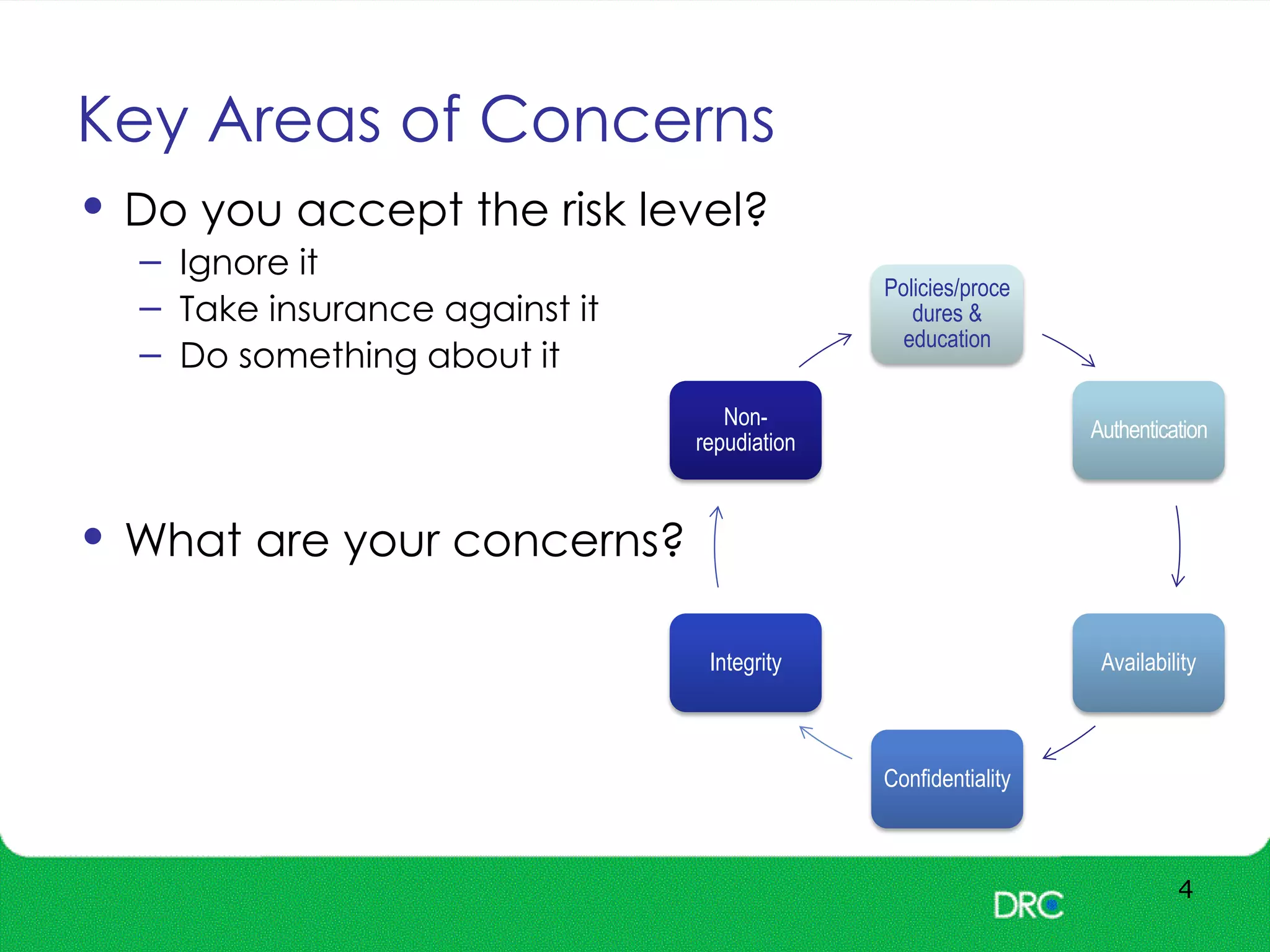
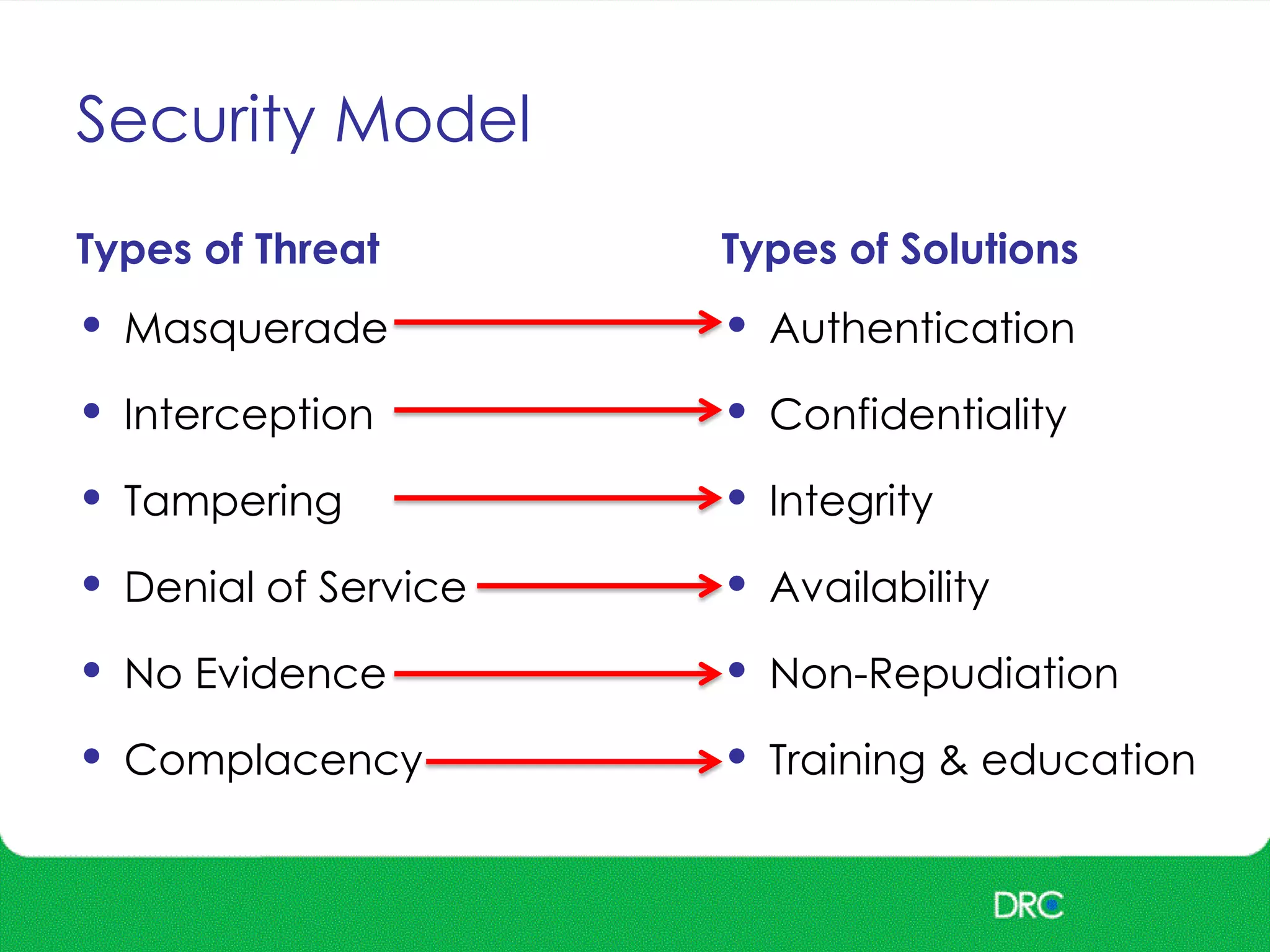
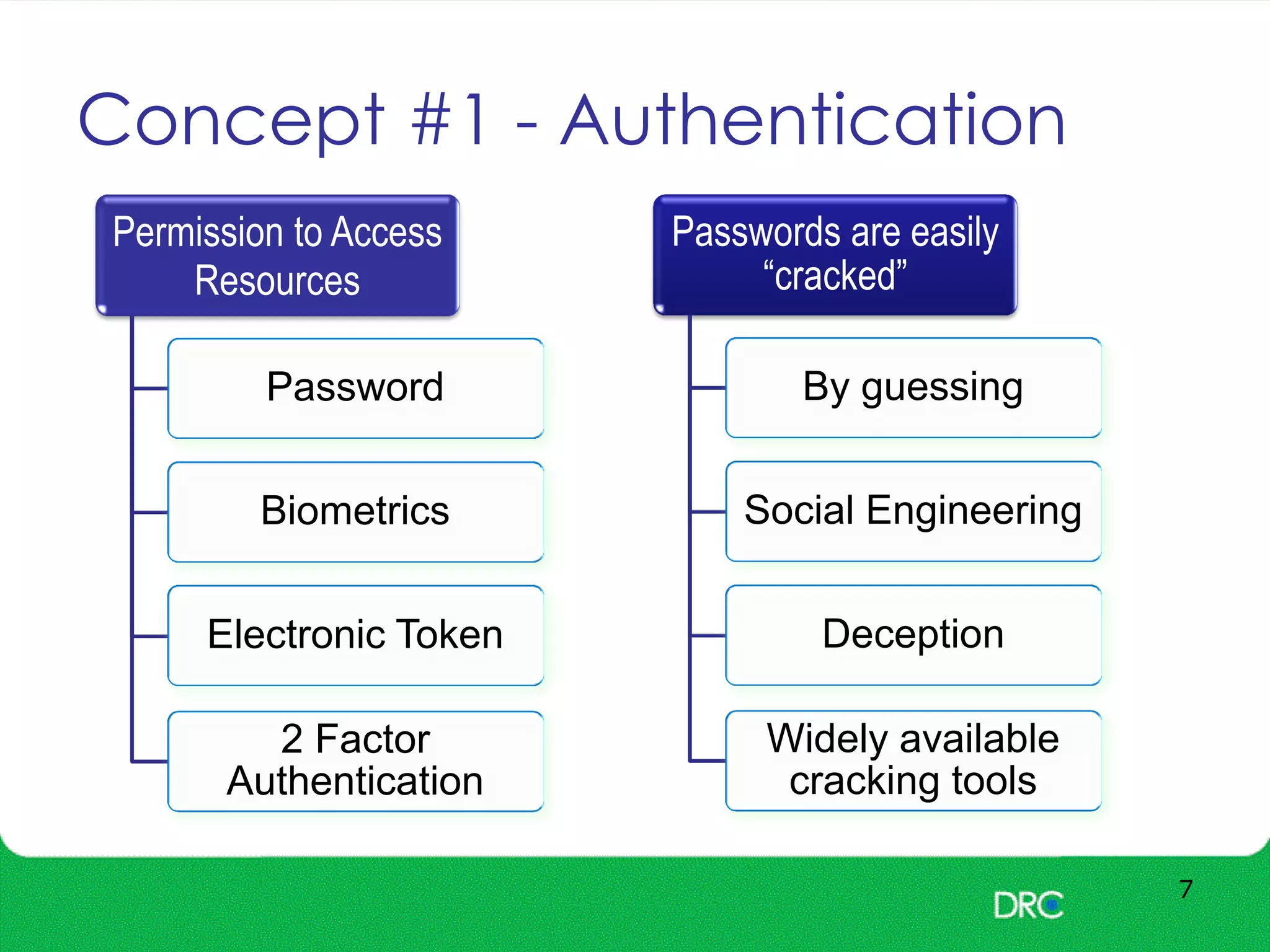
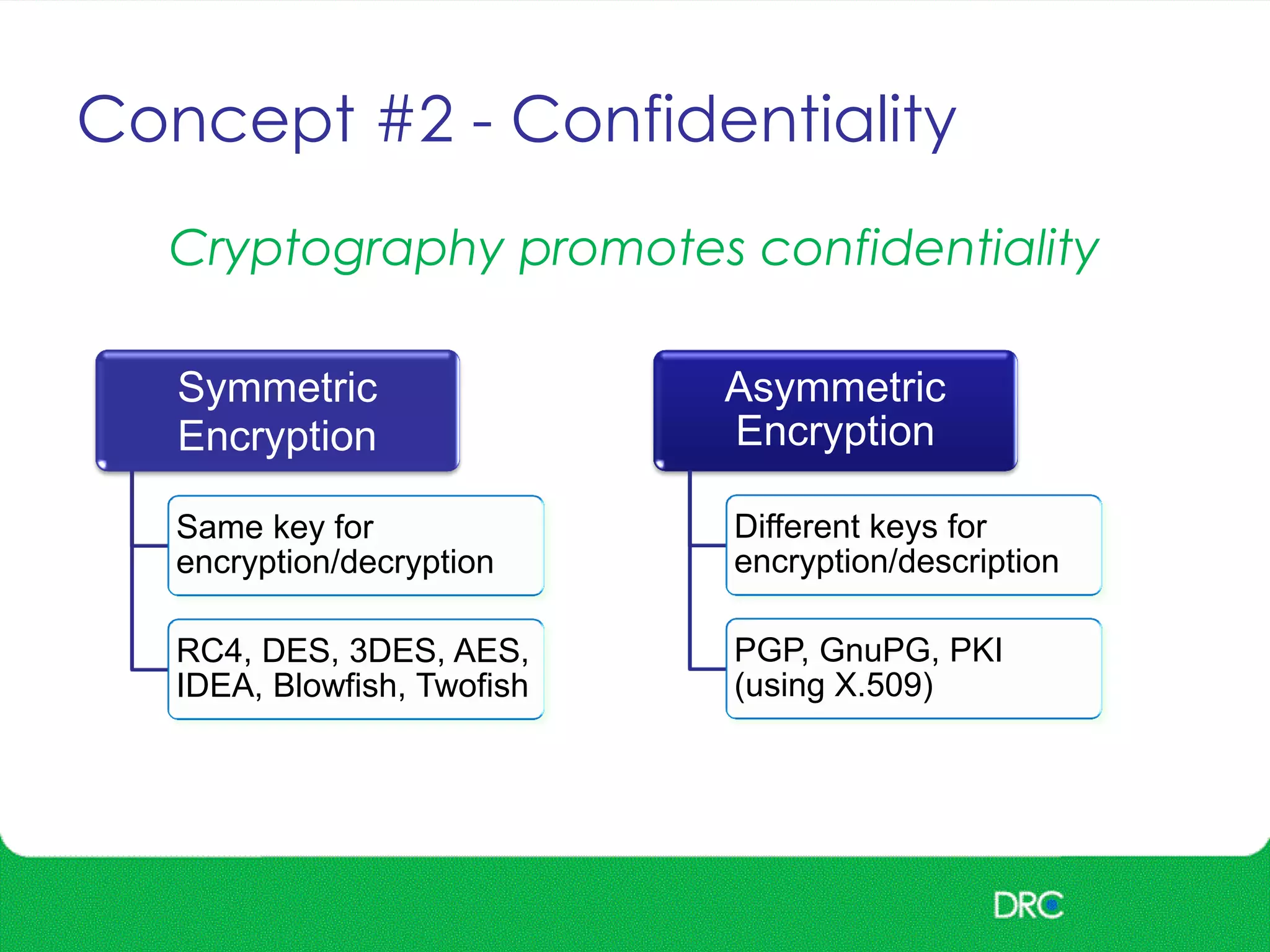
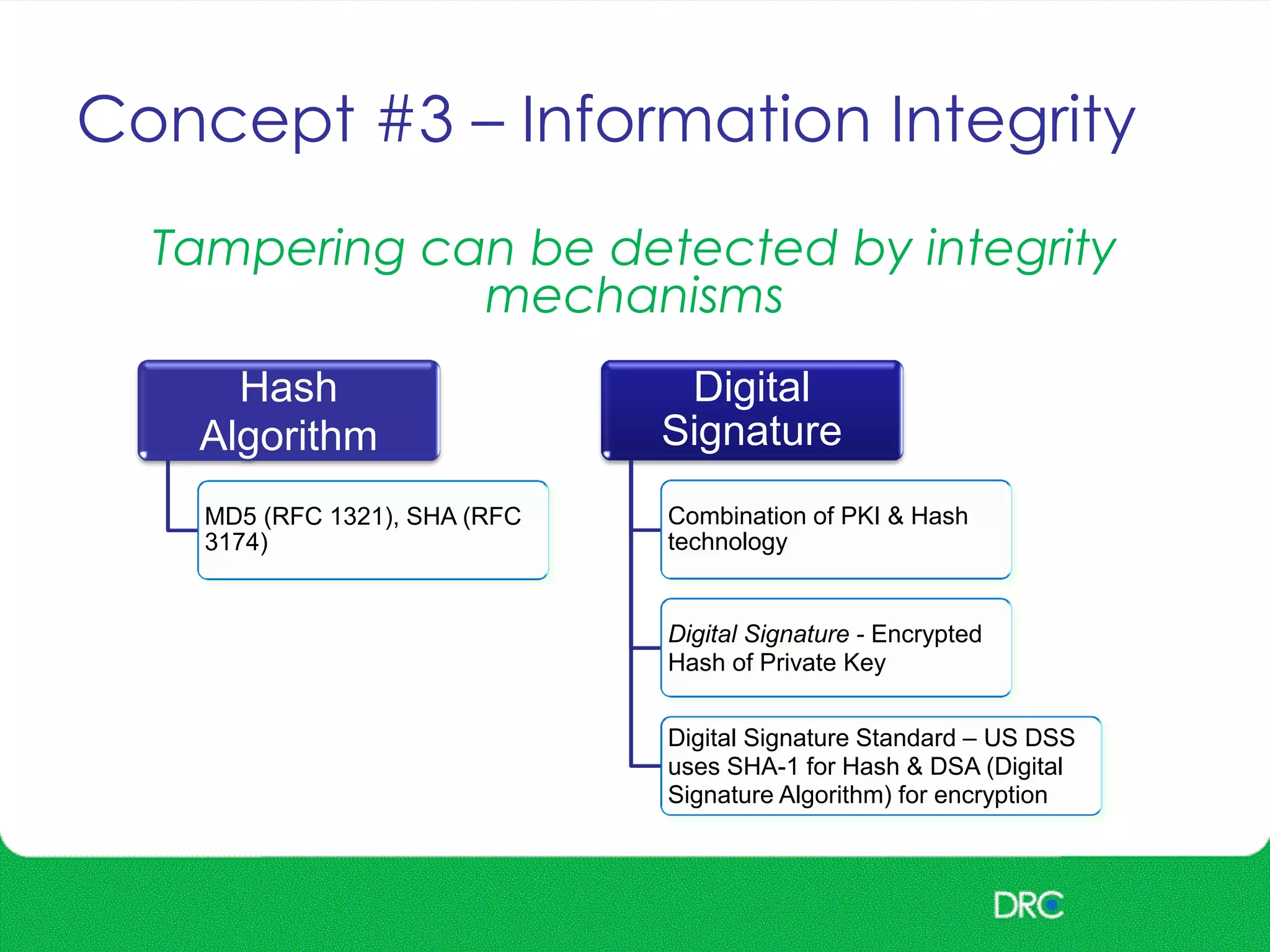
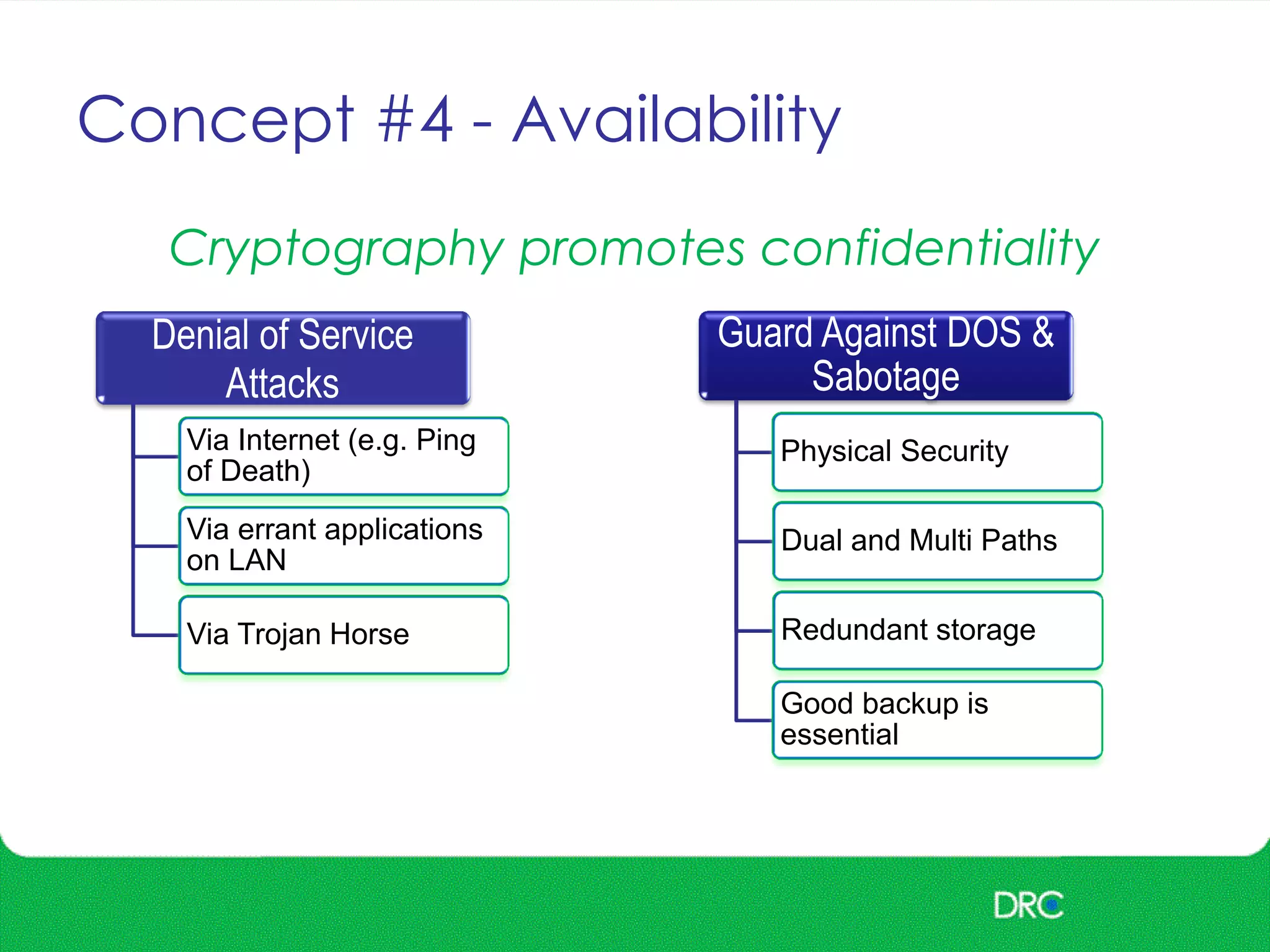
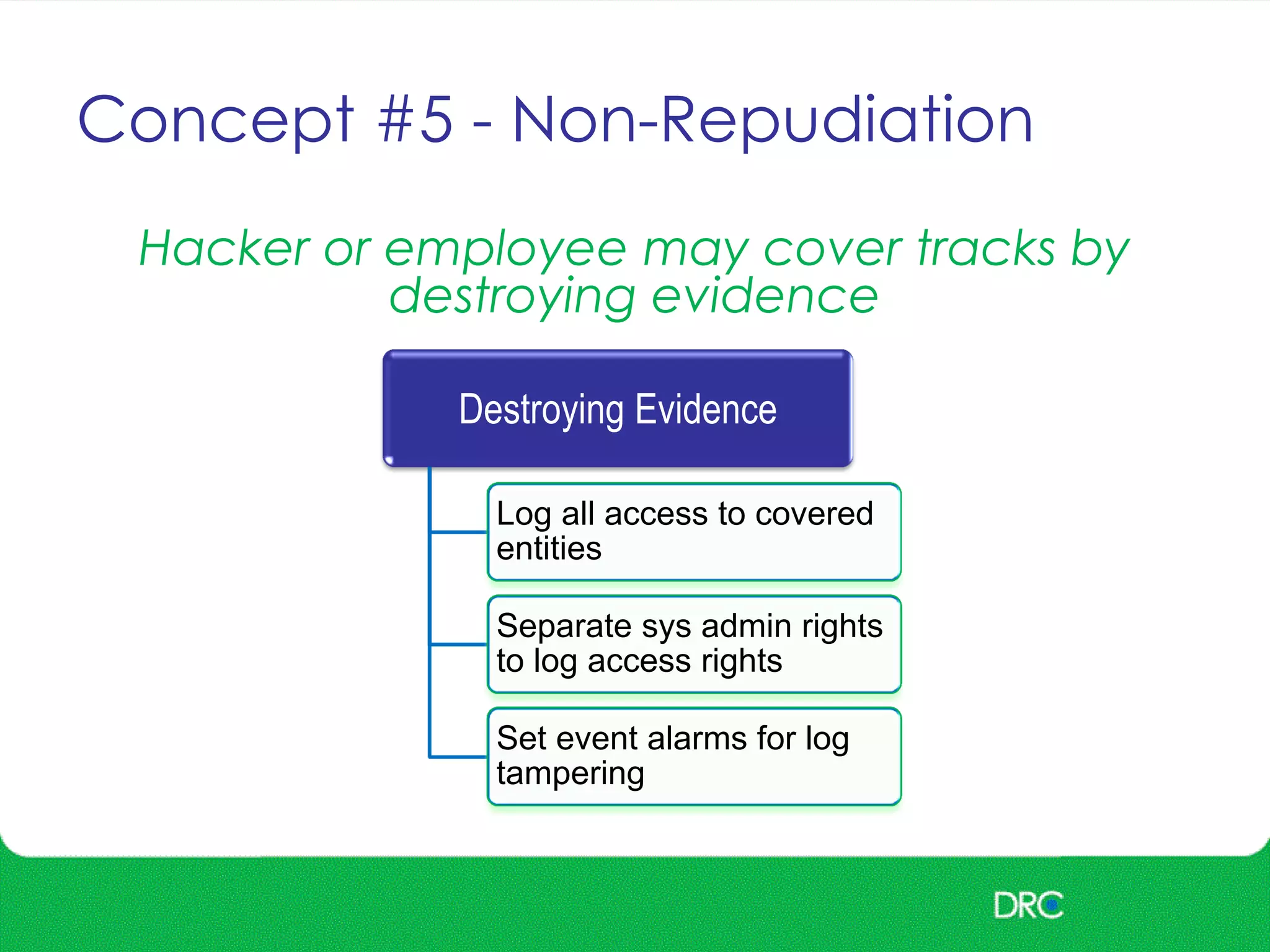
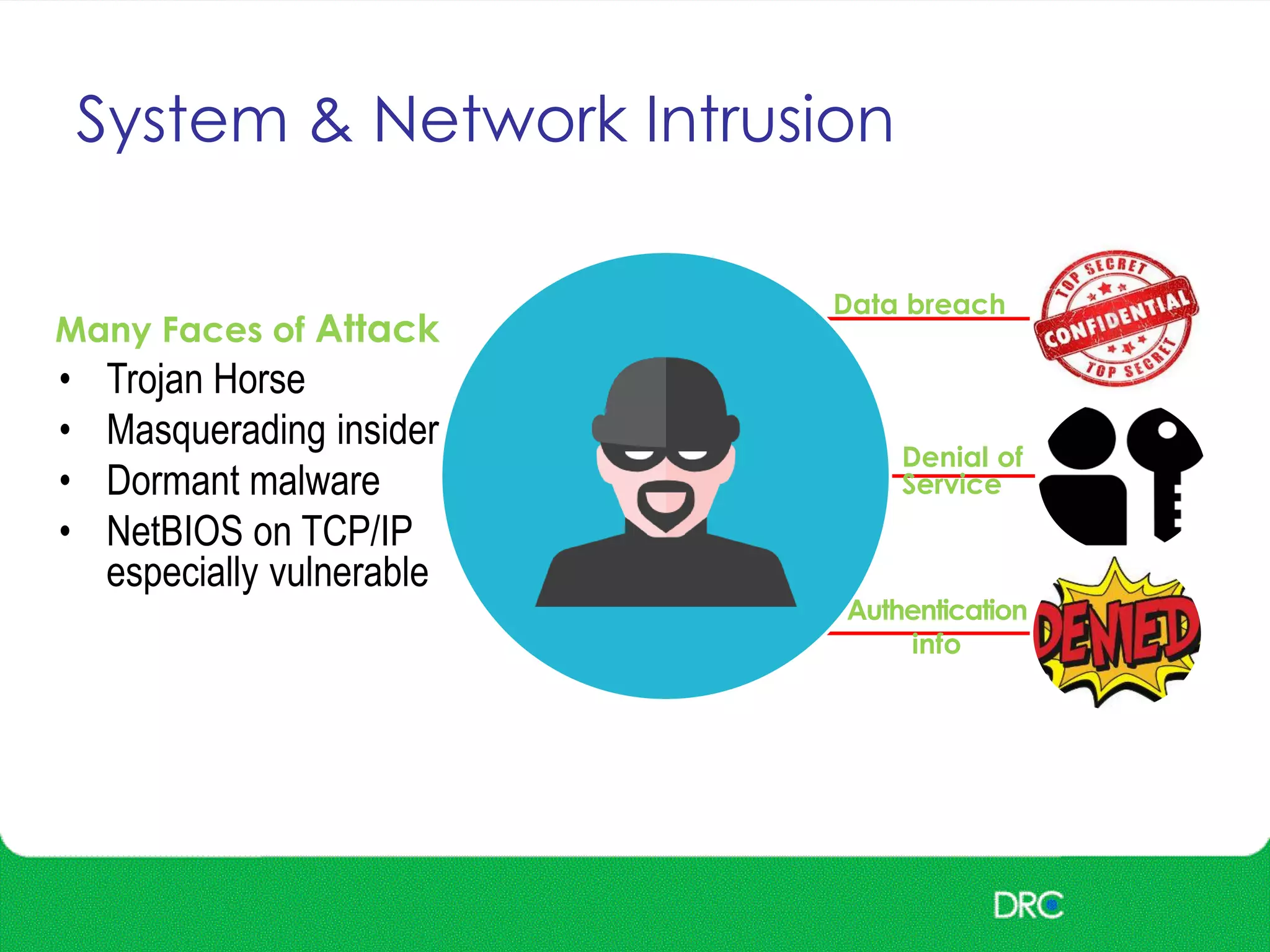
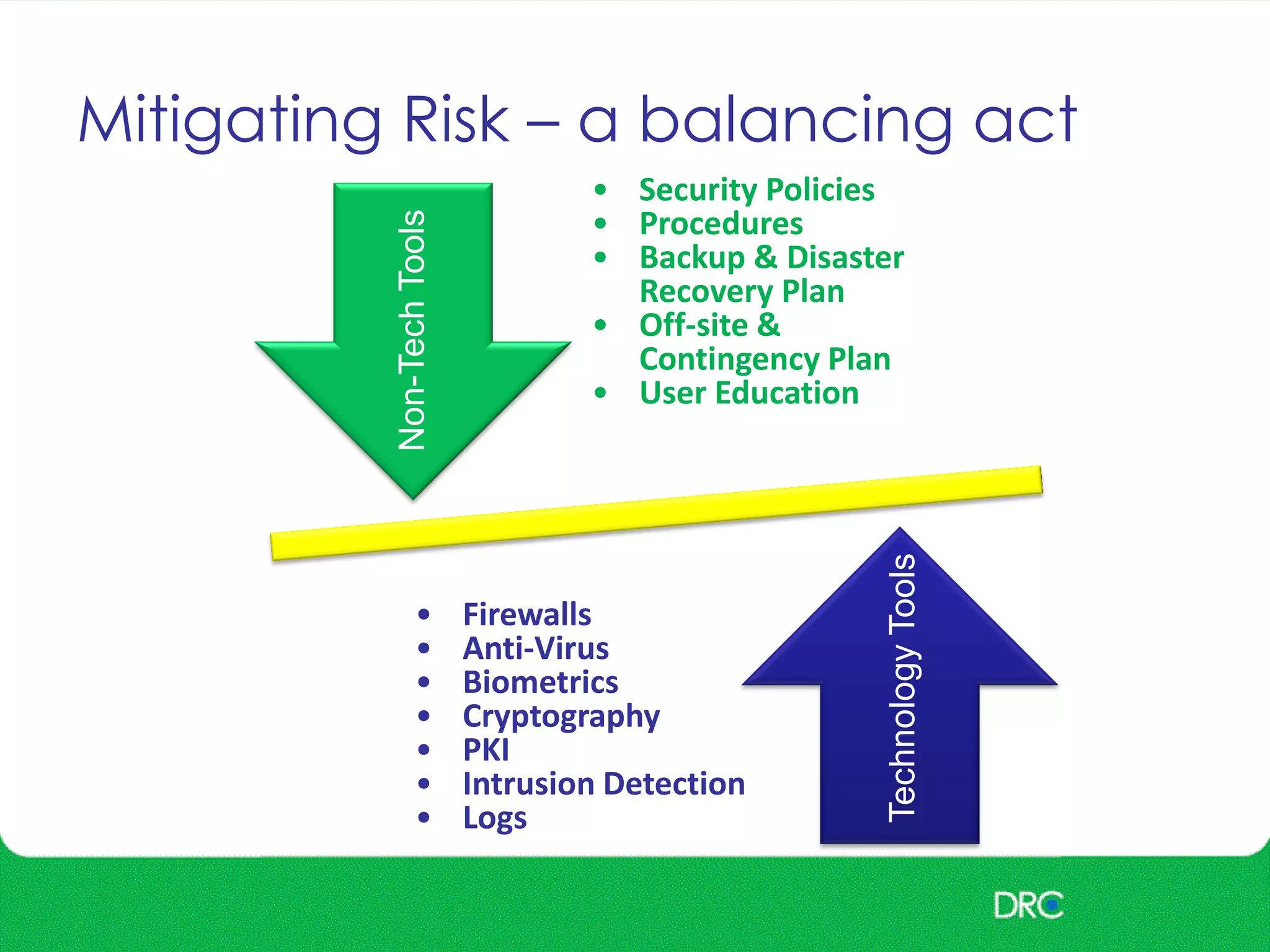
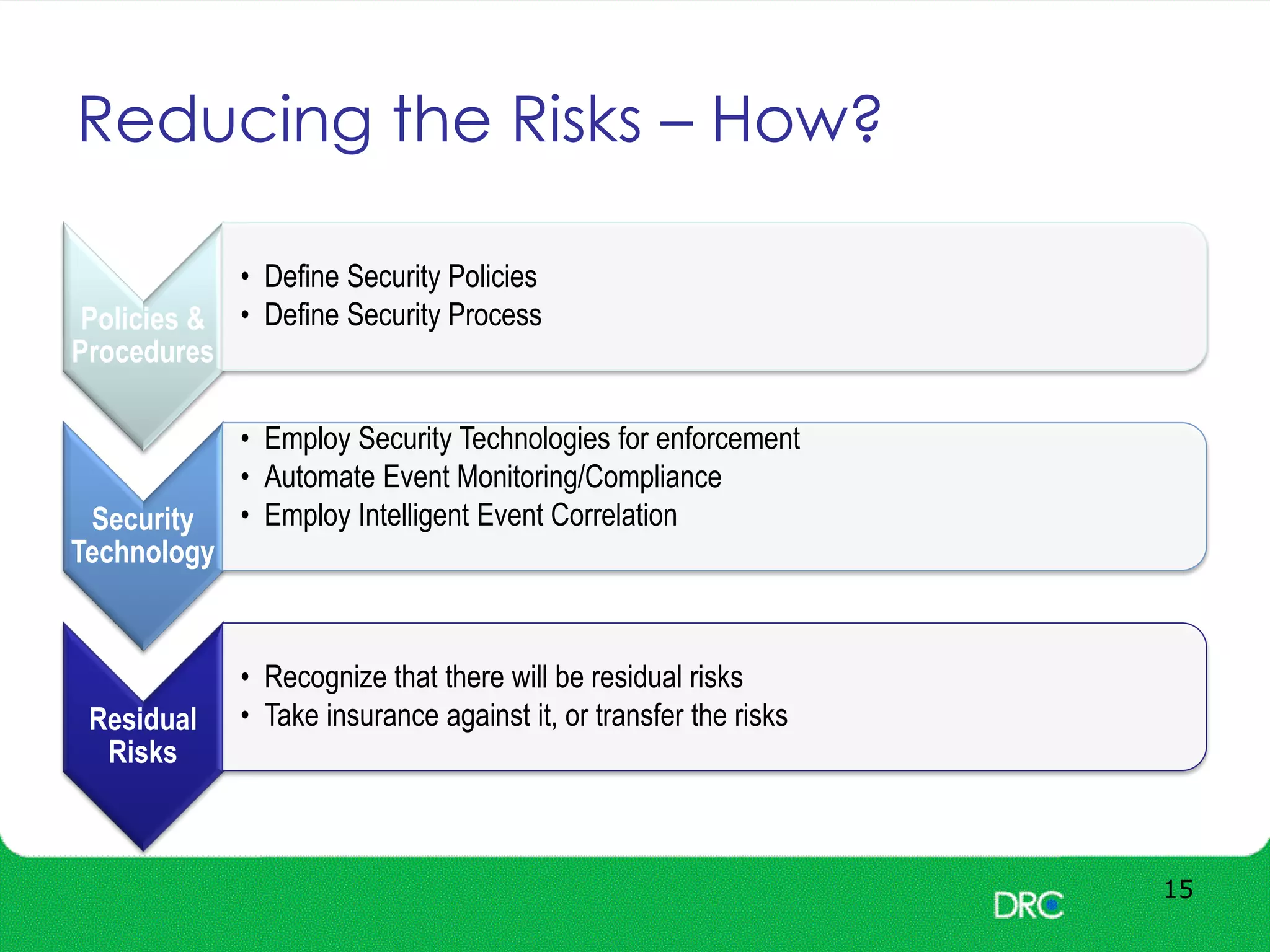
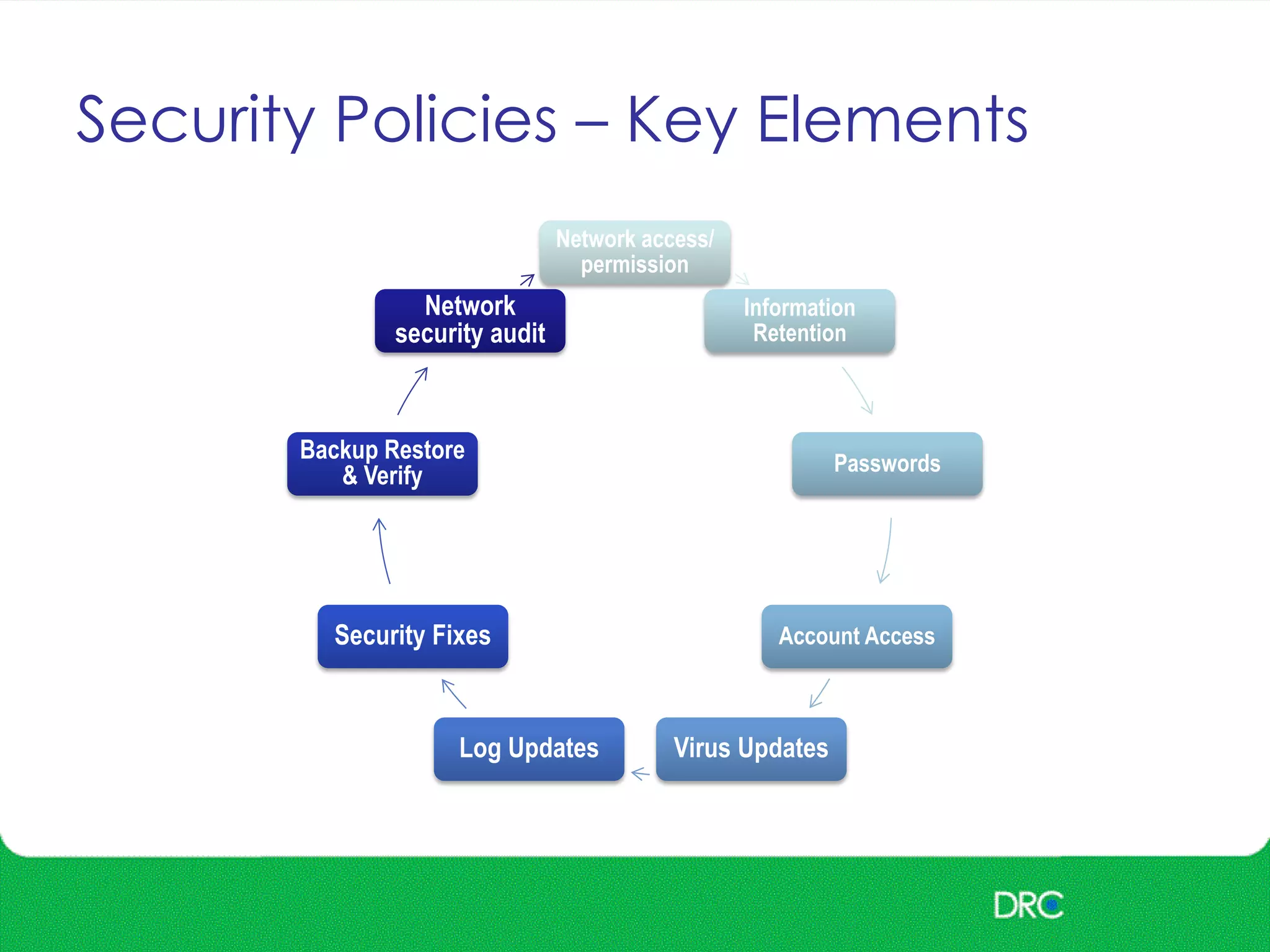
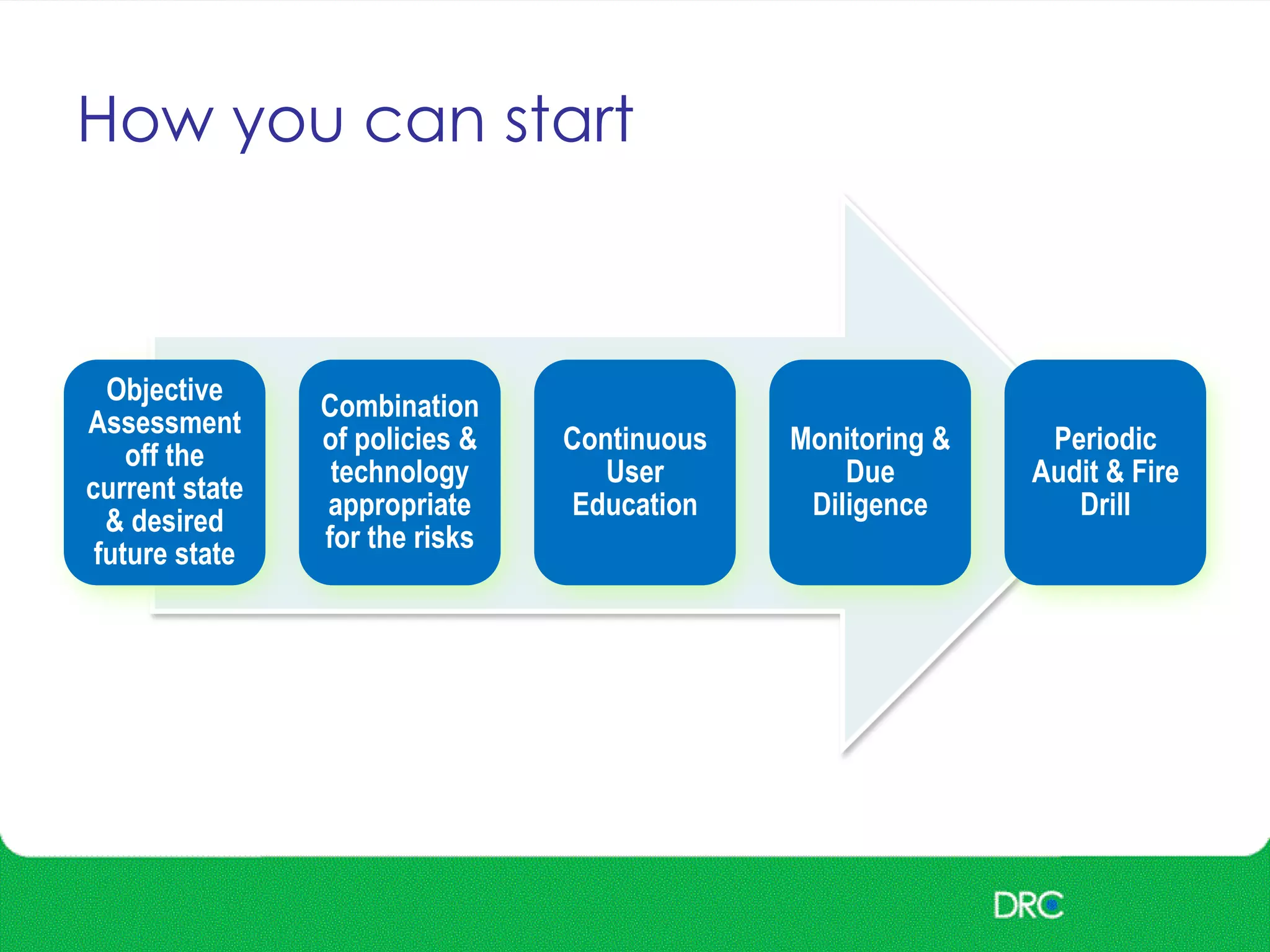
The document outlines essential cybersecurity concepts, identifying threats from hackers, insiders, and natural disasters, while emphasizing the importance of awareness and education. It details key areas of concern such as risk acceptance, security policies, and various cyber threats like denial of service and tampering. Additionally, it discusses solutions for authentication, confidentiality, integrity, availability, and non-repudiation, along with a framework for reducing risks through policies and technology.