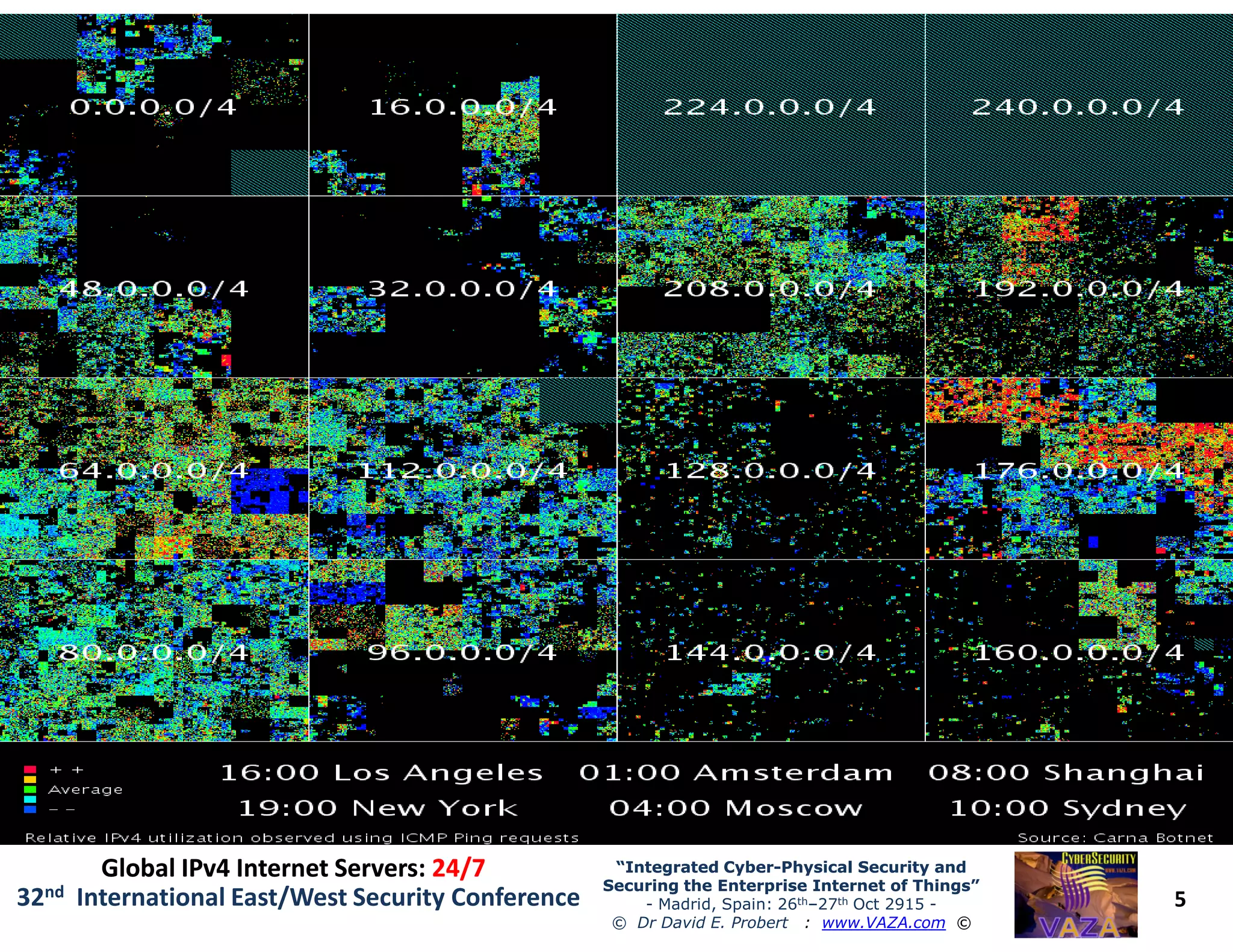
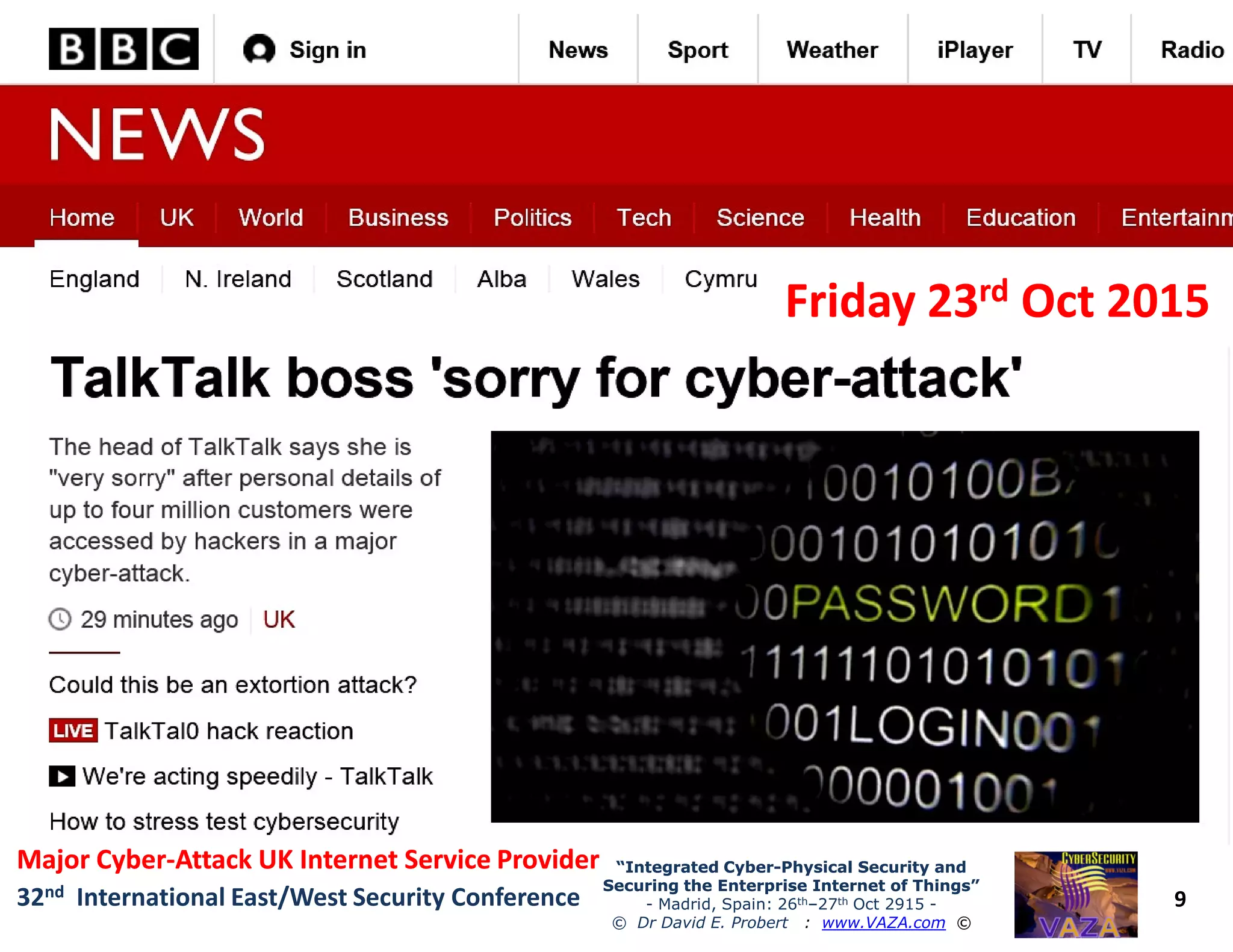
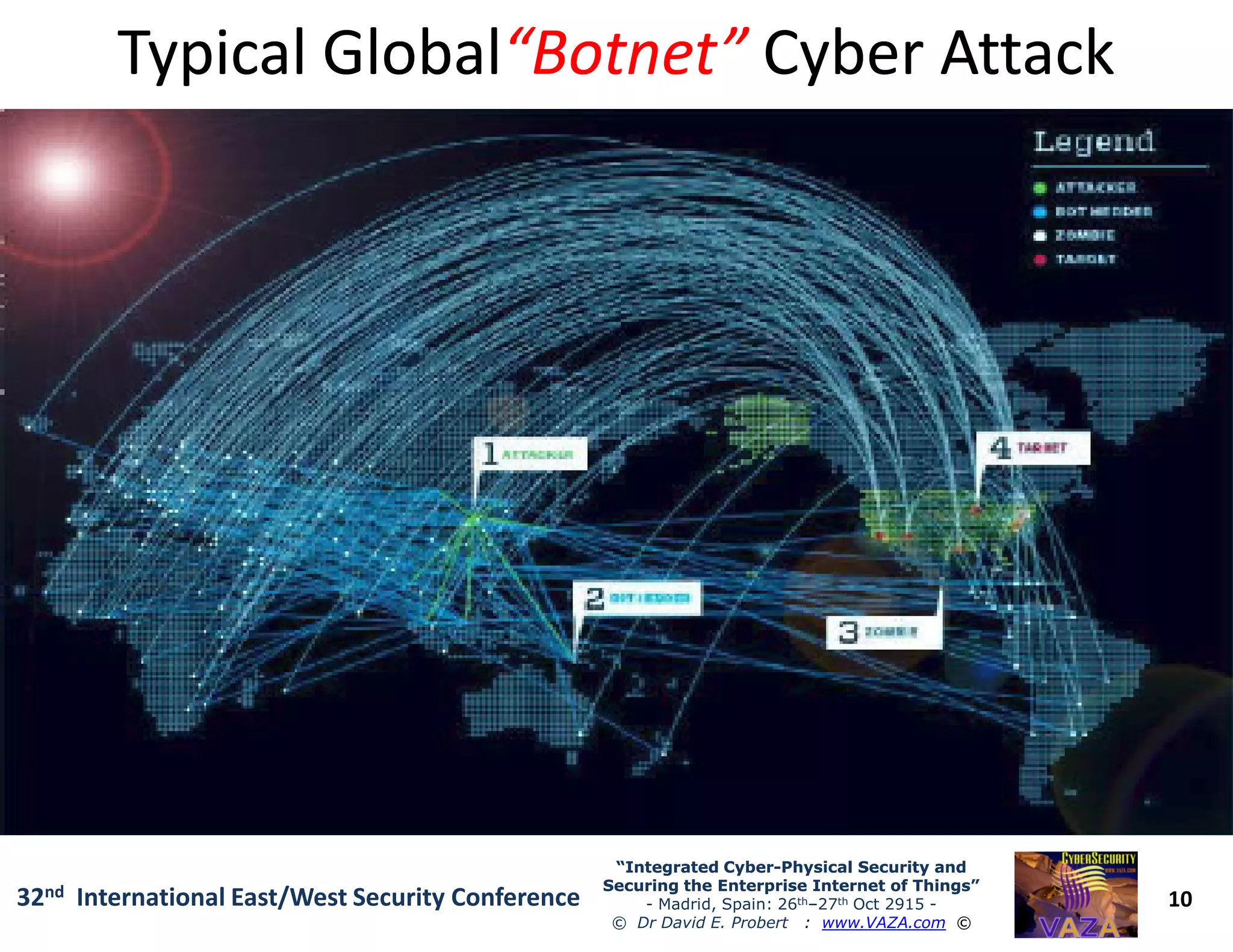
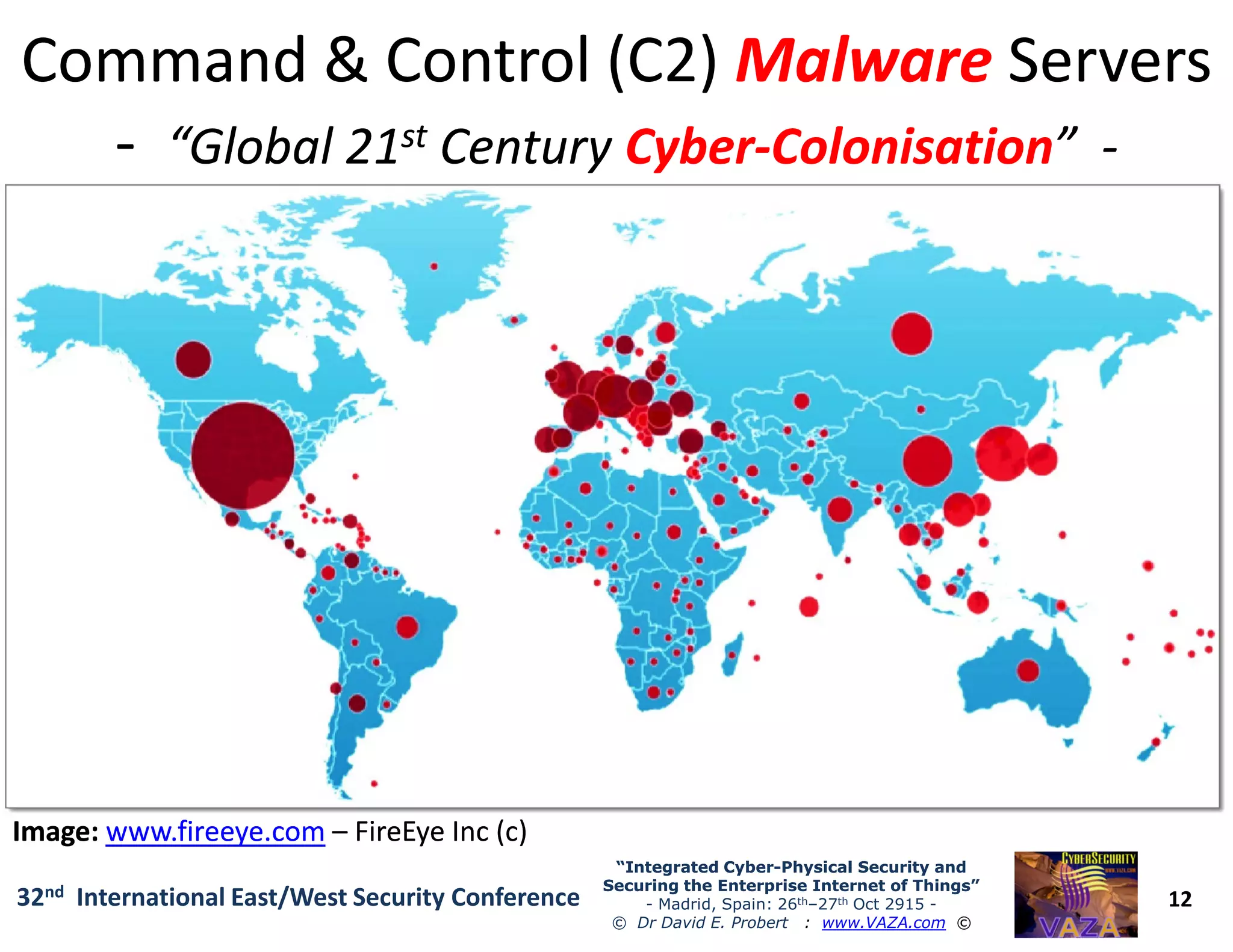
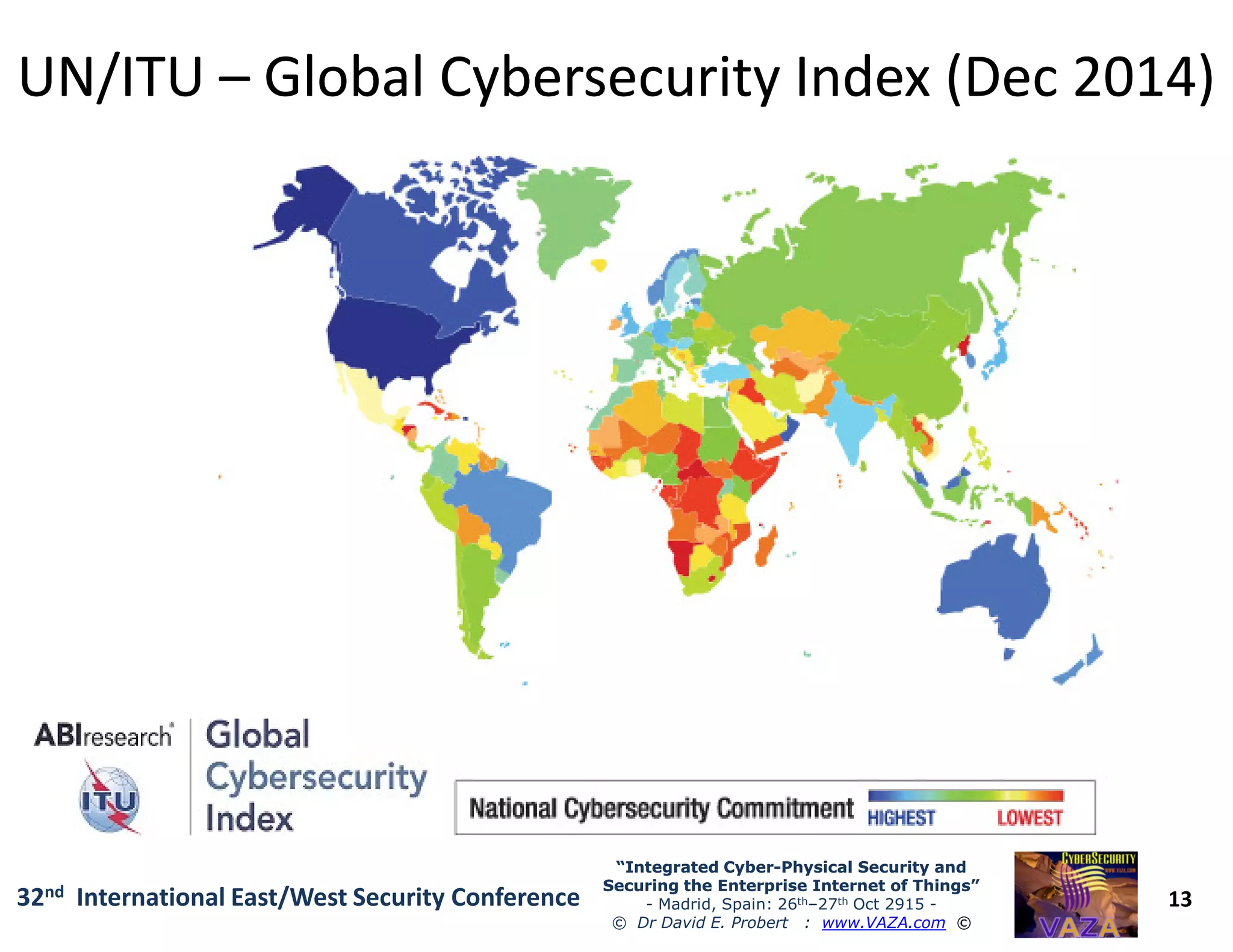
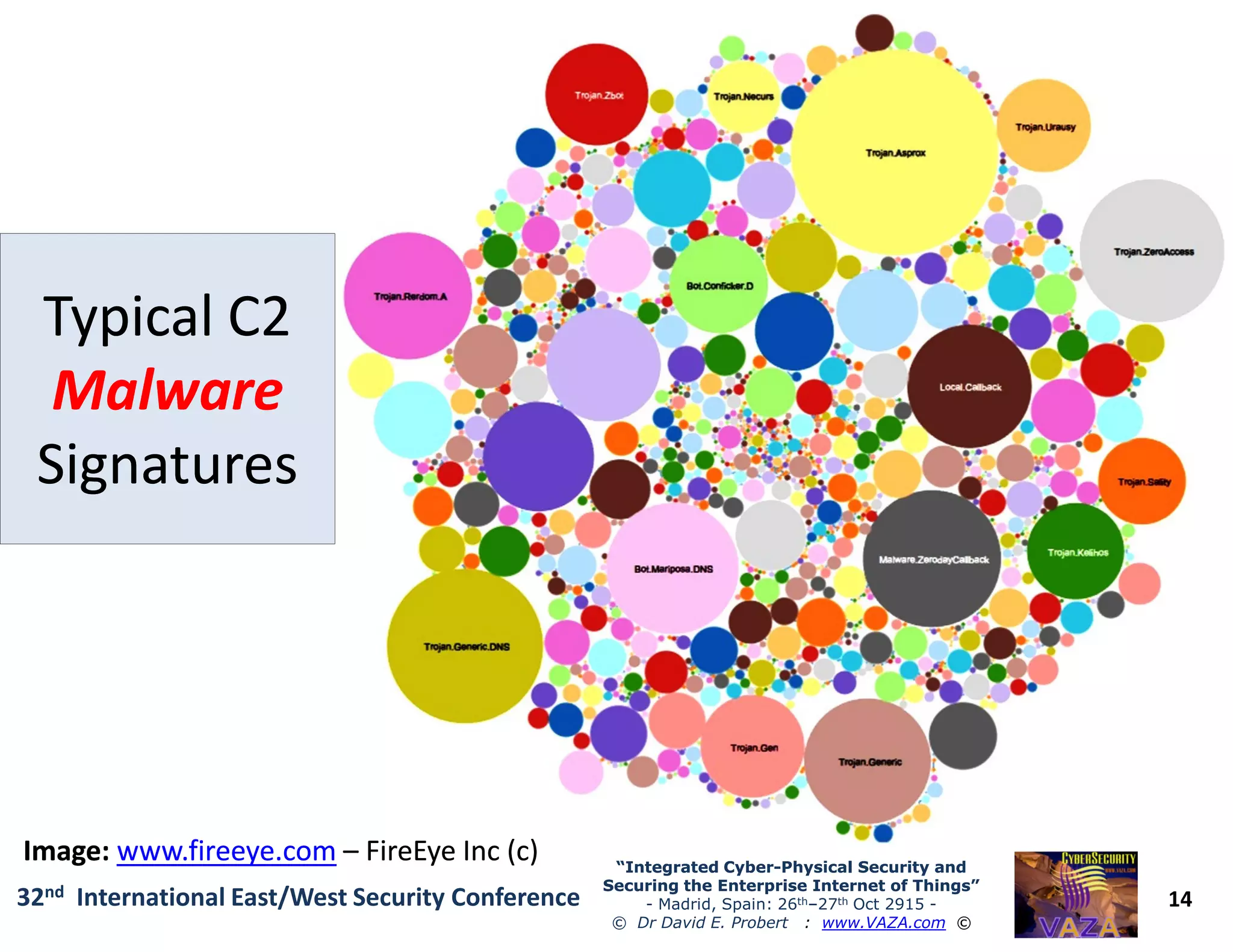
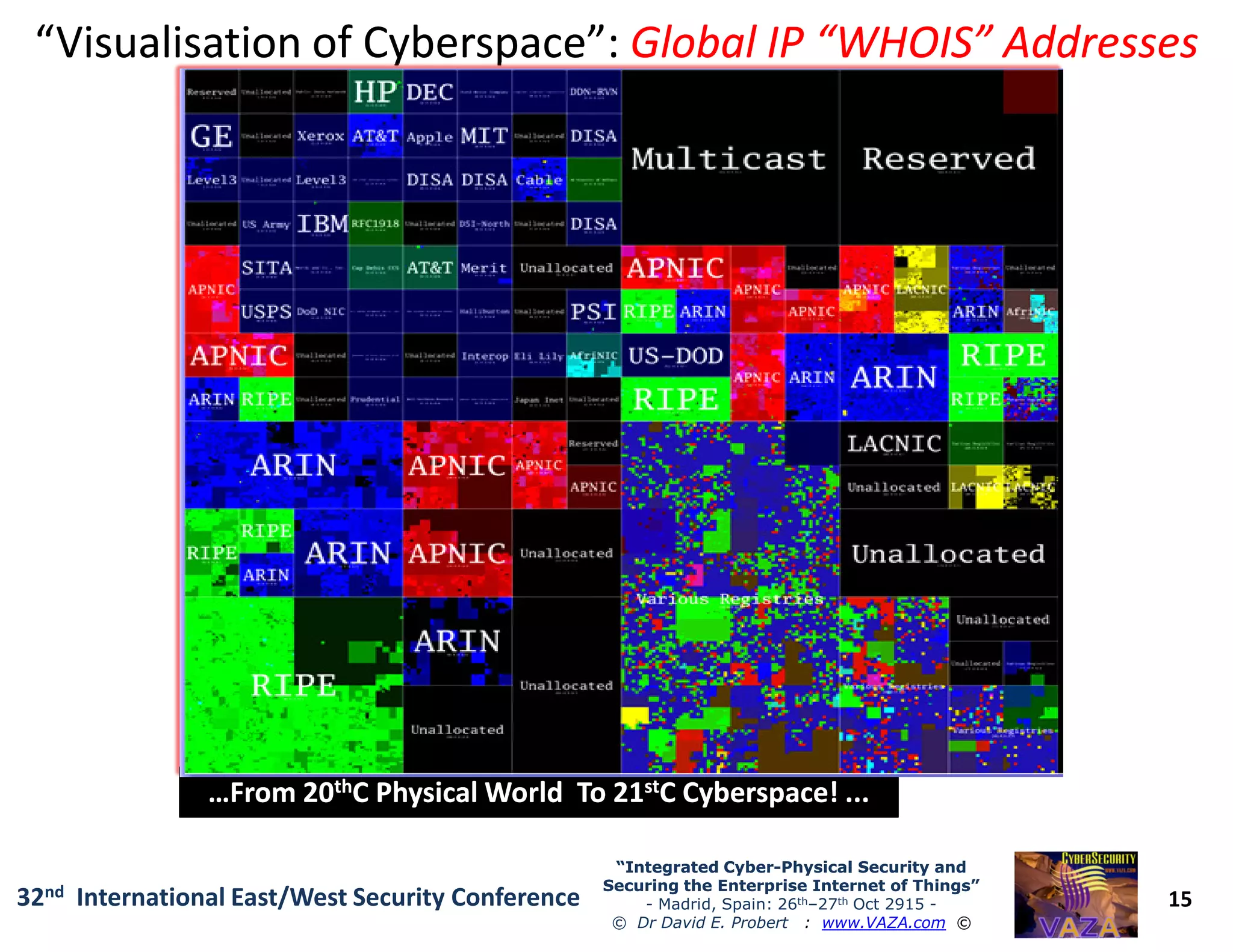
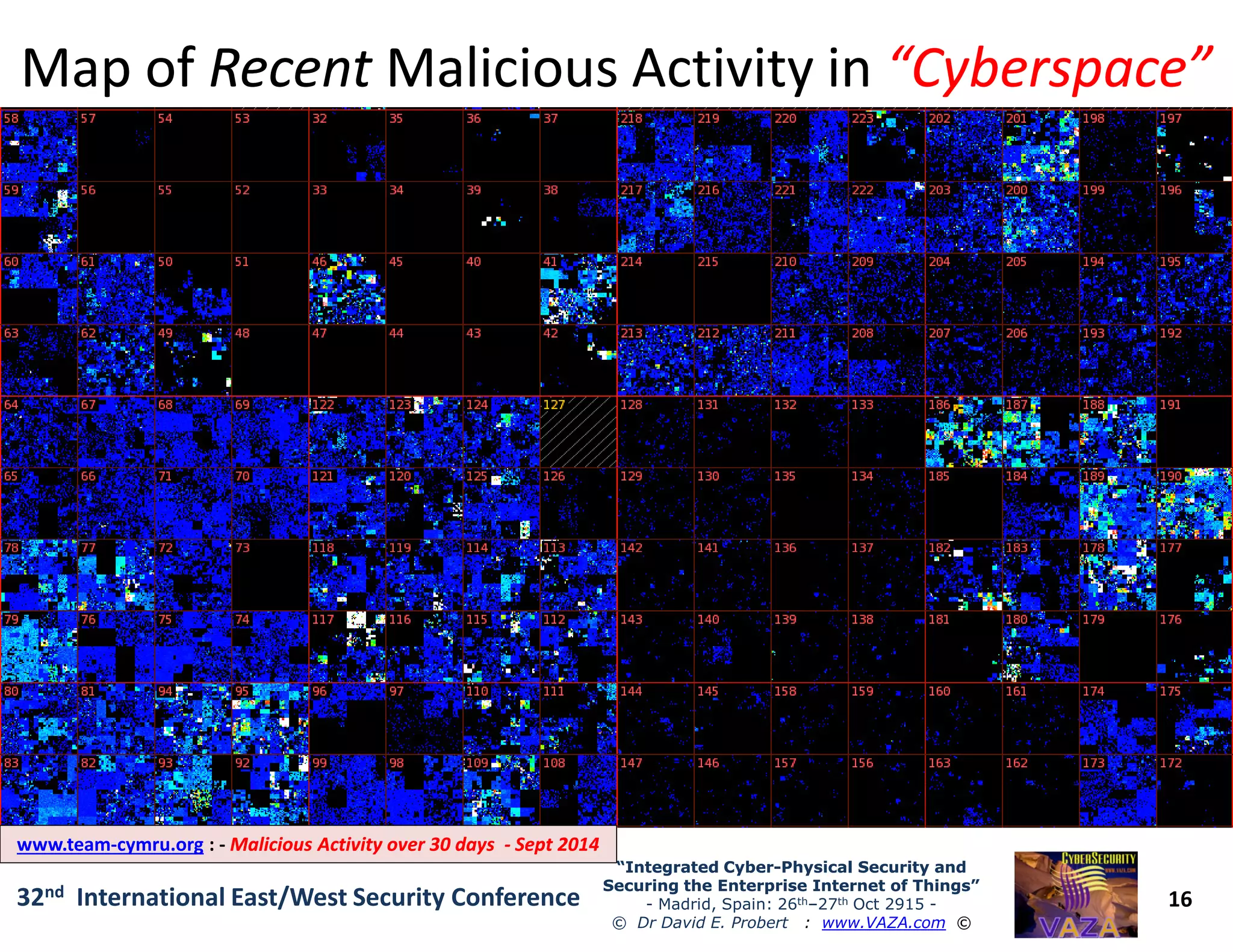
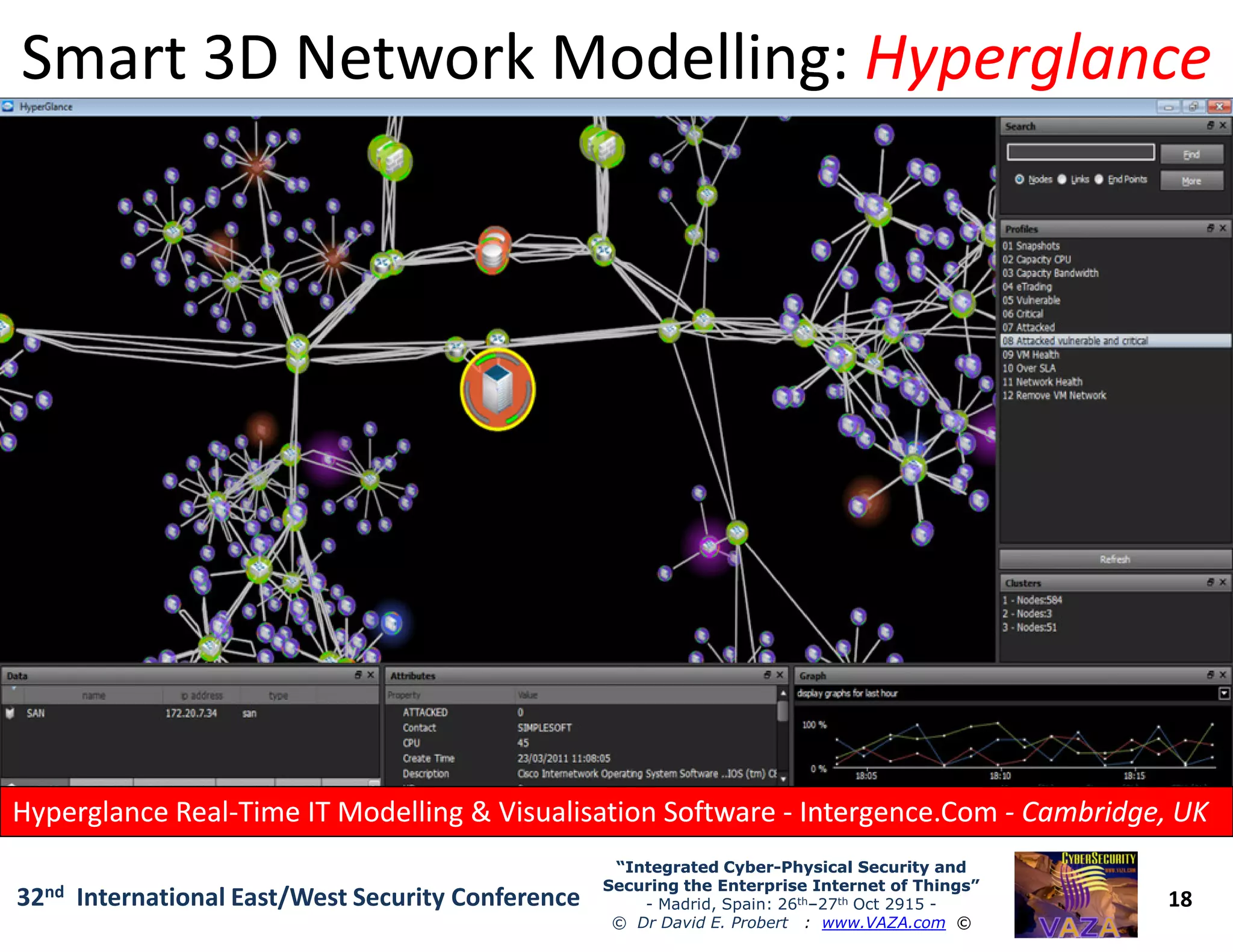
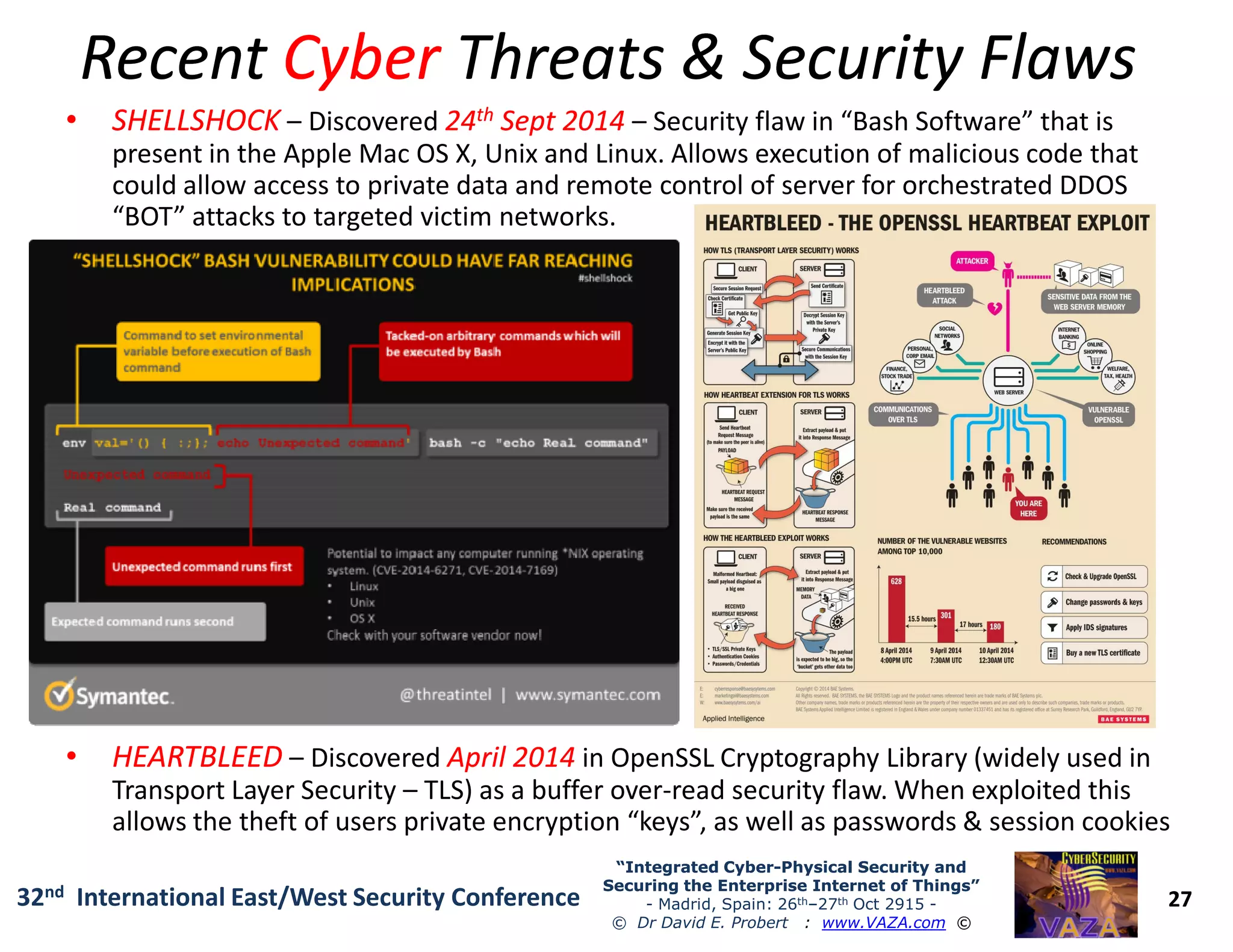
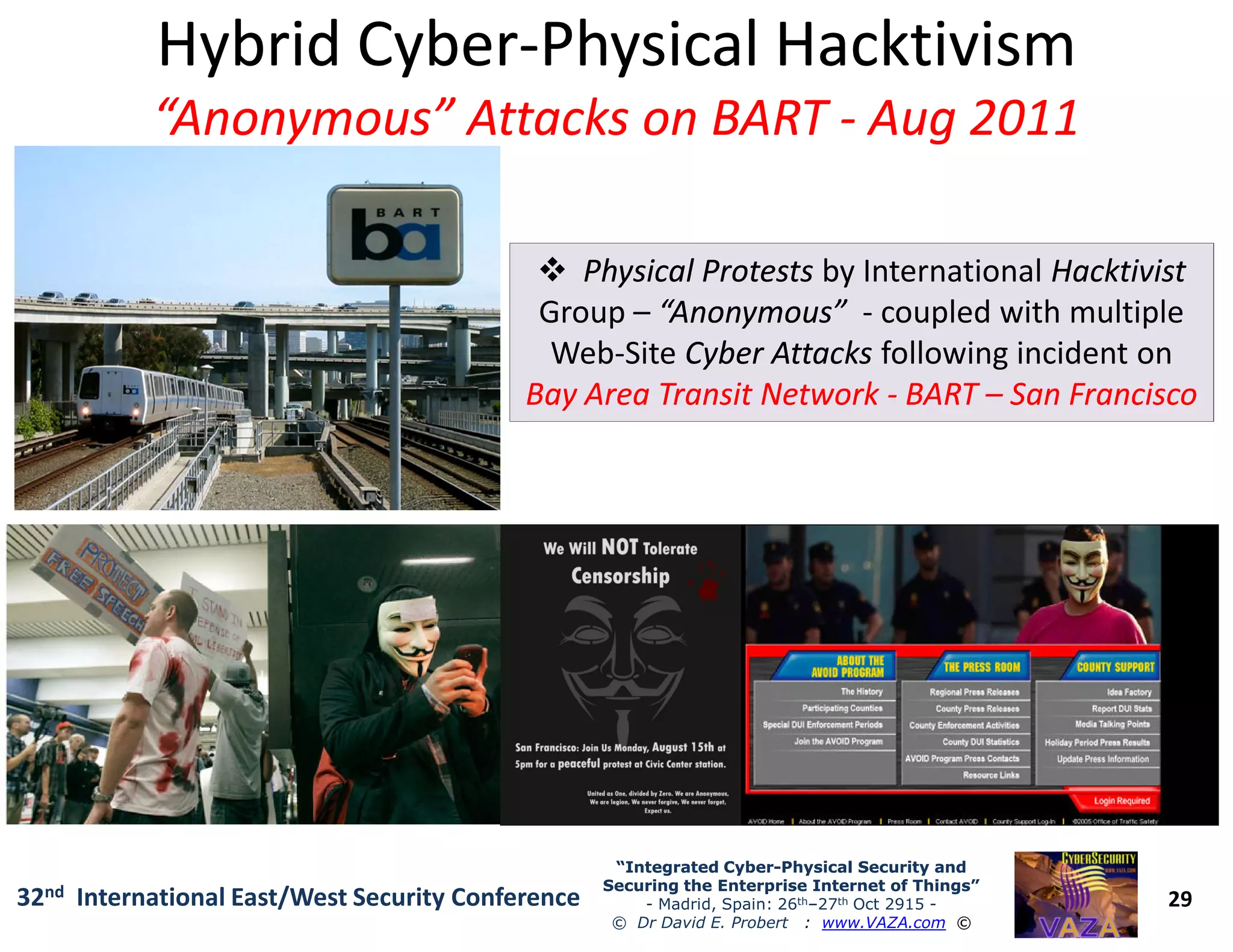
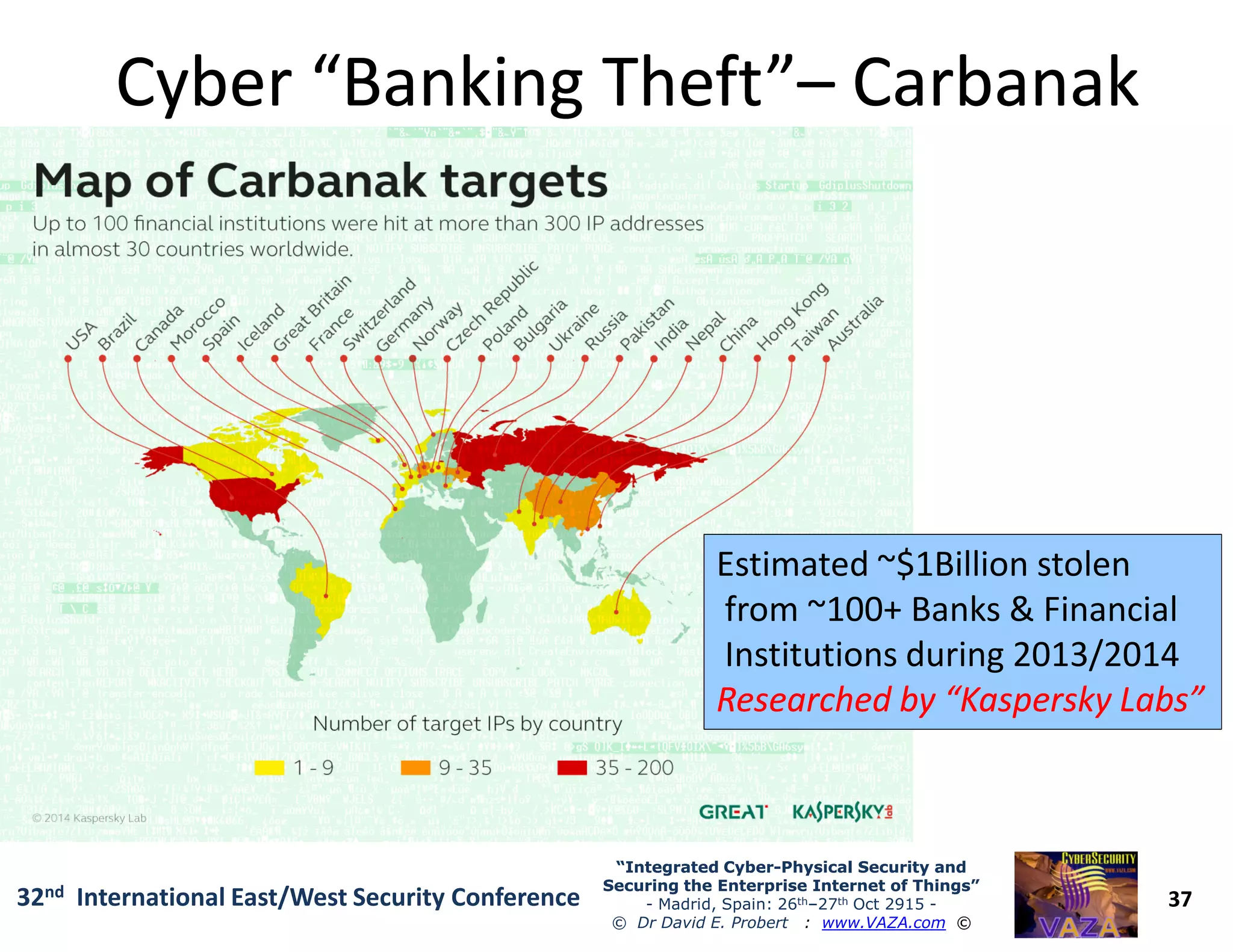
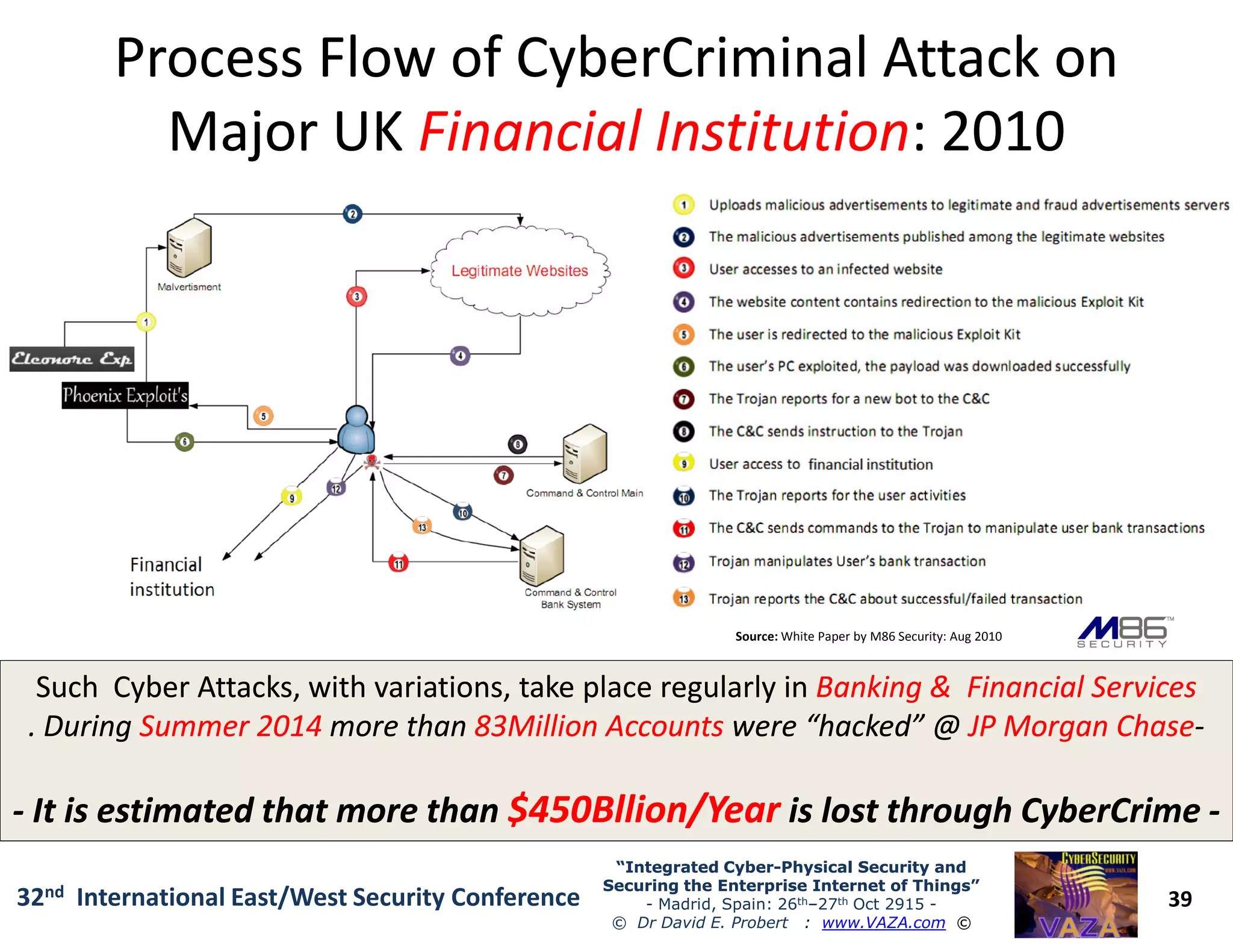
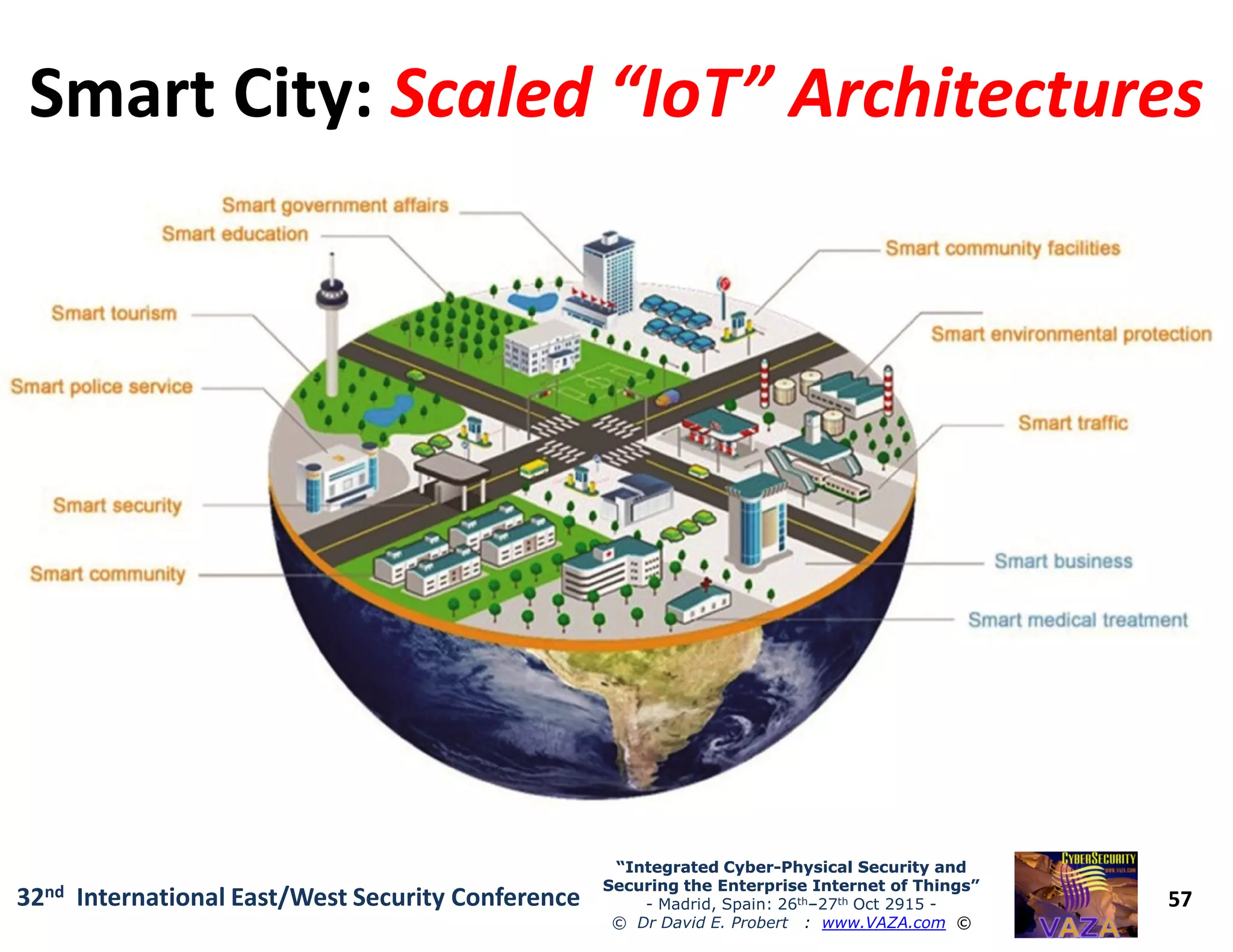
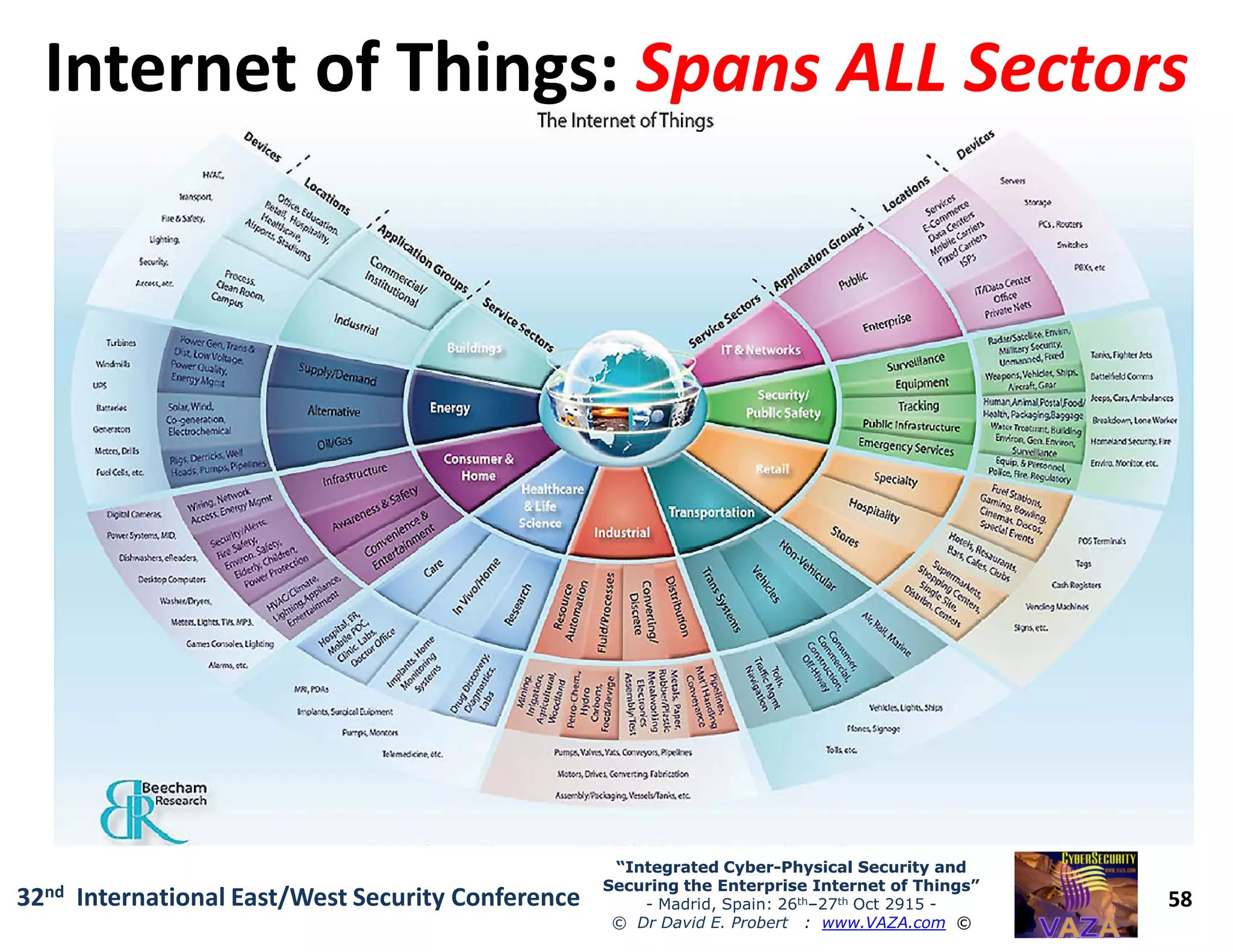
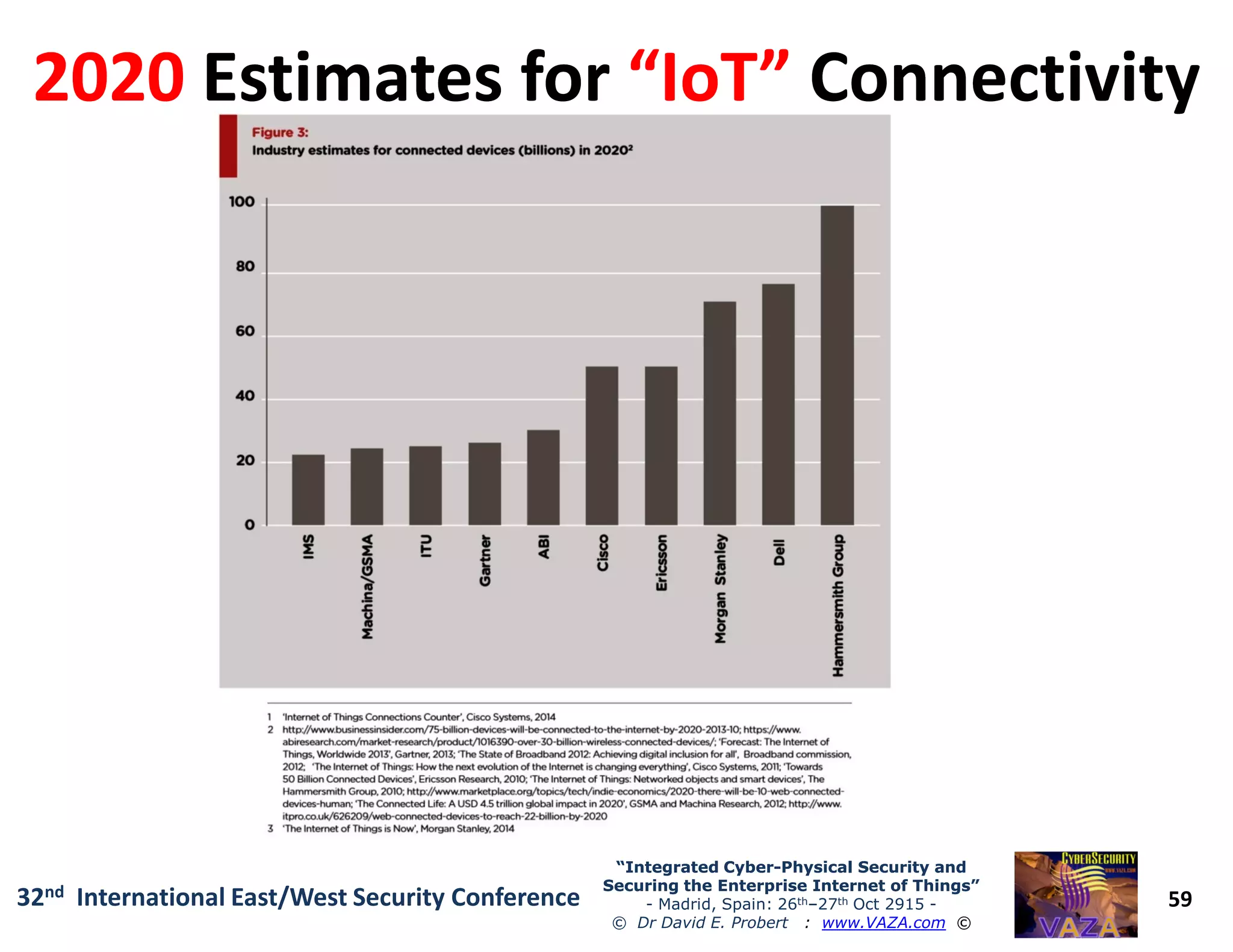
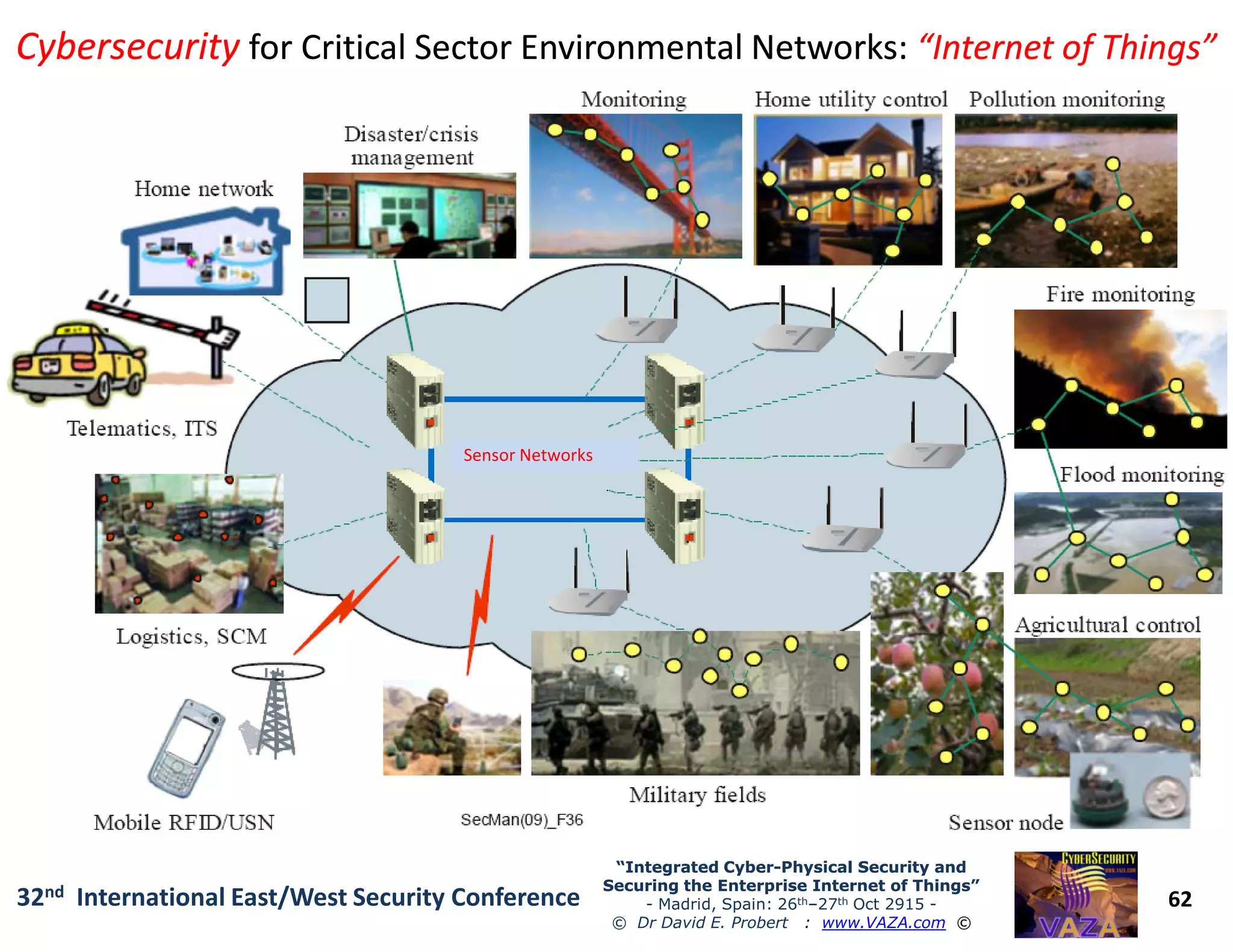
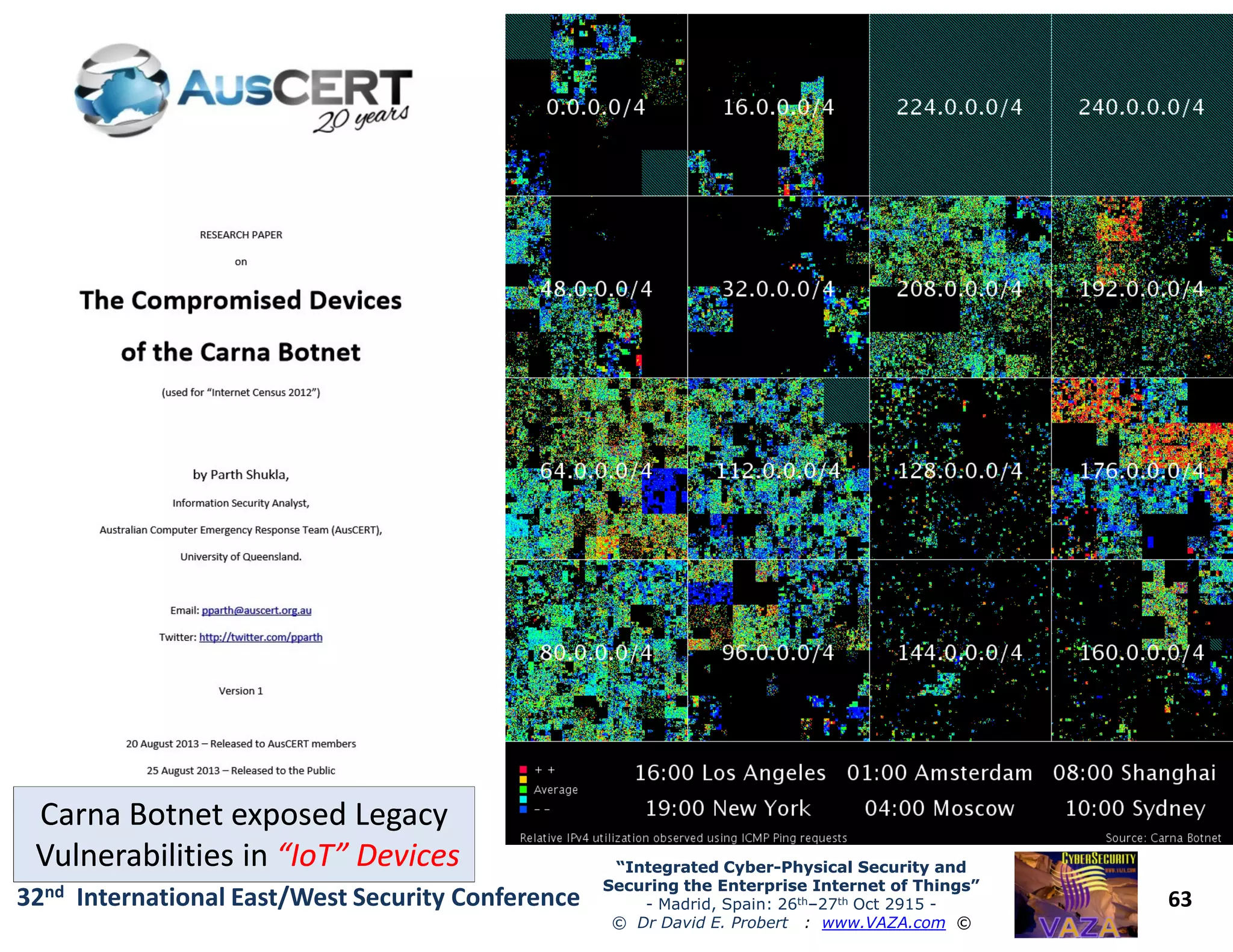
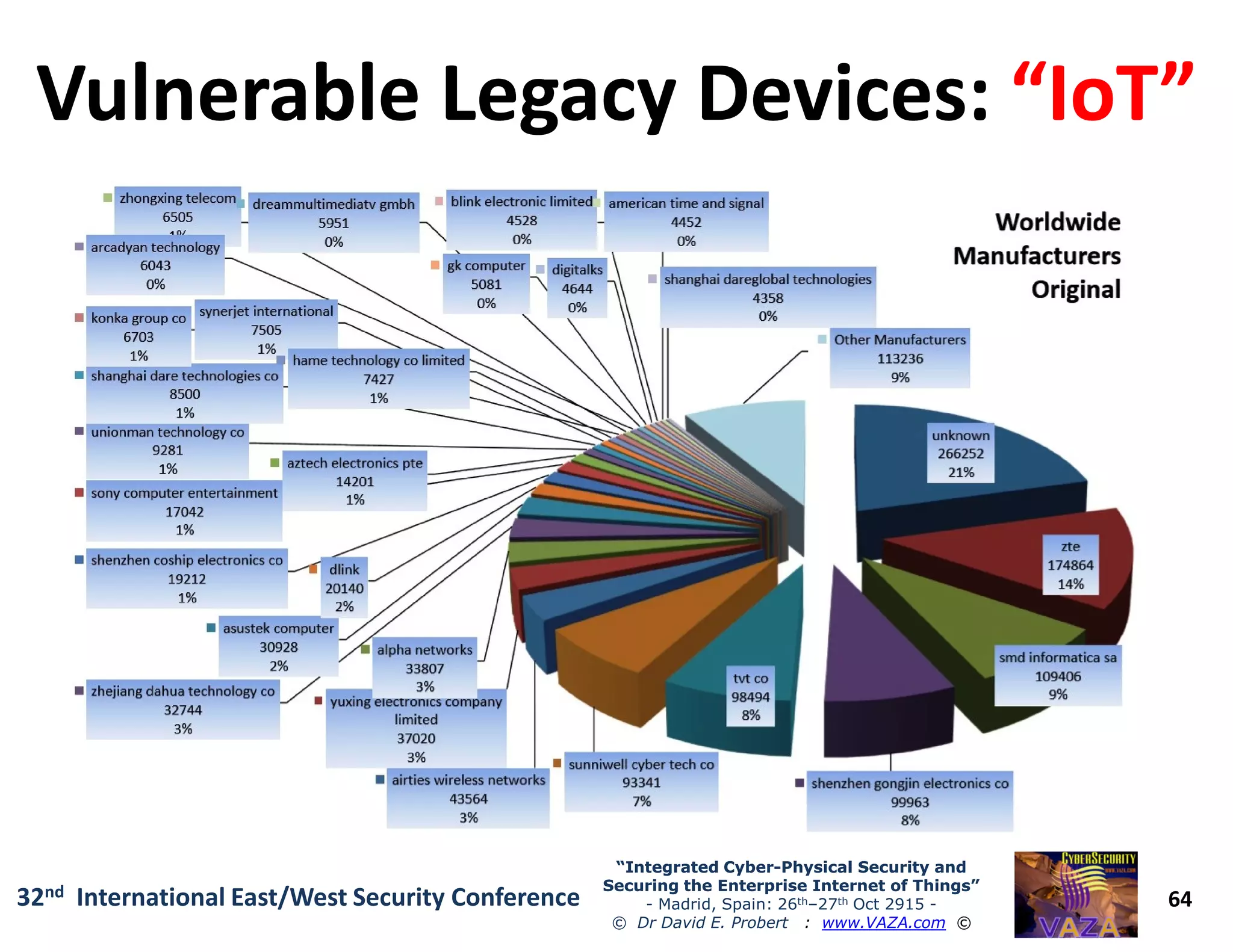
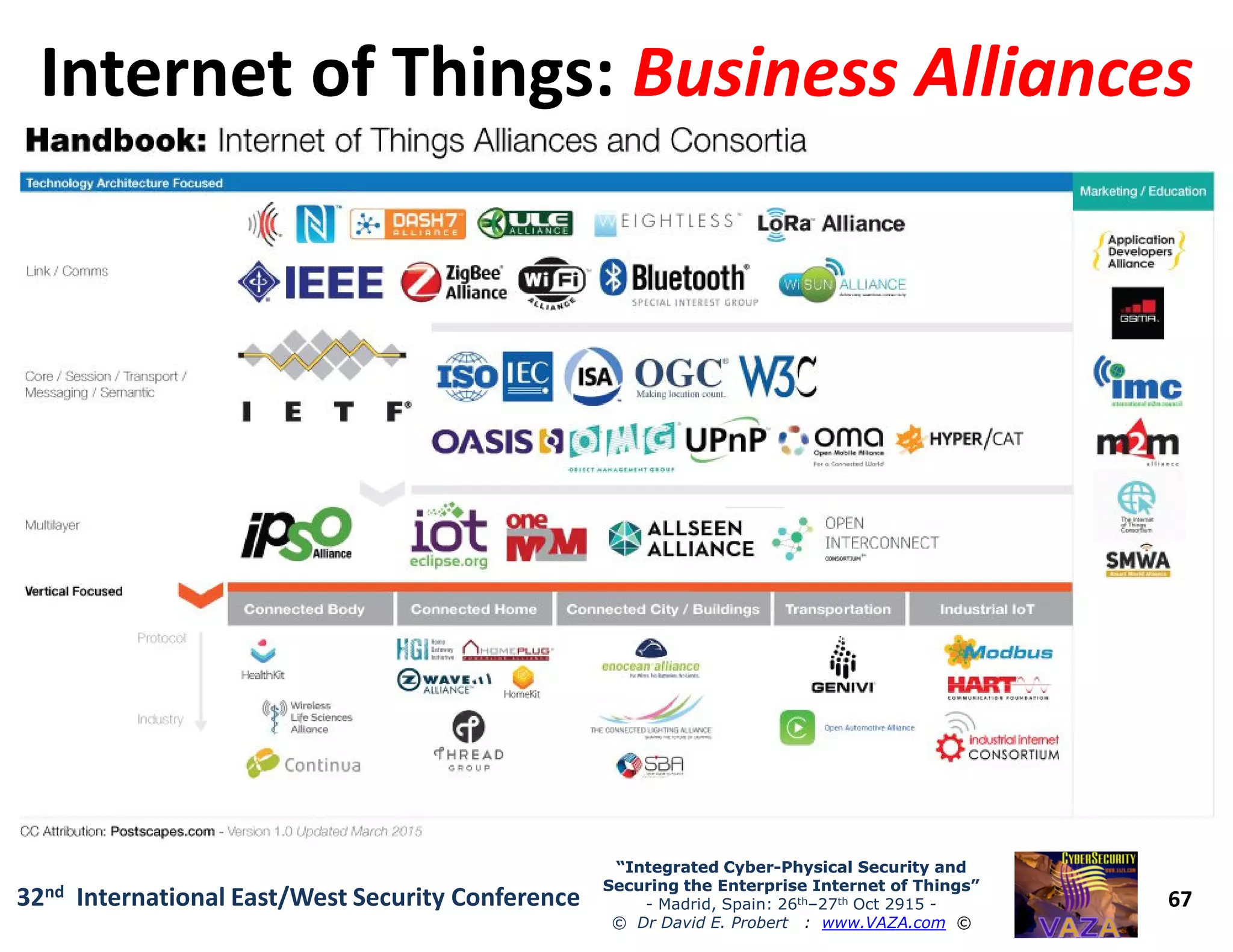
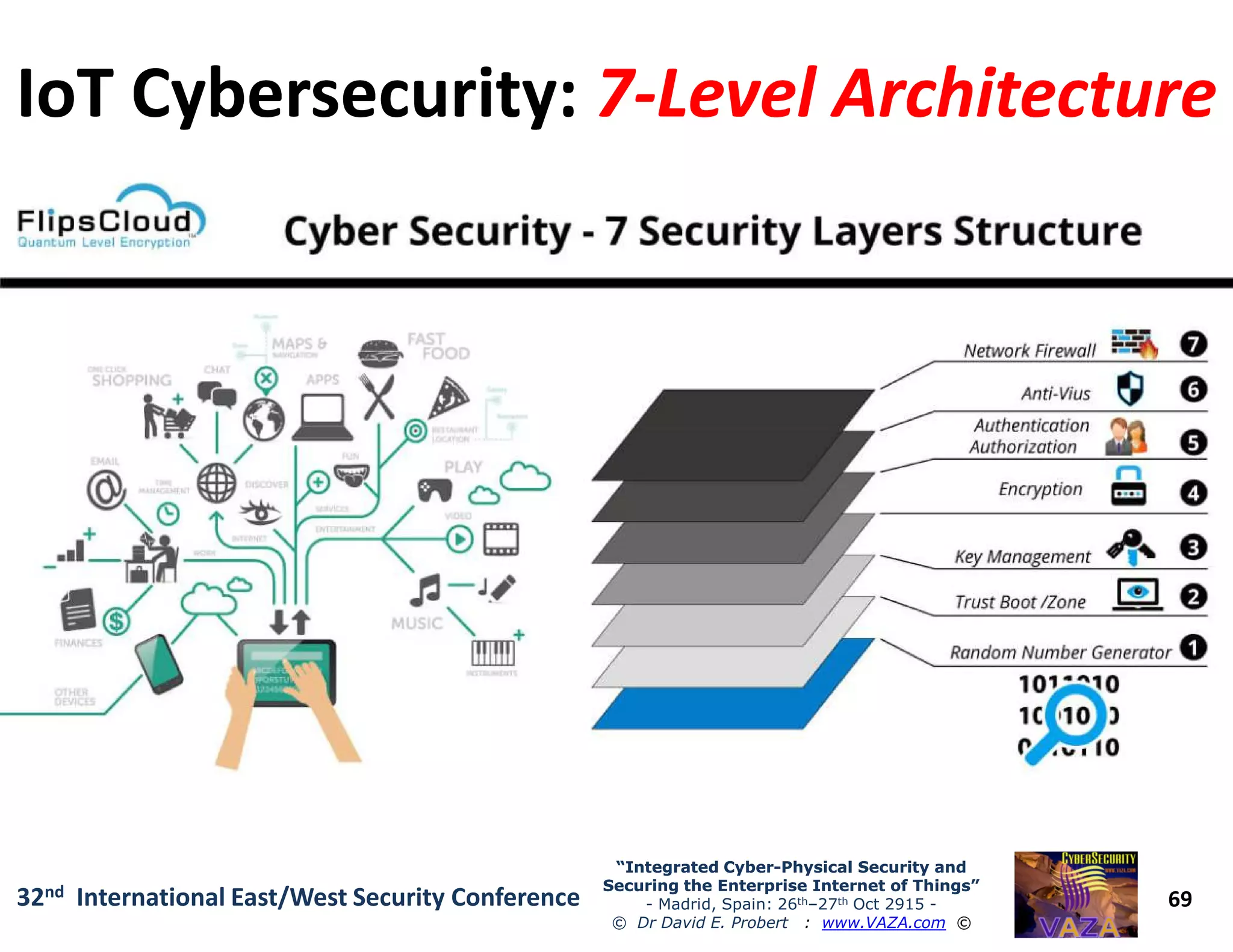
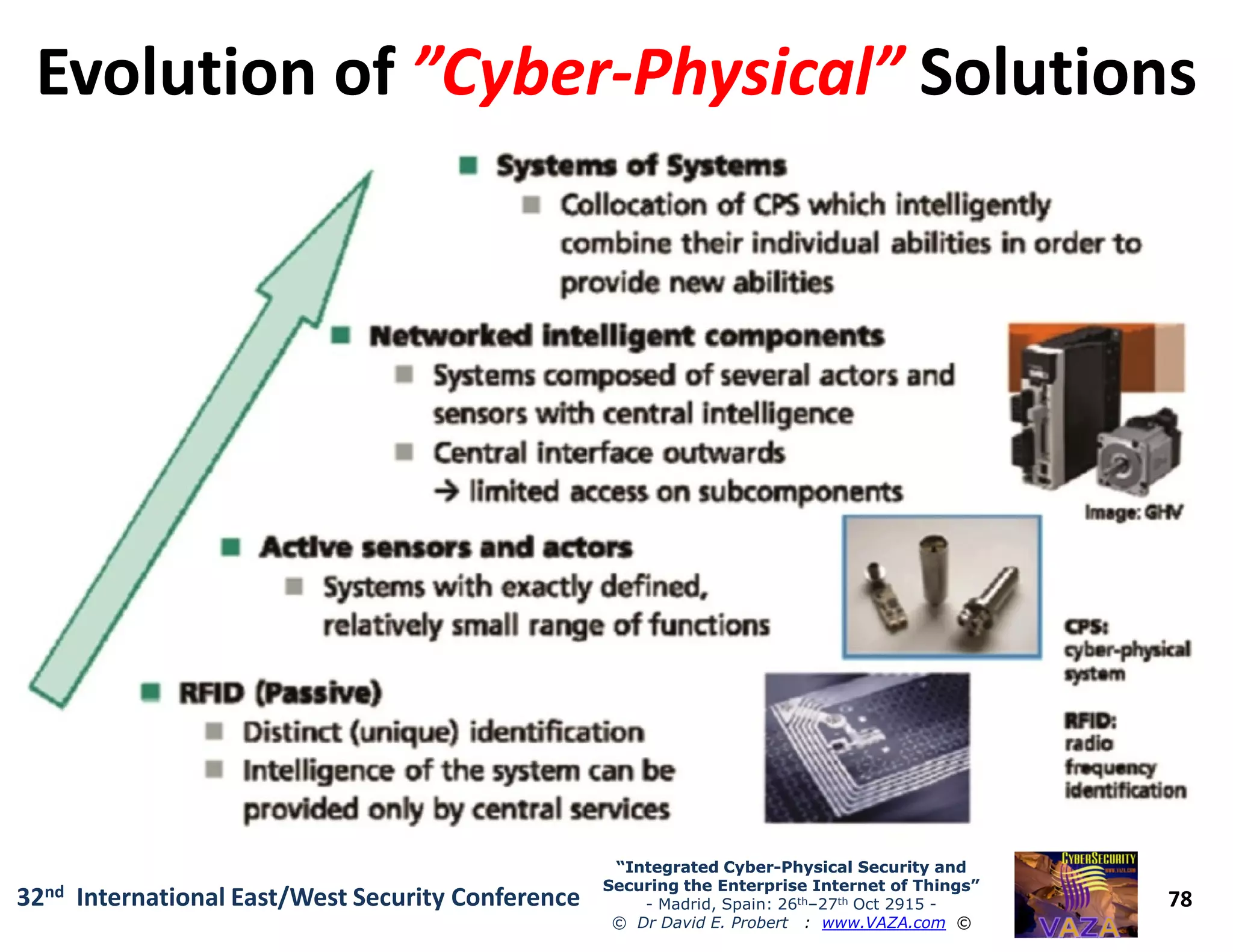
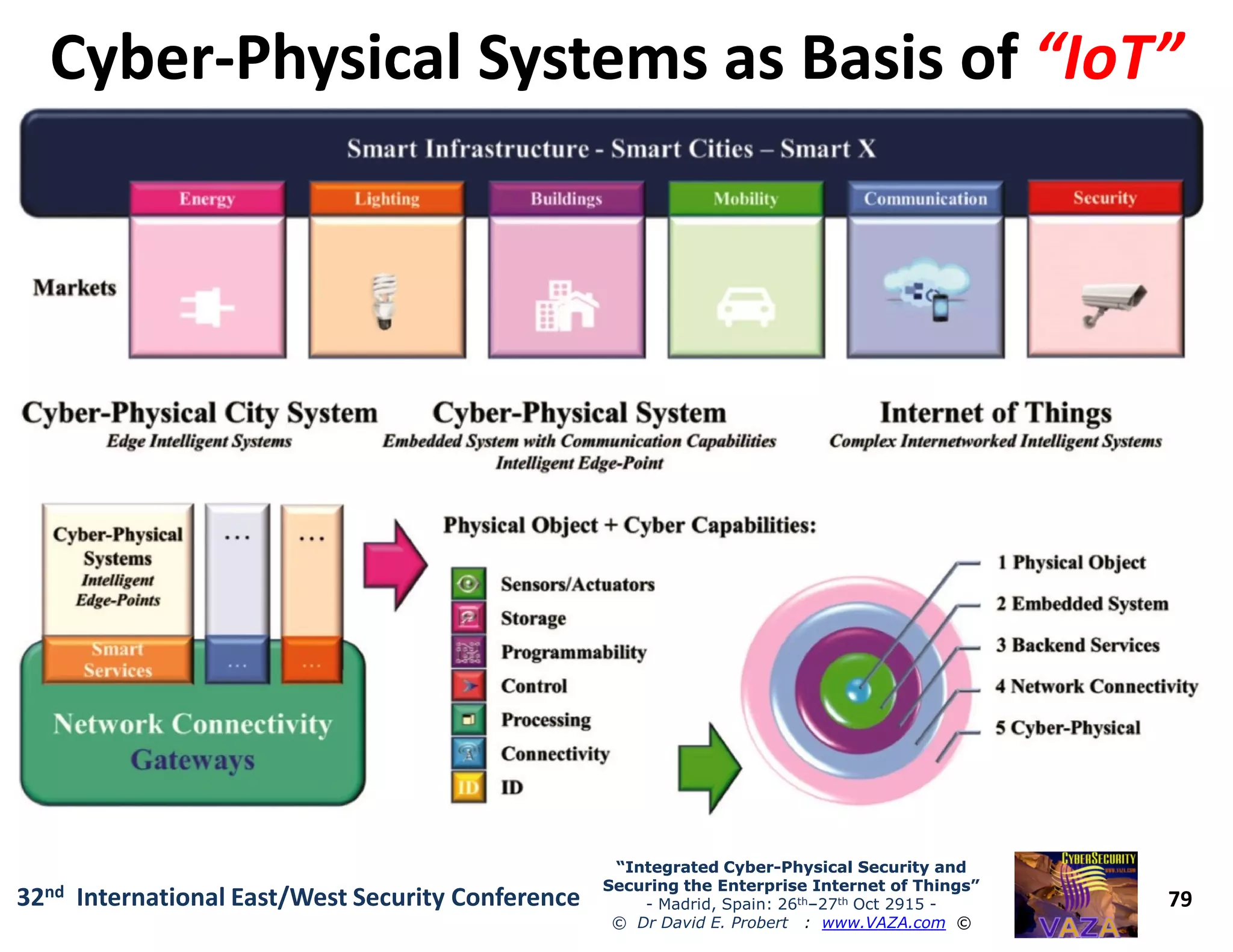
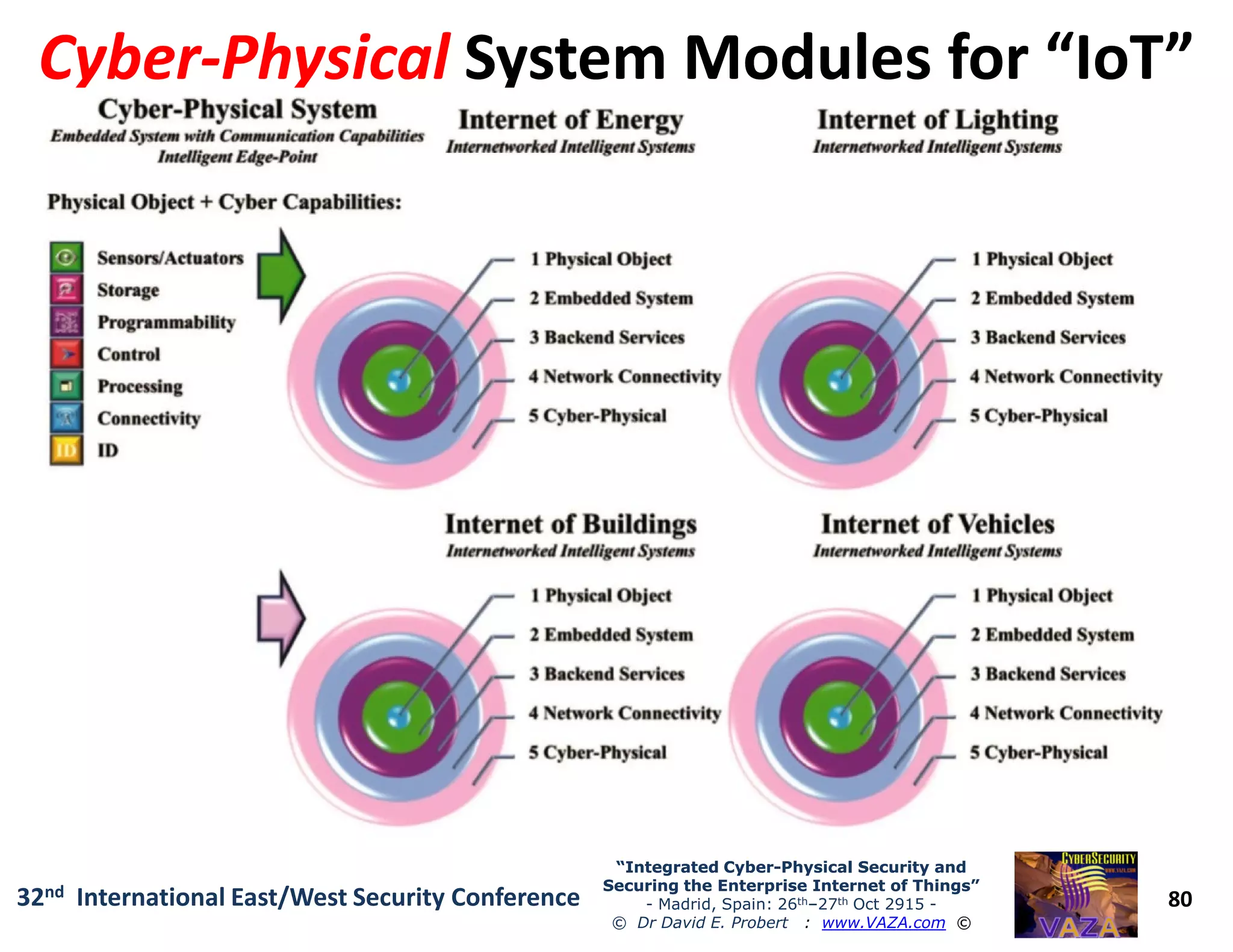
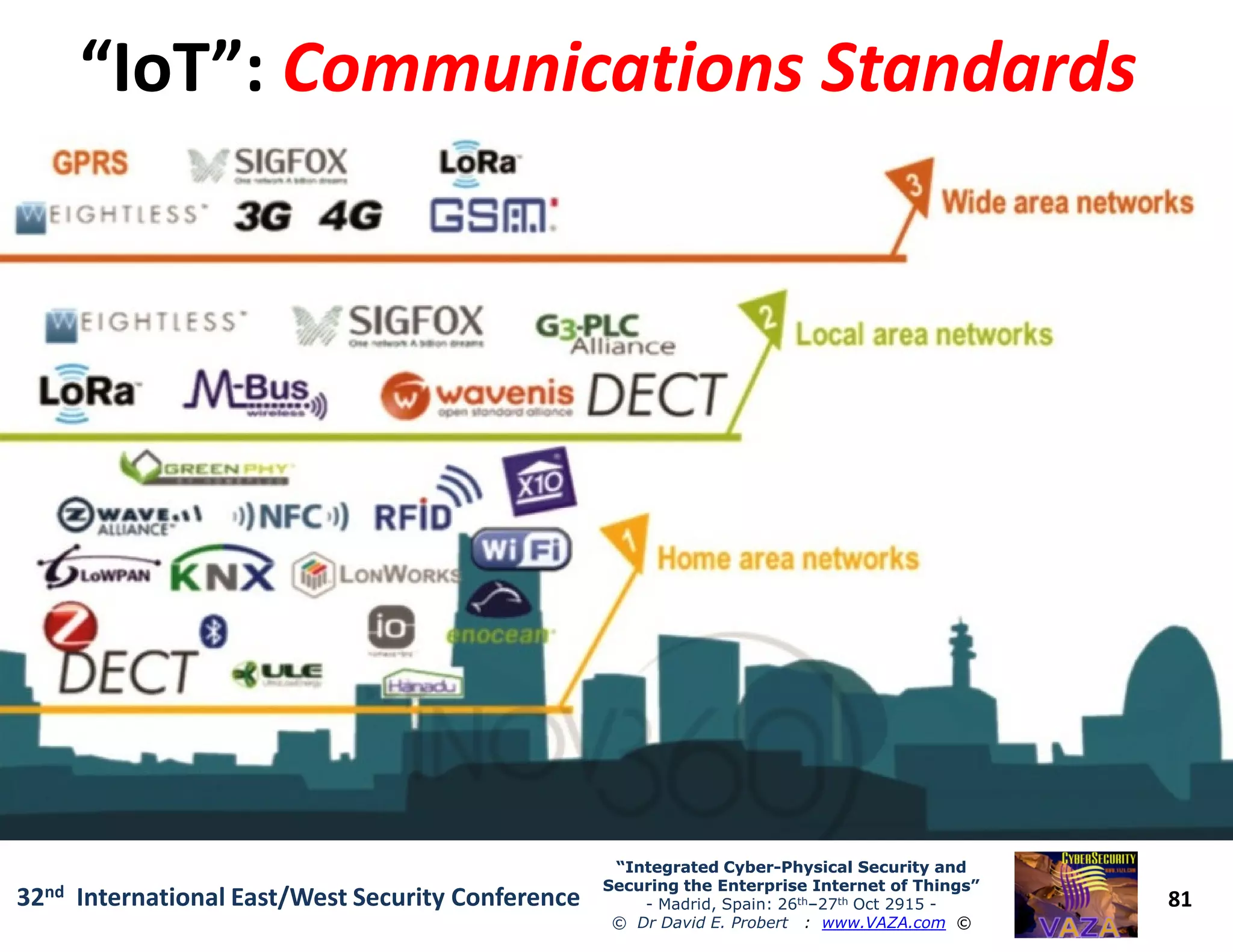
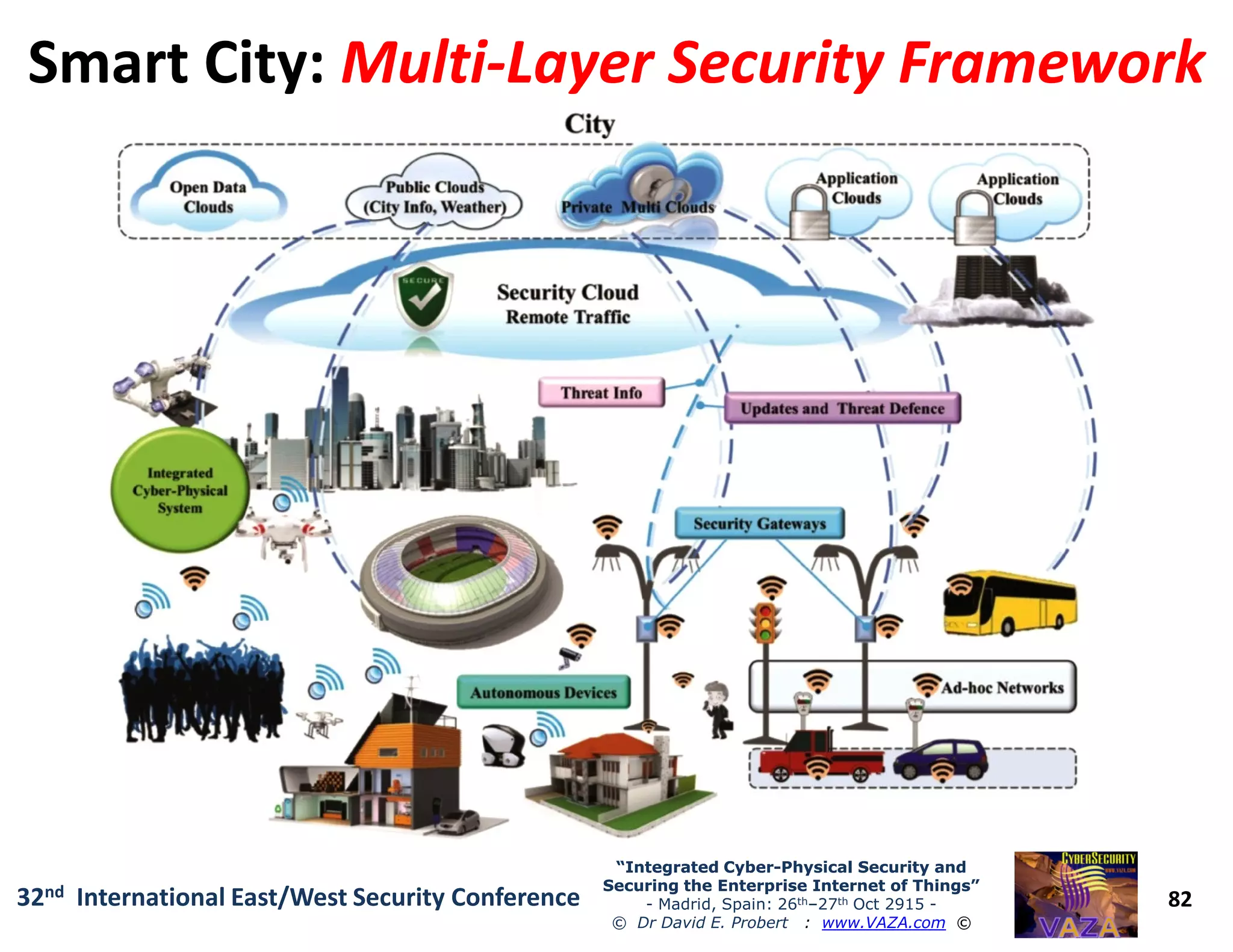
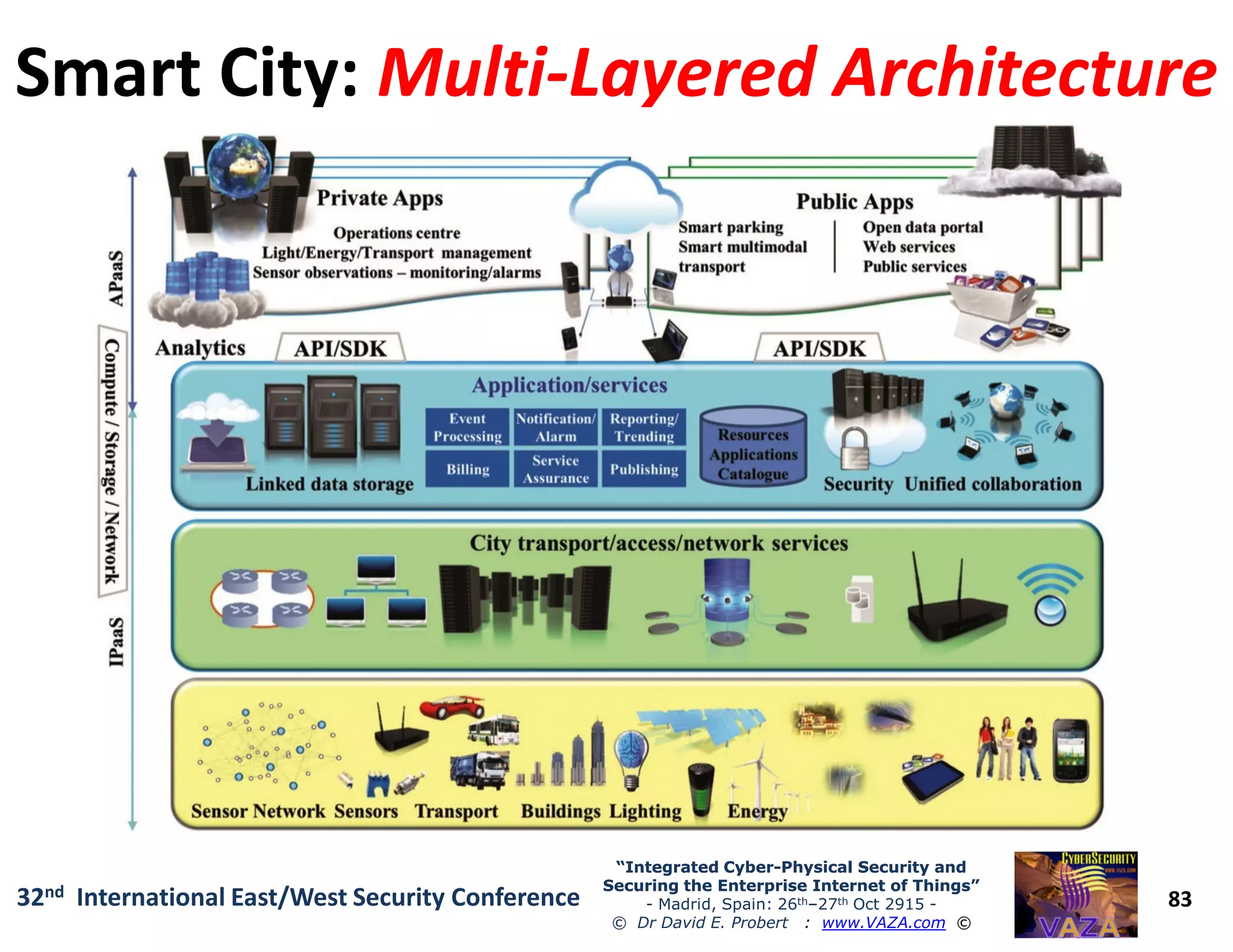
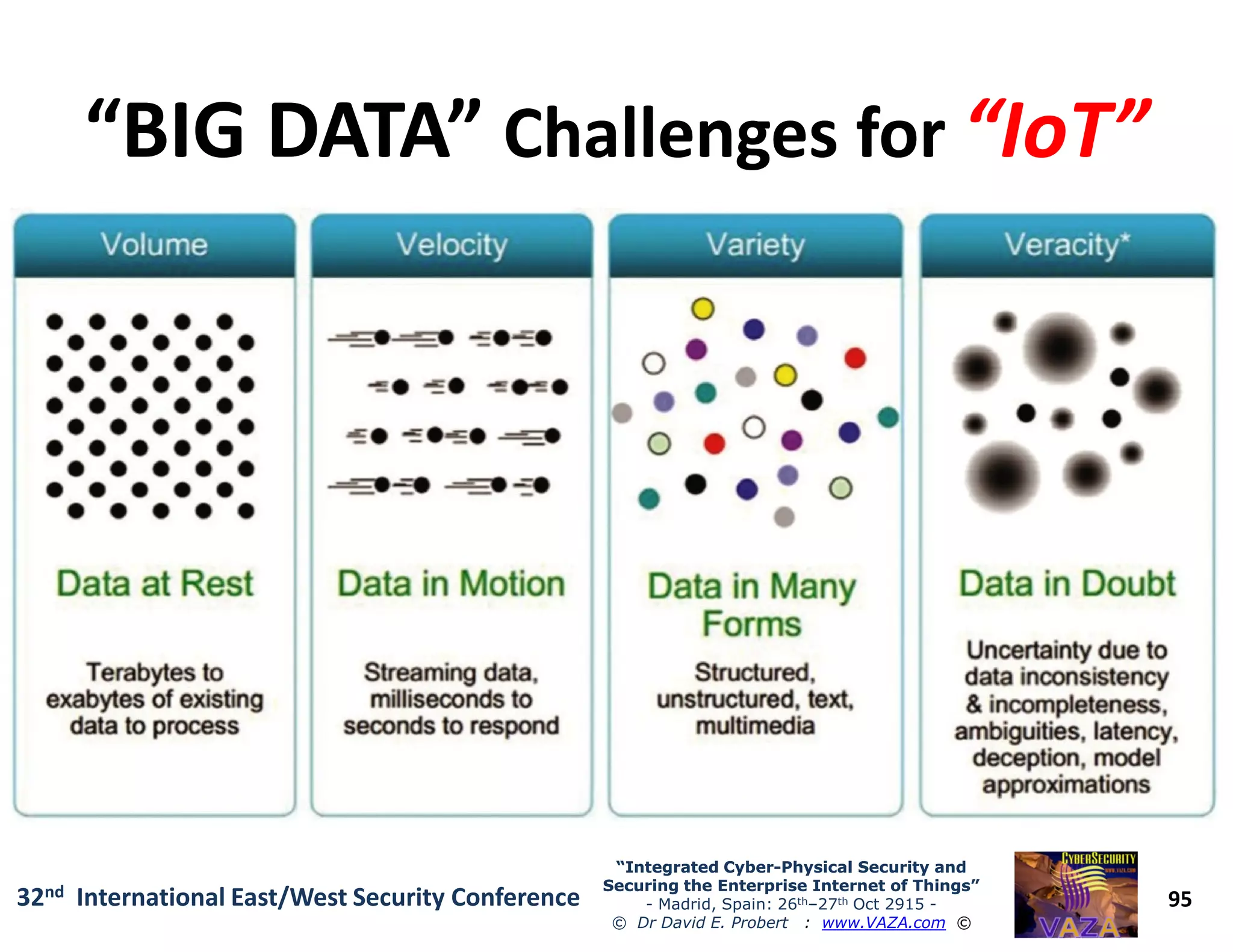
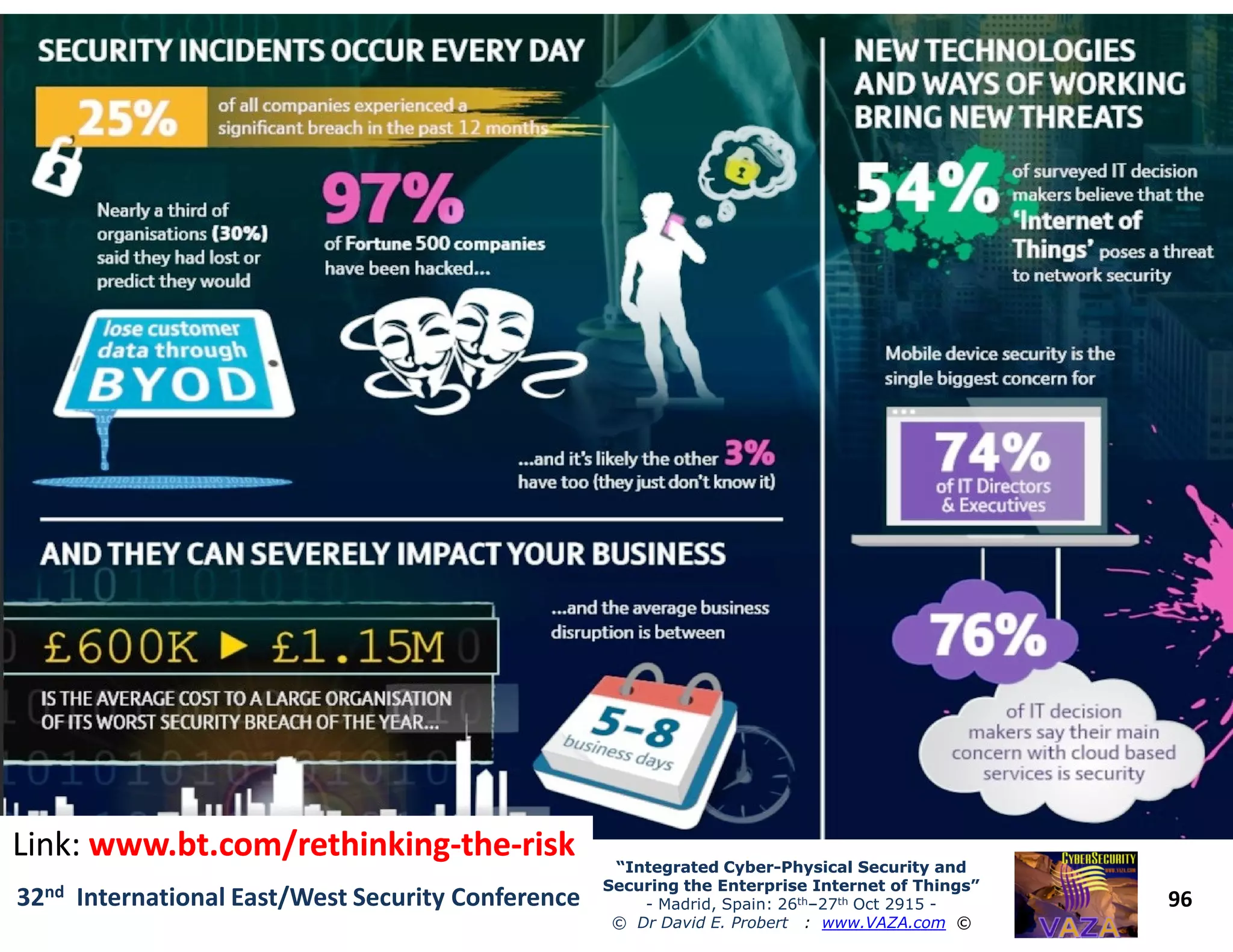
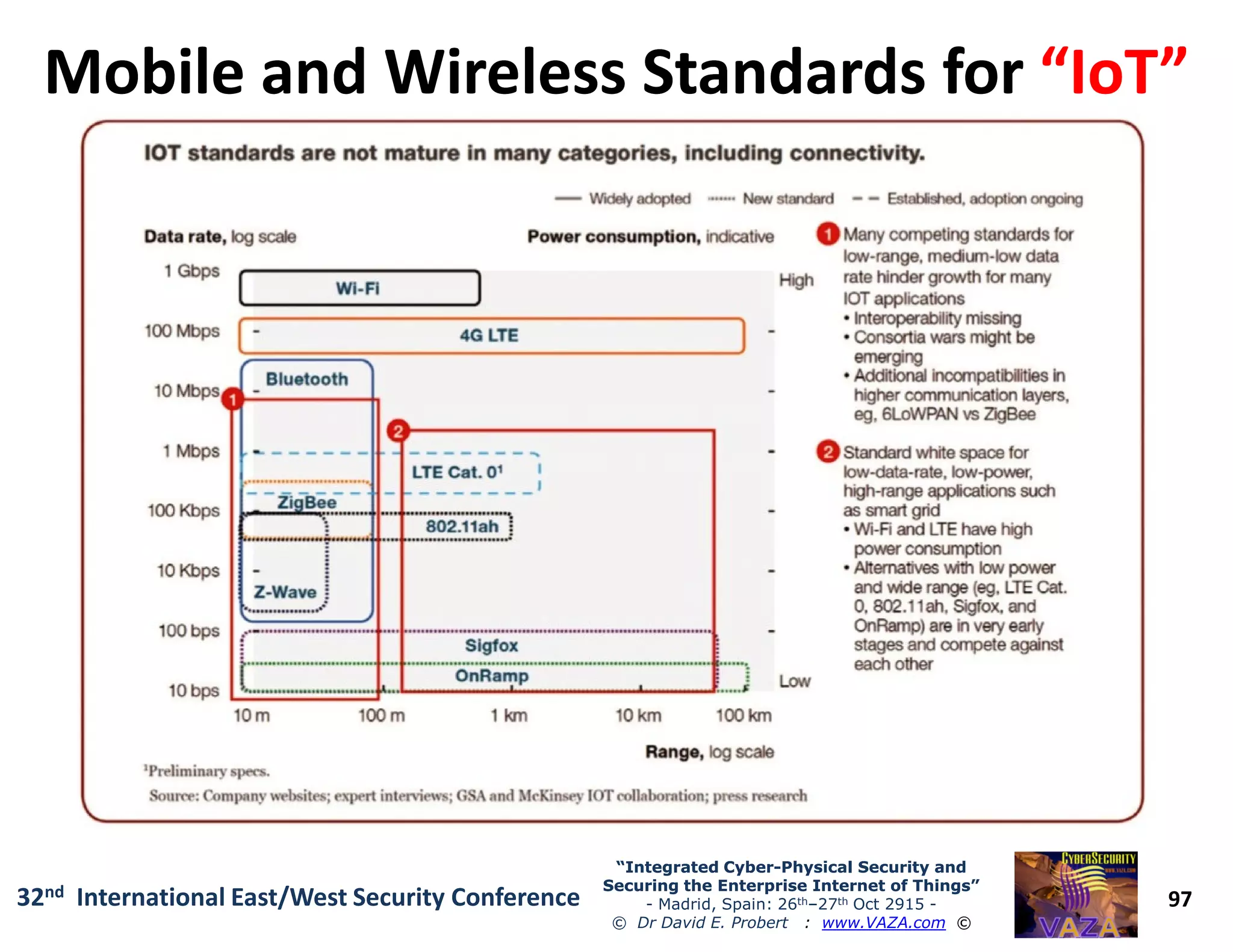
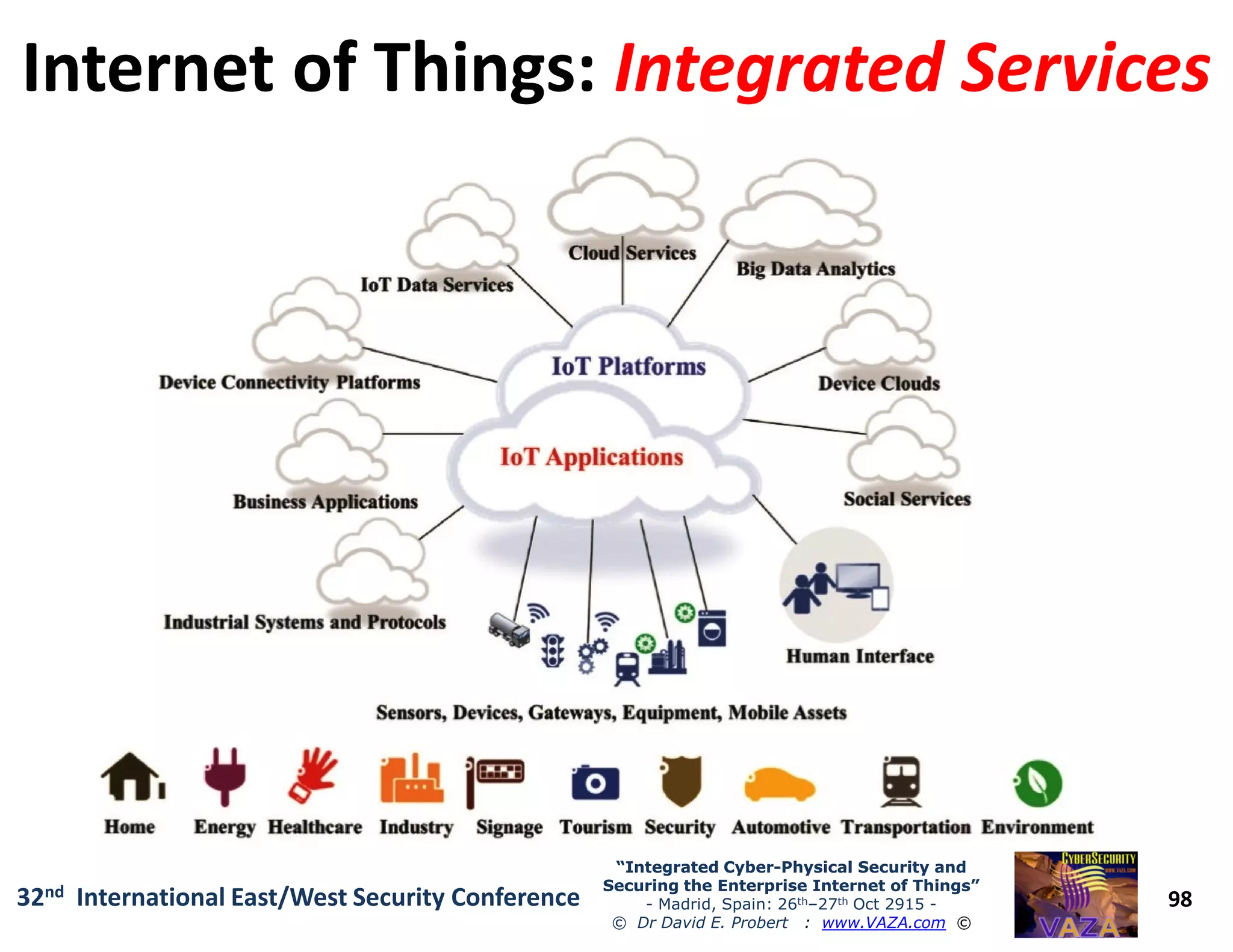
The document covers the 21st-century trends in cybersecurity, focusing on the integration of cyber and physical security to safeguard the Internet of Things (IoT). It highlights emerging threats, such as cybercrime and cyberterrorism, along with the necessity for companies to adapt their security frameworks to include AI and machine learning for proactive defense. It emphasizes the critical need for a cohesive approach to security management at the board level to combat the evolving cyber threat landscape.