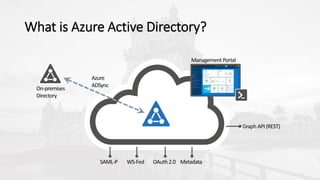
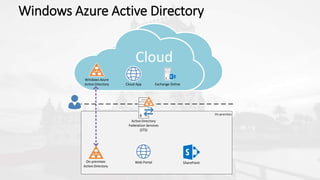
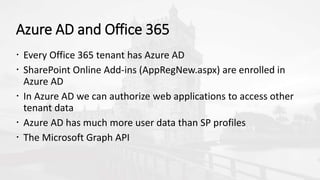
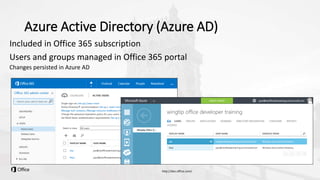
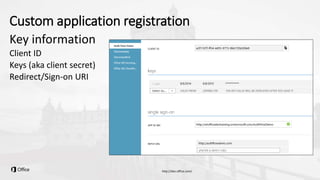
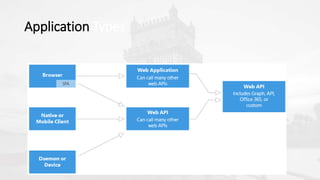
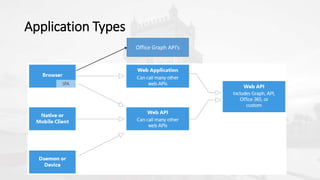
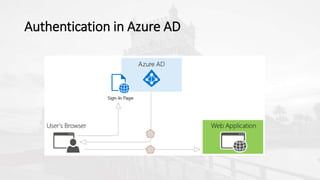
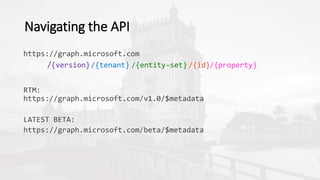
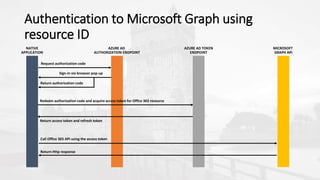
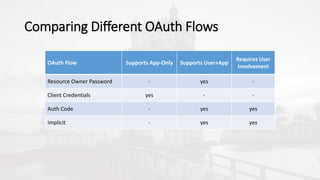
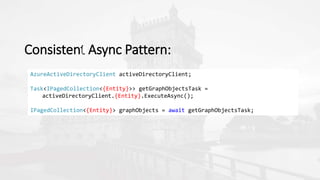
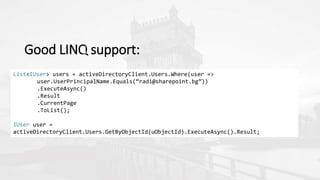
The document outlines a presentation on developing applications using Azure Active Directory (Azure AD) and Microsoft Graph API, highlighting features like OAuth 2.0 authentication, app registration, and integration with Angular and TypeScript. It covers essential tools needed for development, including Visual Studio and the Azure subscription, as well as a comparison of Application types in Office 365 versus SharePoint. Key takeaways include the benefits of Azure AD, Graph client libraries, and the importance of modern development techniques in building scalable applications.