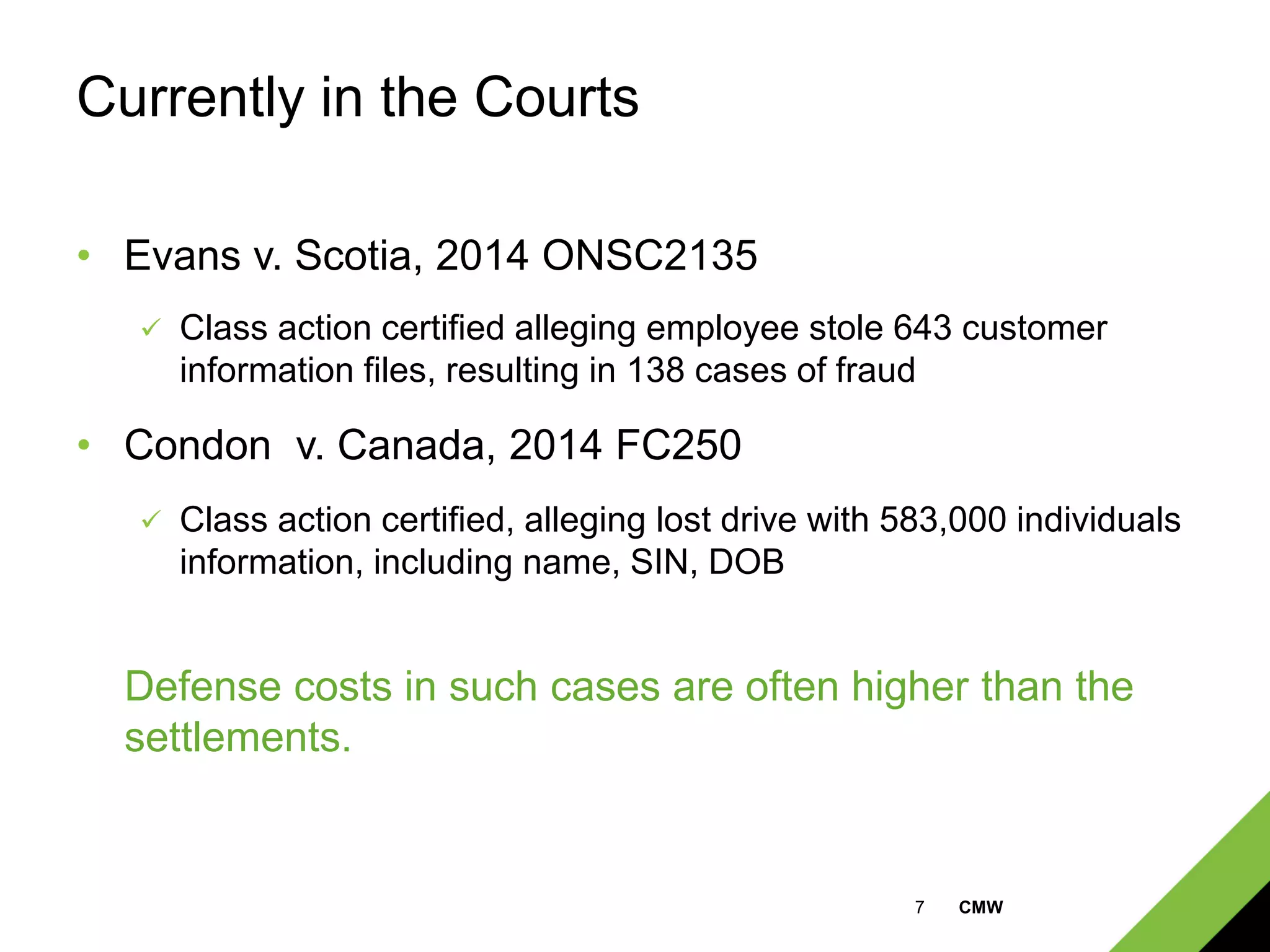
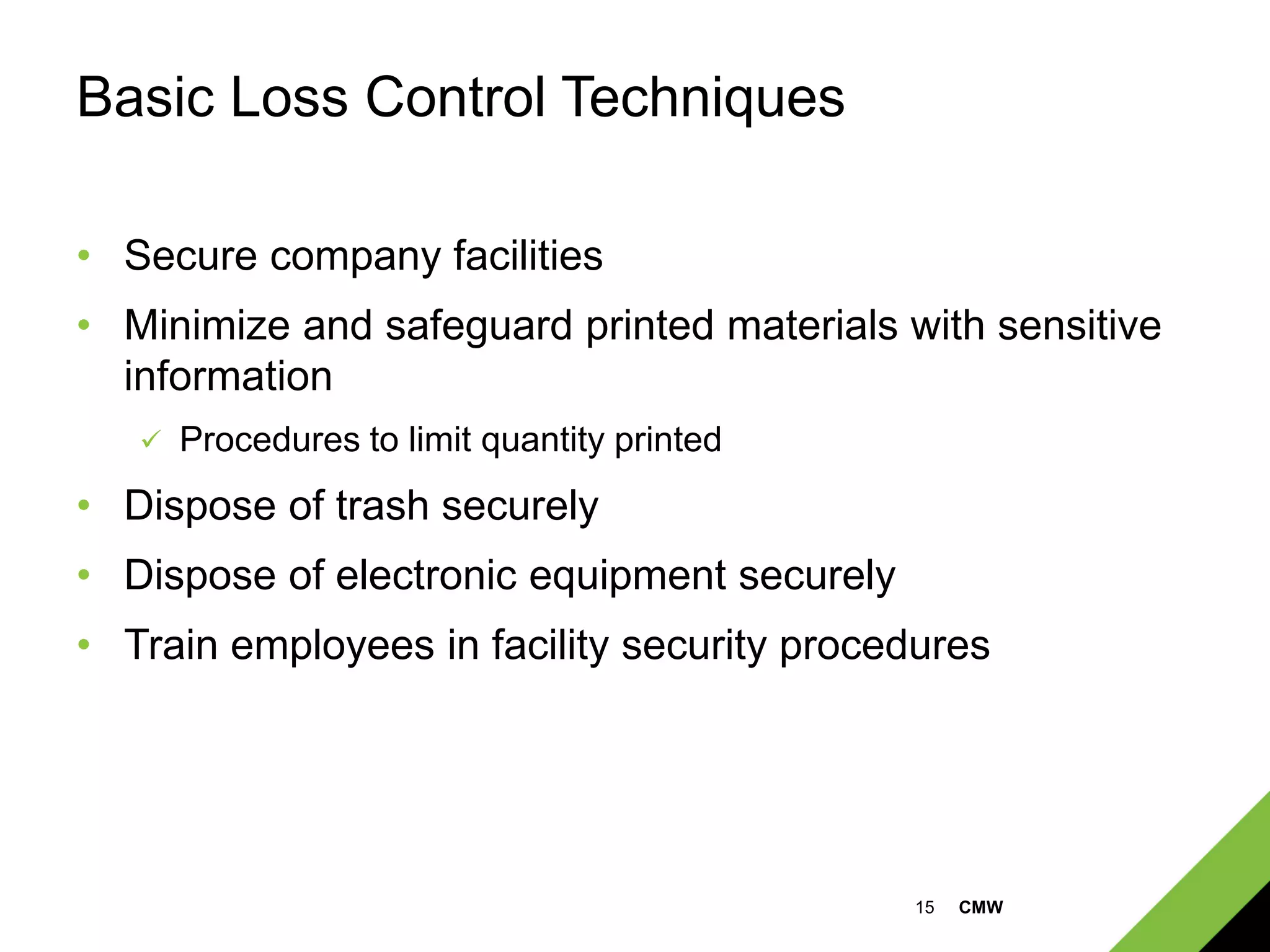
This document discusses cyber risks and cyber liability insurance. It summarizes that many major companies have experienced data breaches in recent years. It outlines common cyber risks like computer intrusions, loss of physical devices, and social media issues. It recommends basic loss control techniques and identifies what cyber liability insurance can cover, such as first and third party losses from network security breaches, privacy breaches, and internet media liability. Coverage limits start at $100,000 with premiums as low as $250.