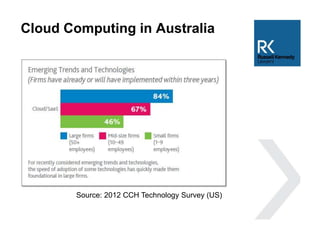
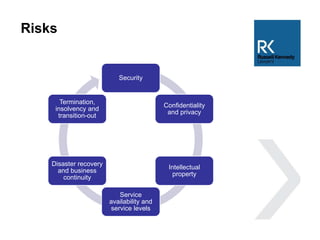
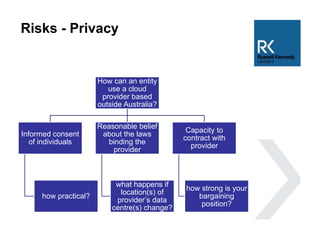
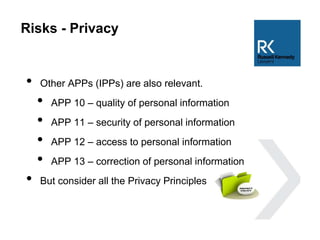
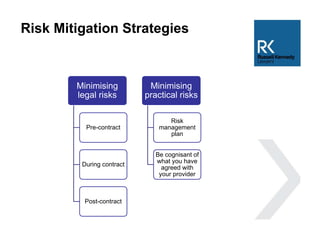
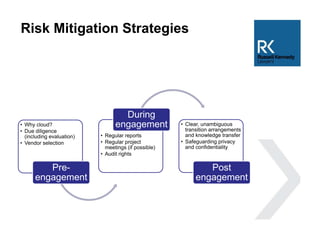
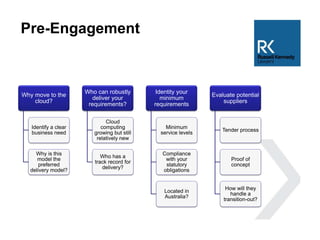
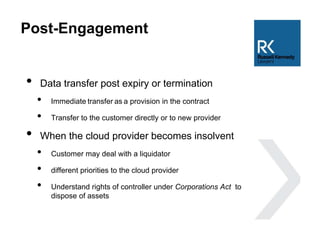
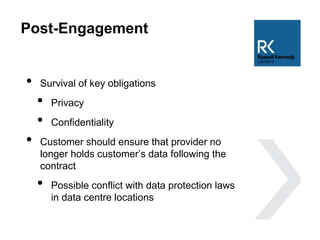
The document discusses the use and risks associated with cloud computing in Australia, highlighting legal, security, and privacy concerns. It outlines strategies for risk minimization during pre-contract, during and post-contract phases, emphasizing due diligence, clear service levels, and disaster recovery plans. The importance of robust vendor selection and compliance with privacy laws is also emphasized to ensure effective data management and protection.