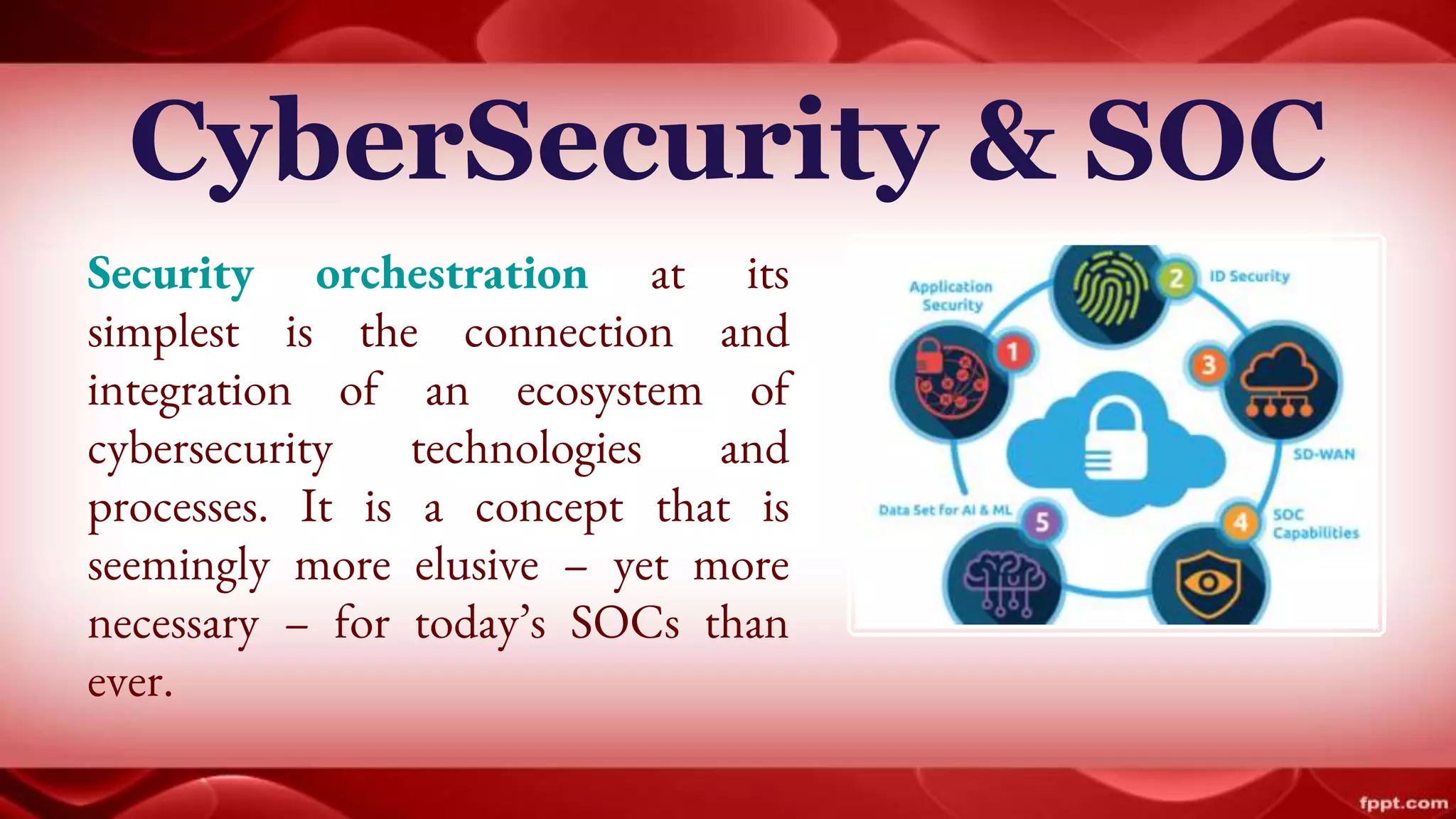
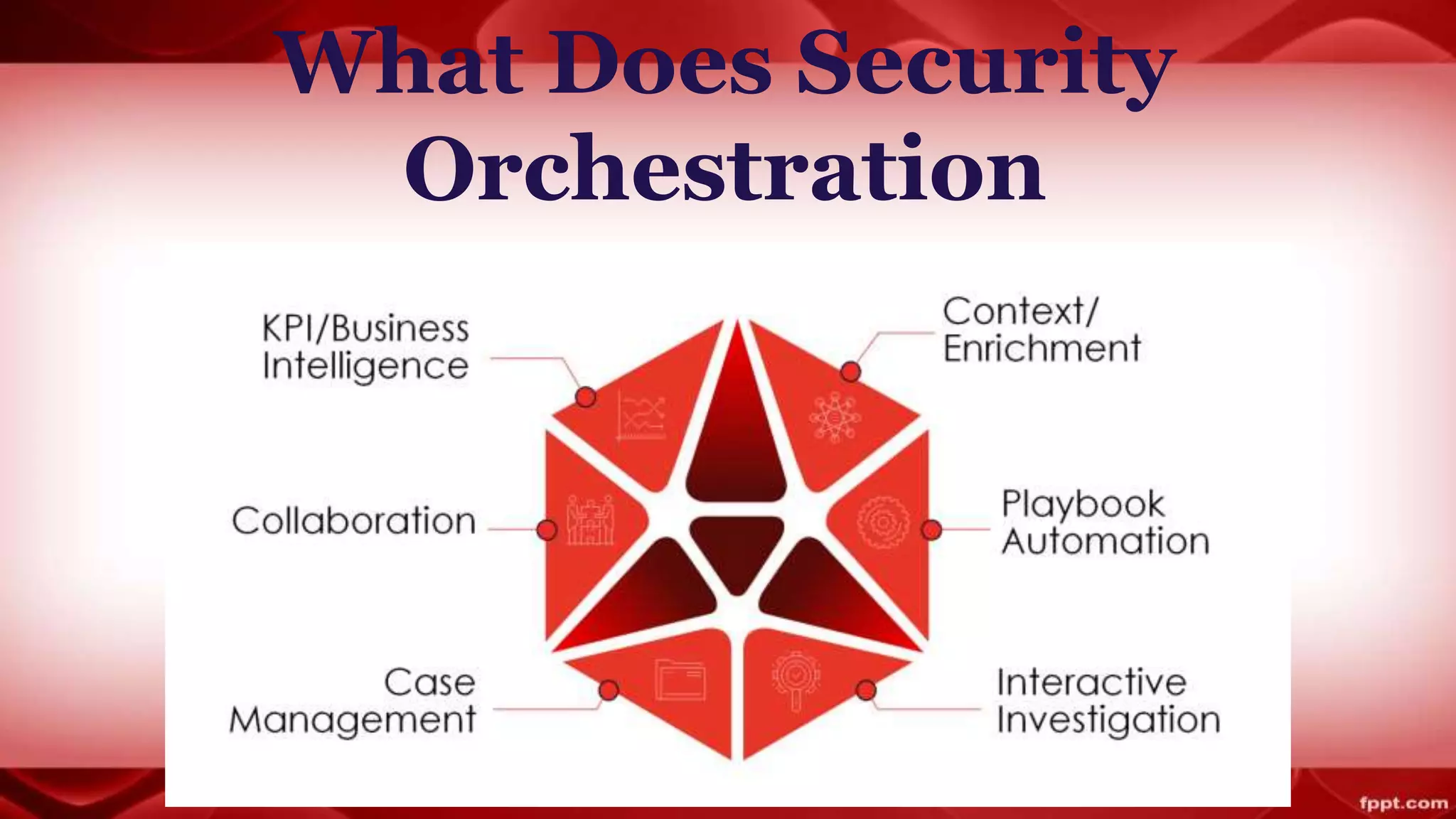
Security orchestration integrates various cybersecurity tools and processes to enhance the efficiency of security operations centers (SOCs). Unlike security automation, which focuses on automating tasks, orchestration allows for collaboration among teams and streamlines investigations by providing context and visibility. As organizations face challenges with disparate systems, implementing security orchestration can significantly improve incident response and overall security management.