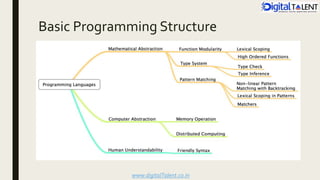
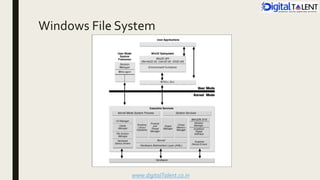
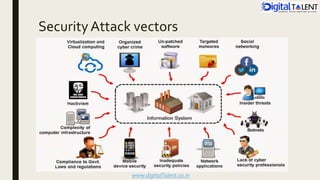
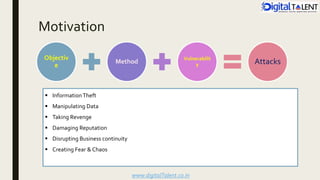
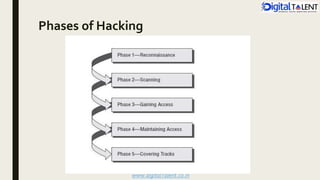
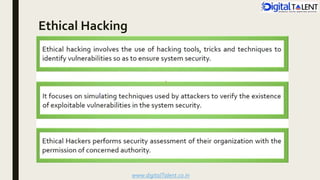
The document outlines the fundamentals of ethical hacking, emphasizing its role in network security by preparing individuals to think like malicious hackers in order to defend against them. It details the various types of hackers, the motivations behind hacking, and the phases of ethical hacking including planning, executing, and reporting. Additionally, it discusses why organizations recruit ethical hackers to identify vulnerabilities and improve security measures.