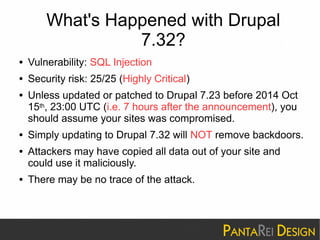
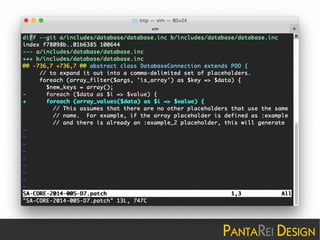
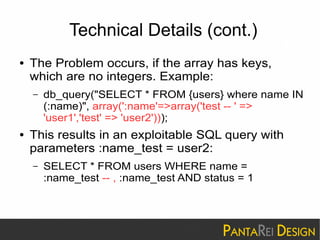
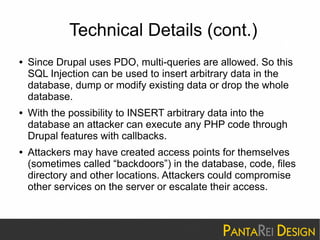
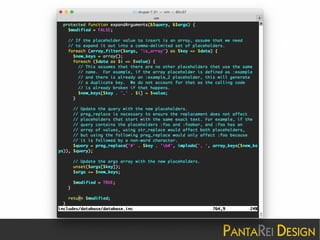
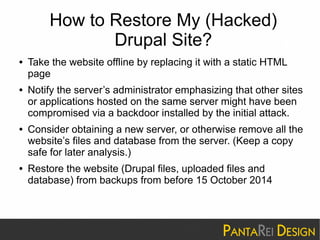
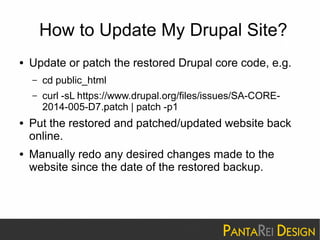
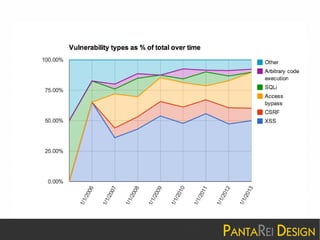
This document discusses a SQL injection vulnerability in Drupal 7.32 that allowed attackers to compromise Drupal sites. It provides technical details on the vulnerability and advises site owners to restore from backups before October 15, 2014 or assume their sites were hacked. The document also provides tips on updating Drupal, checking for backdoors, and improving security going forward.