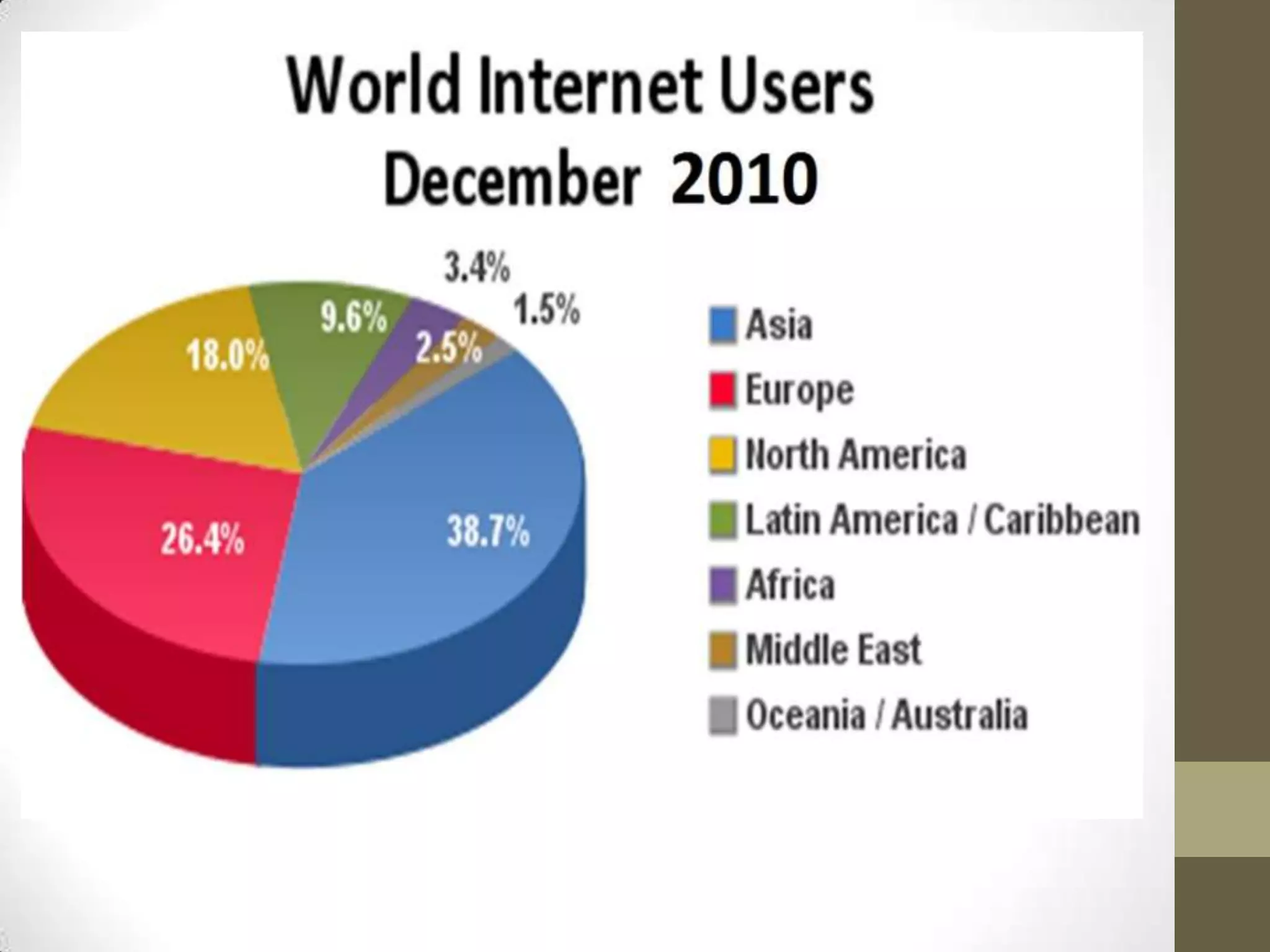
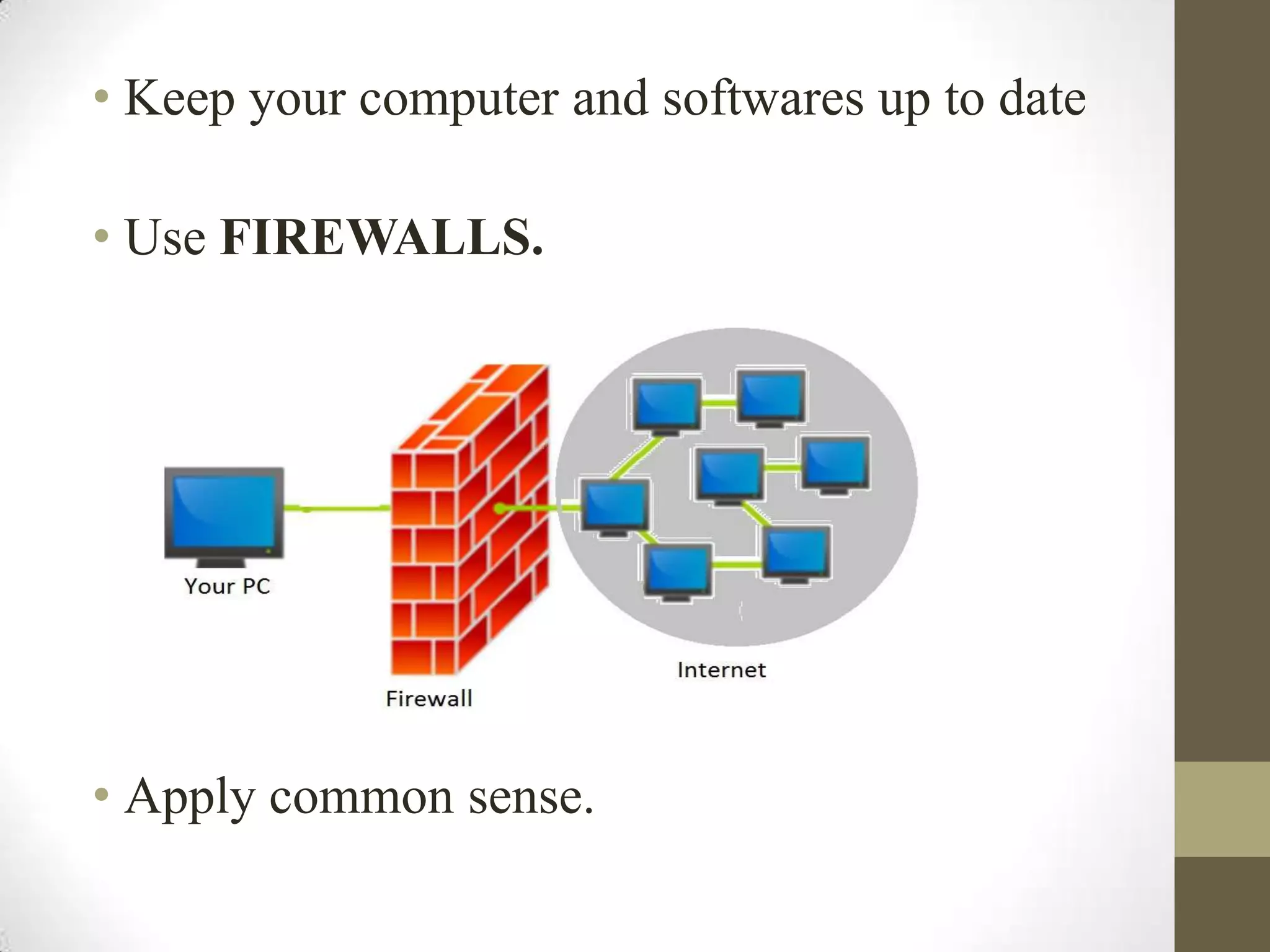
The document provides an overview of the internet, including its history and components. It discusses the world wide web and how browsers are used to access web pages. It also mentions some popular search engines and describes common internet services like email, file sharing, online shopping, and games/videos. The document outlines some security threats like viruses, trojans, spyware and hacking. It provides examples of basic attacks such as intrusion, denial of service, and phishing. Finally, it offers tips for staying safe online like using antivirus software, avoiding unsafe websites, and keeping systems updated.