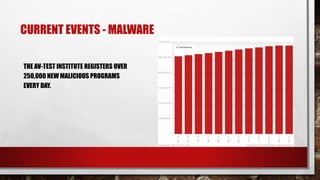
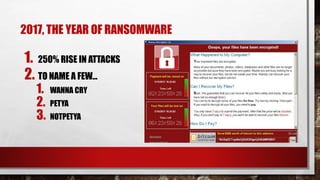
The document summarizes top cybersecurity facts and trends for 2018. It notes that cybercrime costs are projected to reach $6 trillion annually by 2021 and cybersecurity spending is expected to exceed $1 trillion from 2017 to 2021. It also discusses the growing shortage of cybersecurity professionals, with over 3.5 million unfilled jobs predicted by 2021. The document provides an overview of recent malware trends, ransomware attacks in 2017, and projections that hardware vulnerabilities will be a major focus in 2018.