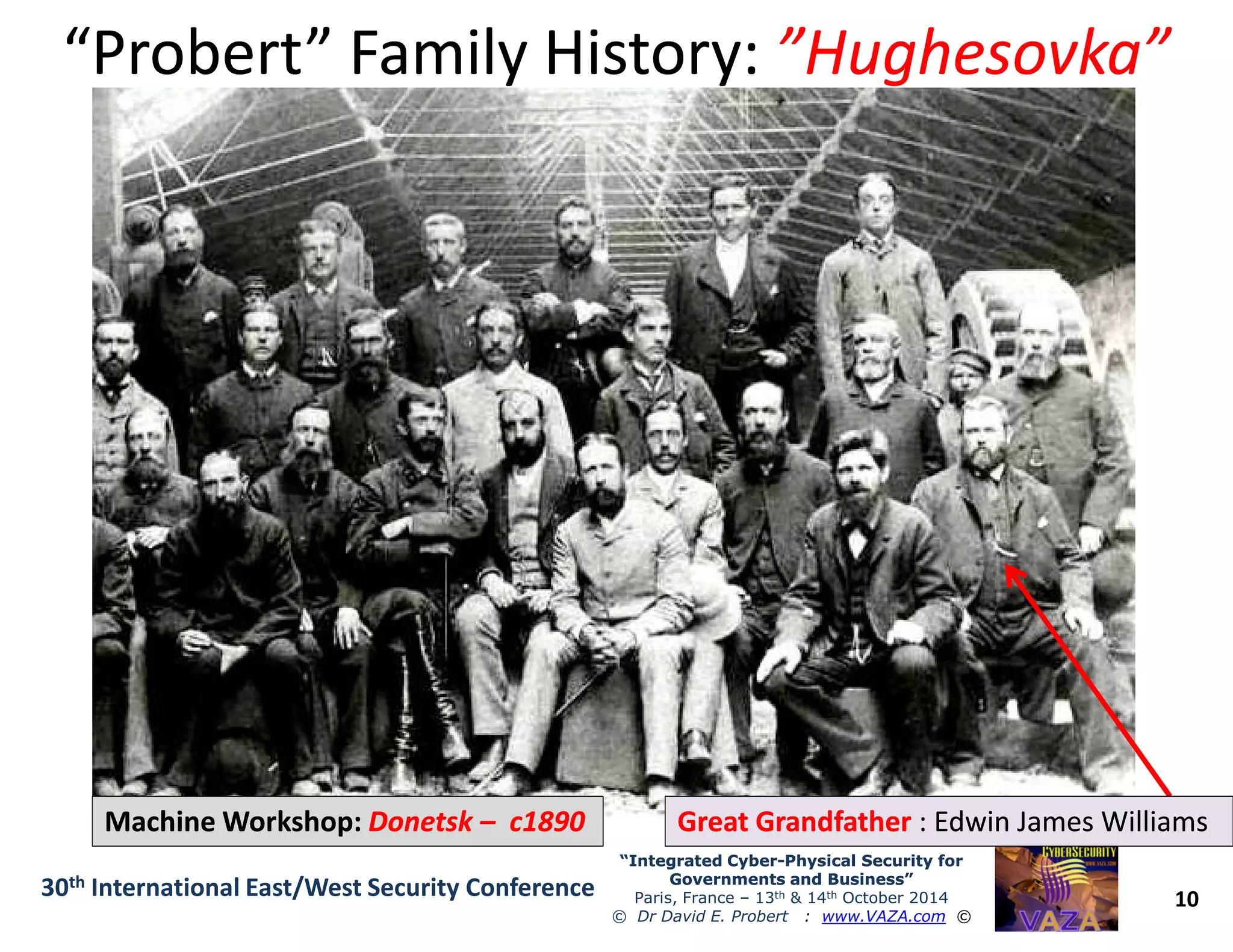
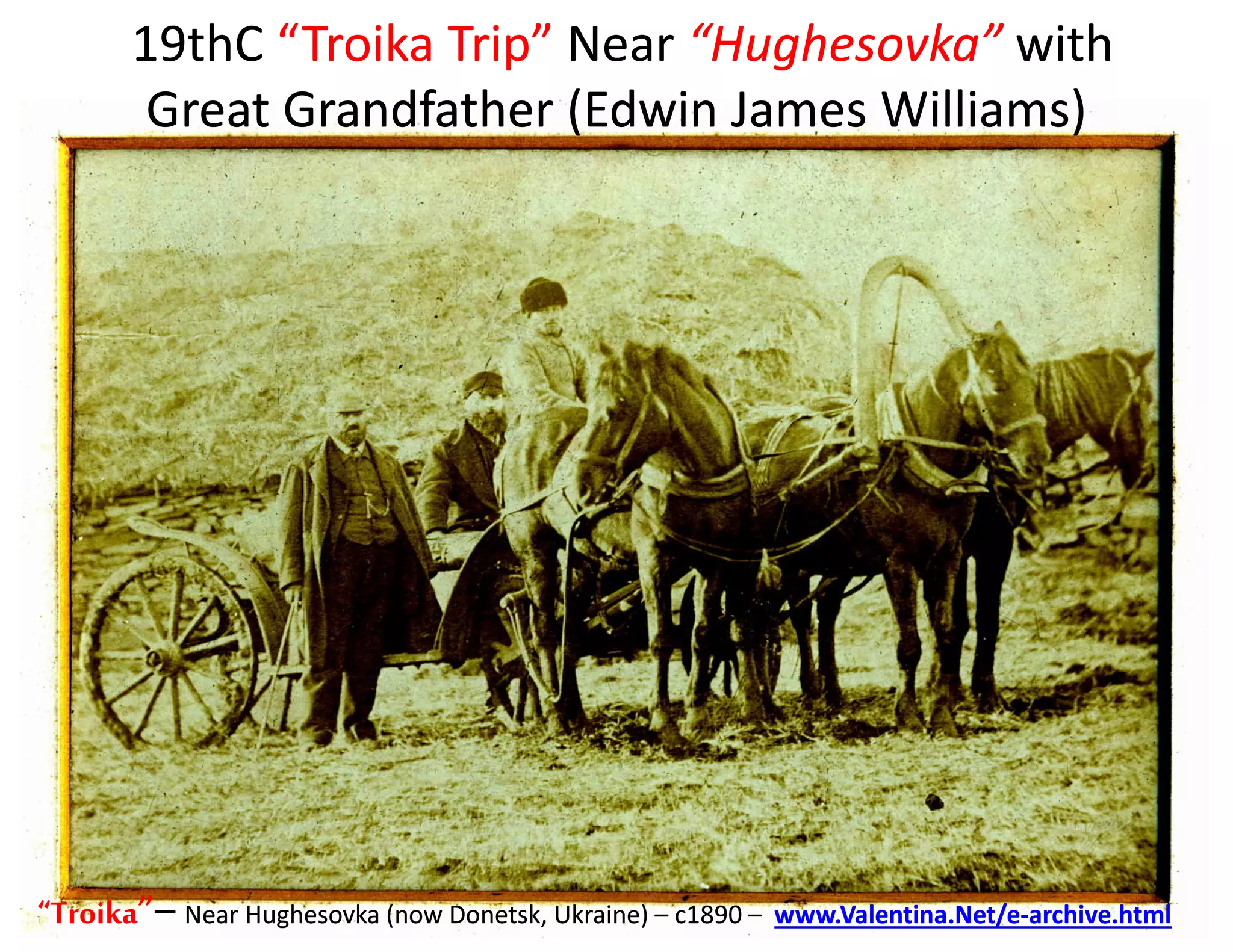
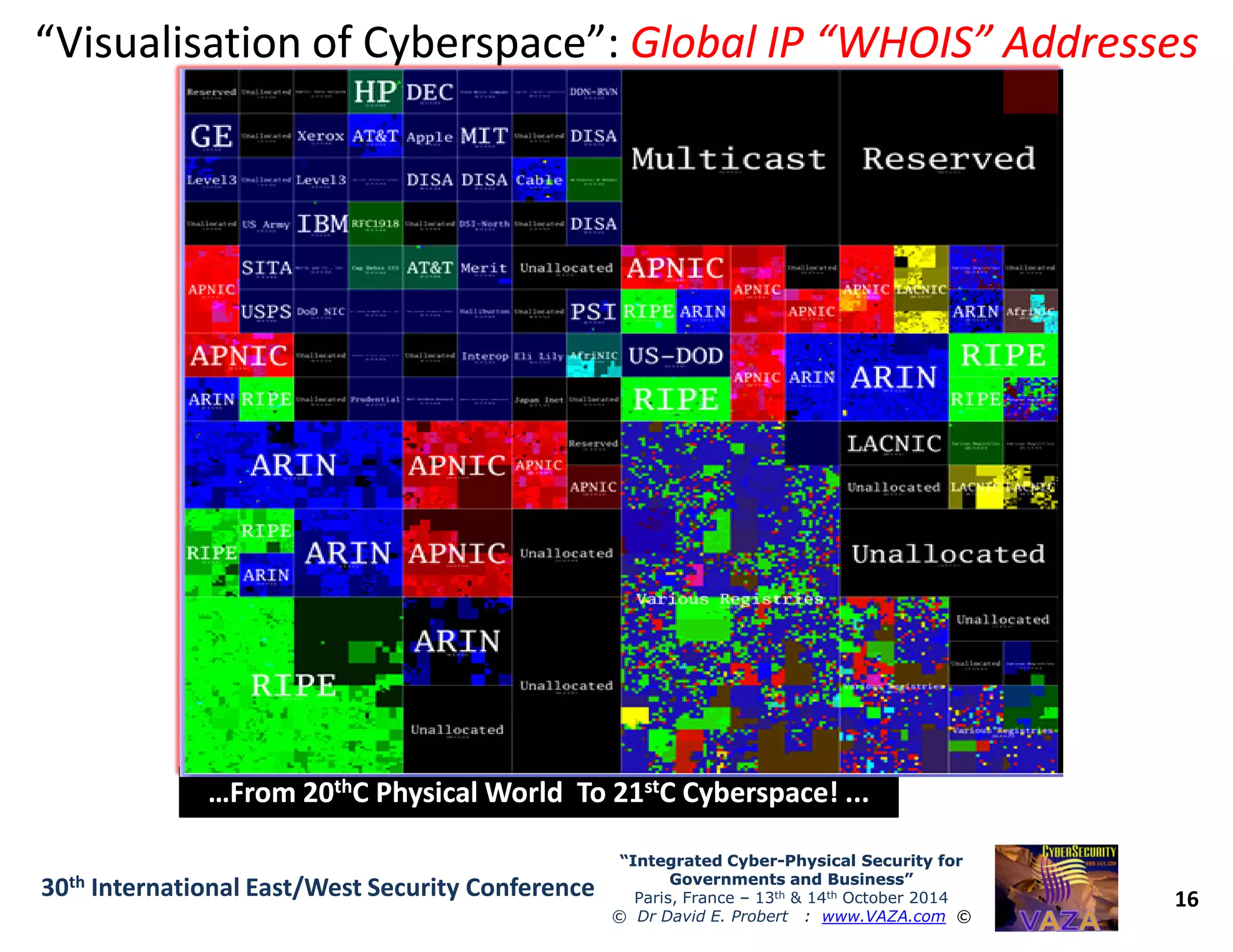
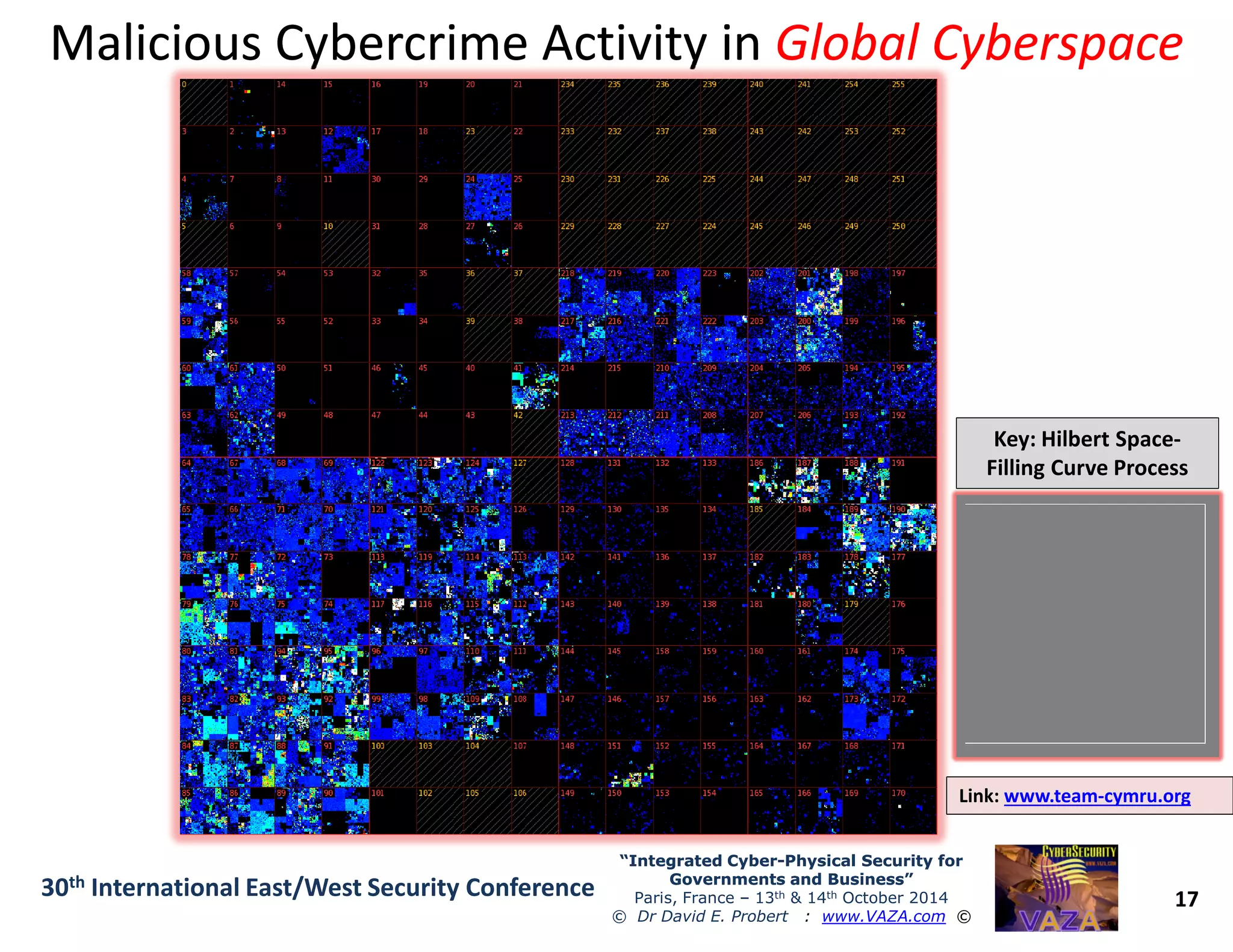
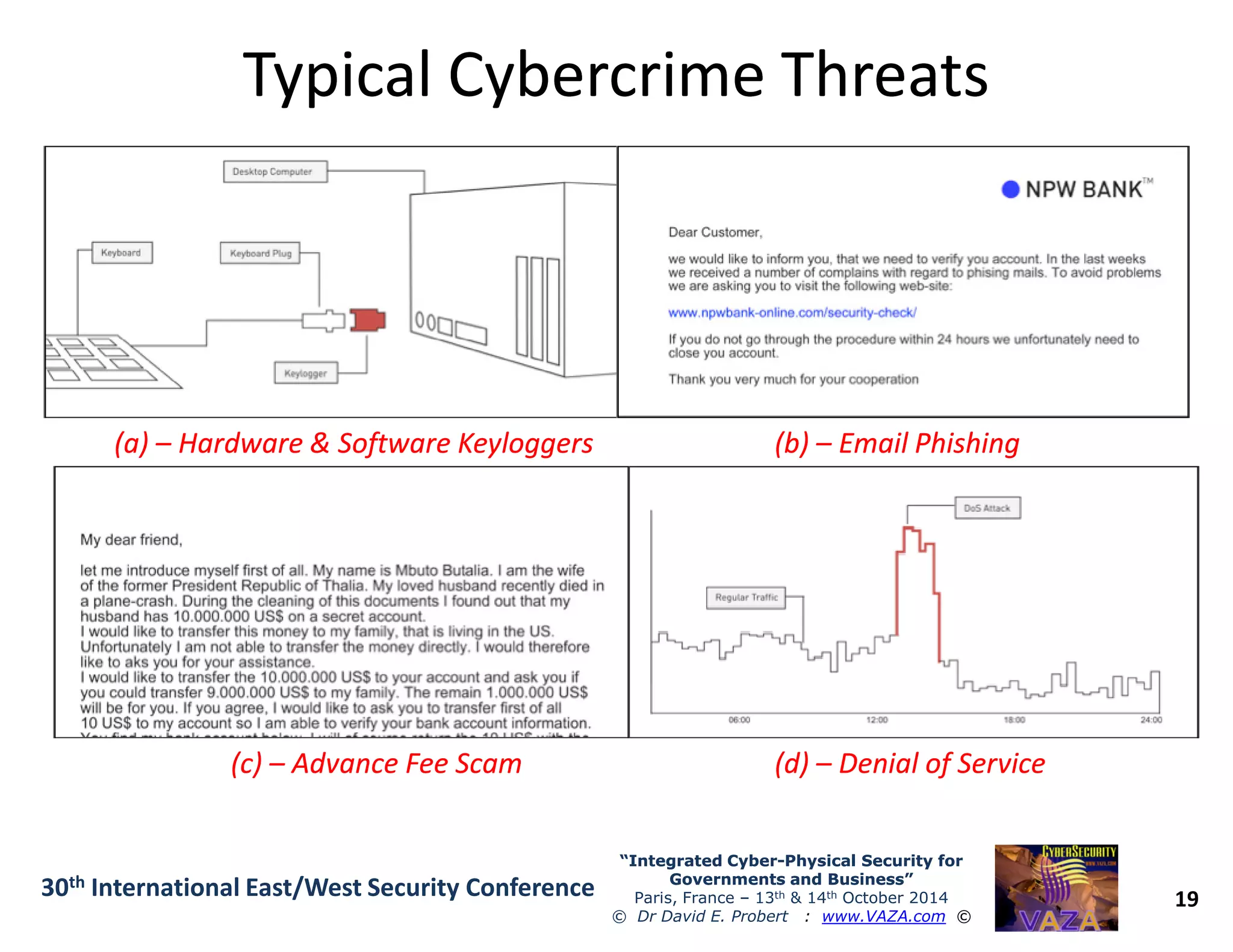
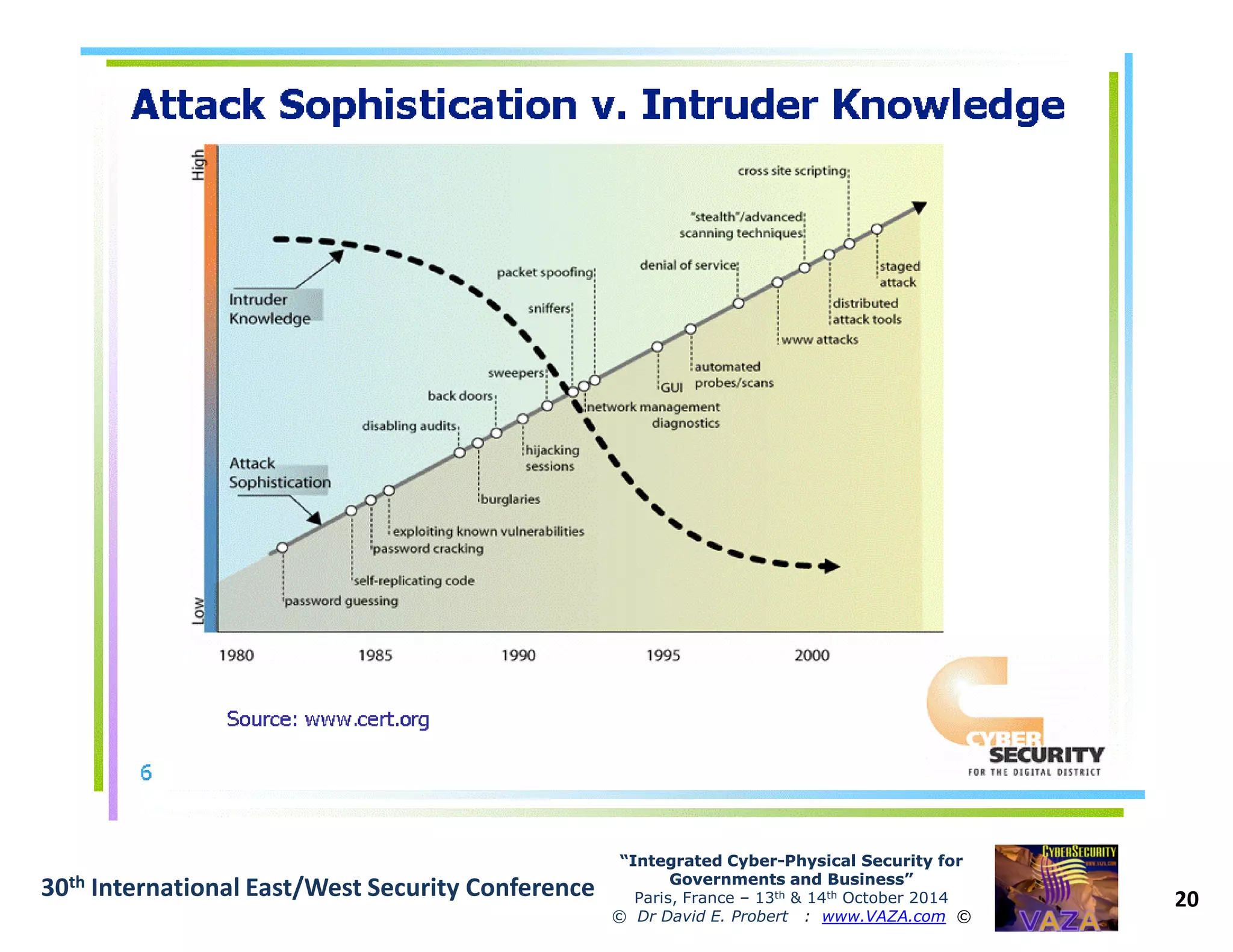
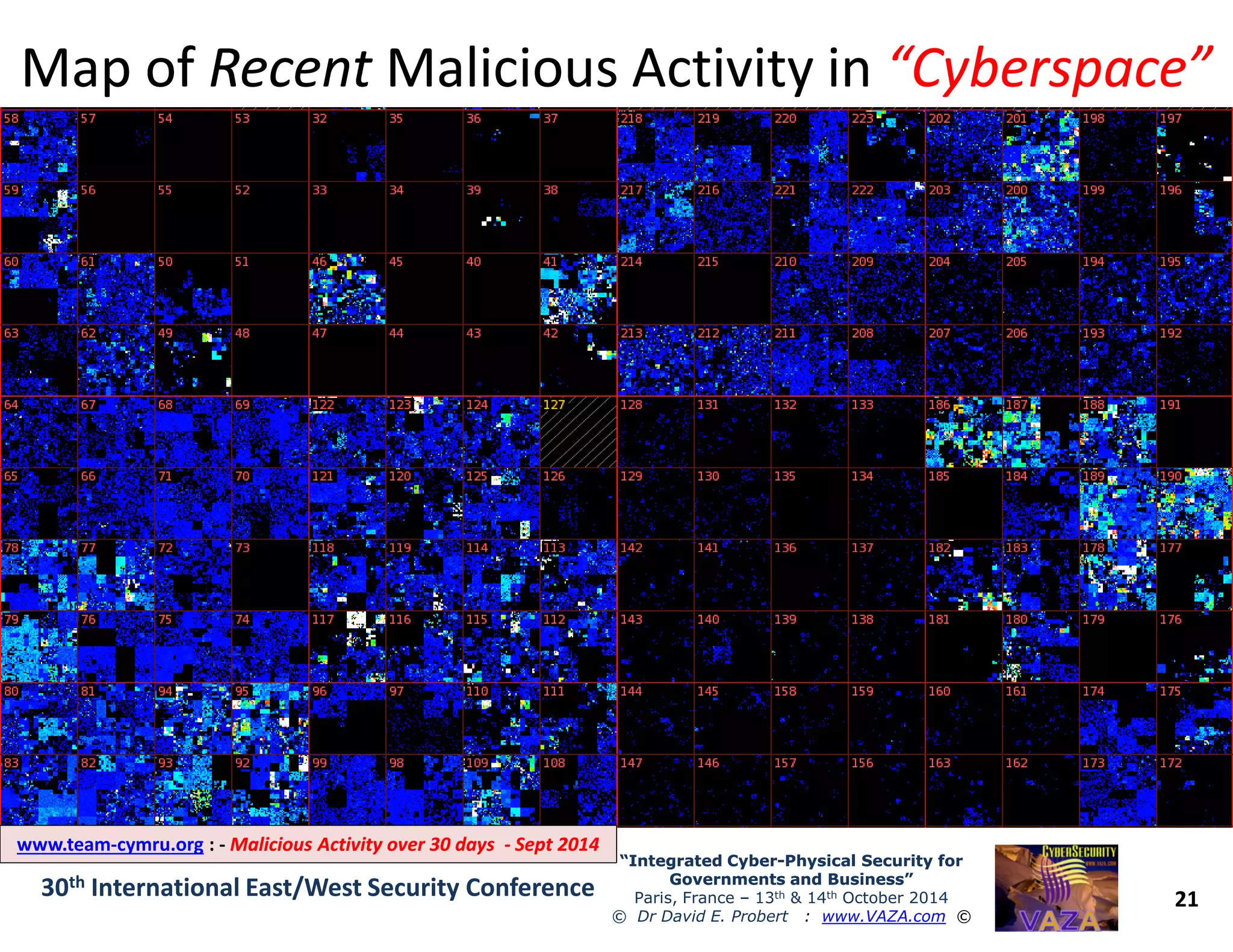
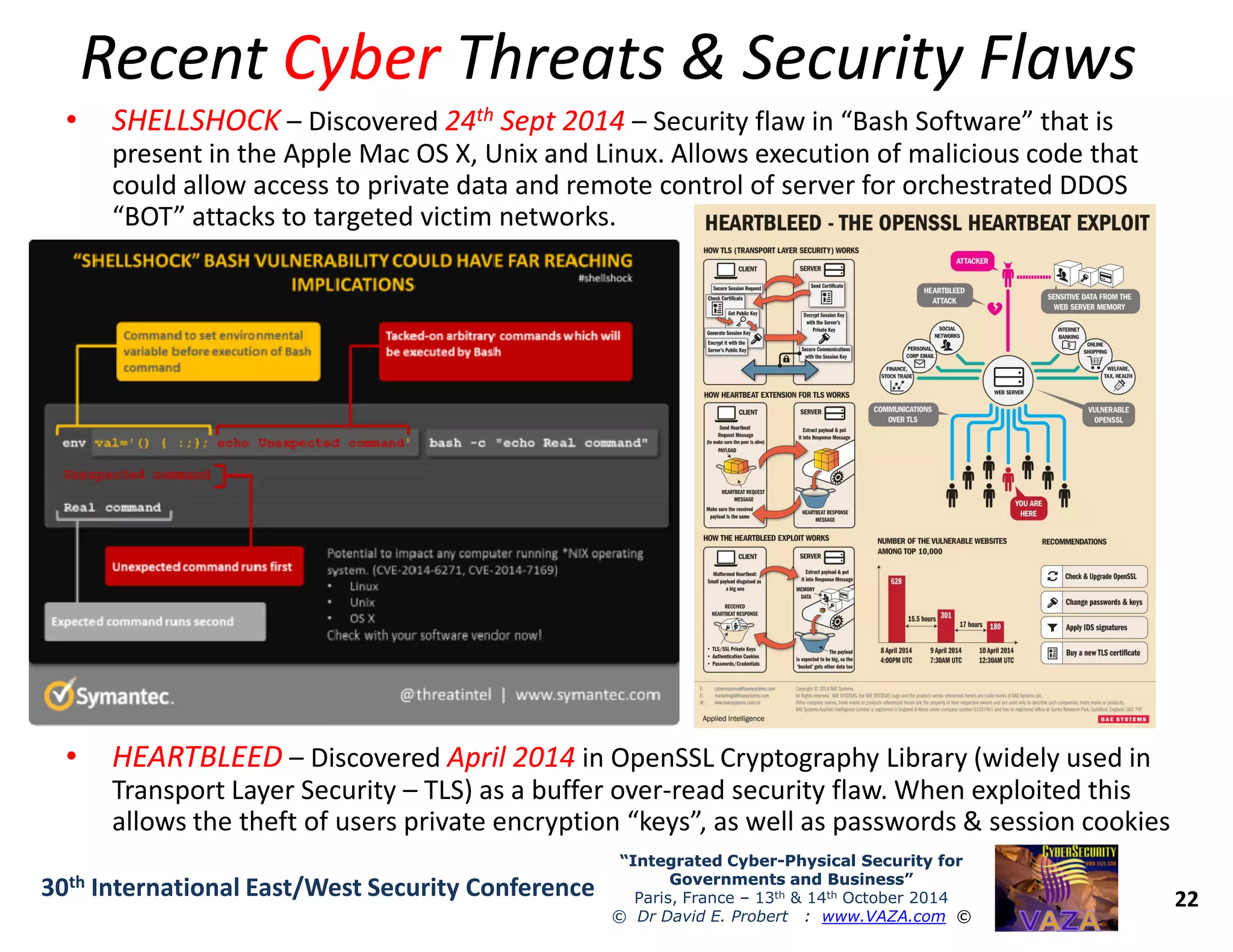
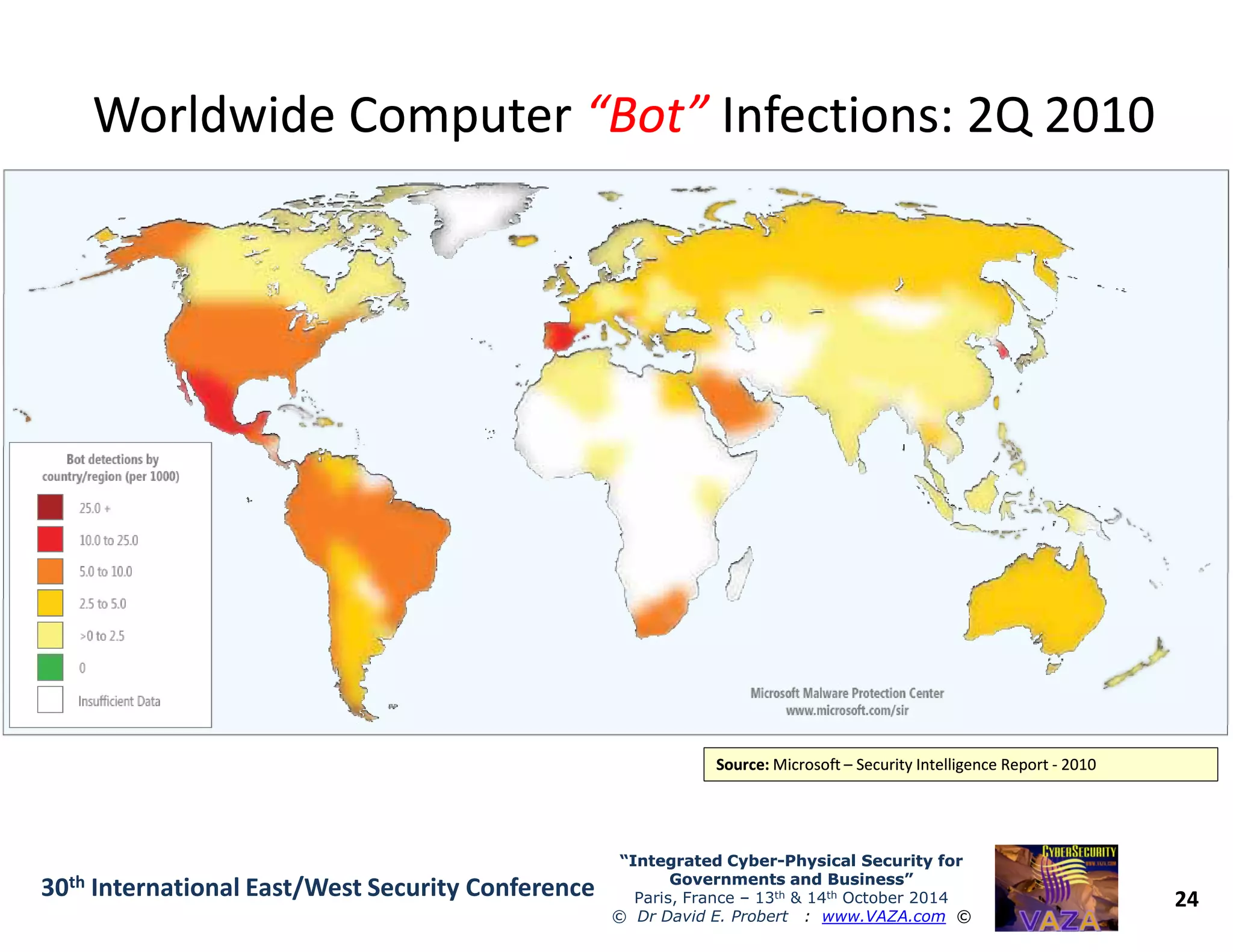
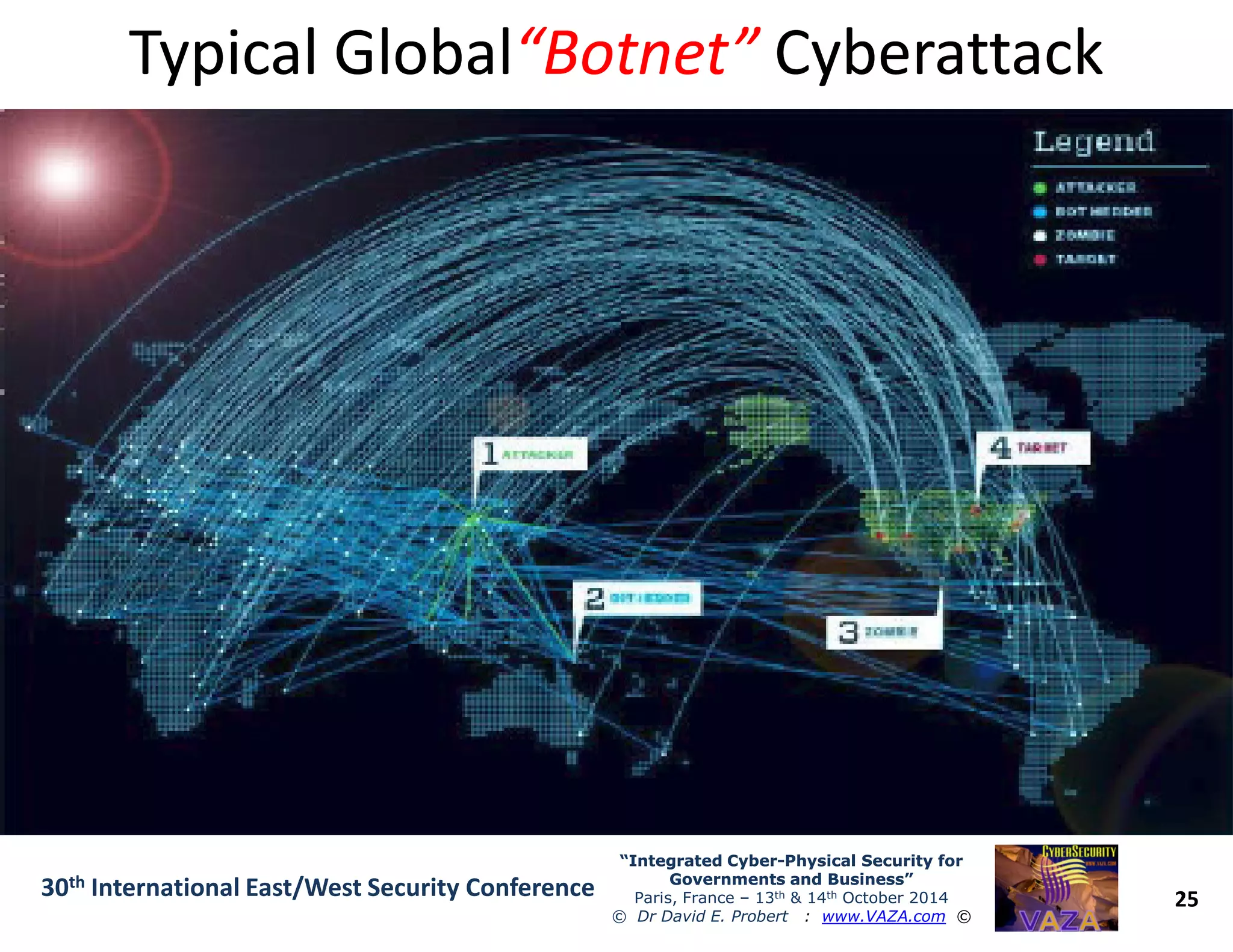
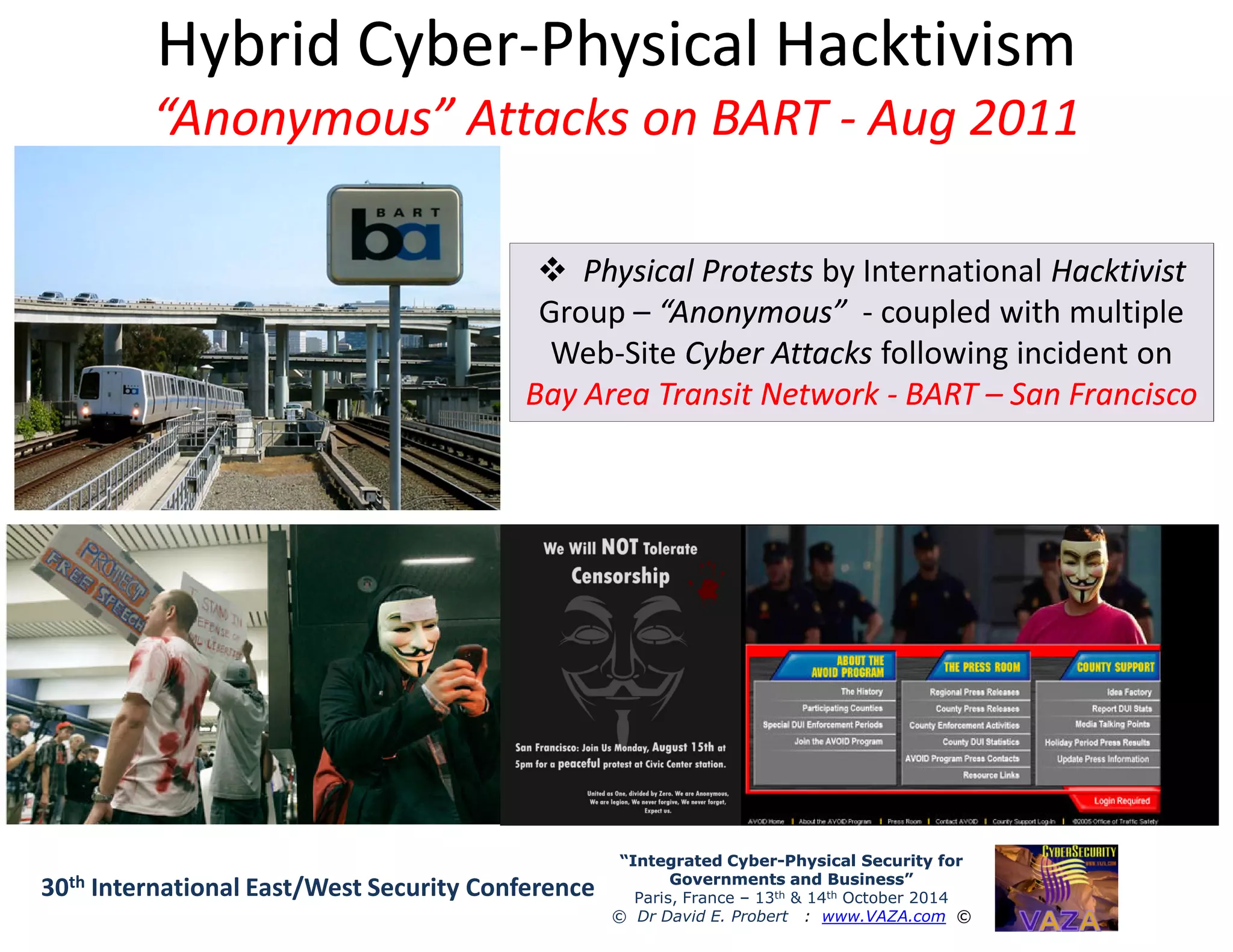
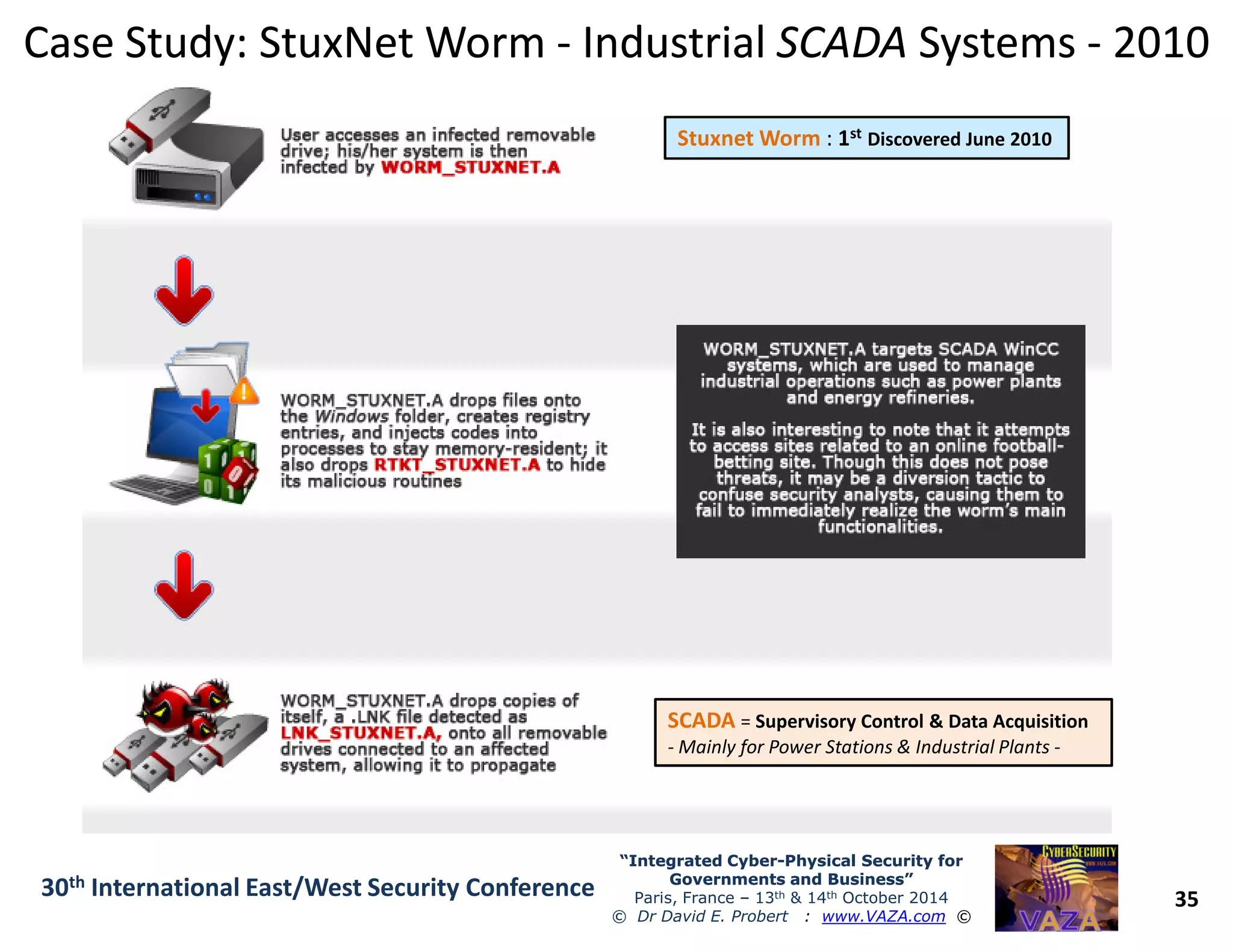
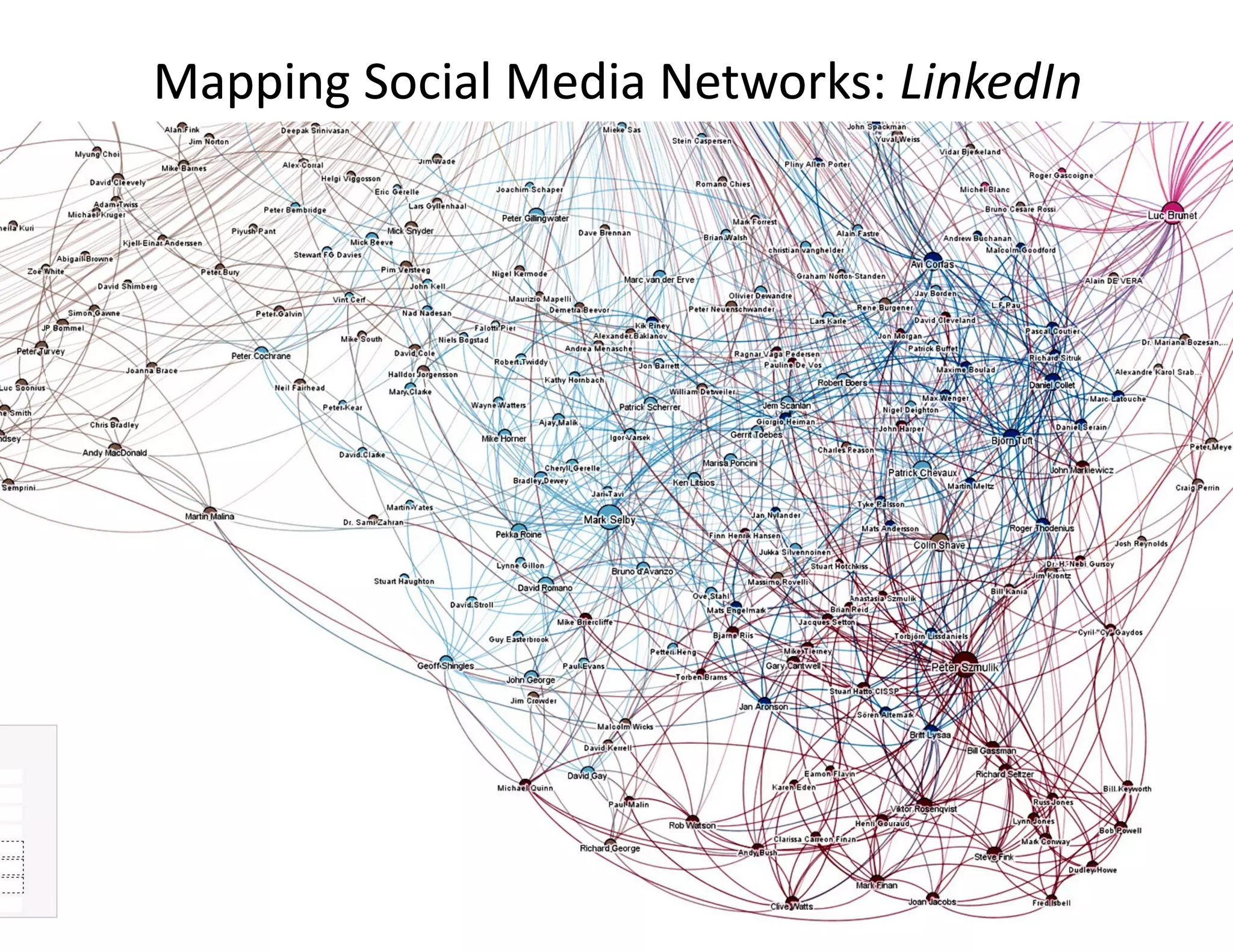
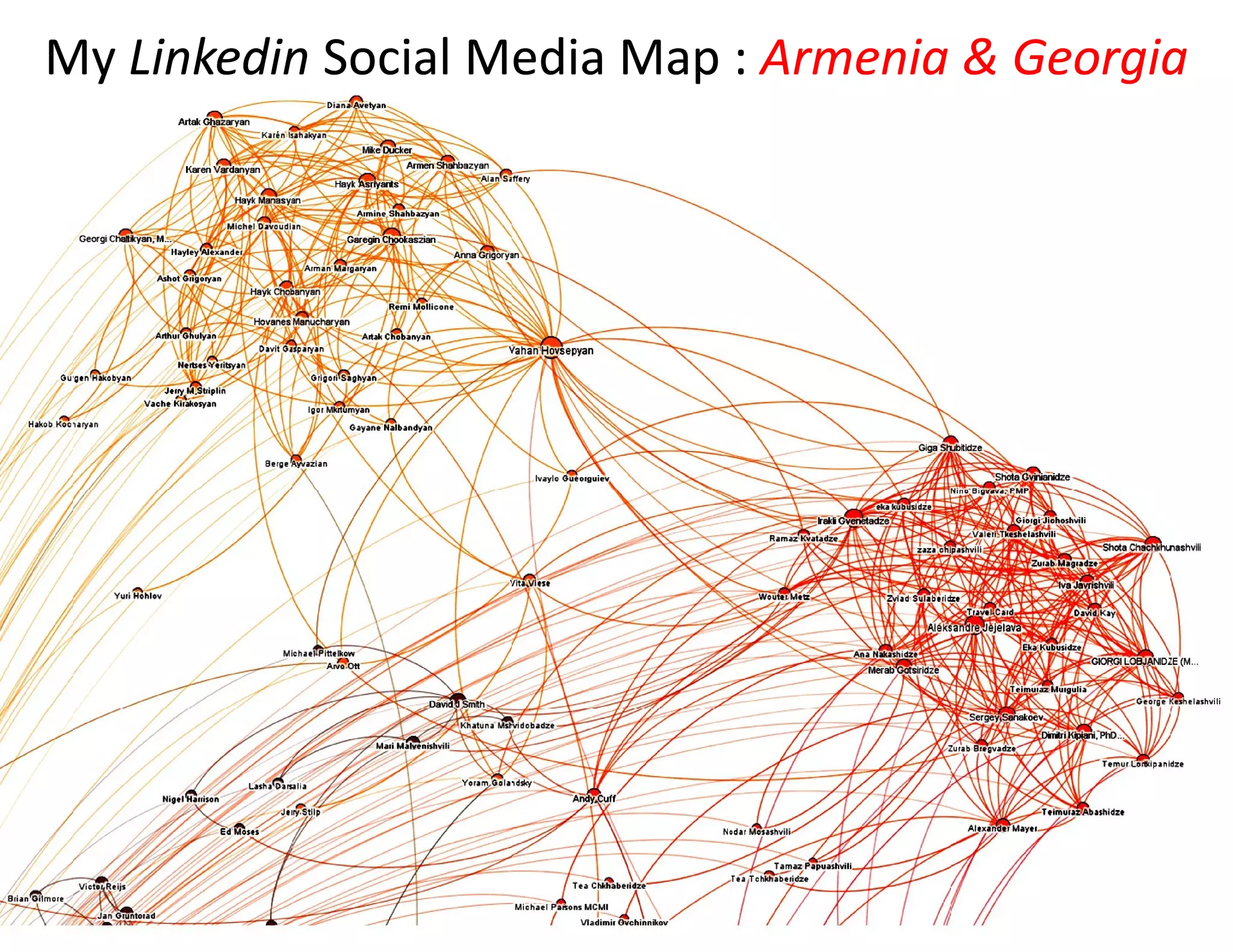
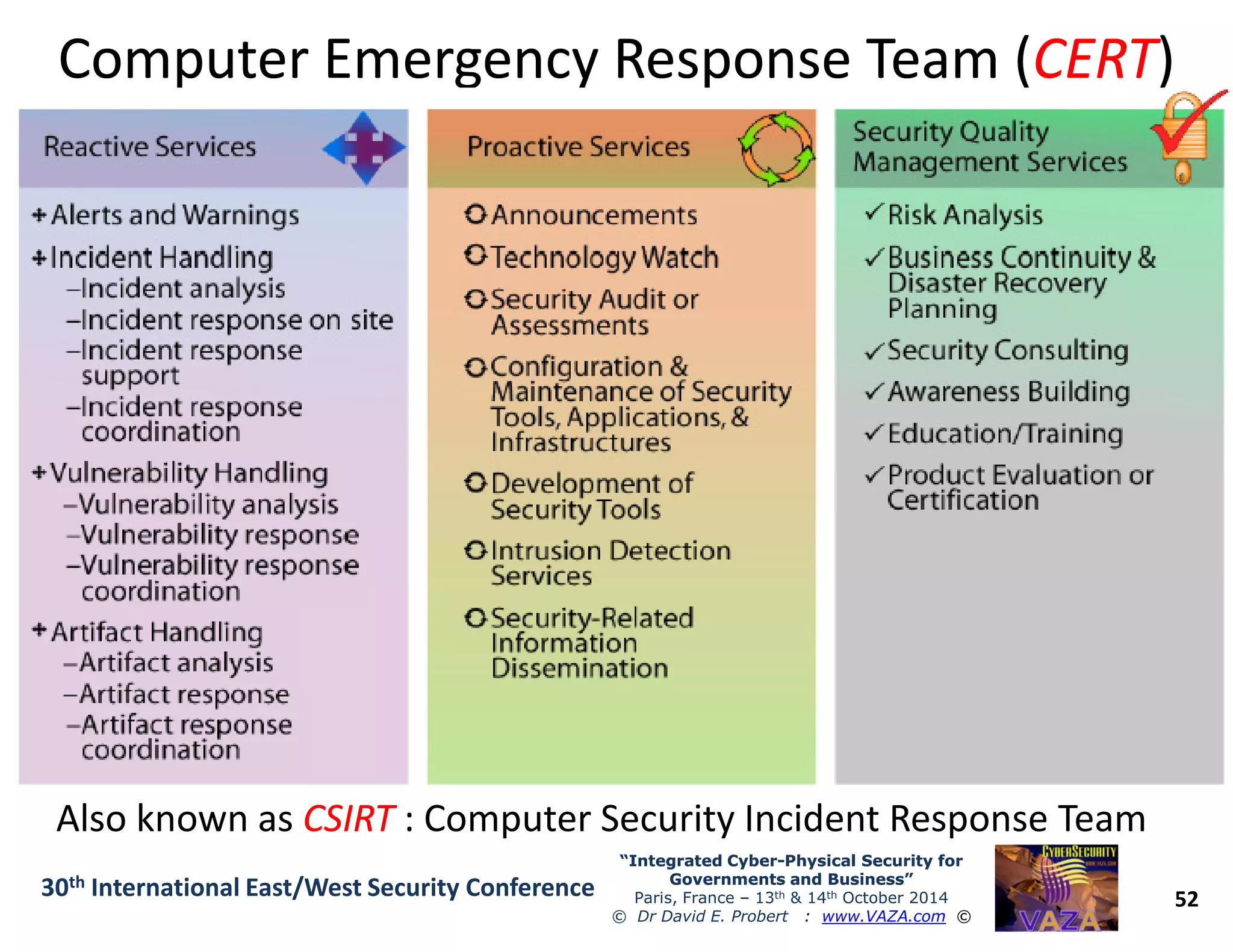
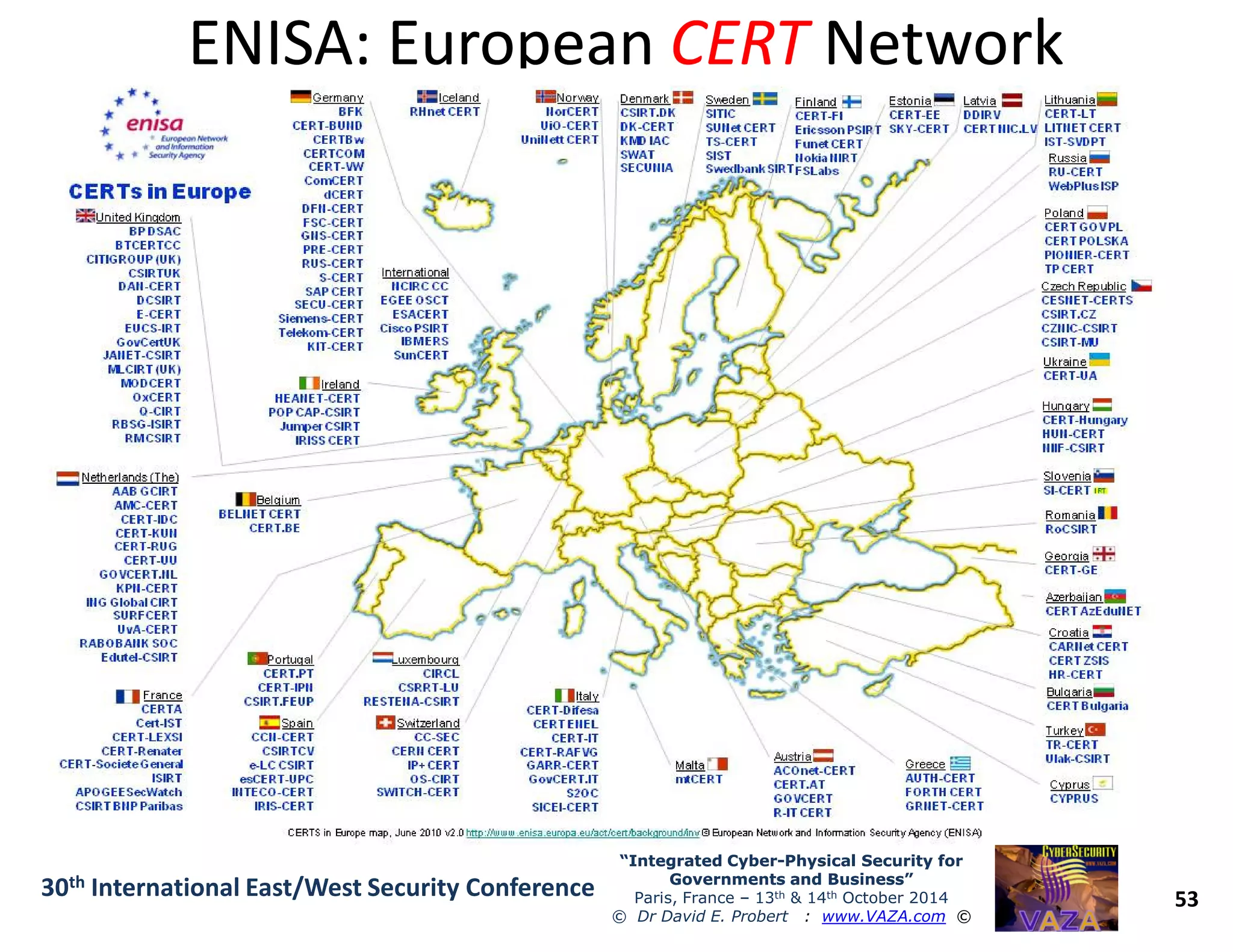
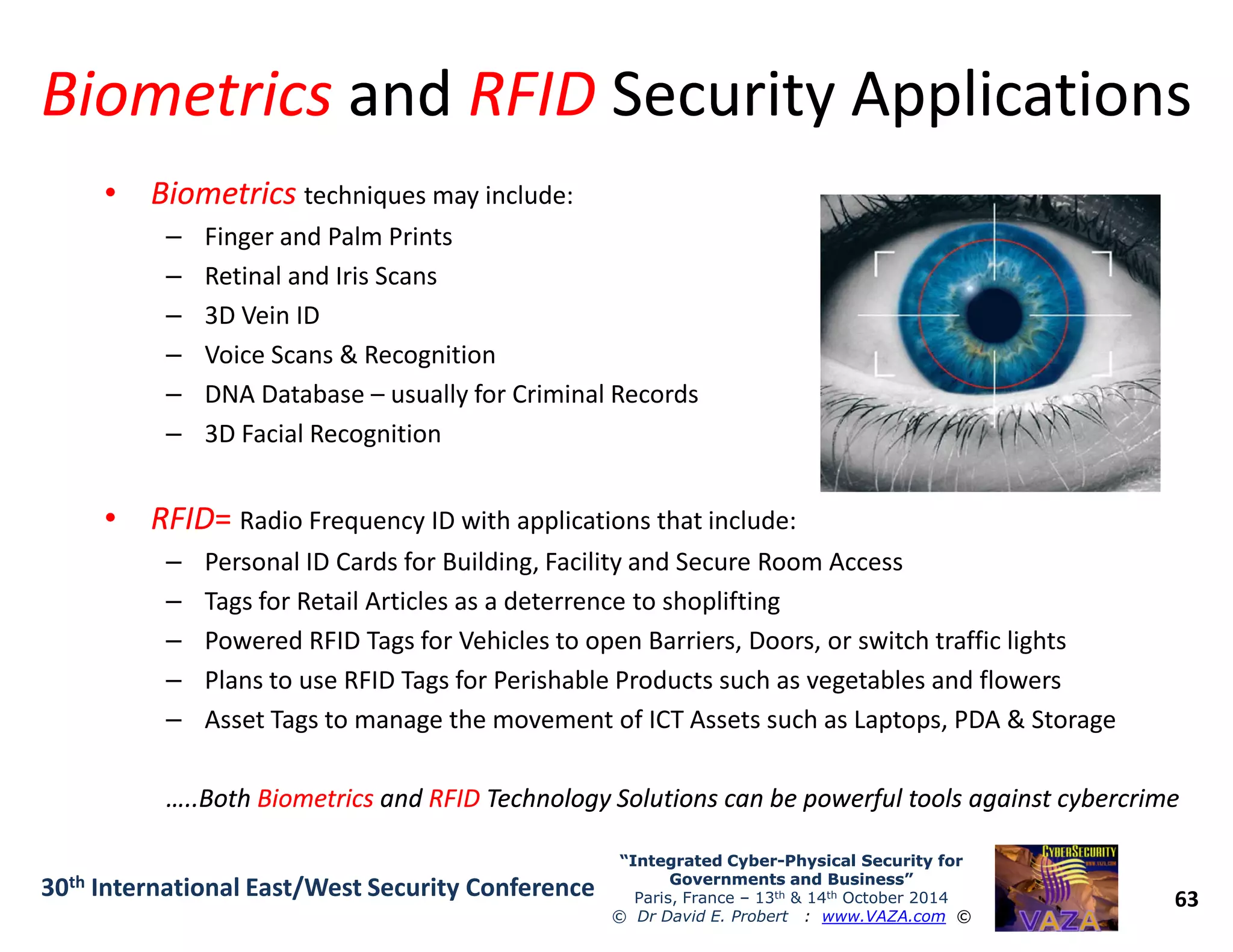
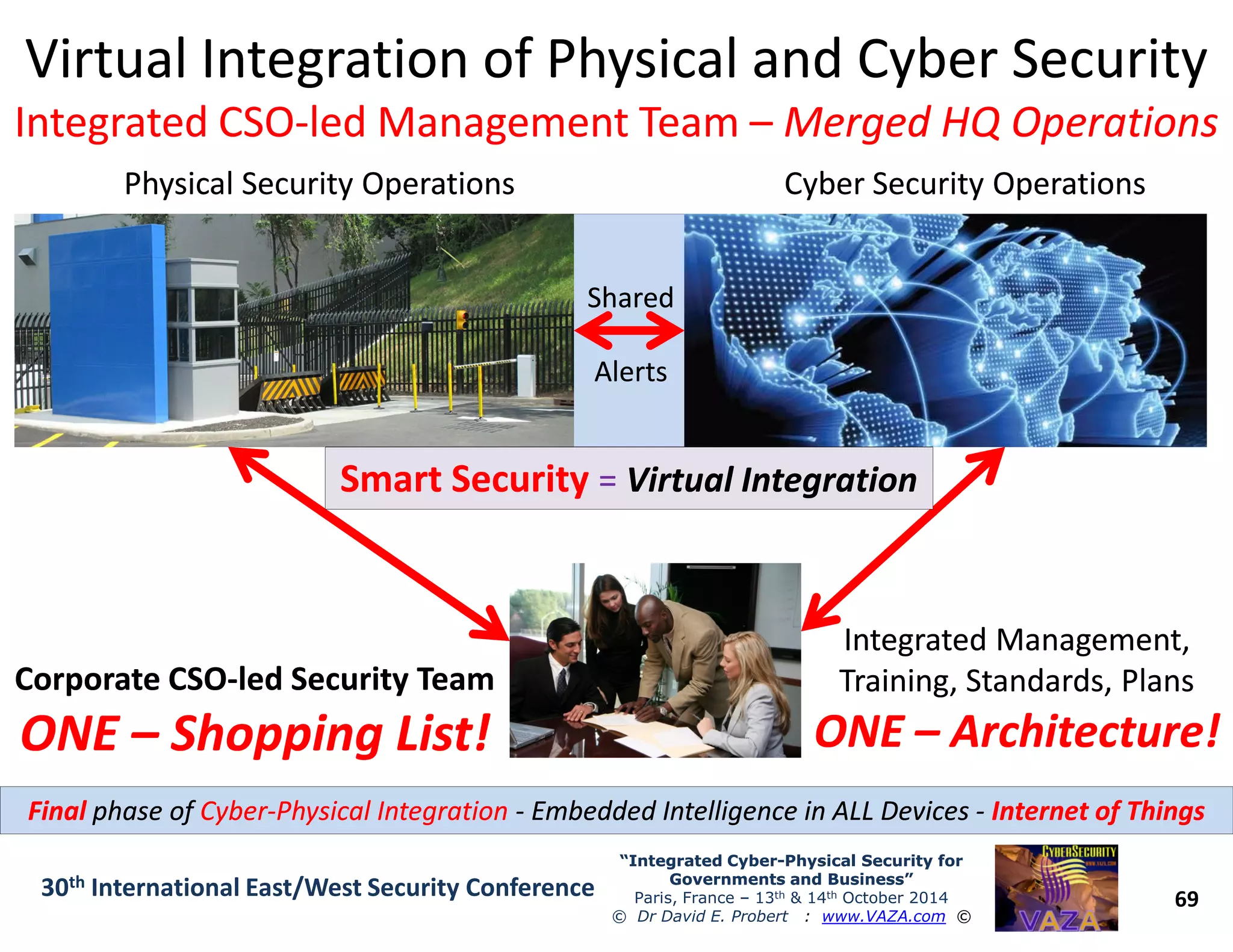
The document discusses the integration of cybersecurity and physical security for governments and businesses, emphasizing the need for smart and resilient security in the face of evolving cyber threats. It highlights themes such as the convergence of national security strategies, mapping cyber threats, and the architecture of cybersecurity operations. The presentation outlines various categories of cybersecurity threats, case studies on national cybersecurity agencies, and the importance of embedding networked intelligence in security systems.