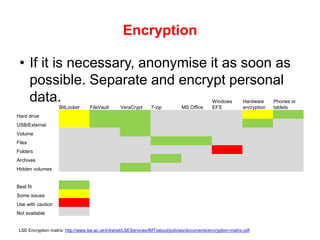
The document outlines the importance of information security within the context of GDPR, emphasizing the need for proper data management practices such as minimal data collection and anonymization. It provides guidance on access controls, encryption methods, and the handling of personal data to mitigate risks of breaches like phishing and ransomware. Additionally, it mentions the use of cloud storage solutions at LSE and highlights the importance of following contractual and security protocols.