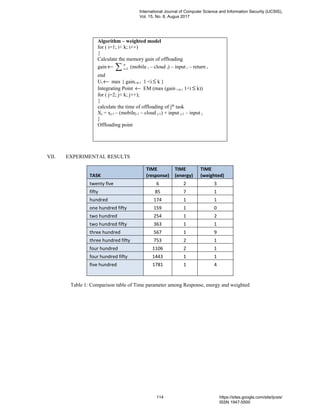
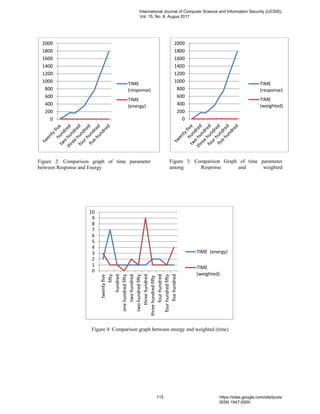
The document discusses an adaptive offloading approach in mobile cloud computing, which aims to partition tasks dynamically to enhance execution by shifting heavy computations from mobile devices to cloud servers. This method improves mobile application performance, reduces energy consumption, and addresses the limitations of mobile devices. Additionally, it outlines different partitioning schemes and models to optimize resource utilization while exploring the benefits of cloud computing in mobile environments.
![Improve the Offloading decision by Adaptive
partitioning of task for Mobile Cloud
Computing
Neha Goswami Sugandha Sharma
Computer Science and Engineering Department,
Chandigarh University
National Highway95, Mohali,140413, Punjab, India;
nggoswamineha@gmail.com
Computer Science and Engineering Department,
Chandigarh University
National Highway95, Mohali,140413, Punjab, India;
Sugandha.ss1@gmail.com
Abstract- Adaptive Offloading in Mobile Cloud
Computing by automatic partitioning approach of tasks
is the idea to augment execution through migrating
heavy computation from mobile devices to resourceful
cloud servers and then receive the results from them via
wireless networks. Offloading is an effective way to
overcome the resources and functionalities constraints
of the mobile devices since it can release them from
intensive processing and increase performance of the
mobile applications, in terms of response time.
Offloading brings many potential benefits, such as
energy saving, performance improvement, reliability
improvement, ease for the software developers and
better exploitation of contextual information.
Parameters about method transitions, response times,
cost and energy consumptions are dynamically re-
estimated at runtime during application executions.
Keywords- Cloud Computing, Mobile Cloud
Computing(MCC), Offloading, System model (cost model,
energy model, weighted model)
I. INTRODUCTION
With the computing technology advancements, the
desktop computer usage expands and main frame is
also expanded to a wider range of embedded
applications and mobile applications which includes
environmental sensing, surveillance, mobile phones
and GPS navigation, etc. These several applications
on systems run with resources that are limited.
Fore.g, battery powered is the mobile phones. The
environmental sensors comprises of smallersize
physically, small storage amounts and slow
processors. Wireless applications are used by most of
these applications and low are their magnitude orders
in comparison with wired networks. Meanwhile,
programs that run on these systems have increasing
complexity—for example, video processing on
mobile phones and object recognition on mobile
robots. An increasing gap is there among the complex
programs demand and the limited resources
availability.
A solution is offloading for augmentingthe
capabilities of this mobile system with computational
migration for more computers that are resourceful
(i.e., servers). The client-server architecture
traditionally utilized is different from this, in which
always a thin client migrates to a server computation.
There is a difference between the computation
offloading and the migration model which utilizes in
grid computing and multiprocessor system, where for
load balancing migrating the process [1-6]. The key
difference is that computation offloading differs
mainly when it migrates programs to servers outside
the computing environment of the immediate users;
typically migrating the process to grid computing
which occurs within computer in asimilar computing
environment, that is, the grid. In similar principle for
efforts is offloading like SETI@home [8], where for
computation performance sending request to
surrogates. The terms like “surrogate computing” and
“cyber foraging” are also utilized for describing
computation offloading.
Computation offloading[2-3, 6, 9] is growing topic
on which a significant amount of research has been
done which makes it feasible, making decisions of
International Journal of Computer Science and Information Security (IJCSIS),
Vol. 15, No. 8, August 2017
109 https://sites.google.com/site/ijcsis/
ISSN 1947-5500](https://image.slidesharecdn.com/14paper31071723ijcsiscamerareadypp-180202102259/75/Improve-the-Offloading-Decision-by-Adaptive-Partitioning-of-Task-for-Mobile-Cloud-Computing-1-2048.jpg)
![offloading, and developing infrastructures of
offloading. Most of the researches done over
offloading prior to 2000are on making it feasible.
Primarily, this is because of its limitations in wireless
networks, such as lesser bandwidths. The focus
shifted to developing algorithms utilized for making
offloading decisions in early 2000s that is,
decidingwhether mobile users are benefited by
offloading. The offloading direction is shifted with
the improvements in network bandwidths, cloud
computing infrastructures, and virtualization
technology. More practical has become computation
offloading with these developments.
On mobile systems, saving the energy and
performance improvement may be done by utilizing
computation offloading depending usuallyon various
parameters like as the data exchanged amounts
through various networks and network bandwidth.
Various algorithms have been proposed for making
the offloading decisions to save energy or improve
performance [10, 13, 15-16, 18]. Usually decisions
are made with the parameter analyzation including
server speeds, bandwidths, server loads, available
memory, and the data exchanged amount among
mobile systems and servers. In the execution
environment [11], application behavior variation of
predicted parametric and partitioning programs [15]
is included in the solutions.
Resourceful computers access is required in
offloading through networkswireless or wired for
short durations. Virtualization may be used by these
servers for providing offloading services so as
various programs and their data can be protected and
isolated. Protections and isolations have motivated
the researchers to developoffloading infrastructures at
different granularities [16]. Performing offloading
may be at the levels of tasks [9],methods [3], virtual
machines [5], or applications [11]. .NET remoting,
RPC (remote procedure call), and Java RMI are the
various mechanisms which enables offloading at the
object level and class level. At the virtual-machine
level, techniques have been proposed for offloading
enabling [8, 17]. The offloading and elastic resources
allowed by cloud computing for multiple servers;
which enables the computation offloading. Several
solutions and infrastructures and solutions have been
proposed to improve offloading: they deal with
various issues forprivacy, users, security, mobility,
etc.The goal is paper to improve the utilization of
computing resources and reduce energy consumption.
II. LITERATURE REVIEW
For the mobile codes execution on the remote server
suchas the wall-powered PCs or cloud, a technique
has been employed in previous work, called
offloading execution, which is the execution
transferring act between two machines run time. By
computational loads relieving, the labors technique
for bring benefits of smartphones in terms of
execution time and batteryin their proximityfrom the
servers. In offloadingexecution, two maintasks are
there which involves before the remote execution:
state migration and code partitioning. In recent years,
greater deal of research has been conducted there for
finding or supportingof distributed systems optimal
partitioning with mobile devices.The static
partitioning schemes are proposed [10] by several
researchers where the assigned jobin the system to
each machine at compile timeis fixed. More doable
ought to be the static partitioning if the resource
configurations computationallysuch as memory
capacity, processor speed, network characteristics,
and energy consumption, remain fairly constant as
process is launched. In mobile computing, however,
the change in configurations is possible due to user
mobility even in the process execution mid.
Therefore, in other works mostly [4], [5], [8], [11]
have been on the semi-dynamic or dynamic
partitioning schemes development to execute
offloading. In a partitioning schemedynamically,
annotated is the code commonly
withdirectivesdelimiting the code regions which can
be delegated for remote executionto the server, if
profitable? Which regions run on the server actuallyis
decided during the execution of code when for
execution the resource configurations areknown.
Finally, once certain region at run time is selected,
execution needs for current state tobe captured and
server migration with the control command in which
execution resumption is directed.In other approach
[5], the entire state including the existing stack is
included in entire state and migrated all
heapreachableobjects for offloading the full process.
In anotherapproach [4], the stack is not to be
migrated as the functions set to run remotely will be
newly invoked in the server. Clearly, these two
International Journal of Computer Science and Information Security (IJCSIS),
Vol. 15, No. 8, Augus 2017
110 https://sites.google.com/site/ijcsis/
ISSN 1947-5500](https://image.slidesharecdn.com/14paper31071723ijcsiscamerareadypp-180202102259/85/Improve-the-Offloading-Decision-by-Adaptive-Partitioning-of-Task-for-Mobile-Cloud-Computing-2-320.jpg)



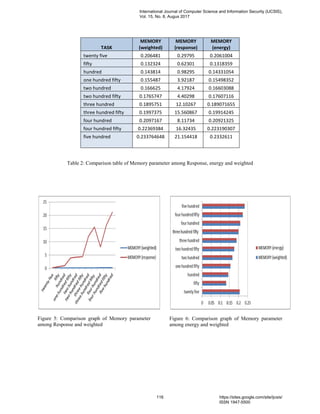
![Figure 7: Comparison graph of Memory parameter among Response and energy
VIII. CONCLUSION
Several solutions have been proposed to enhance the
CPU performance and to manage the disk and screen
in an intelligent manner to reduce power
consumption. However, these solutions require
changes in the structure of mobile devices, or they
require a new hardware that results in an increase of
cost and may not be feasible for all mobile devices.
By offloading the computational intensive part of the
application which requires less communication to the
rest of the application, to the cloud, a mobile device
can save significant amount of battery energy and
provide more responsive user experience. In this
thesis, we have presented a computation offloading
scheme on virtual devices. Our partition algorithm
finds optimal program partitioning for given program
input data. Experimental results show that our
computation offloading scheme can be significantly
improve the performance and energy consumption on
handheld devices.
IX. FUTURE SCOPE
Computation offloading technique is proposed with
the objective to offload the large computations and
complex processing from resource-limited devices
(i.e., mobile devices) to resourceful machines (i.e.,
servers in clouds). This helps in reducing the
application execution time and also power
consumption.
More work is needed to be done for offloading field.
Future work can be extended in the following fields:
Here, we use EM algorithm for optimal partition the
application running on Smartphone, in future we will
use metaheuristic algorithm, since metaheuristics are
one of the most practical approaches for solving hard
optimization problems. This approach is interesting
for very large problem instances. We will also take
our operations to hardware for better understanding
the calculate delay and memory usage.
REFERENCES
[1] Li Z,WangC,XuR,”Computation offloading to save energy on
handheld devices: a partition scheme”,InProceedings of the 2001
international conference onCompilers, architecture, and synthesis
for embeddedsystems (CASES),238–246,2001
[2] ChengWang and ZhiyuanLi,”A computation offloading scheme
on handheld devices”, Journal of Parallel and Distributed
Computing, 2003
[3] Karthik Kumar and Yung-Hsiang Lu,“Cloud computing for
mobile users: Can offloading computation save
energy?”,Computer, vol. 43, no. 4, pp. 51–56,IEEE 2010
[4] S. Kosta, A. Aucinas, P. Hui, R. Mortier, and X. Zhang,
“Thinkair: Dynamic resource allocation and parallel execution in
the cloud for mobile code offloading.” in Proc. IEEE INFOCOM
2012
International Journal of Computer Science and Information Security (IJCSIS),
Vol. 15, No. 8, Augus 2017
117 https://sites.google.com/site/ijcsis/
ISSN 1947-5500](https://image.slidesharecdn.com/14paper31071723ijcsiscamerareadypp-180202102259/85/Improve-the-Offloading-Decision-by-Adaptive-Partitioning-of-Task-for-Mobile-Cloud-Computing-9-320.jpg)
![[5] J.Lei, F.Roy, FU.Xiaoming, S.Stefano, S. Zbigniew and T.
Hannes,”Cloud-based Computation Offloading forMobile Devices:
State of the Art, Challenges and Opportunities”,Future Network
and Mobile Summit Conference Proceedings, IIMC,2013
[6] SokolKosta. Alessandro Mei, JulindaStefa,”To offload or not to
offload? The bandwidth and energy costs of mobile cloud
computing”, INFOCOM, Proceedings IEEE 2013
[7] Huber Flores, SatishNarayanaSrirama,
RajkumarBuyya,”Computational Offloading or Data Binding?
Bridging the Cloud Infrastructure to the Proximity of the Mobile
User”IEEE,2014
[8] Roopali, Rajkumari,”Overview of Offloading in Smart Mobile
Devices for Mobile Cloud Computing”,Vol 5, Number 6, 2014
[9] Jaya Ashok Suradkar and R. D. Bharati, “Computation
Offloading: Overview, Frameworks and Challenges” International
Journal of Computer Applications Volume 134 – No.6, January
2016
[10] KarthikKumar·JibangLiu·Yung-Hsiang Lu· Bharat
Bhargava,”A Survey of Computation Offloading for Mobile
Systems”, Springer Issue on Mobile Network Application,10 April,
2012.
[11] Monika Dudeja and KritikaSoni,” Offloading Schemes in
Mobile Cloud” International Journal of Computer Applications
Volume 96– No.8, June 2014
[12] Xu Chen,” Decentralized Computation Offloading Game For
Mobile Cloud Computing”, IEEE 2015
[13] Chung.J, Park.Y, Park.J, and Cho.H,”Adaptive Cloud
Offloading of Augmented Reality Applications on Smart Devices
for Minimum Energy Consumption”,Ksii Transactions On Internet
And Information Systems VOL. 9, NO. 8, 31 August 2015
[14] D. Murali, J. Vamsinath,”Cloud Computing For Mobile
Users: Be Capable of Offloading Computation save Energy?”,
International Journal of Advanced Research in Computer Science
and Software Engineering, Volume 4, Issue 9, September 2014
[15] Ying-Dar Lin, Chu, E.T.-H., Yuan-Cheng Lai and Ting-Jun
Huang, "Time-and-Energy-Aware Computation Offloading in
Handheld Devices to Coprocessors and Clouds," in Systems
Journal, IEEE , vol.9, no.2, pp.393-405, June 2015.
[16] R. Kemp, N. Palmer, and T. Kielmann, “Cuckoo: A
computation offloading framework for smartphones,” presented at
the Proc. 2nd Int. Conf. Mobile Comput., Appl., Serv., Santa Clara,
CA, USA, 2010.
[17] Kaushik. N, Kumar. J,”A Computation Offloading
Framework to Optimize Energy Utilisation in Mobile Cloud
Computing Environment”, International Journal of Computer
Applications & Information Technology Vol. 5, Issue II April May
2014
[18] S.Rathnapriya, S. Sumithra,” Techniques to Minimize State
Transfer Cost for Dynamic Execution Offloading In Mobile Cloud
Computing”, Int. Journal of Engineering Research and
Applications, Vol. 5, Issue 5, ( Part -5), pp.32-35, May 2015
AUTHORS PROFILE
Neha Goswami, Student of ME(maters of engineering in CSE) at
Chandigarh University.
Er. Sugandha Sharma, Assistant Professor at Chandigarh
university.
International Journal of Computer Science and Information Security (IJCSIS),
Vol. 15, No. 8, Augus 2017
118 https://sites.google.com/site/ijcsis/
ISSN 1947-5500](https://image.slidesharecdn.com/14paper31071723ijcsiscamerareadypp-180202102259/85/Improve-the-Offloading-Decision-by-Adaptive-Partitioning-of-Task-for-Mobile-Cloud-Computing-10-320.jpg)