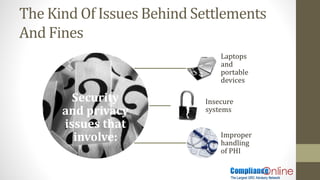
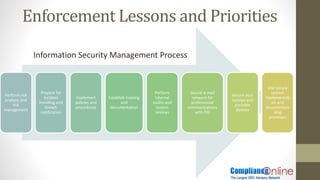
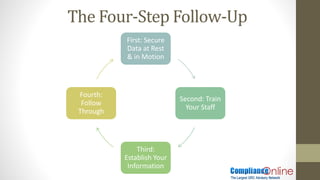
The document outlines significant HIPAA enforcement examples, highlighting substantial fines and settlements for various violations, including mishandling of personal health information (PHI) and lack of security measures. It emphasizes the importance of rigorous compliance, including conducting risk analyses, implementing proper policies, and maintaining staff training to avoid costly breaches. Additionally, it suggests proactive measures to ensure data security and the adherence to HIPAA regulations to mitigate risks and potential penalties.