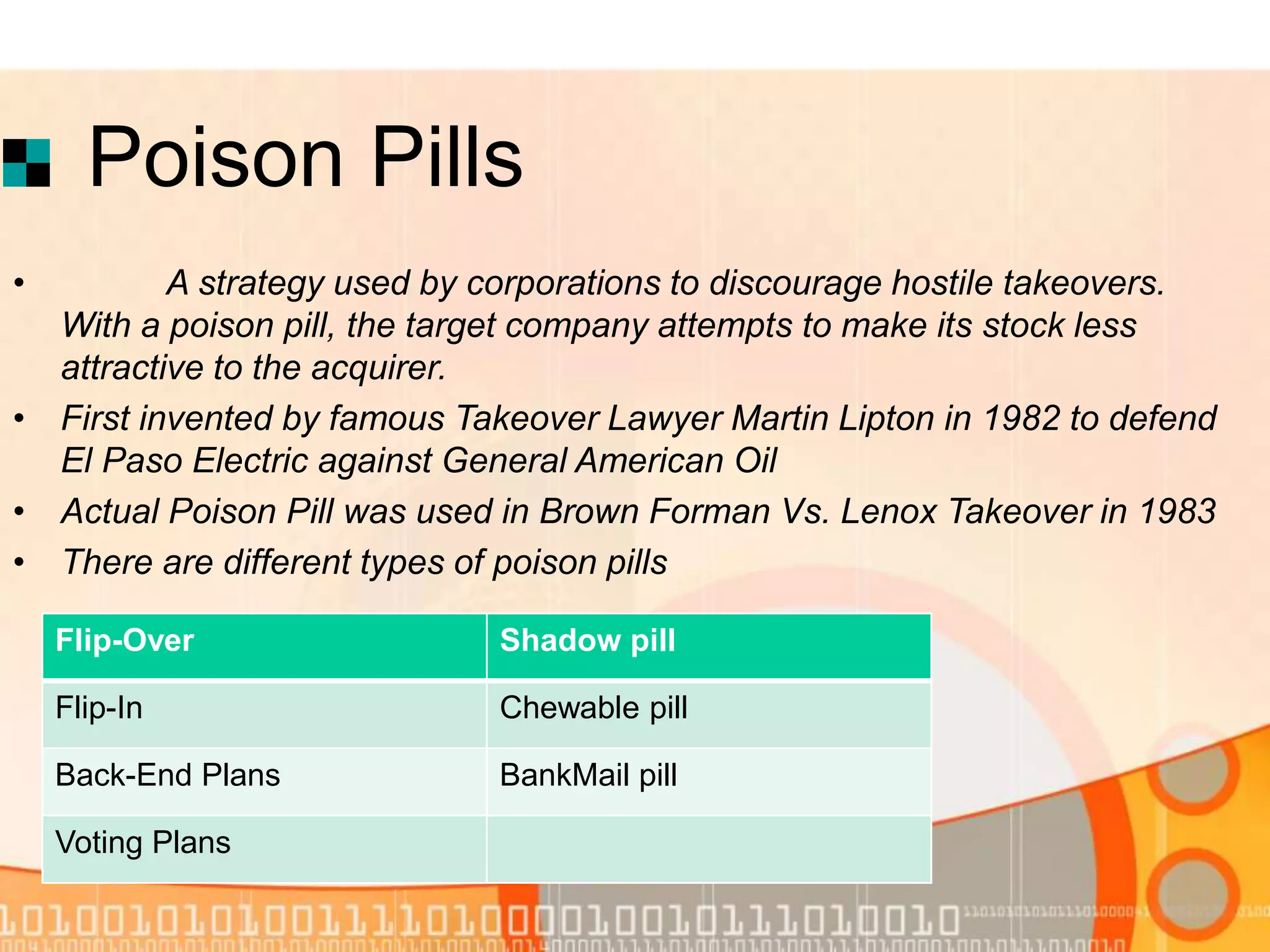
The document provides a comprehensive overview of hostile takeover defenses, detailing types of takeovers, strategies employed by companies to prevent or respond to hostile bids, such as preventive and active defenses. It explains various methods including poison pills, greenmail, and proxy fights, along with specific techniques like the 'white knight' and 'pac-man defenses.' Additionally, the document delves into mechanisms like golden parachutes and corporate charter amendments that serve to thwart hostile takeovers while maintaining company integrity.