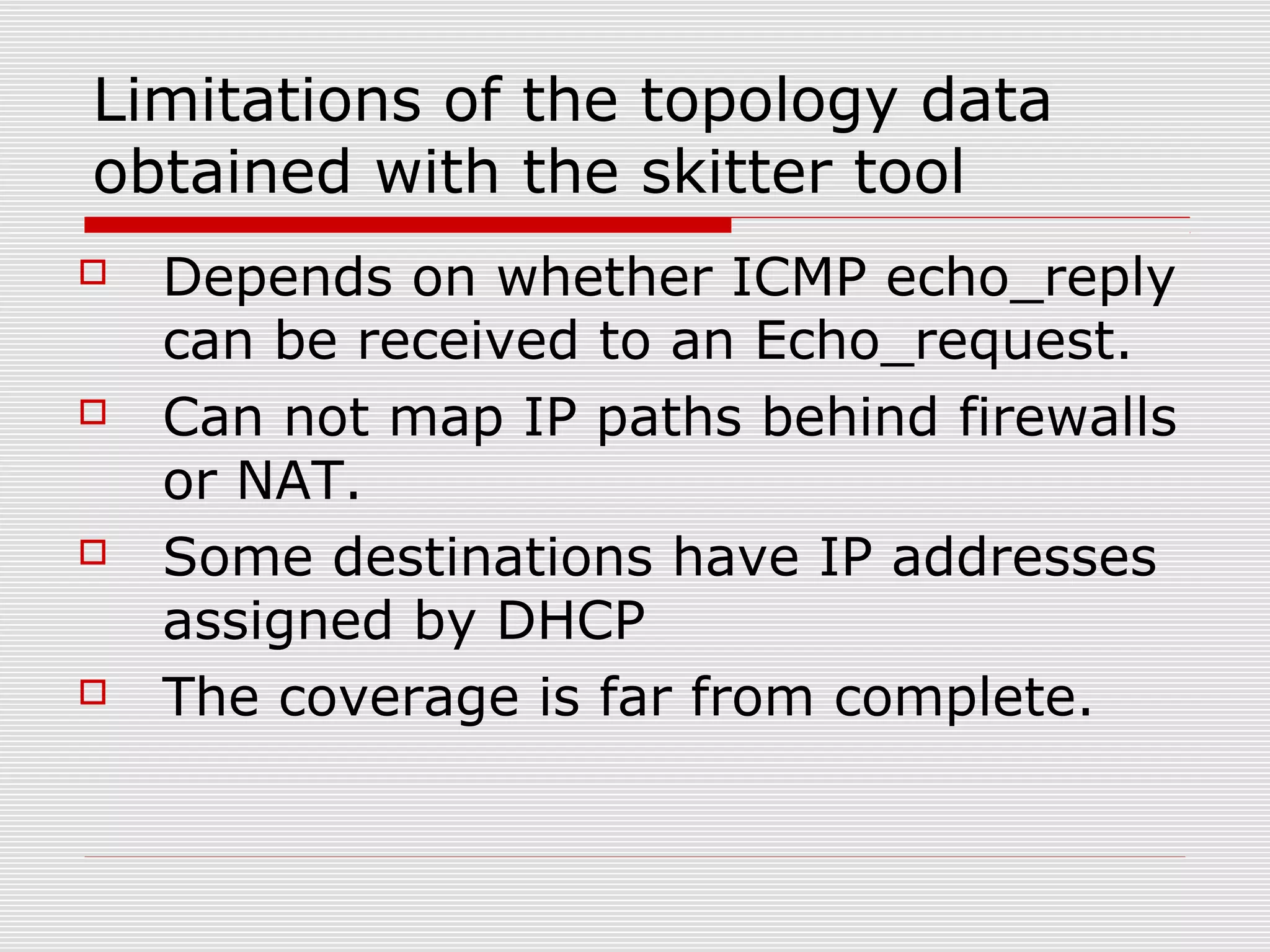
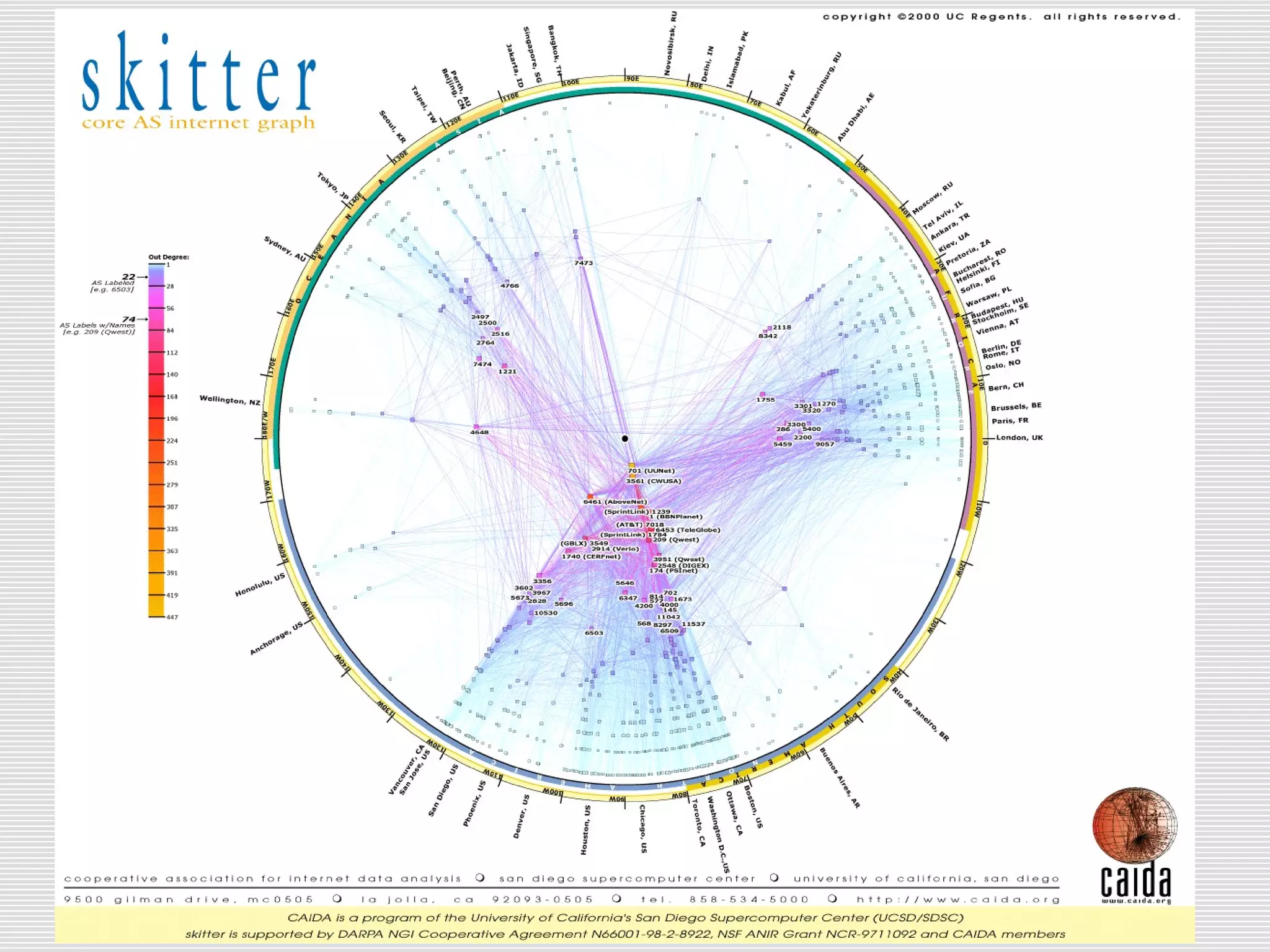
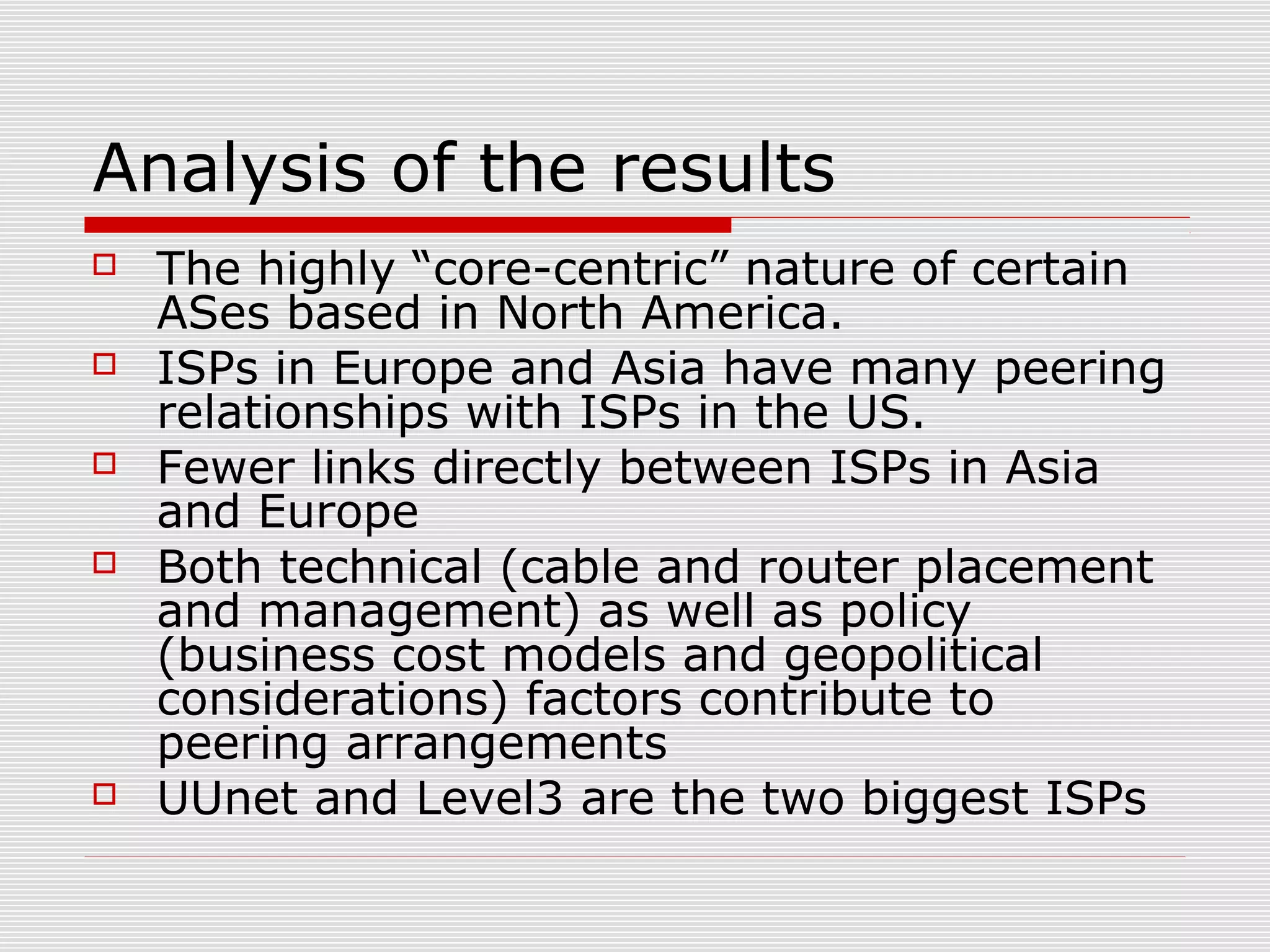
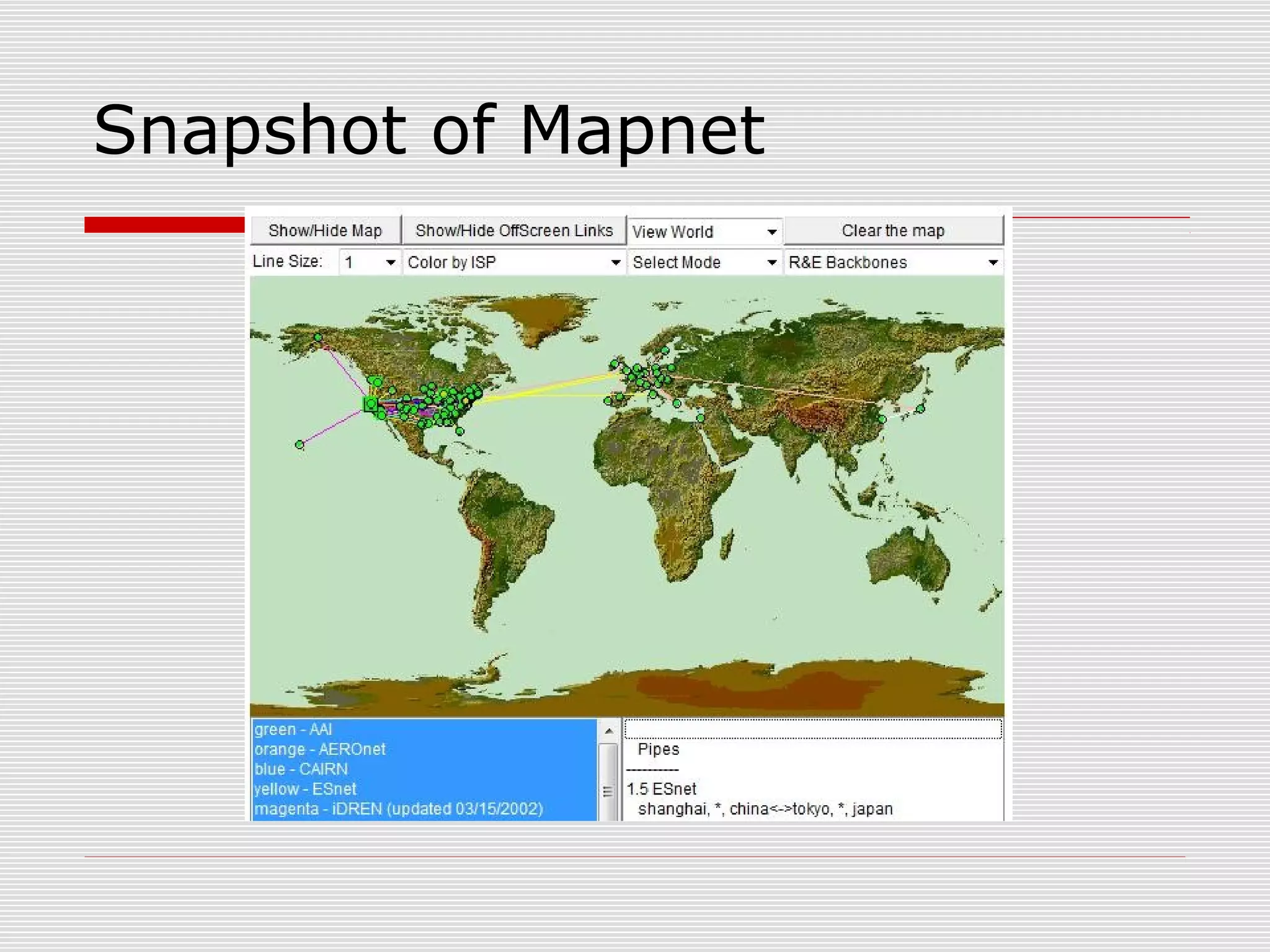
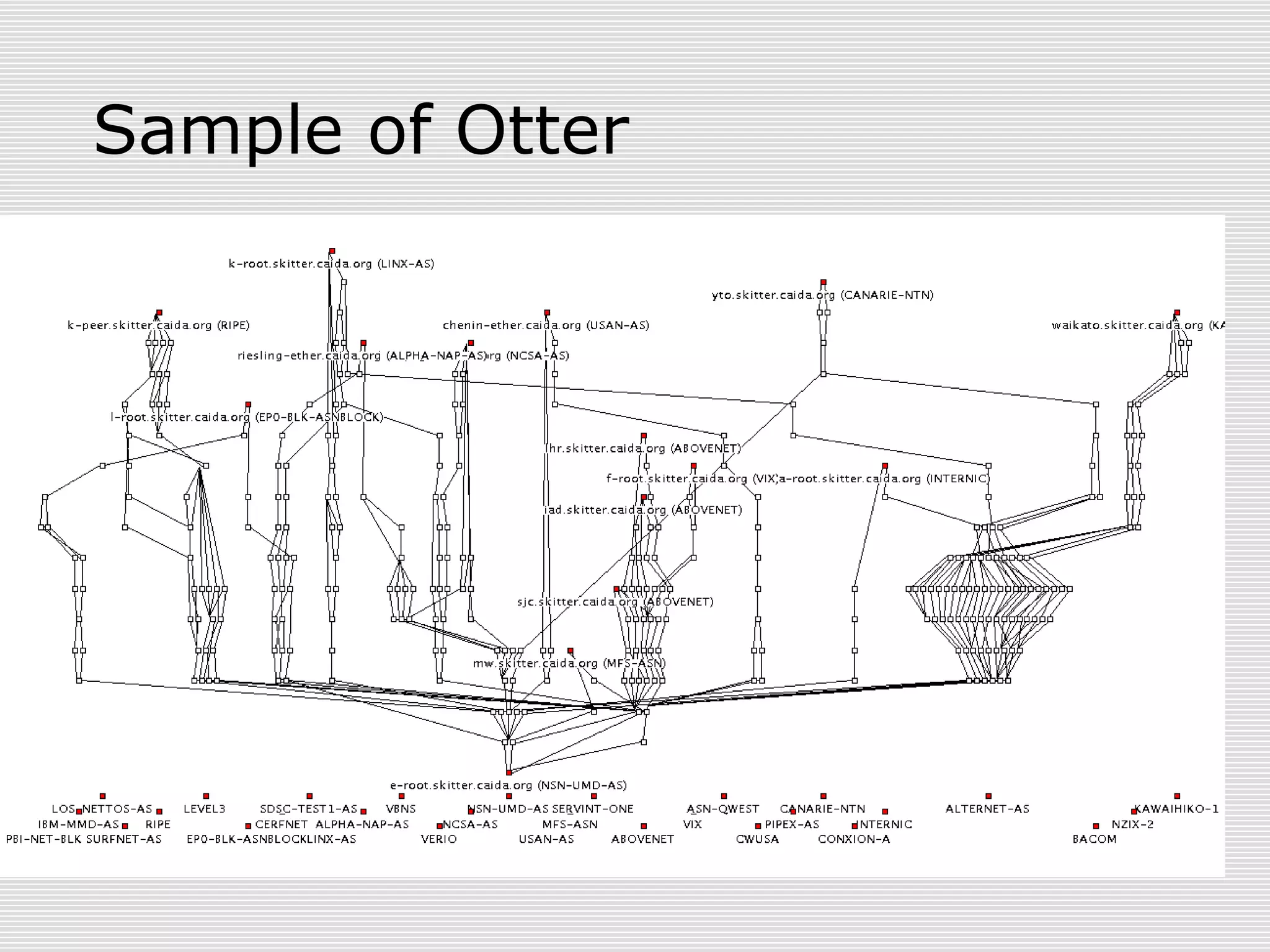
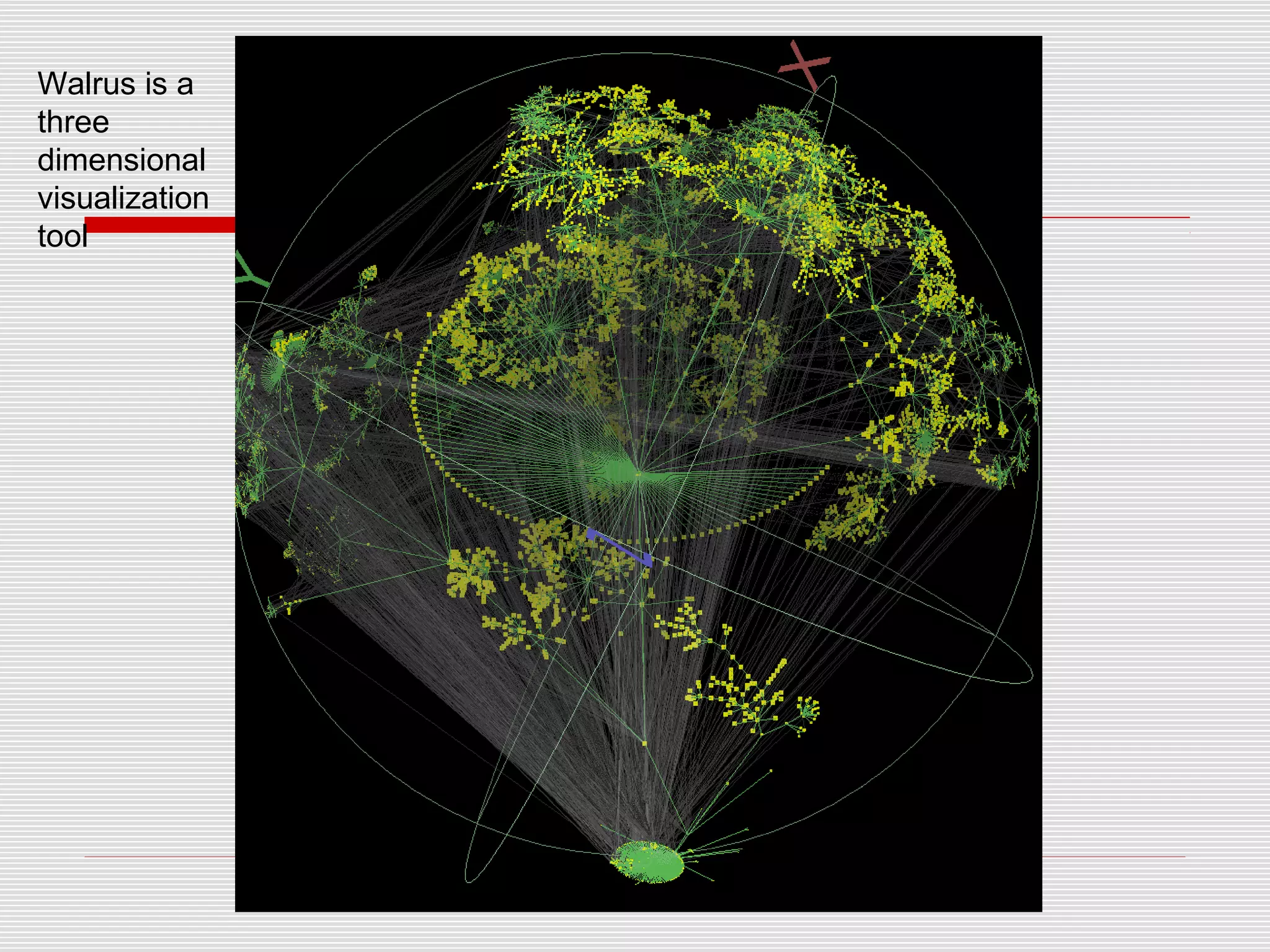
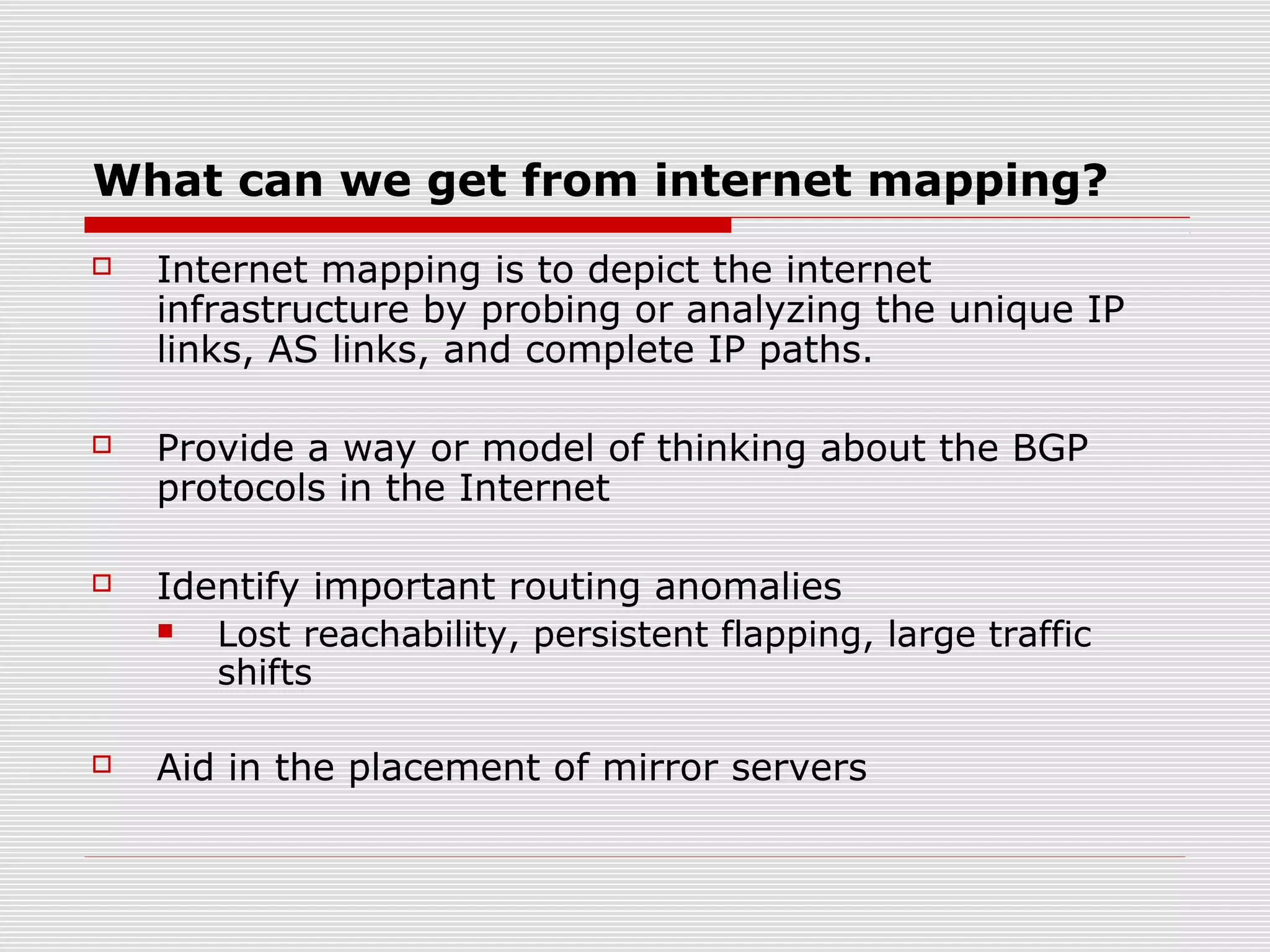
This document discusses internet mapping and visualization. It describes collecting BGP and traceroute data from multiple vantage points to map IP addresses and autonomous systems (AS). This involves extracting prefix-AS mappings from BGP tables and using traceroute to map IP addresses to ASes. Several projects are examined, including Routeviews which collects BGP routing data and CAIDA which maps the IPv4 address space. Tools for visualization like Mapnet, Otter, and Walrus are also overviewed. Internet mapping provides insights into the internet infrastructure, routing anomalies, and AS relationships.