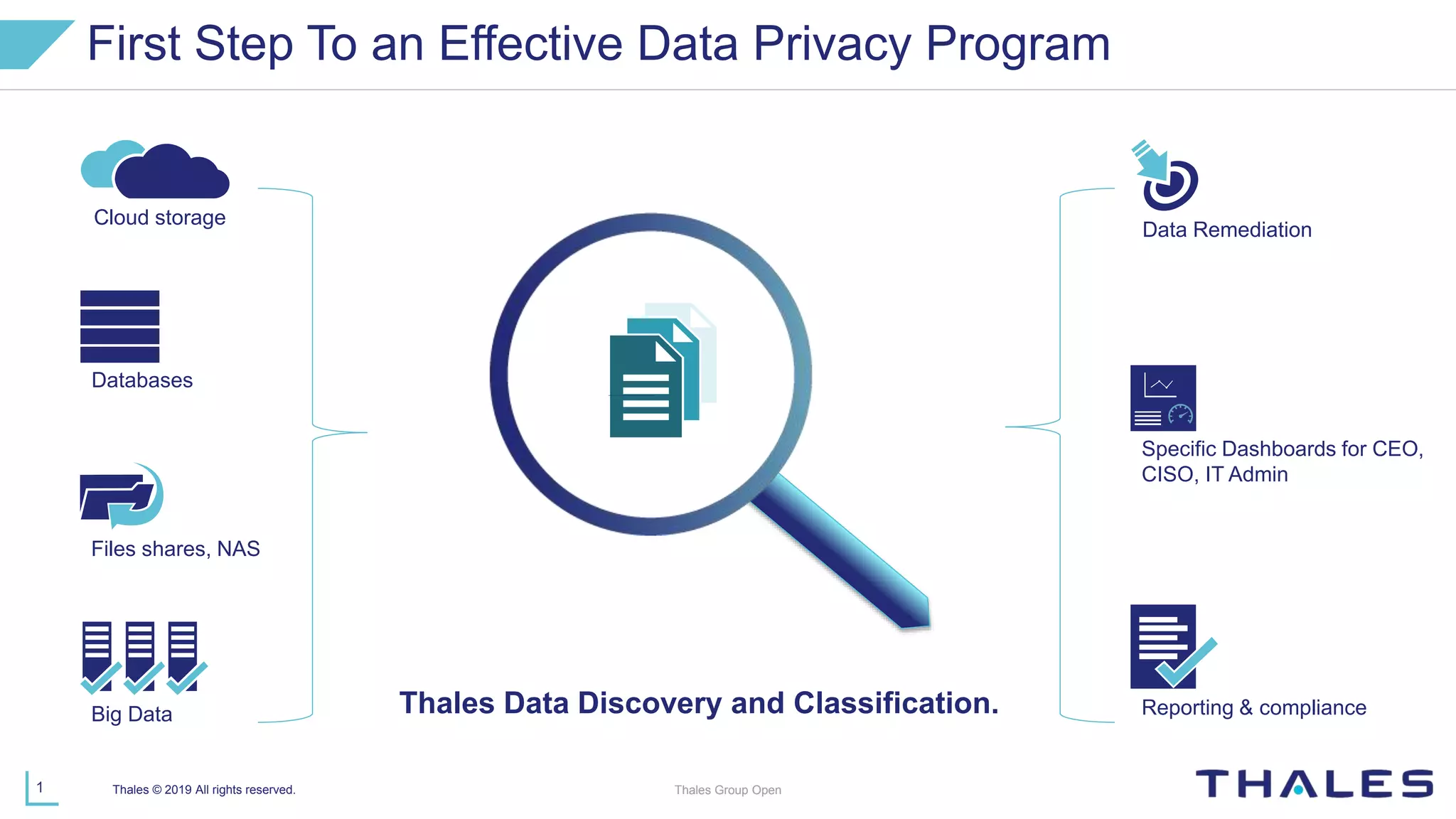
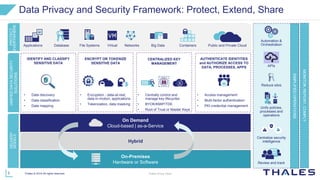
Thales provides data privacy and security solutions to help organizations protect sensitive data everywhere, including in networks, virtual applications, databases, big data, and file systems. Their framework focuses on monitoring, reporting and compliance; protecting data through encryption, tokenization, and centralized key management; and extending security through identity management and access control. Thales offers delivery models including on-premises, cloud-based, and hybrid options to suit different customer needs.