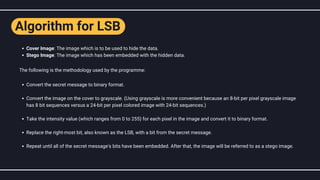
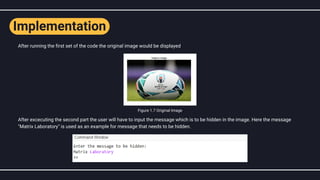
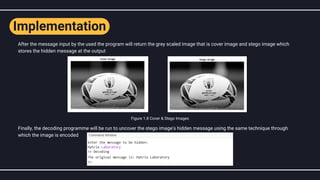
The document discusses steganography, particularly image steganography, which is the technique of hiding messages within digital images to ensure secrecy. It explains the least significant bit (LSB) method for embedding secret messages within pixel values while maintaining image quality, and provides a step-by-step implementation approach. The text also covers the applications, advantages, and disadvantages of image steganography in fields such as cyber forensics and data protection.




![[(225),(155),(99),(15),(155),(63),(1),(99),(219),(69),(18),(25)]
[(224),(154),(99),(14),(154),(63),(1),(99,(219),(69),(18),(25)]
How LSB technique works ?
Each pixel has an associated value that represents grey scale values ranging from 0 to 255, or 8-bit values.
Let's look at an example of how this technique works. Let's say we want to conceal the message "hi" in a 44 image with the
following pixel values:
Using the ASCII Table, we can convert the secret message into decimal
values and then into binary: 01101000110101. Now we convert each pixel
value to binary and replace each least significant bit with the message bits
in order (for example, 225 is 11100001, and we replace the last bit with the
first data bit(0), and so on). The pixel values will only change by +1 or -1,
which will be barely noticeable.
here is the changed pixel values they will have a minimal effect on image
Cover Image
Cover Image
Text
Stego Image
Text
Encryption Algorithm
Encryption Algorithm
Figure 1.4 Working of LSB](https://image.slidesharecdn.com/communicationsystemsppt-220512093825-1b6249df/85/Image-Steganography-using-MATLAB-5-320.jpg)