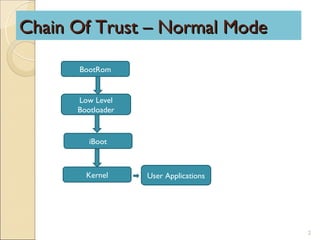
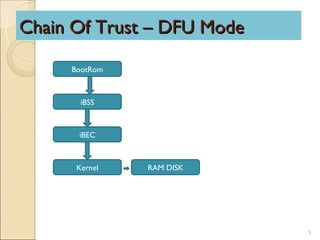
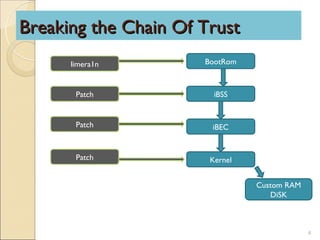
iPhone forensics involves bypassing an iPhone's passcode restrictions, reading its encrypted file system, and recovering deleted files. This is done by creating a forensic toolkit on the device without damaging evidence, establishing communication between the device and computer, and patching the iPhone's chain of trust from the BootRom to kernel. References provide more information on the iPhone's data protection and tools for forensic investigation.