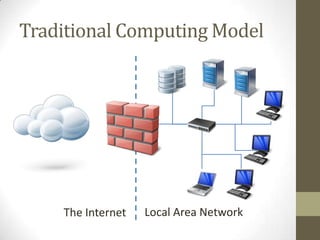
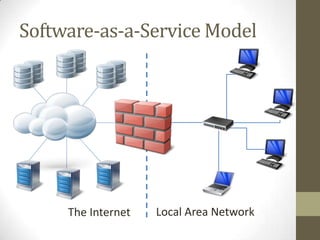
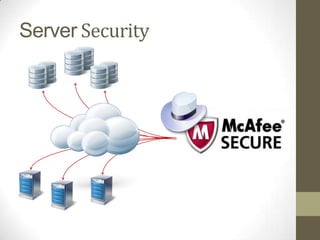
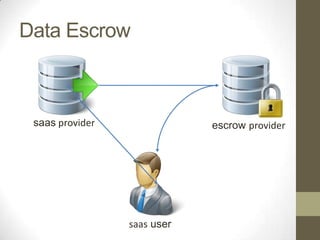
The document discusses the ethical obligations of lawyers regarding informed consent and the use of cloud computing. It emphasizes that lawyers must take reasonable steps to protect client confidentiality while using technology and must obtain informed consent when disclosing confidential information. It also outlines the necessary security procedures cloud providers should have to safeguard client data.