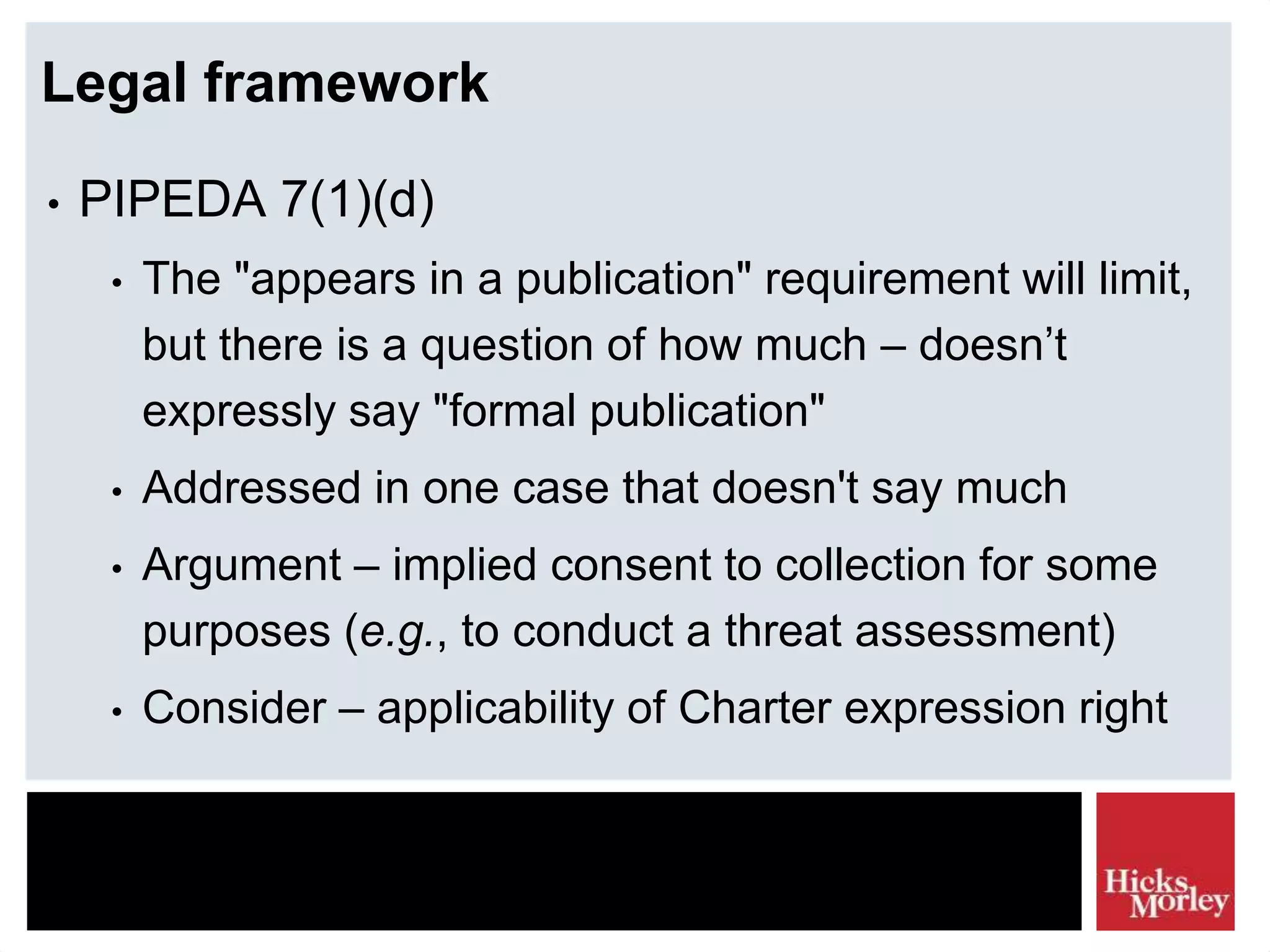
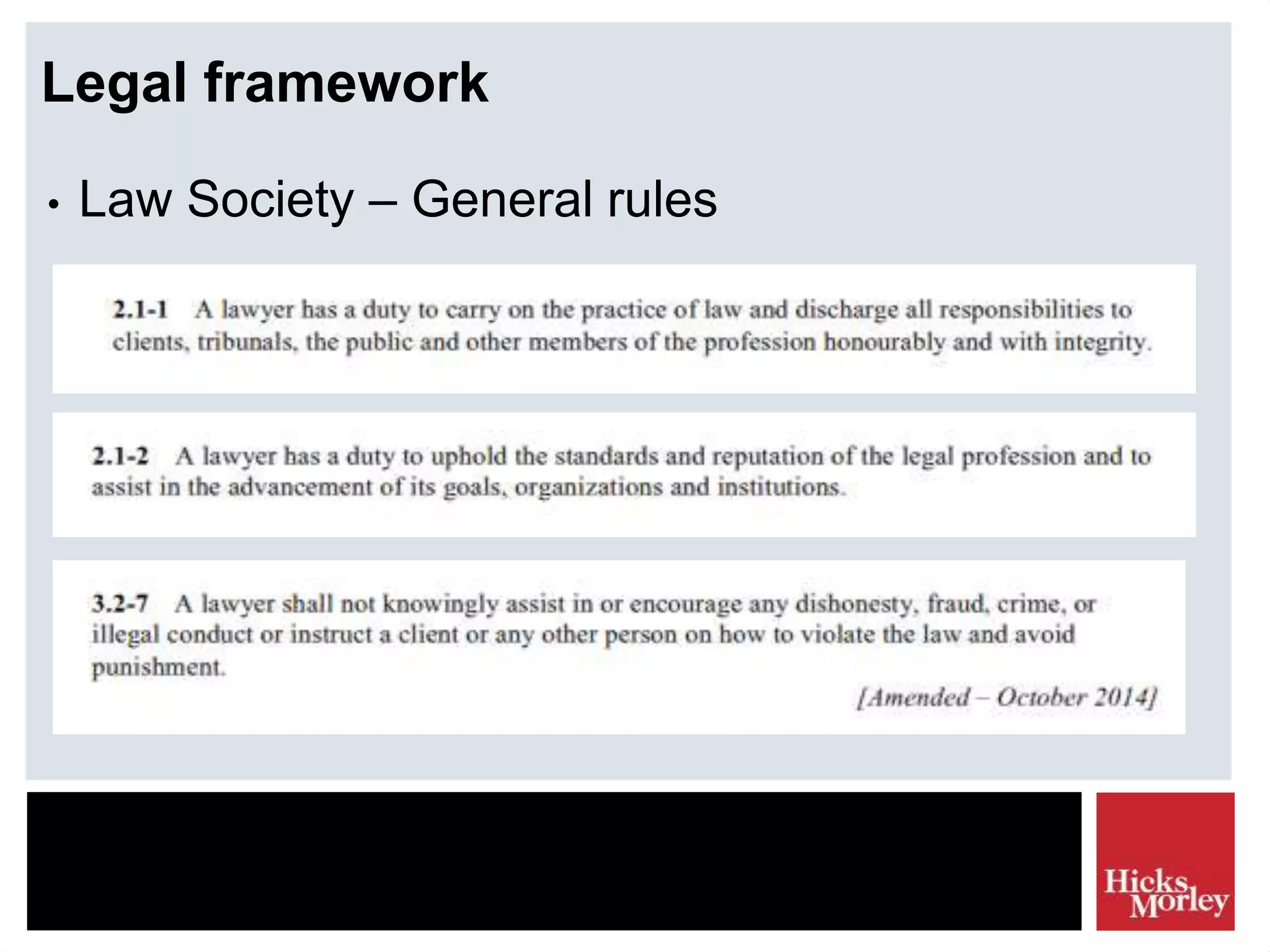
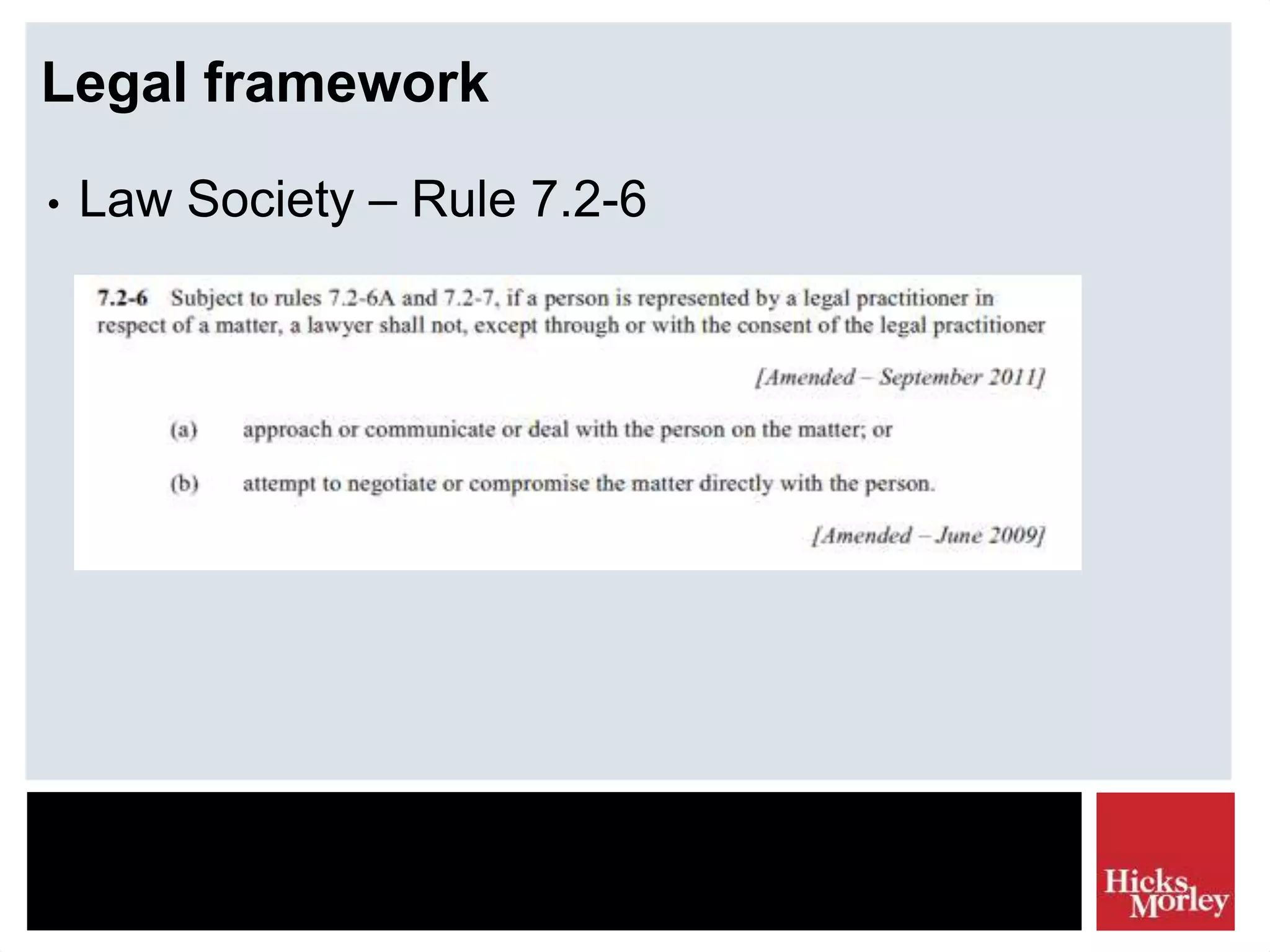
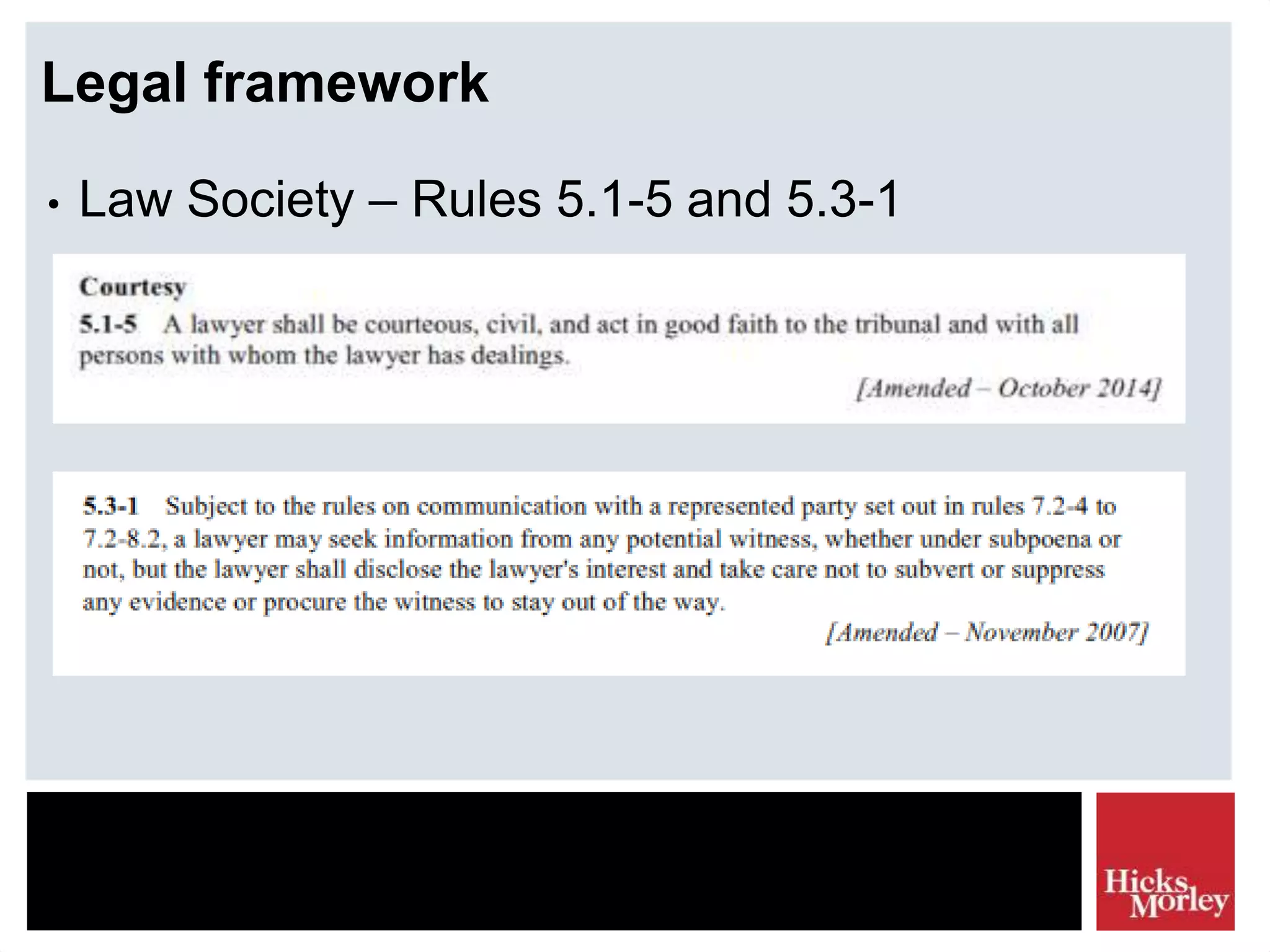
The document discusses the legal framework and tactics involved in using the internet as a corporate security resource, focusing on privacy laws such as PIPEDA and investigation tactics like background checks and intelligence gathering. It emphasizes the importance of balancing privacy rights with corporate investigation needs, outlining various tactics and their associated risk scores. Additionally, it highlights the need for ethical considerations and legal compliance in information collection processes.