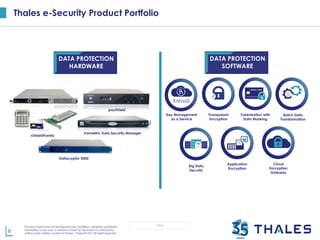
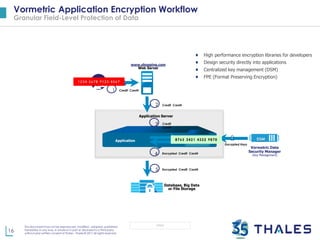
The document outlines Thales e-Security's Partner Program aimed at enhancing data security for customers, particularly in cloud environments. It emphasizes the need for comprehensive security solutions to protect against data breaches and compliance challenges while promoting partnerships with leading technology providers. The program offers a range of tools and solutions, such as encryption and key management, to facilitate secure digital transformation for enterprises.