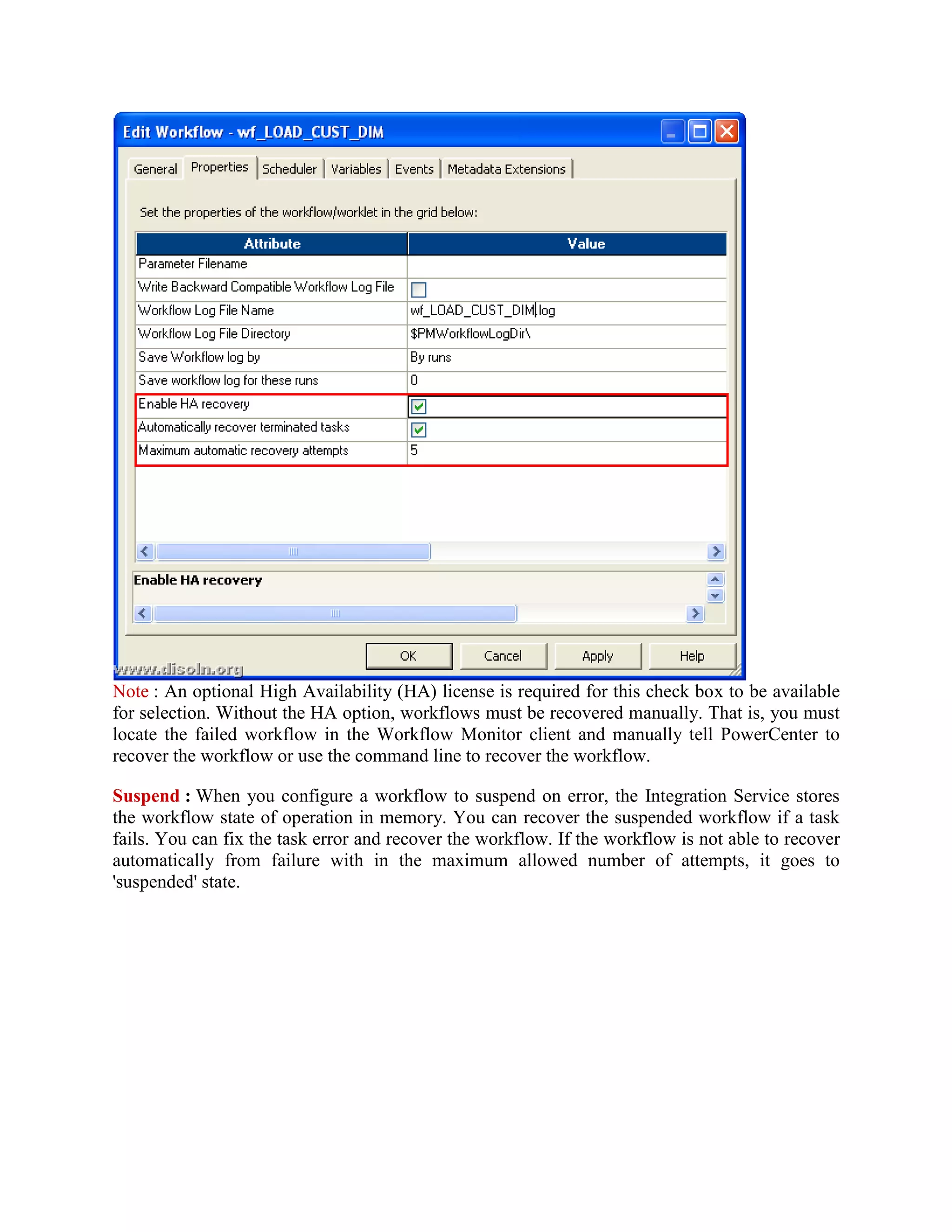
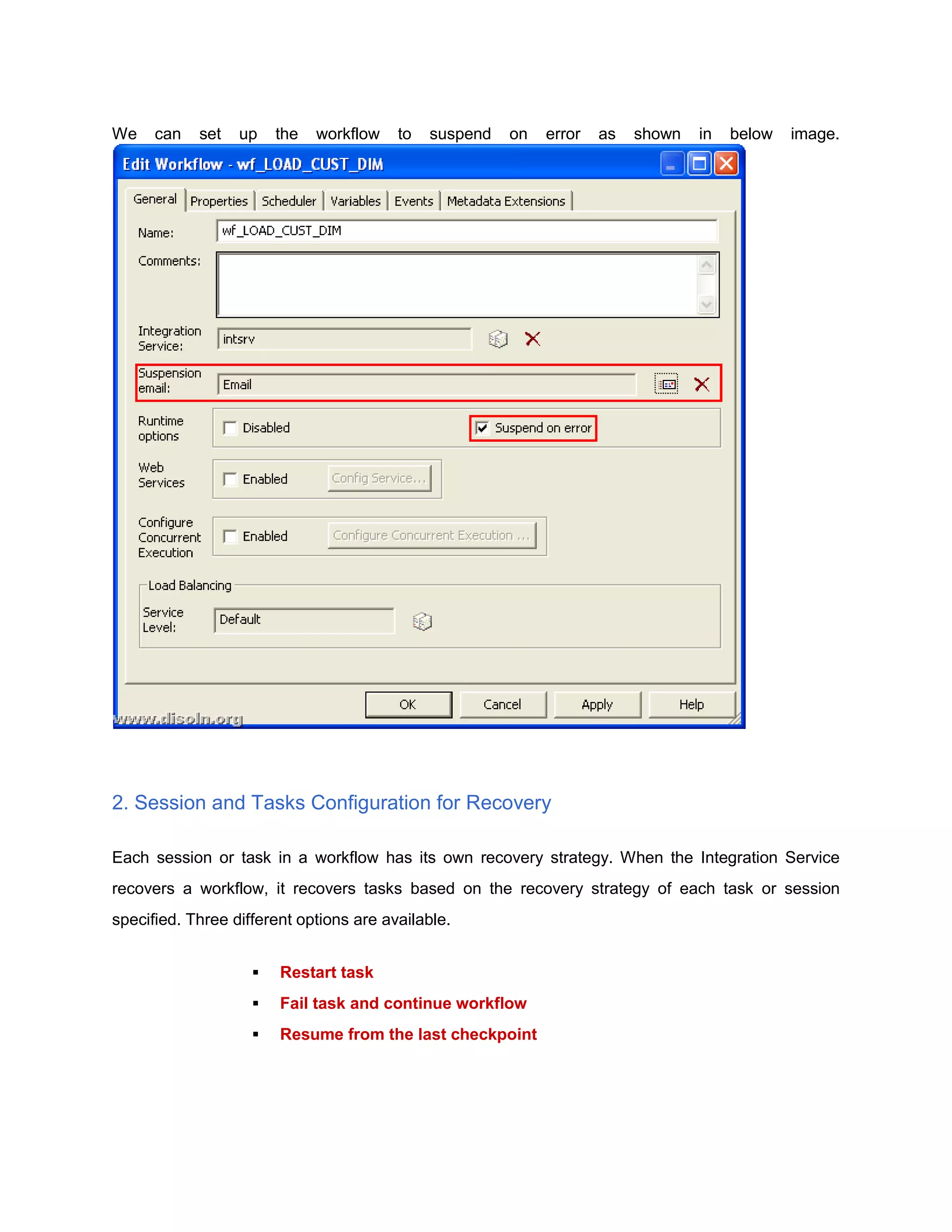
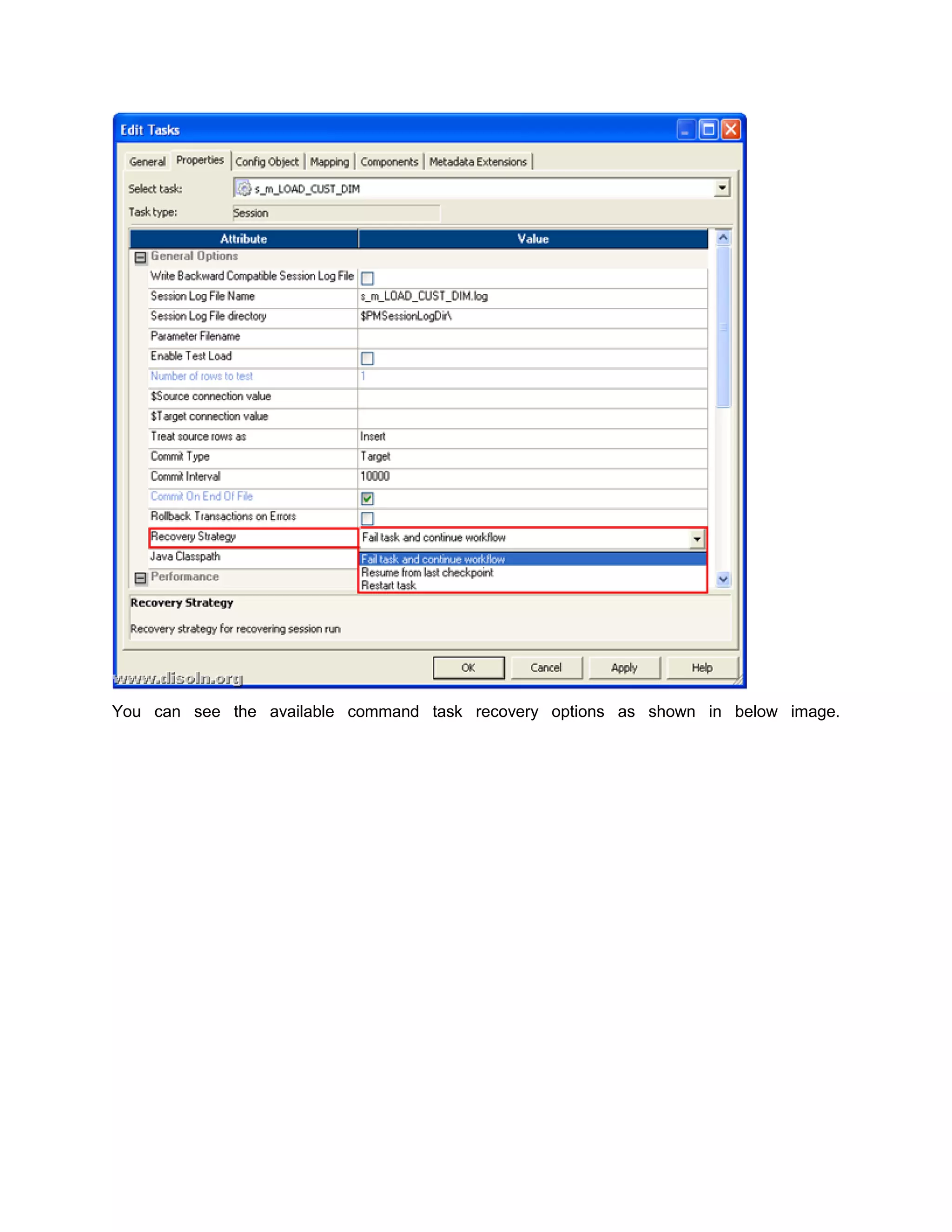
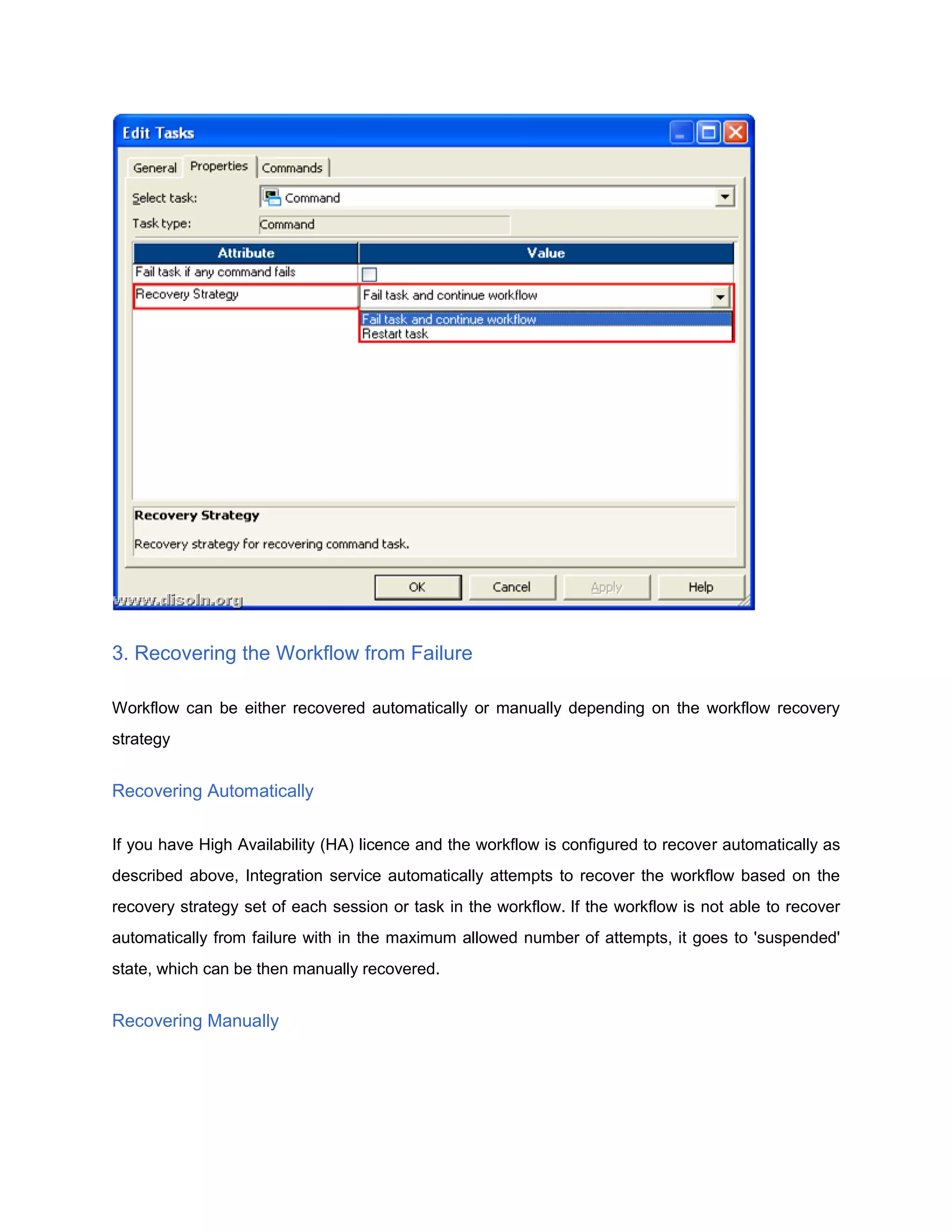
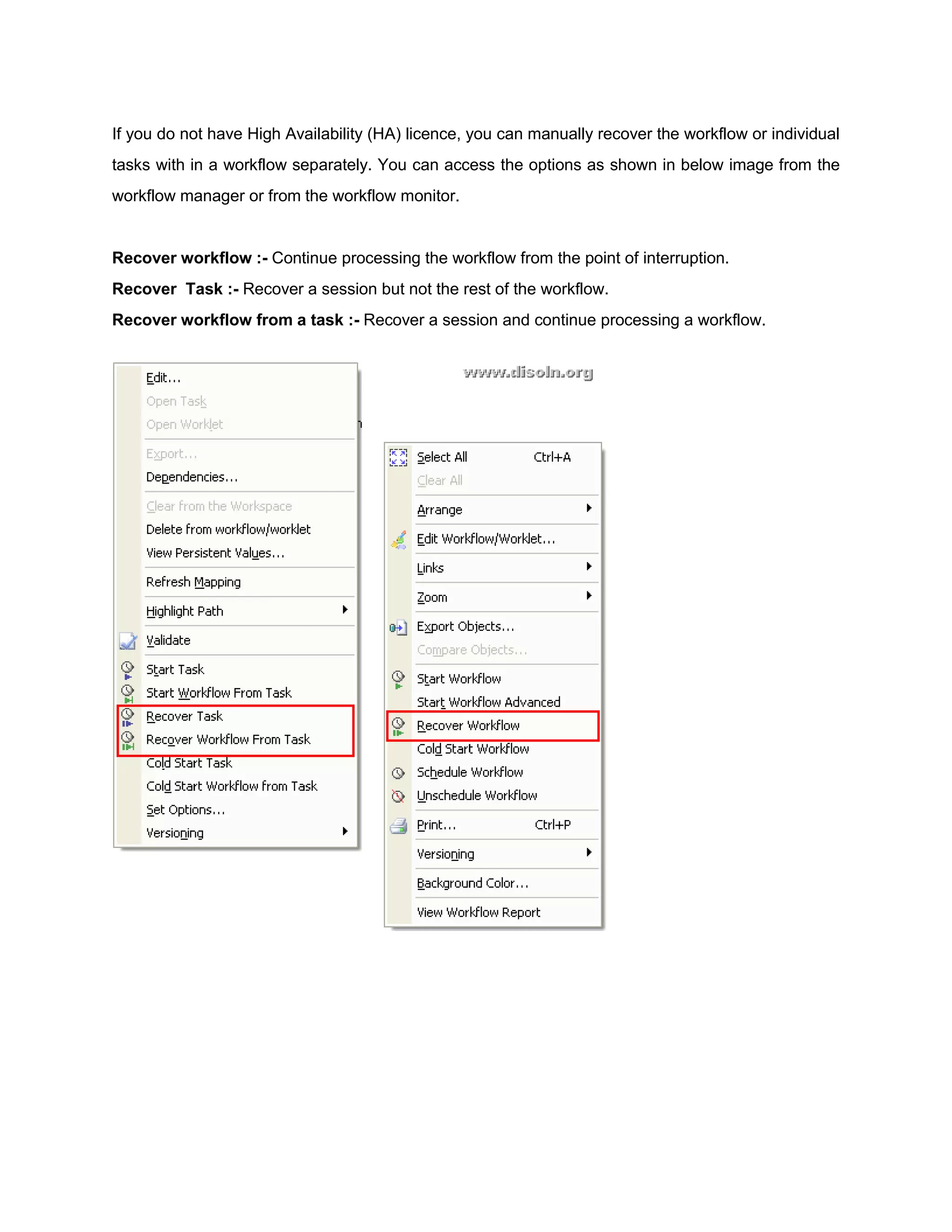
Failure Recovery in Informatica discusses how to configure workflows in Informatica PowerCenter for recovery from failures. It explains that workflows can be configured to recover automatically if enabled for recovery or set to suspend on error. Each session and task within a workflow can be configured with different recovery strategies such as restarting, failing and continuing, or resuming from the last checkpoint. Workflows can then be recovered either automatically if configured for it, or manually through the workflow manager or monitor.