1. The document provides an overview of best practices for implementing enterprise-wide data encryption and protection. It discusses challenges like explosive data growth, evolving compliance requirements, operational complexity, and increasing threats.
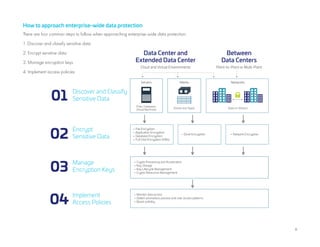
2. The document recommends a data-centric security approach that applies protection to data itself regardless of location. This includes discovering and classifying sensitive data, encrypting data in motion and at rest, and centralized key and policy management.
3. Effective data security requires discovering where sensitive data resides, encrypting that data, managing encryption keys centrally, and implementing access policies to control data use.