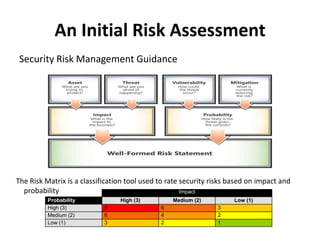
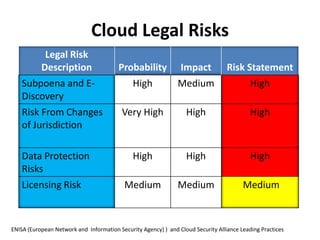
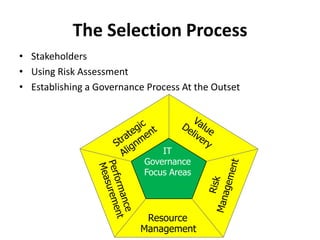
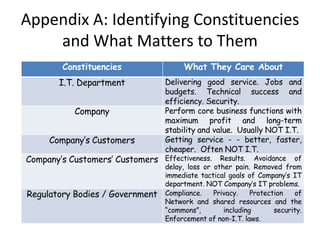
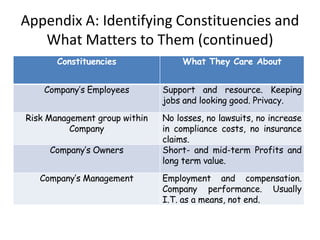
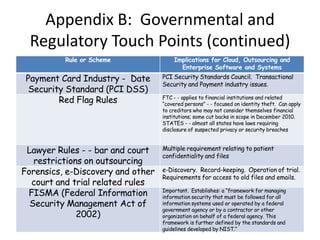
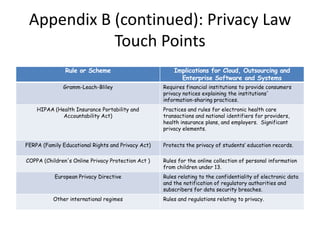
This document discusses key considerations for procuring cloud computing services and drafting cloud services agreements. It identifies legal and business risks, such as data security, privacy, jurisdiction, and termination issues. It provides recommendations for addressing these risks, including conducting due diligence of the vendor, negotiating terms to retain data ownership and ensure access in case of disputes, and establishing governance processes to manage the relationship. The appendices describe relevant stakeholders, regulatory issues, and aspects of assessing security based on NIST standards.