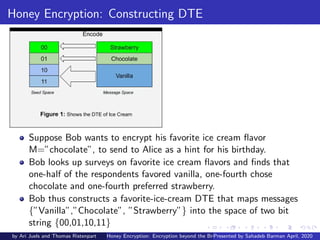
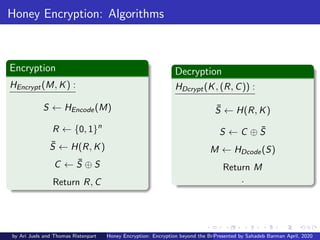
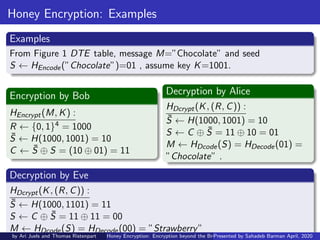
This document discusses honey encryption, a technique created by Ari Juels and Thomas Ristenpart in 2014. Honey encryption aims to protect encrypted data from brute force attacks by generating plausible-looking but incorrect plaintext when an incorrect encryption key is used. It uses distribution-transforming encoders to map messages to seed values based on statistical message distributions. When encrypting data, honey encryption algorithms generate random values and use hash functions with the encryption key to conceal the real encryption. This makes it difficult for attackers to determine if they have correctly guessed encryption keys.