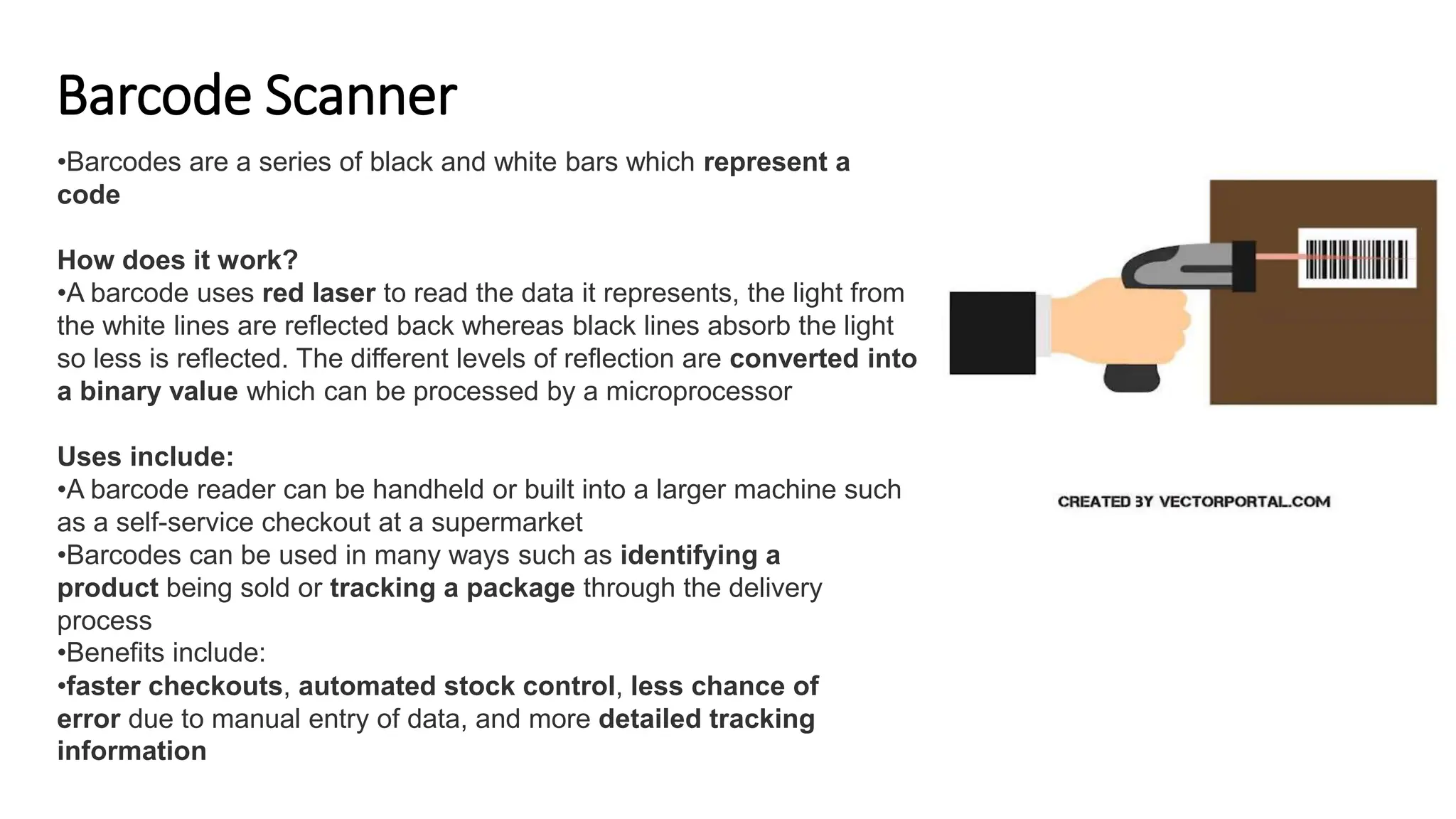
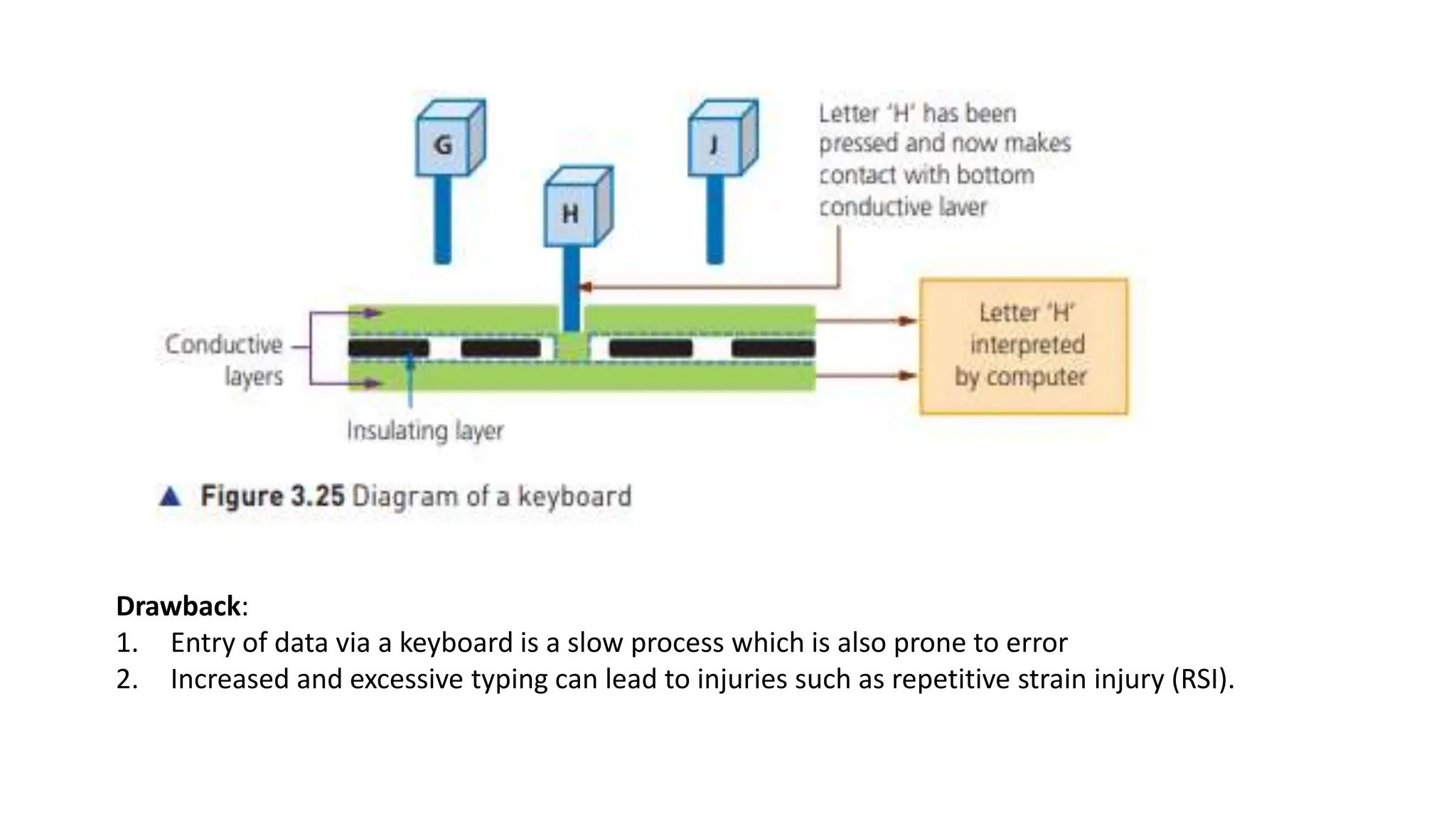
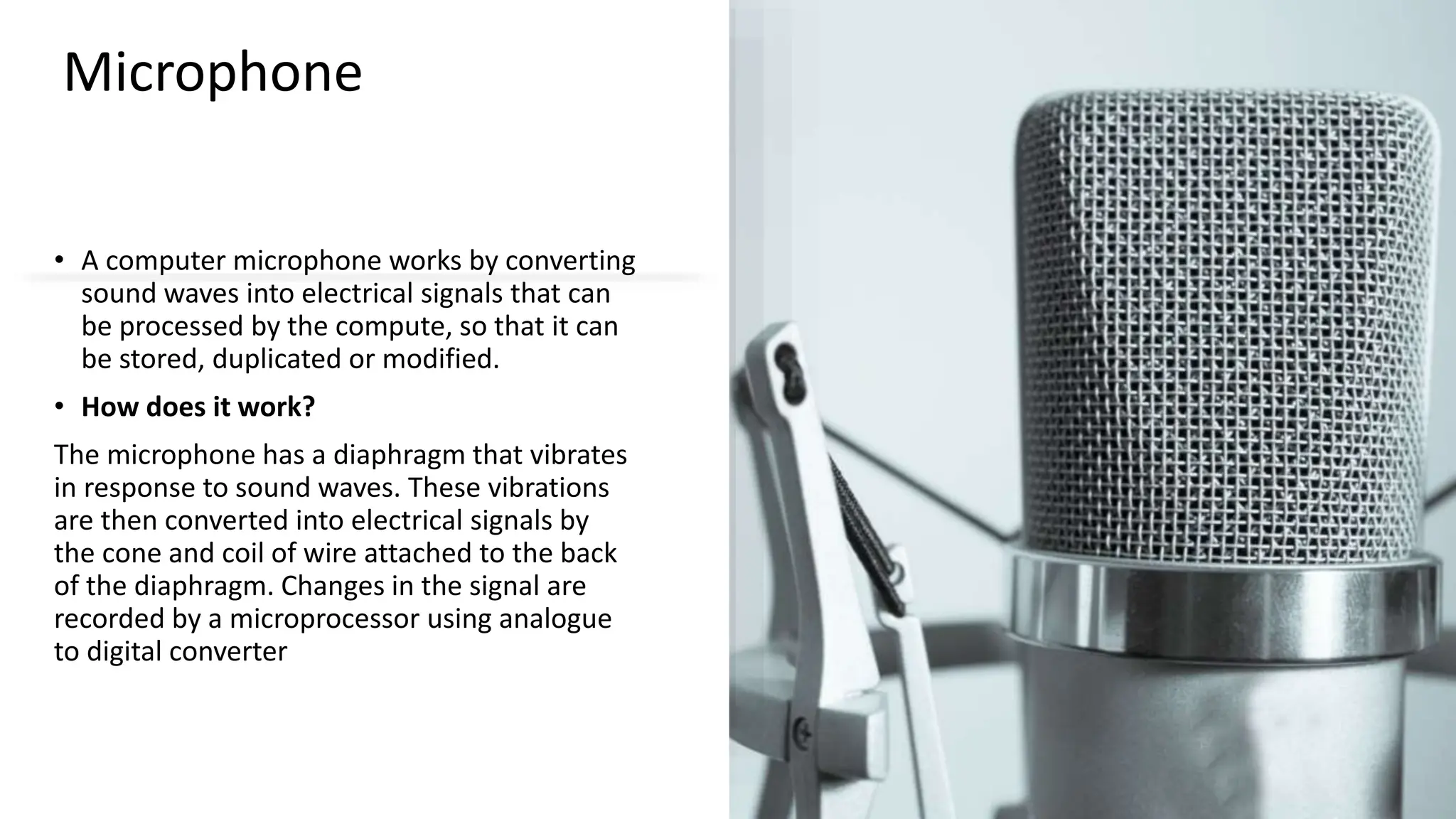
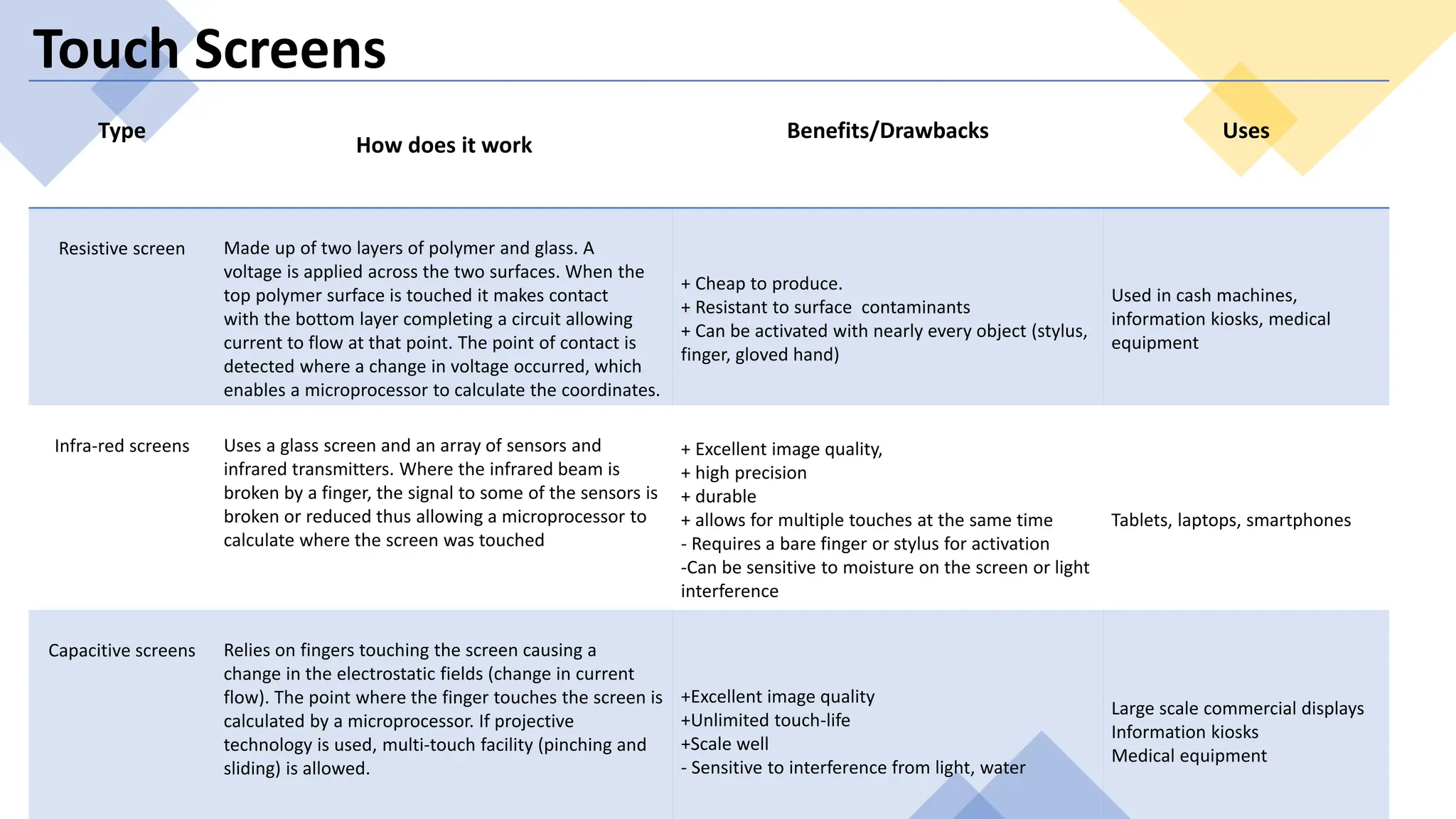
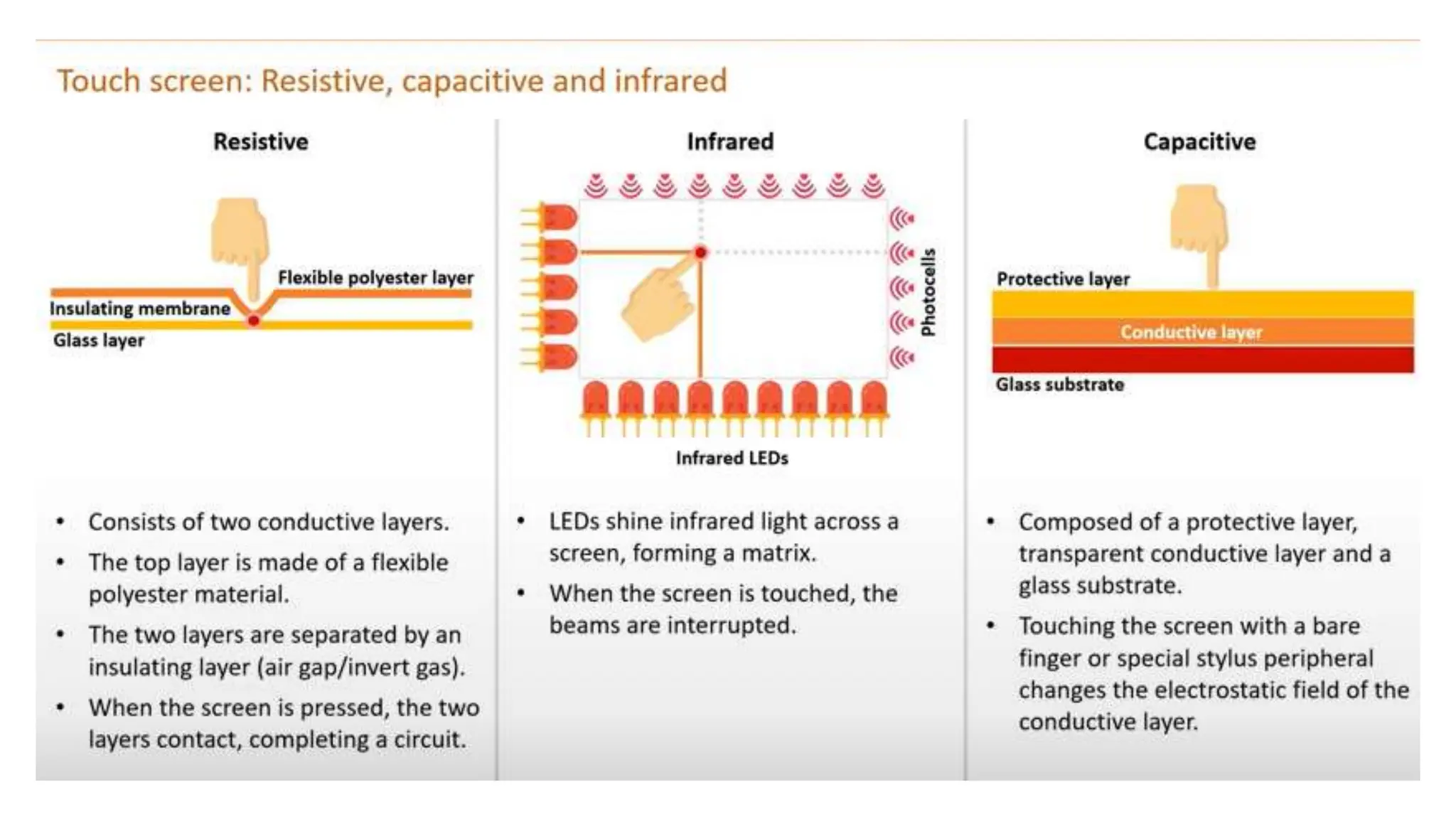
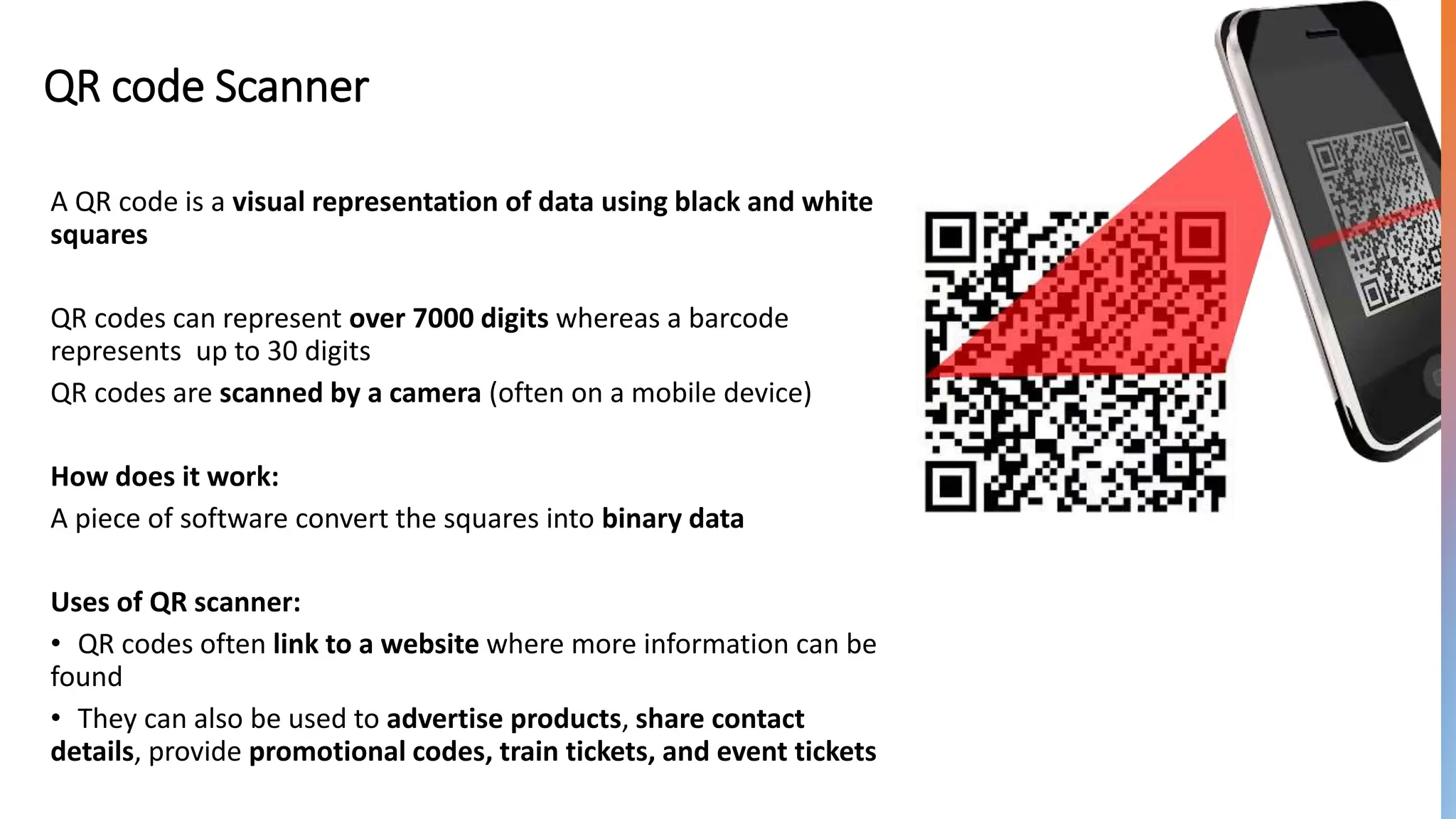
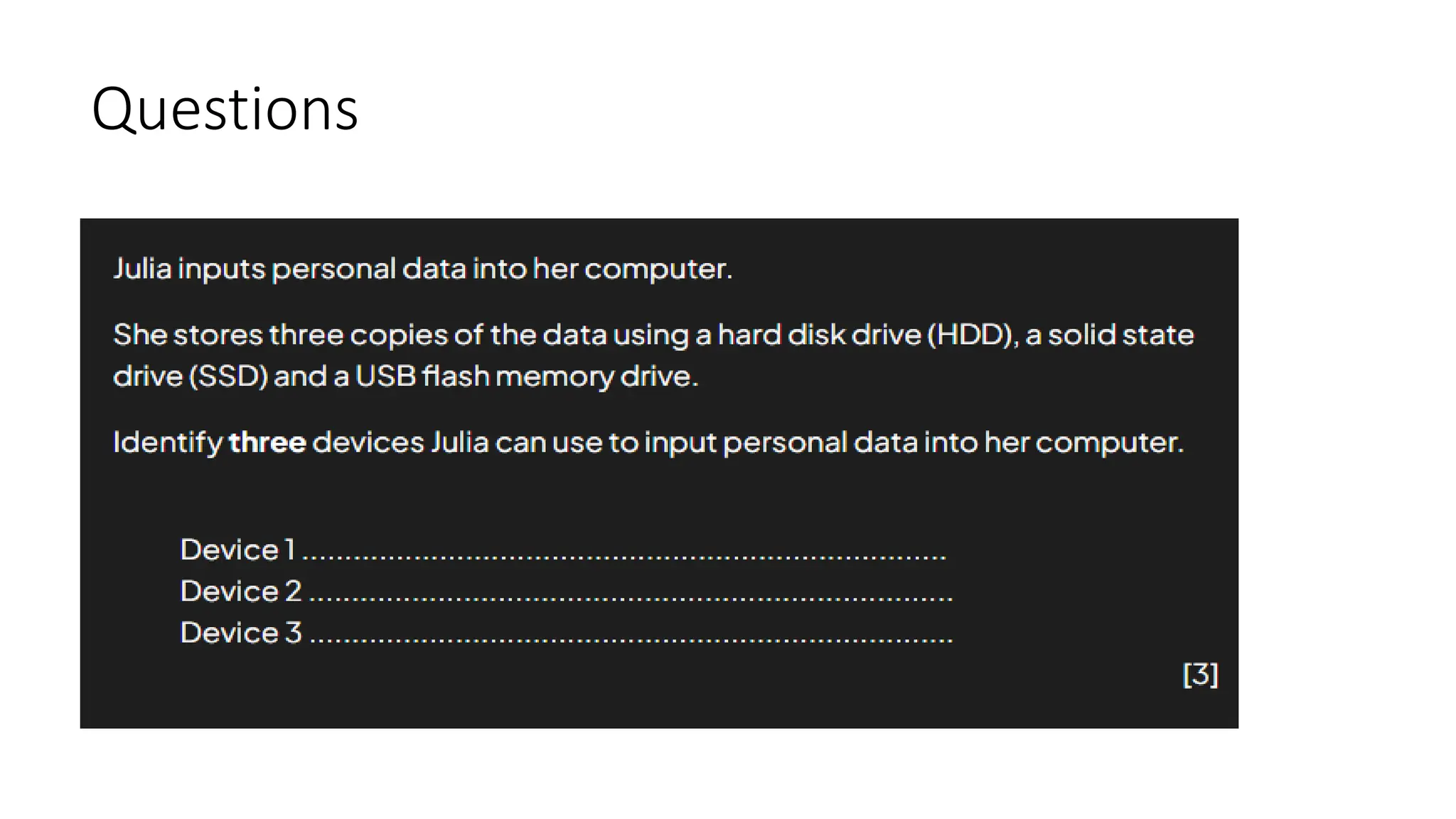
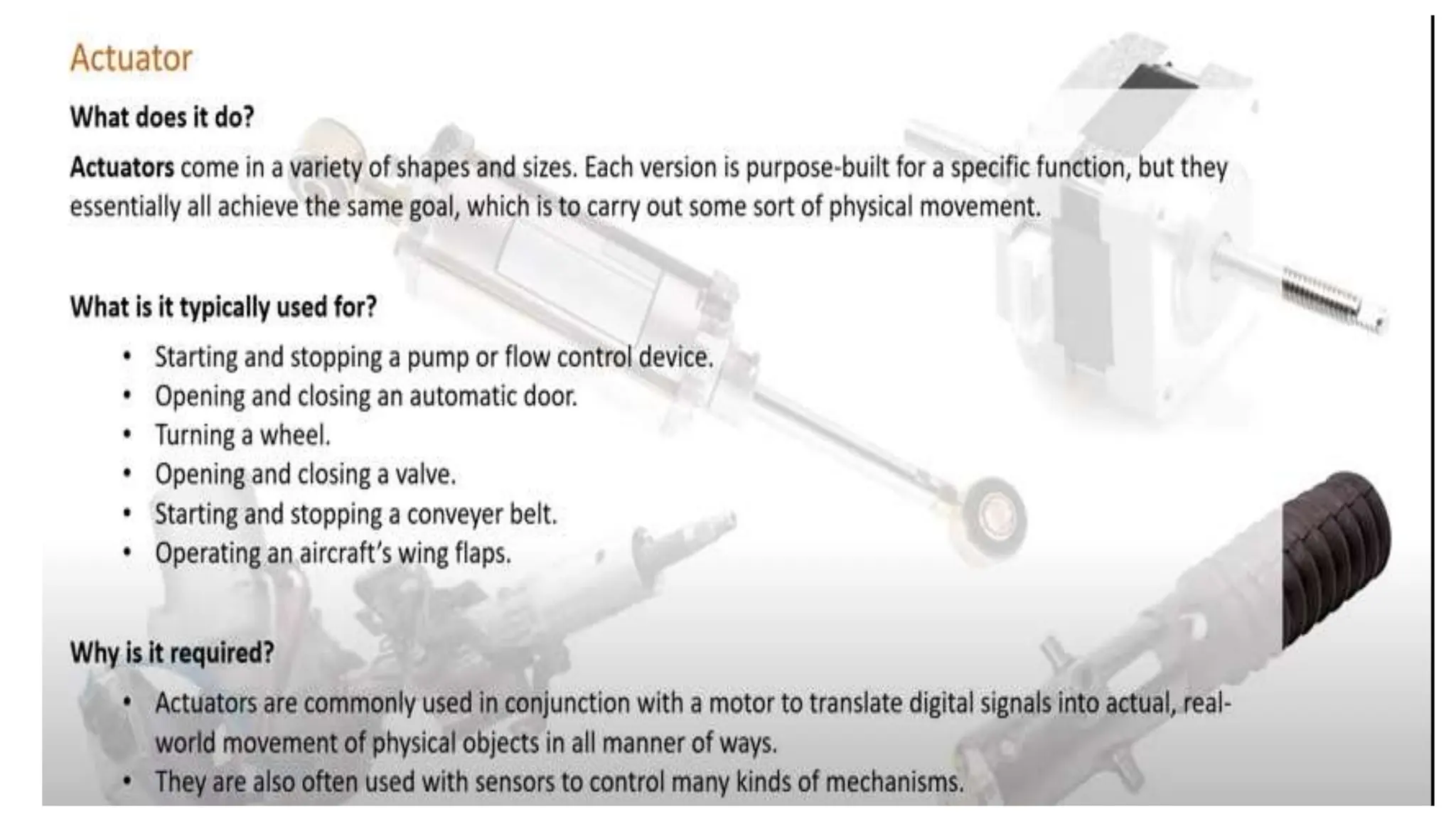
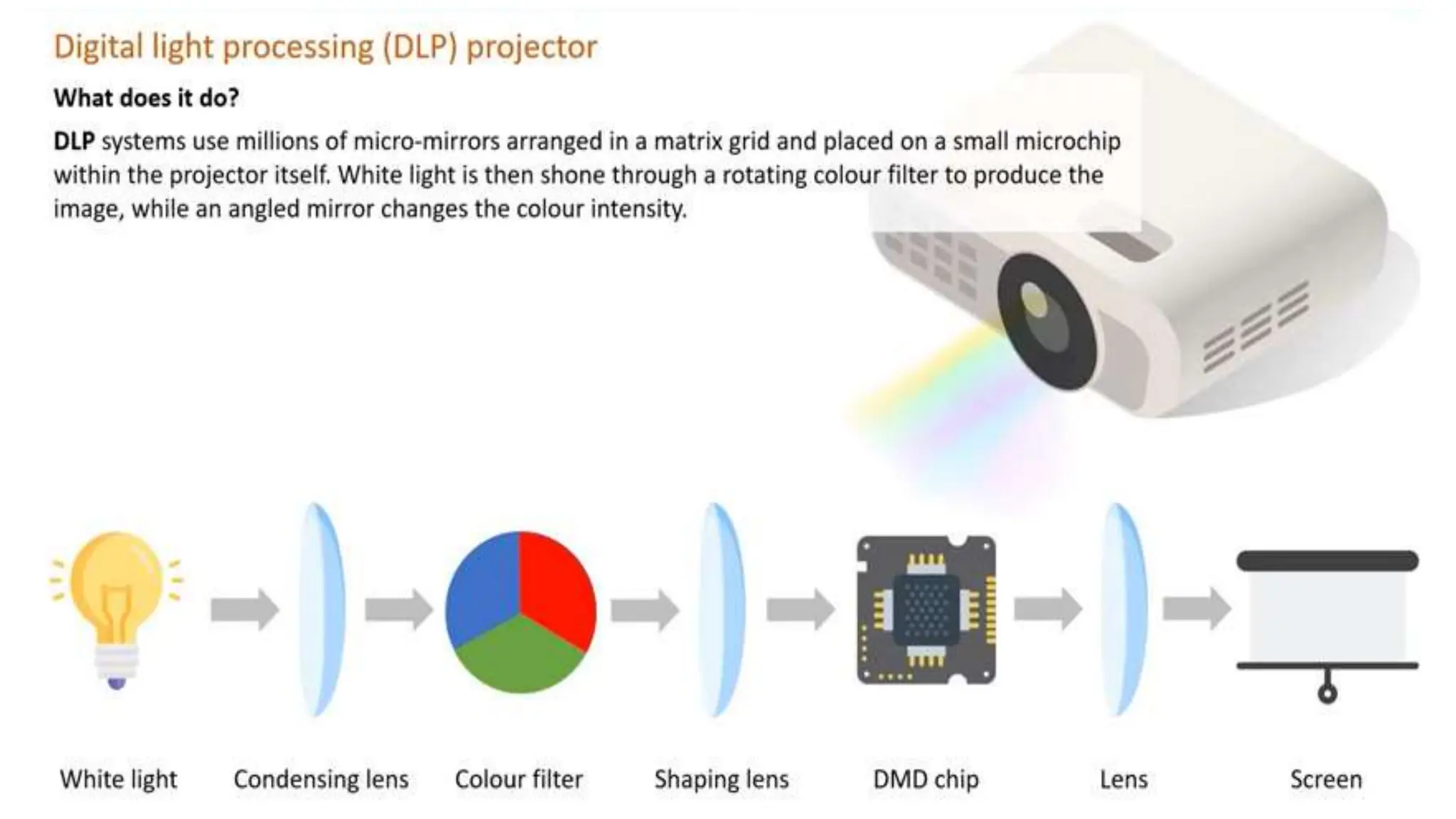
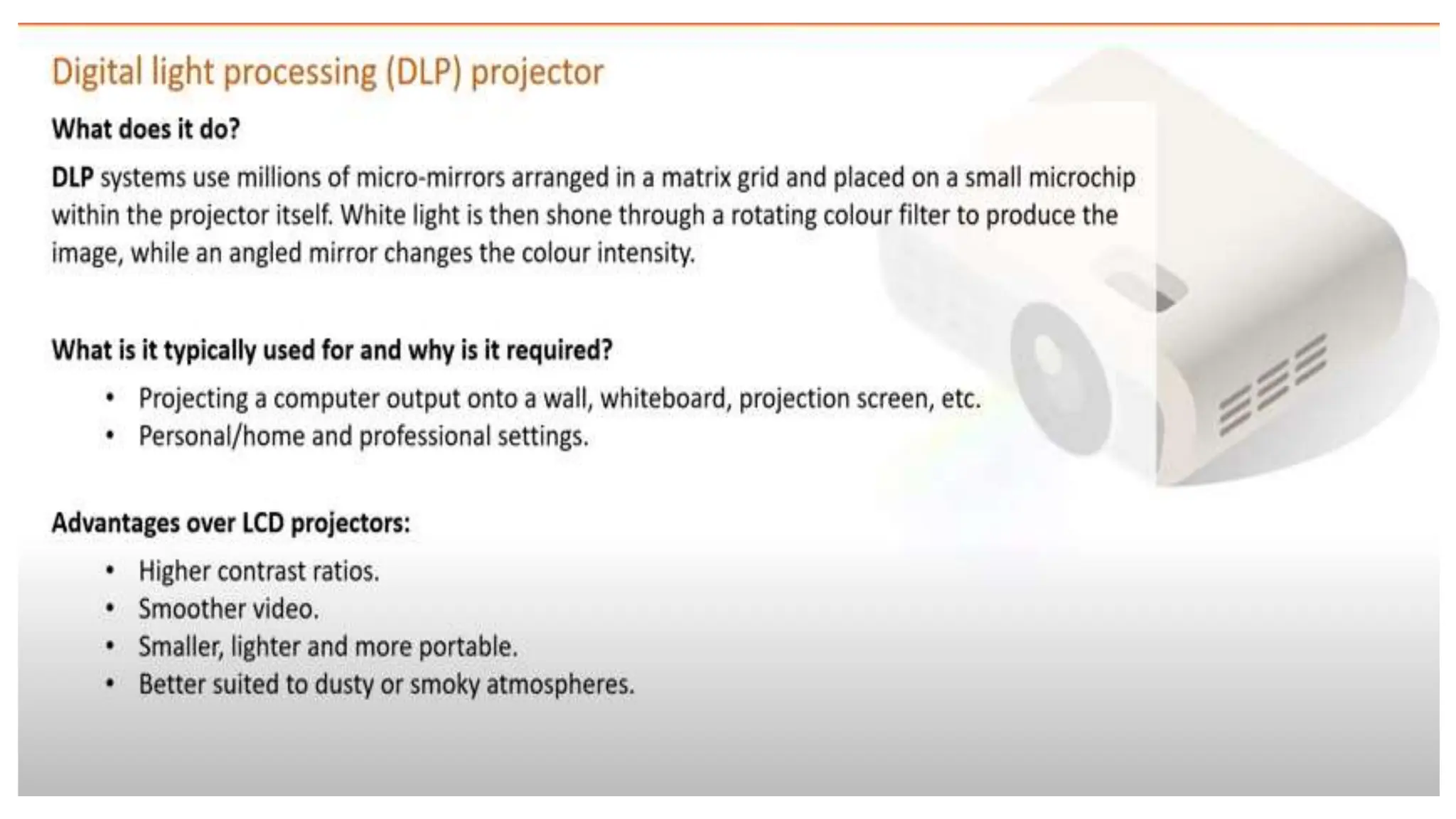
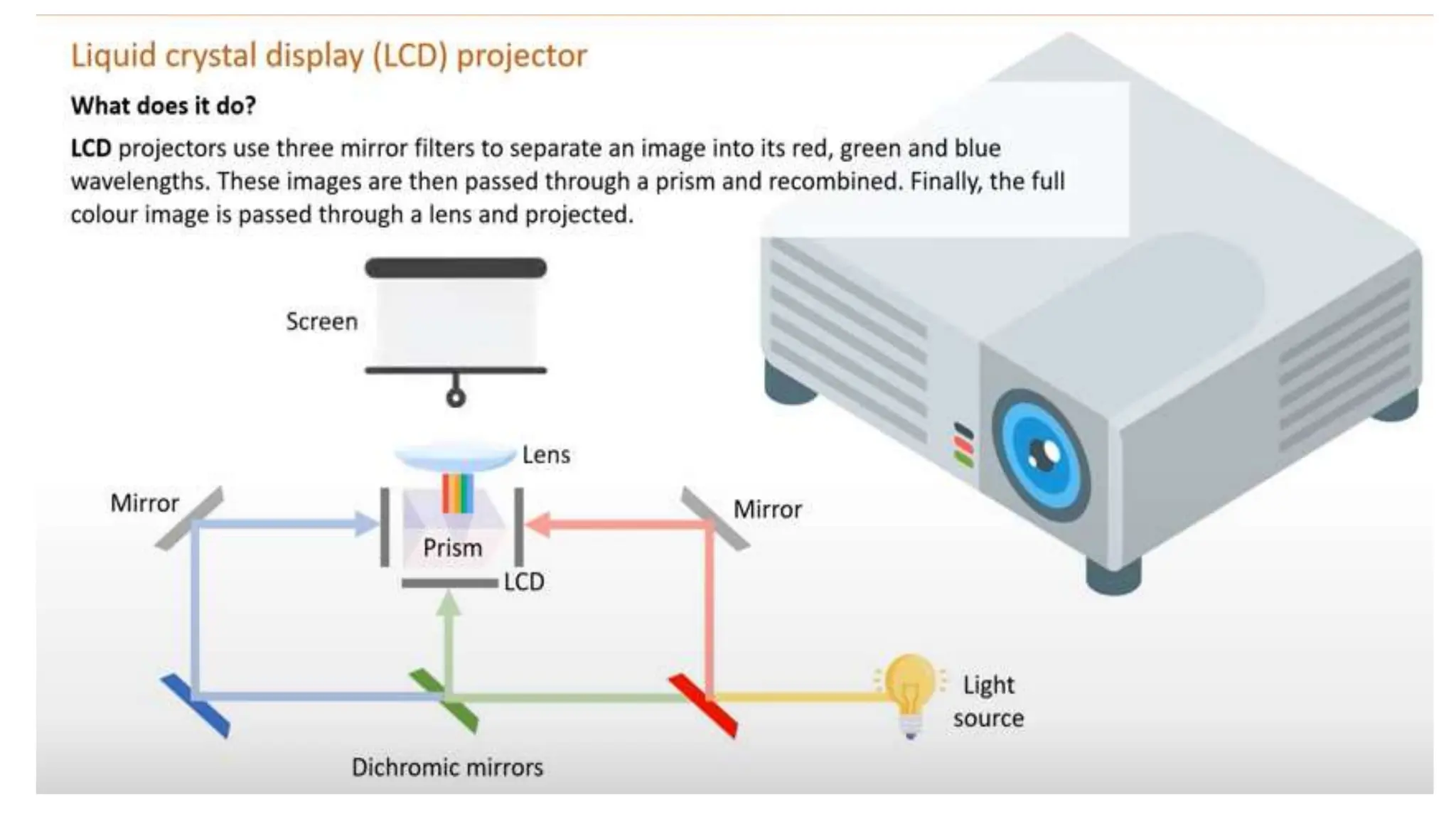
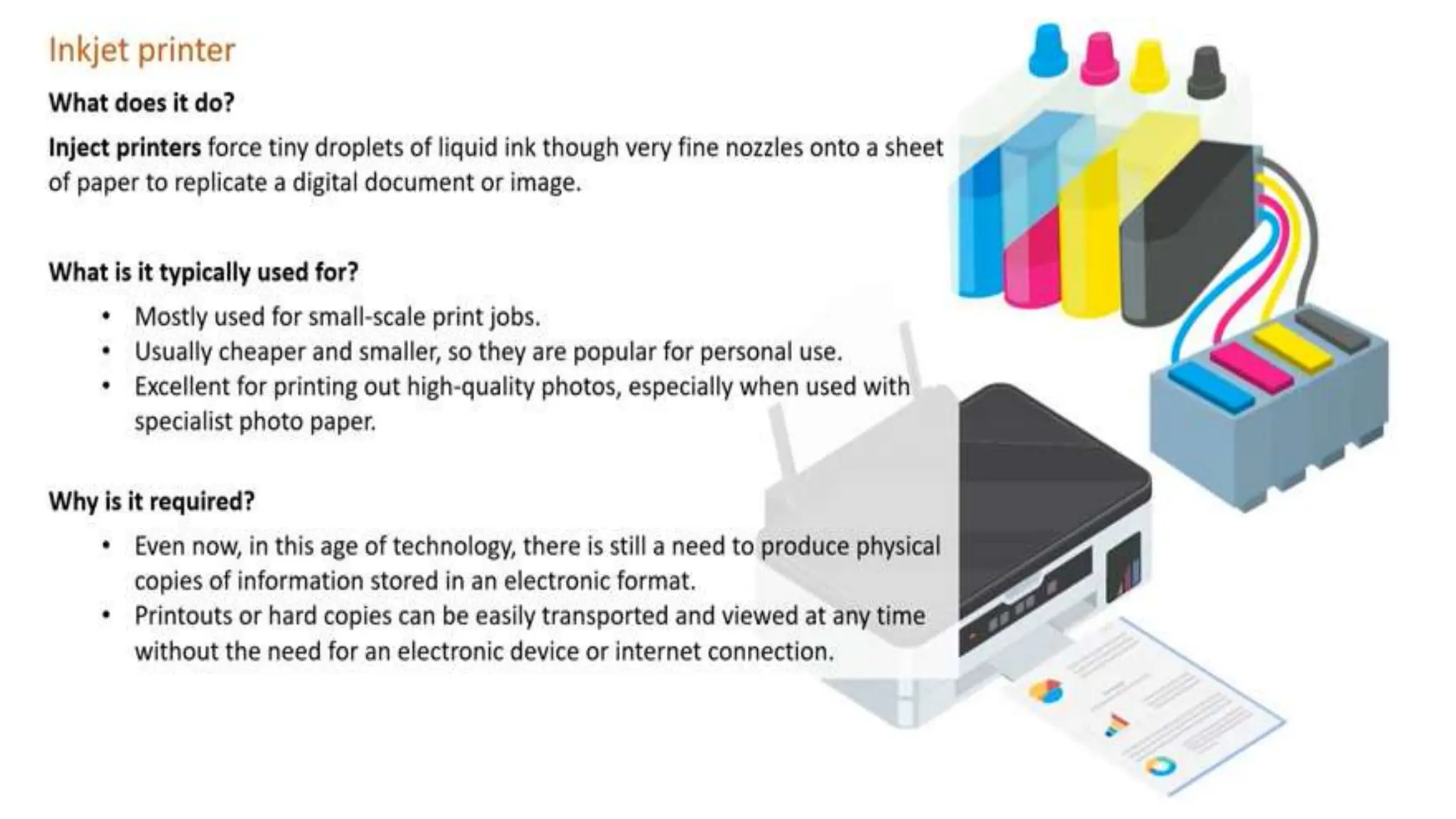
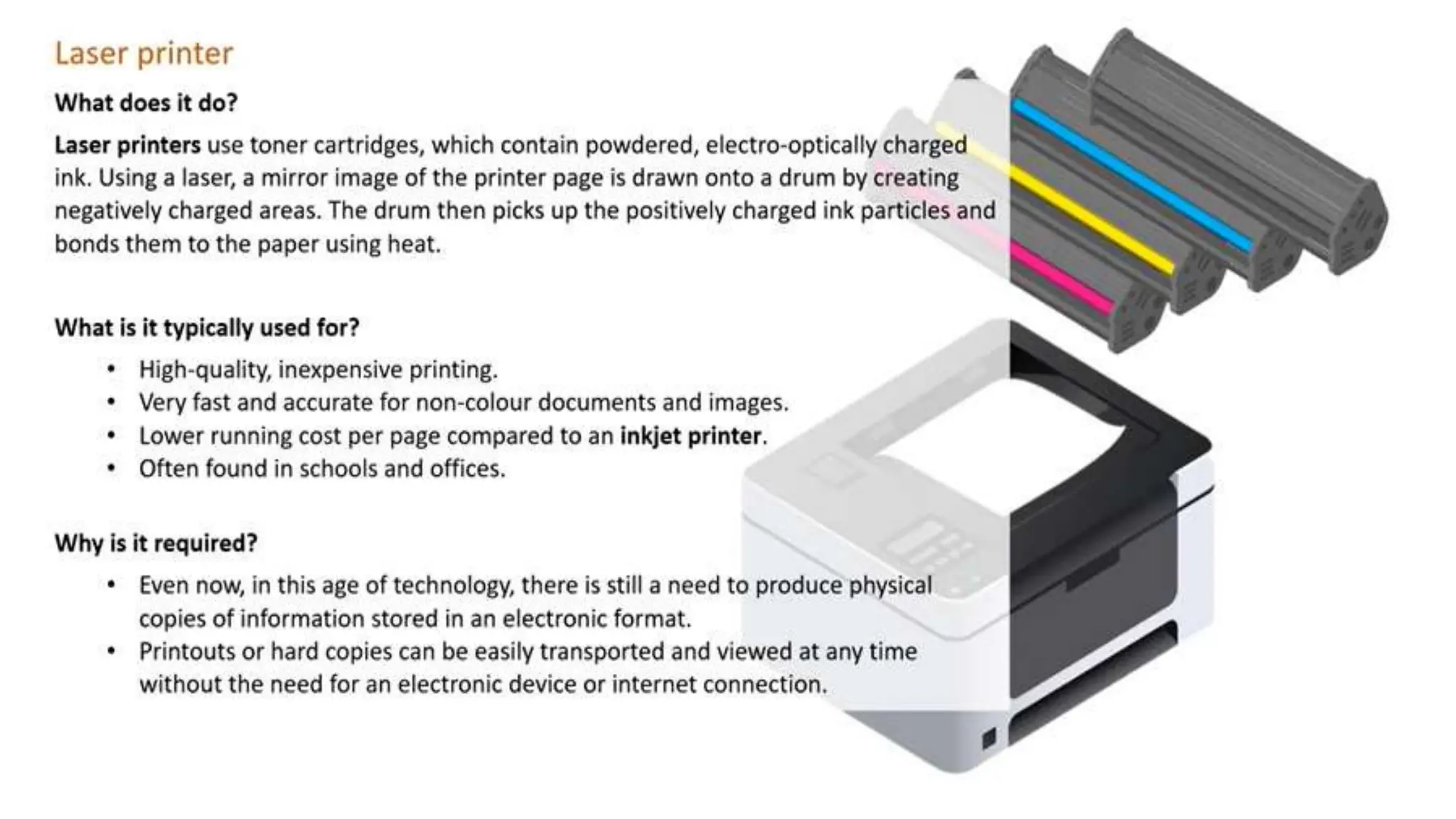
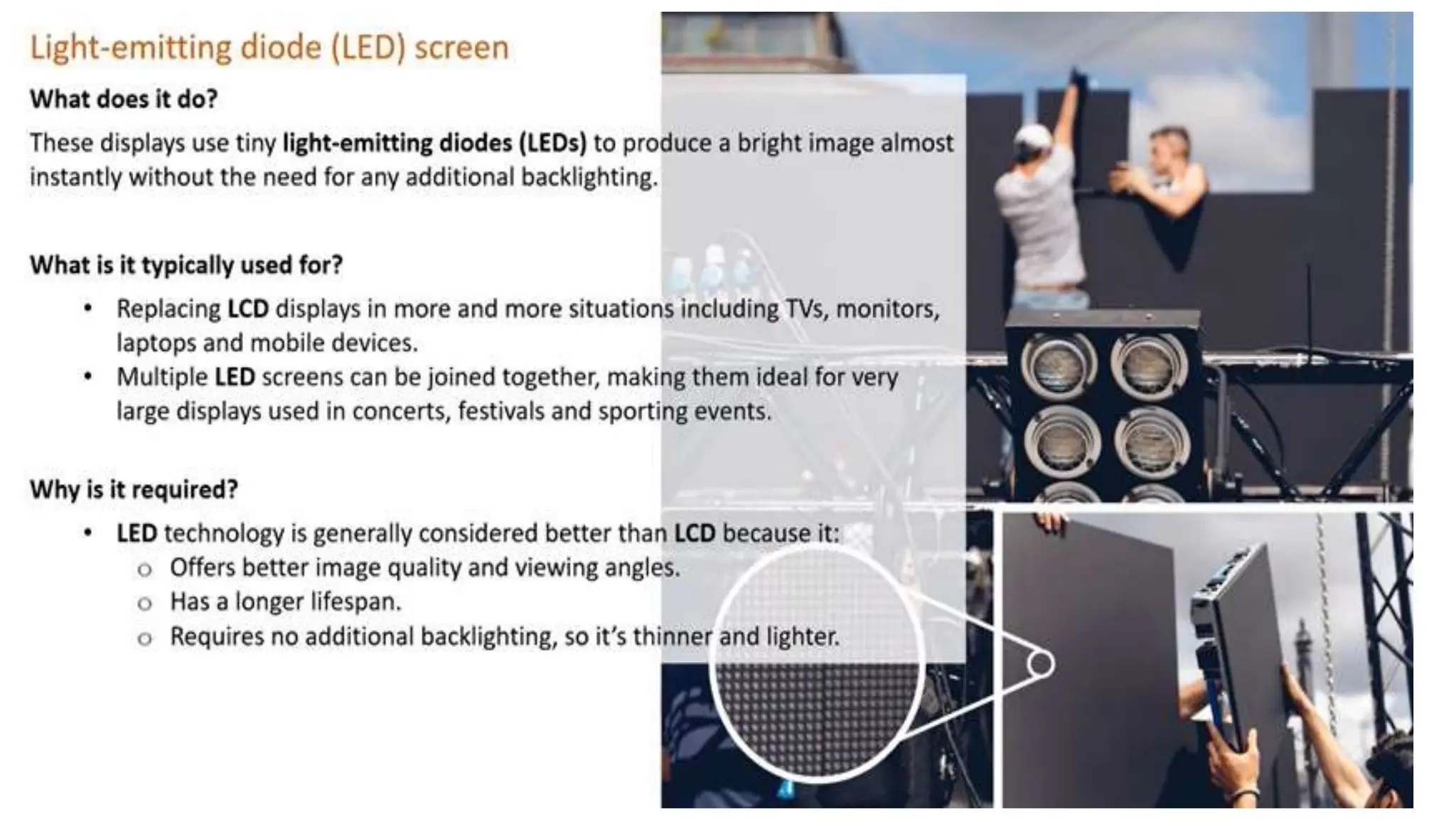
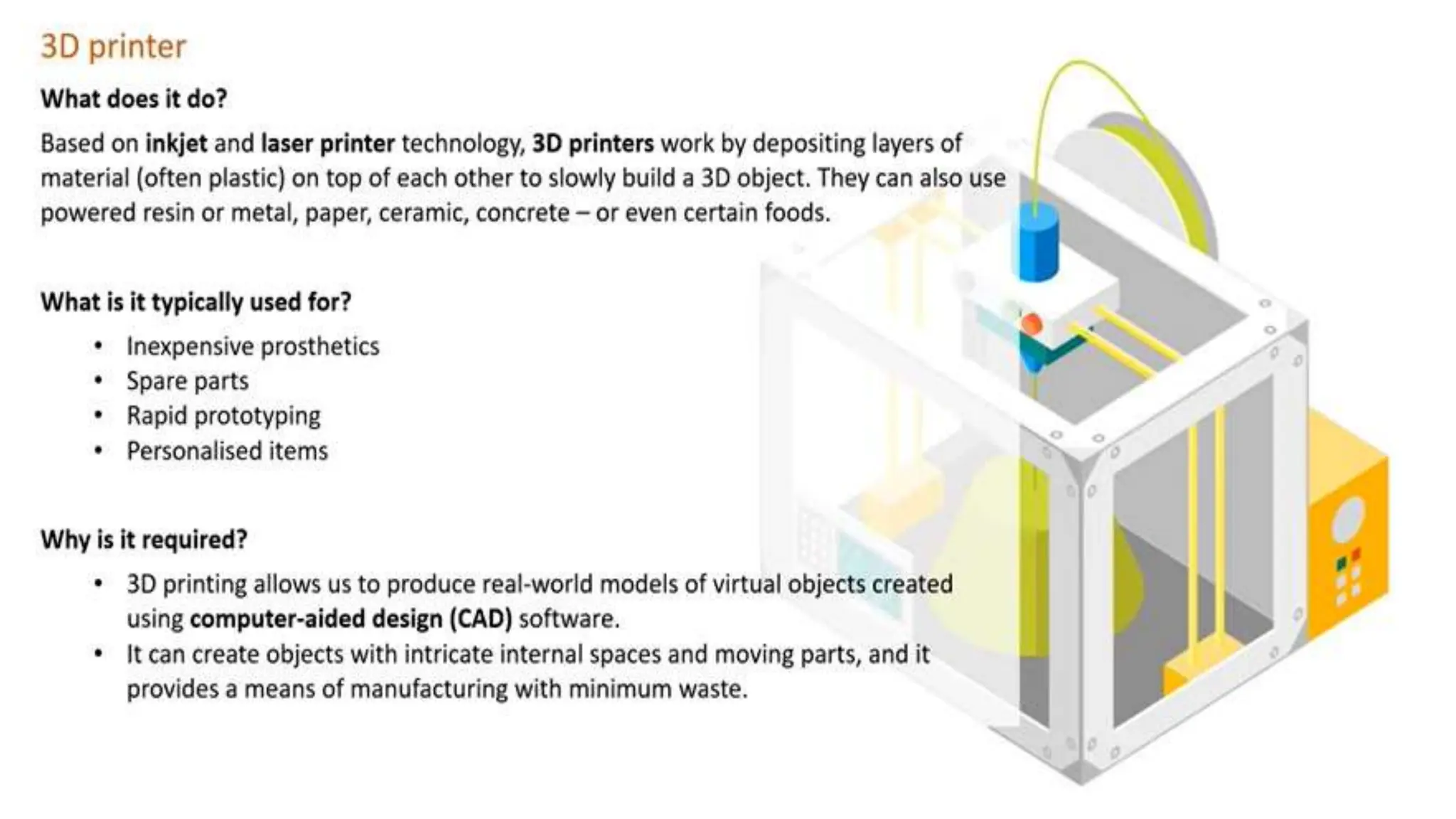
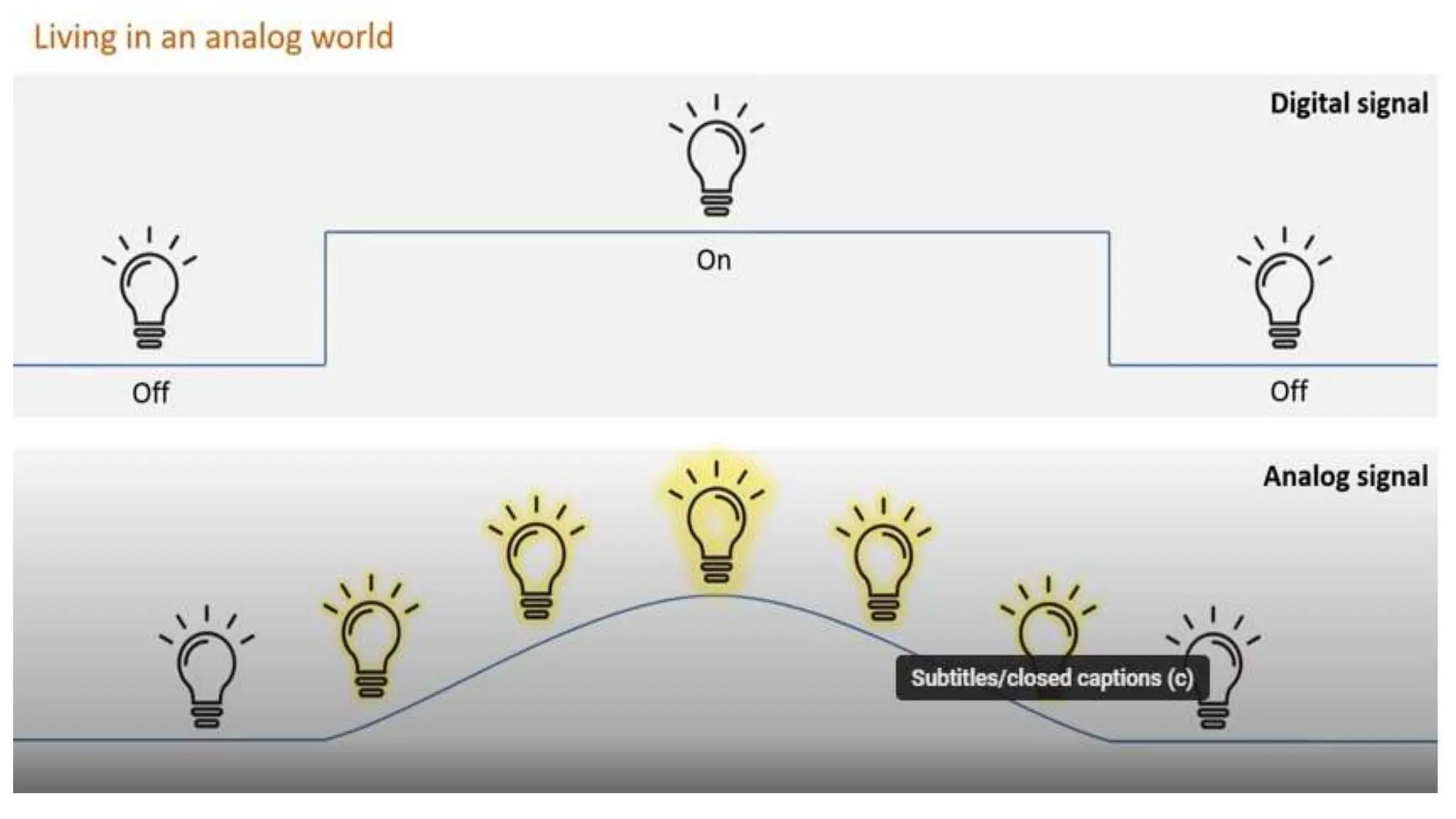
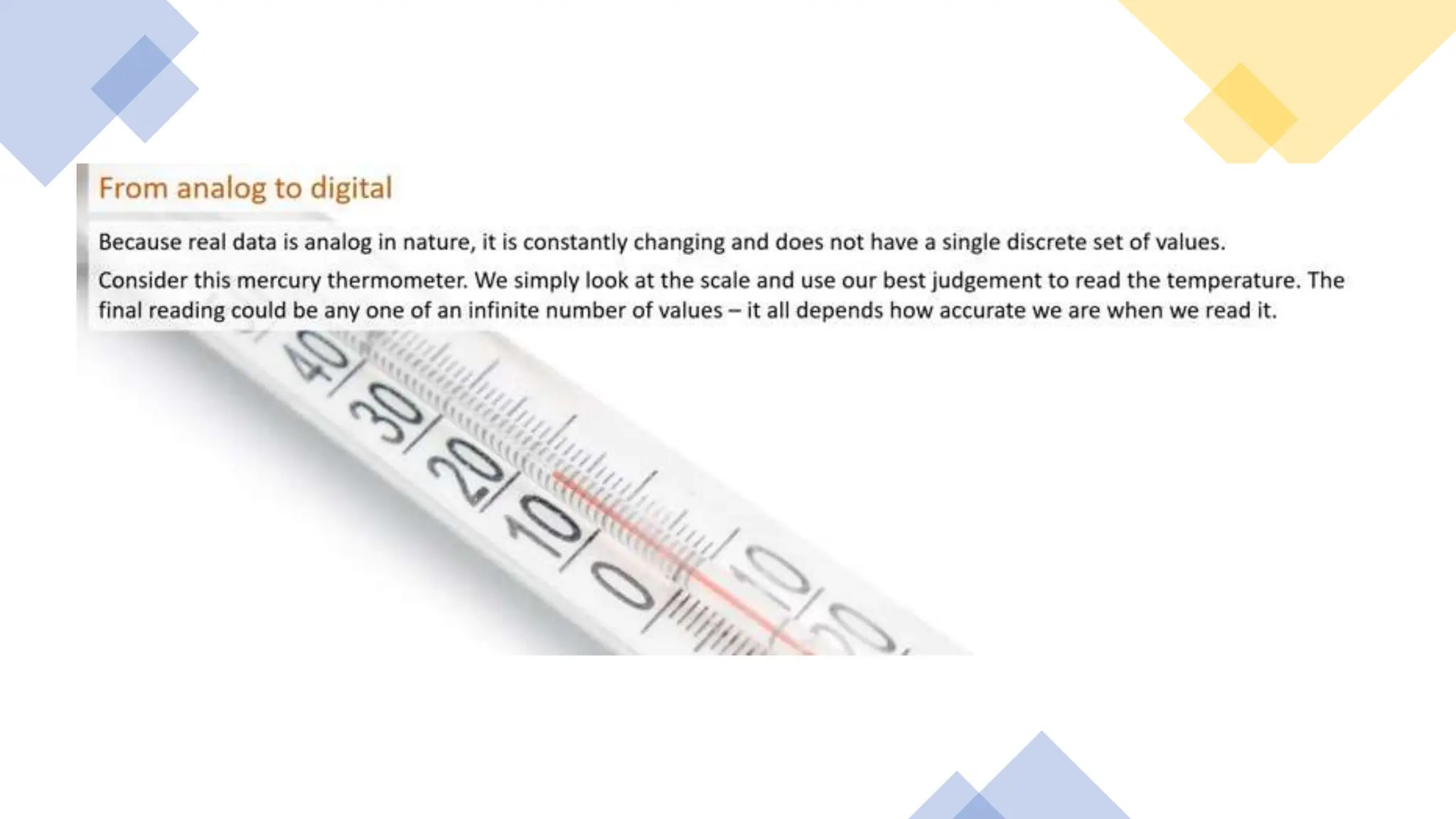
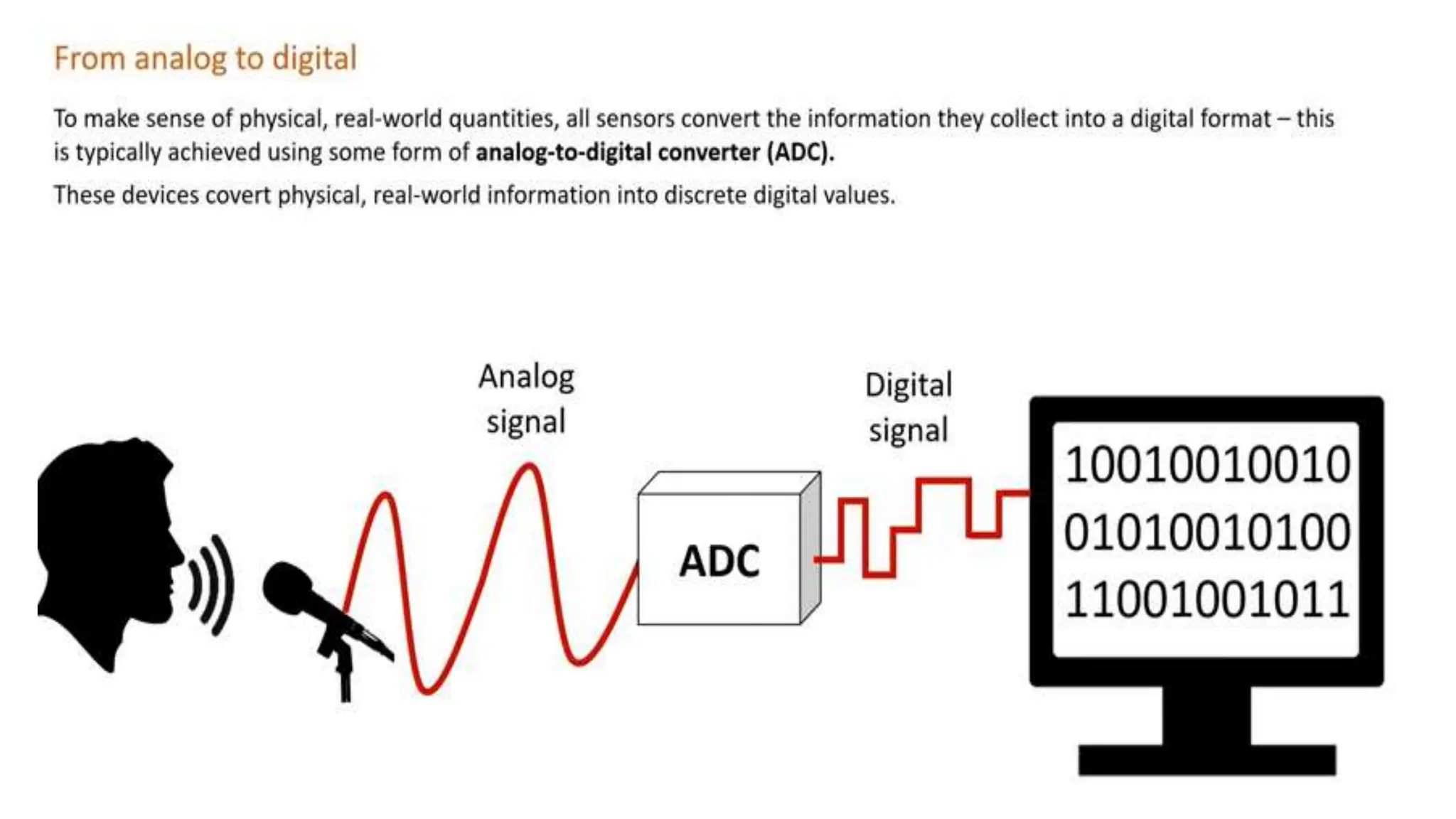
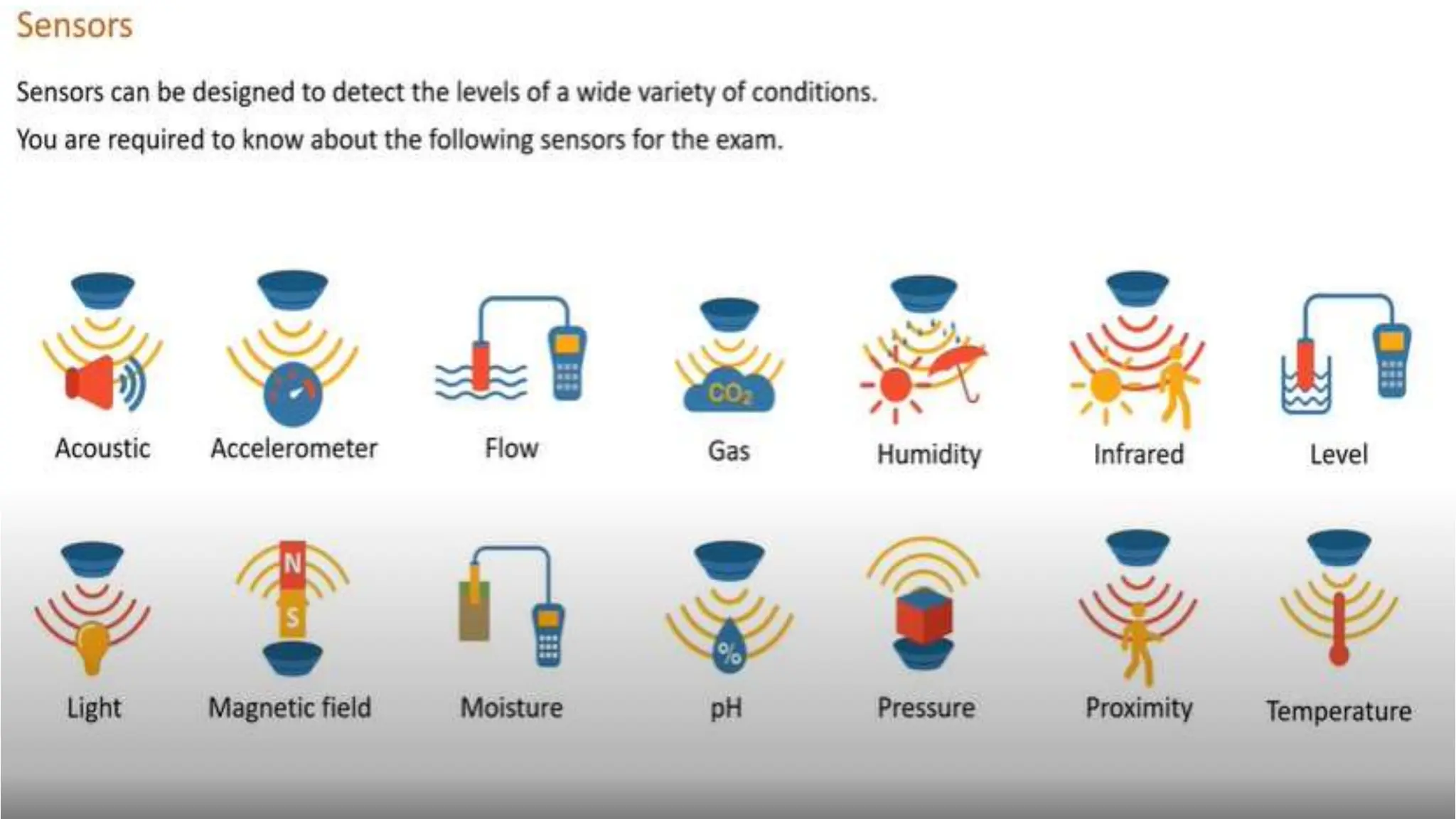
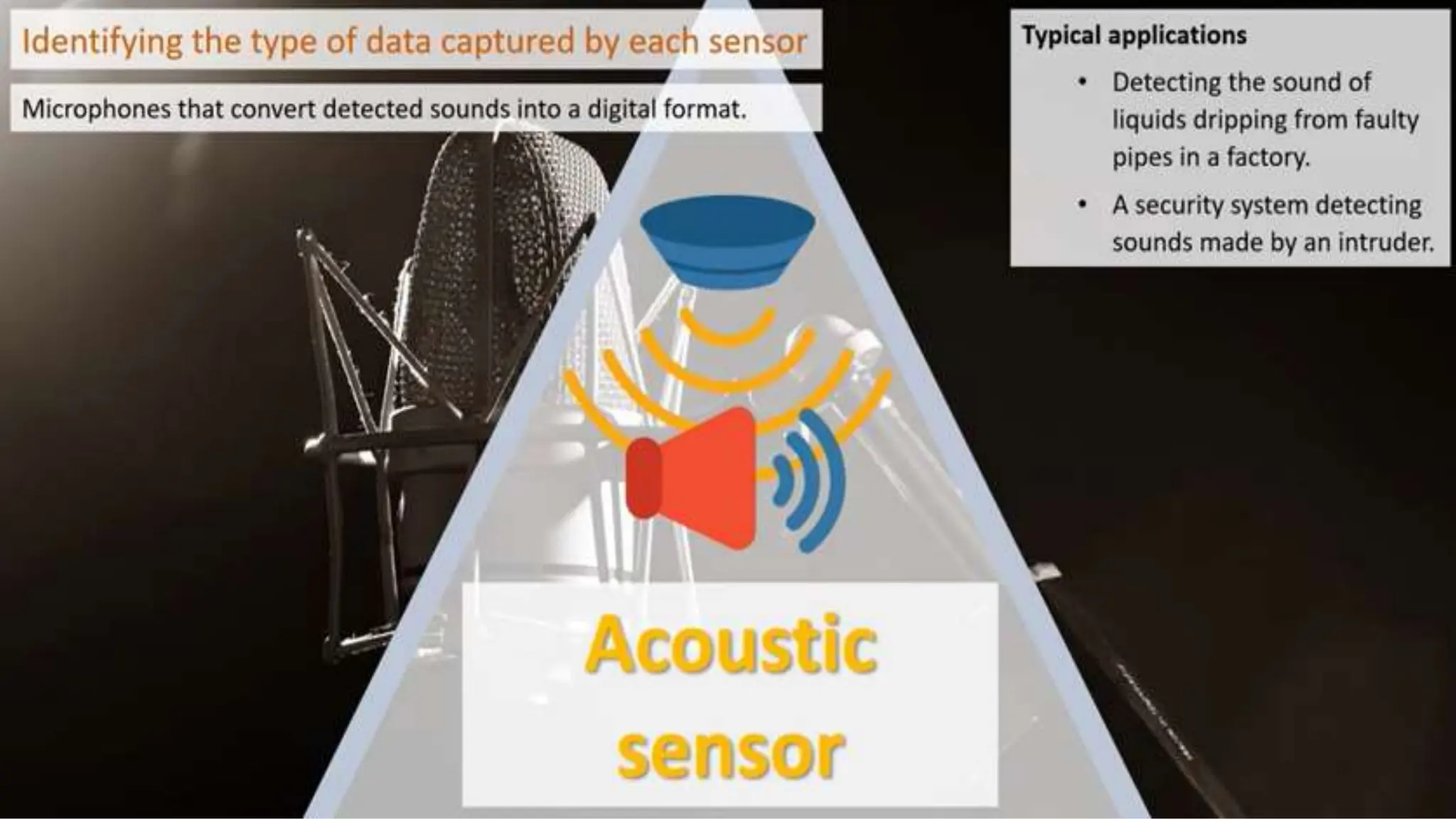
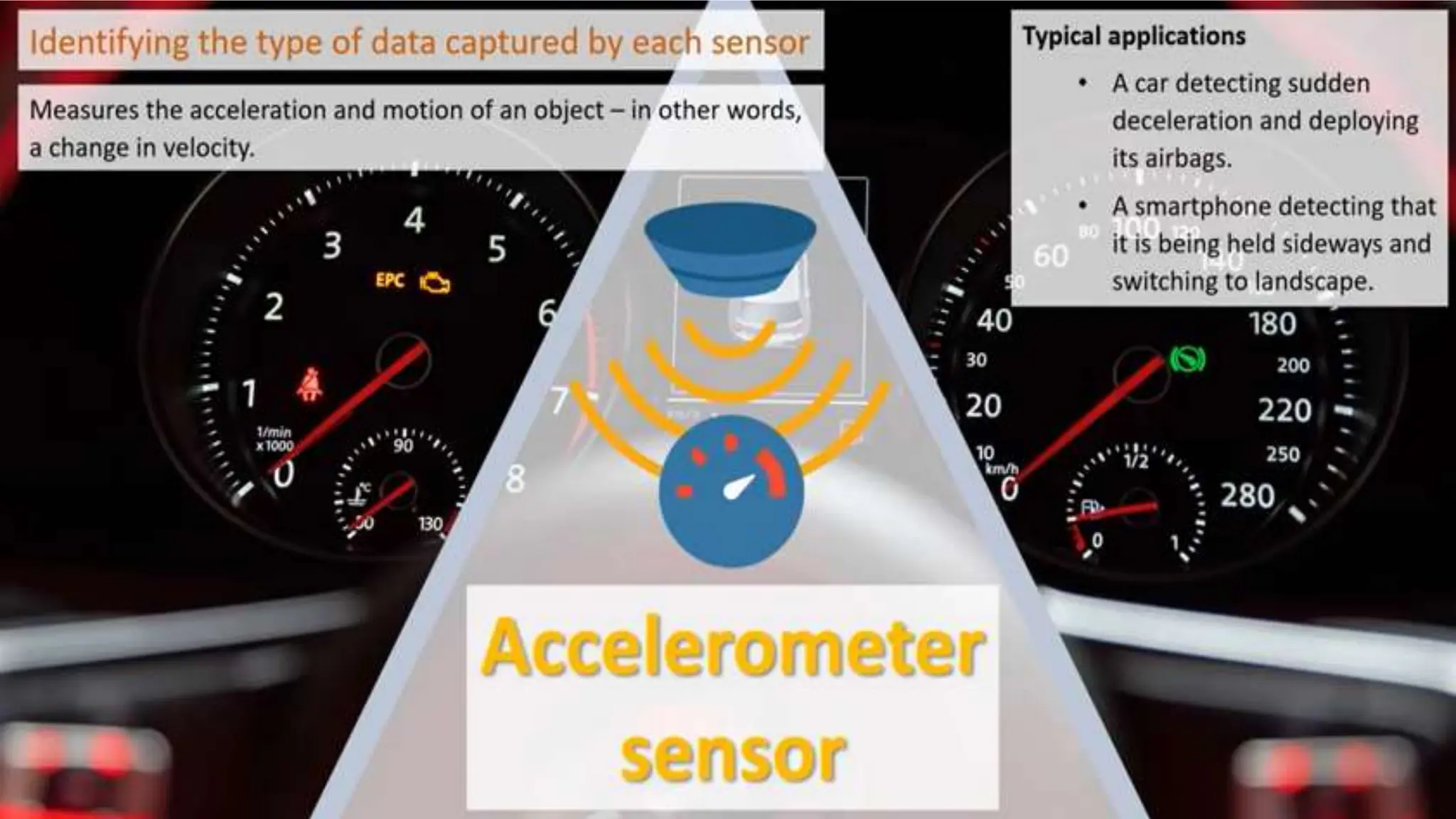
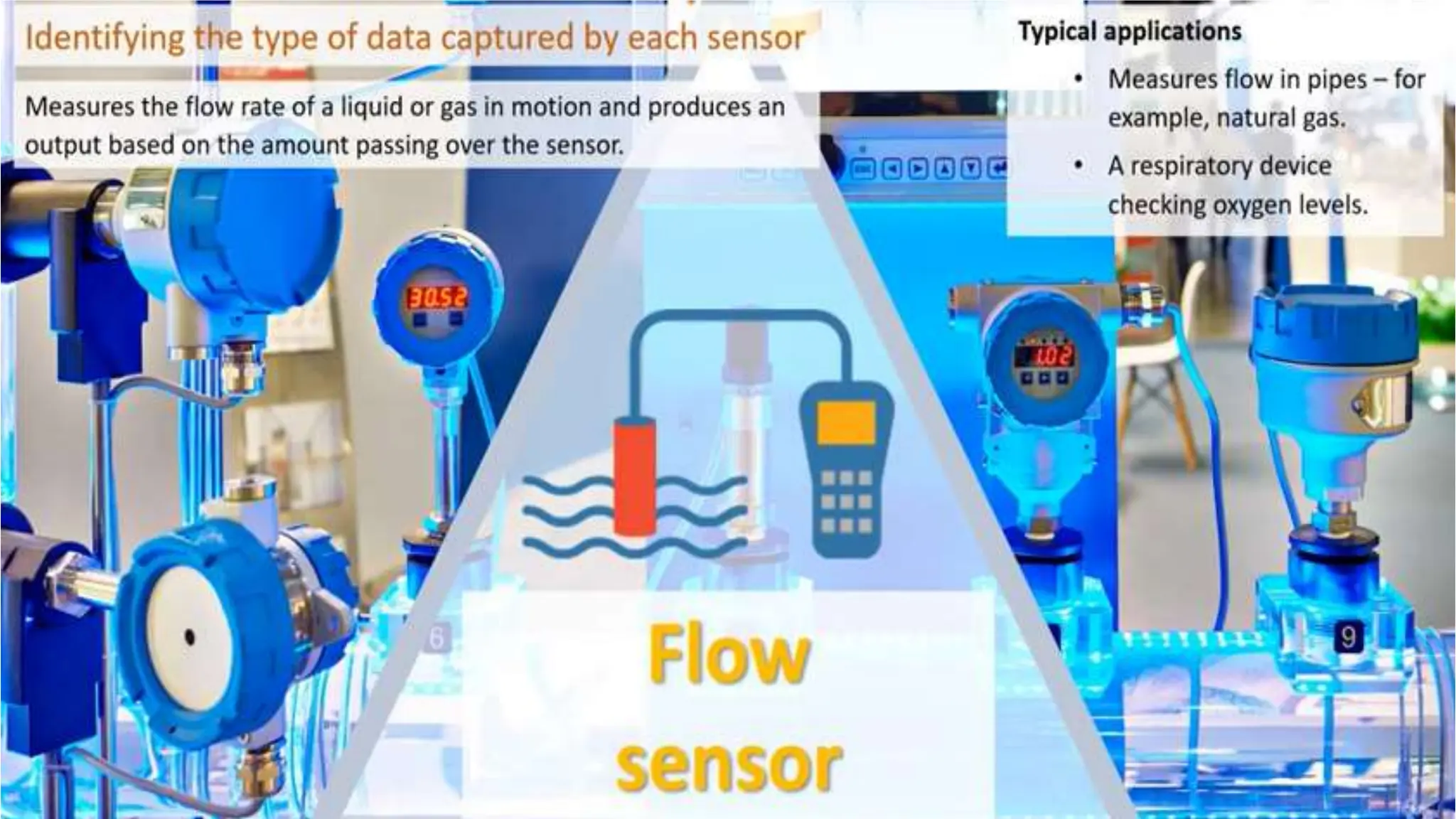
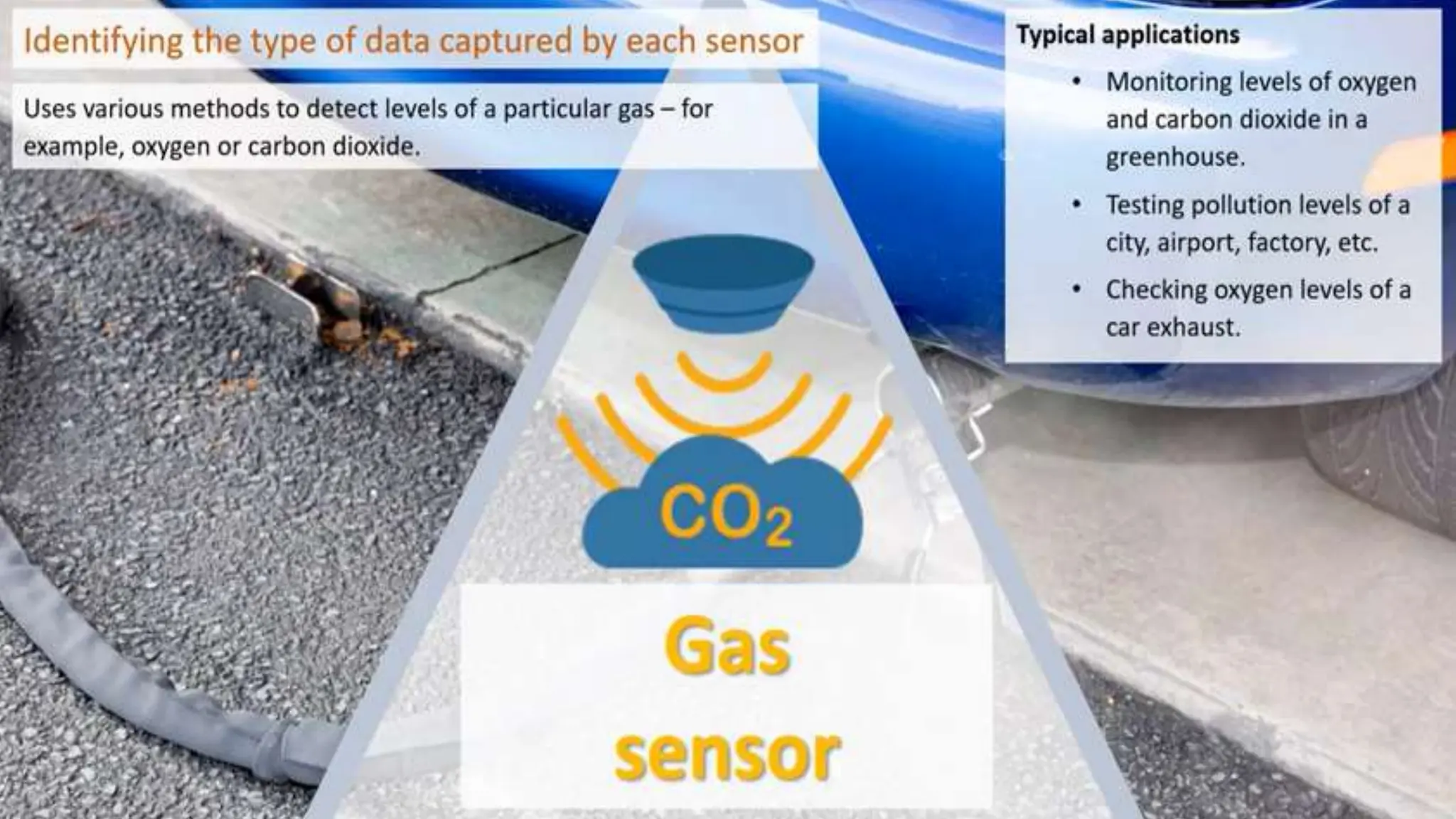
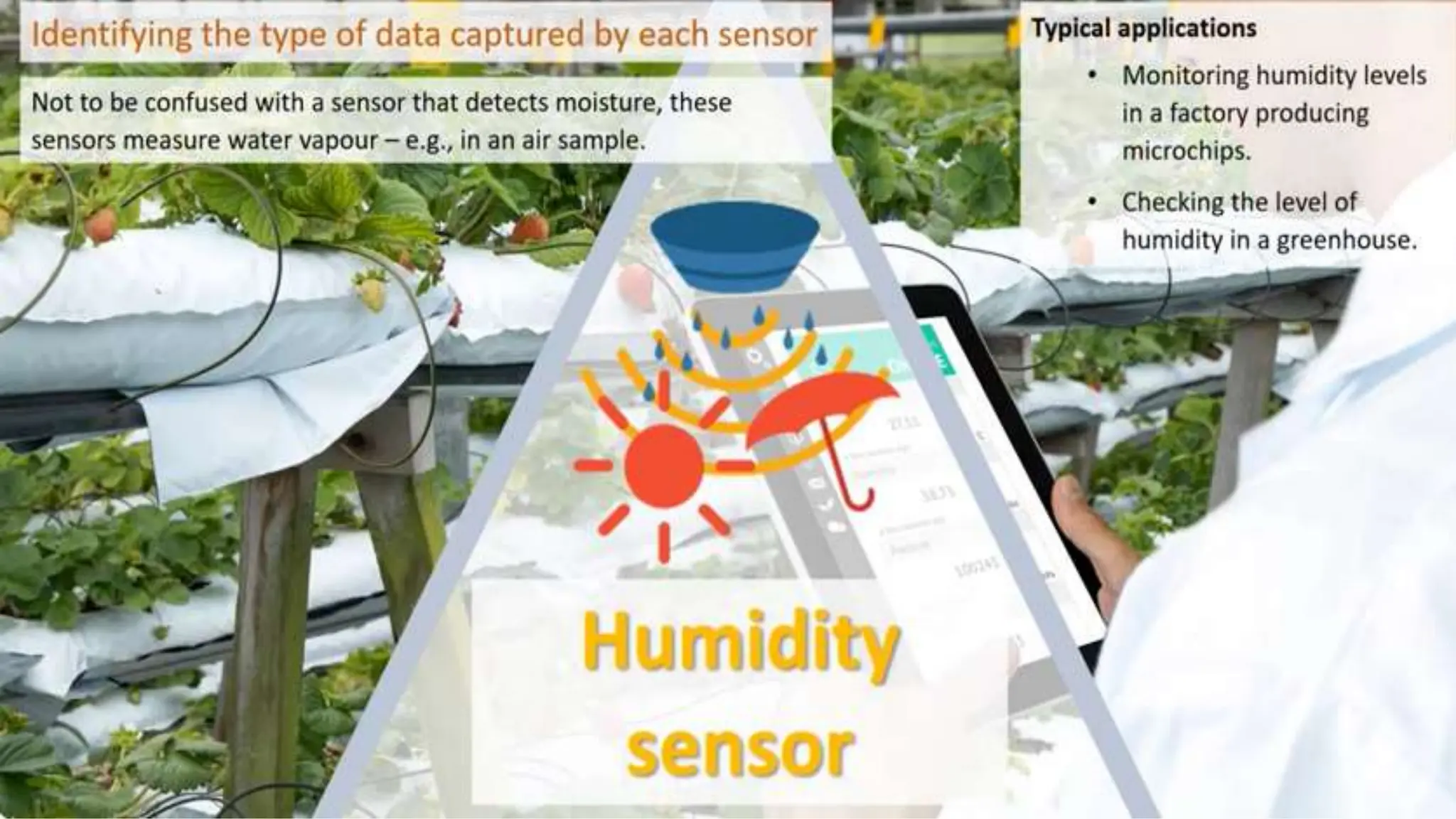
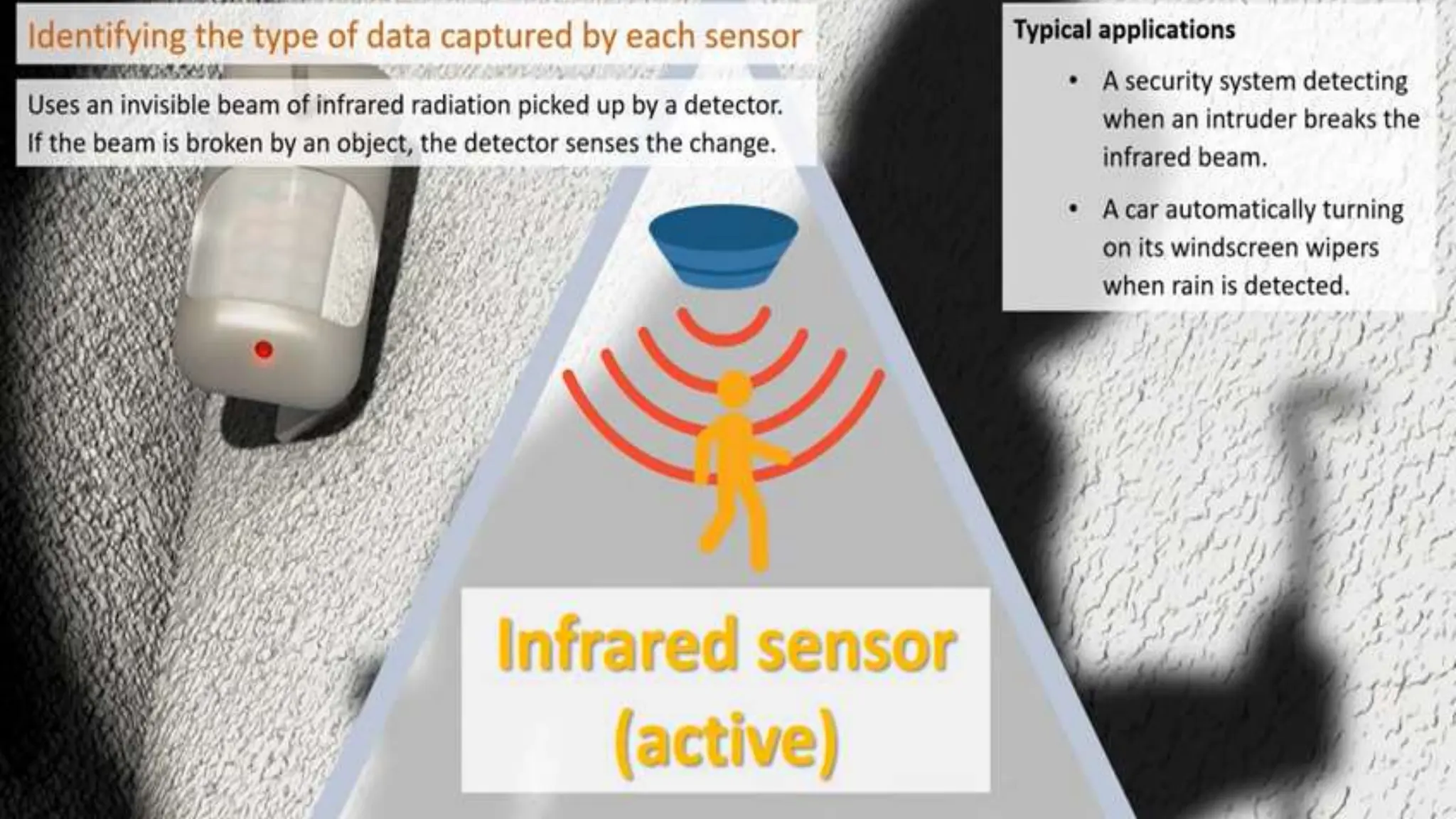
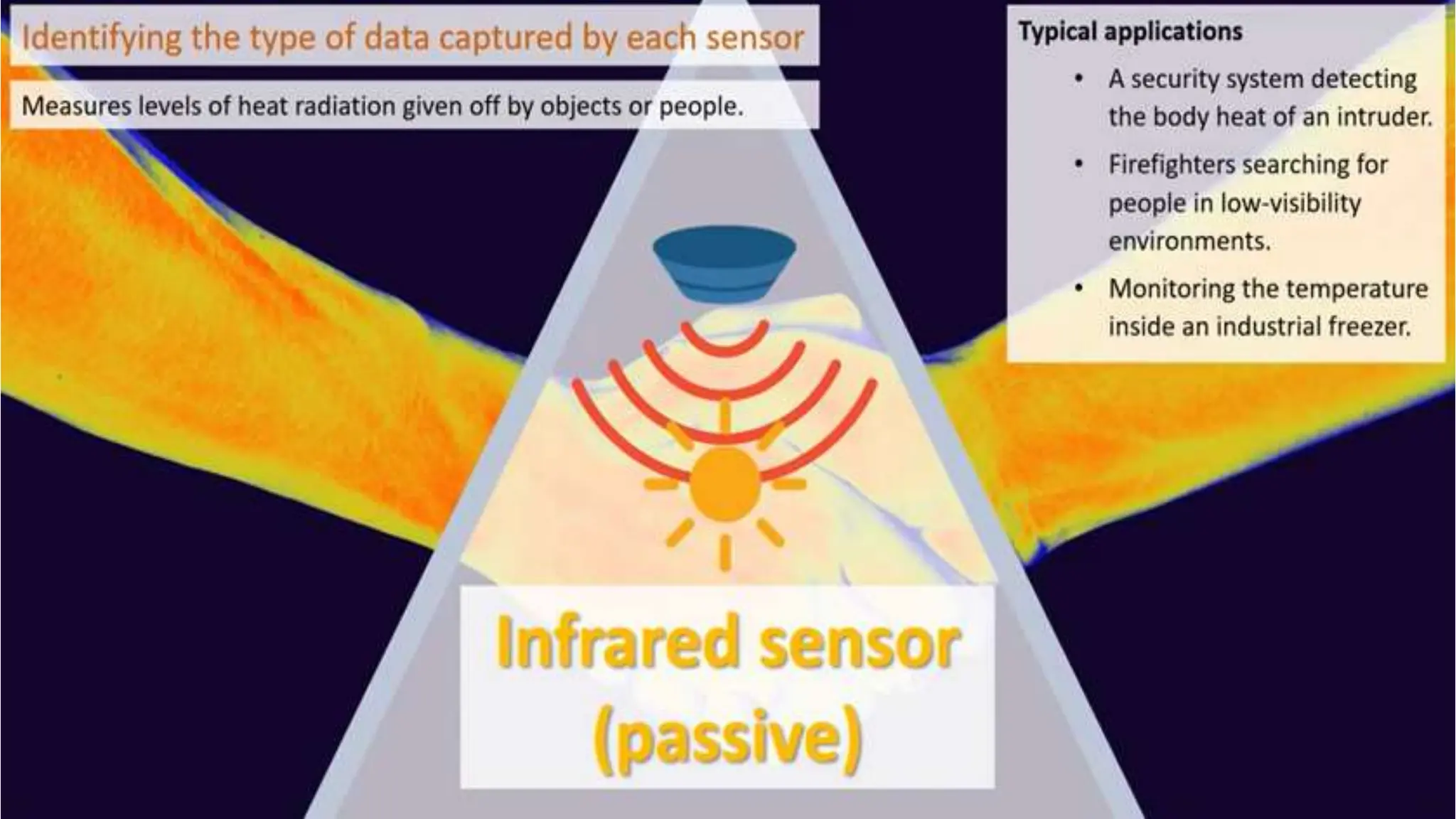
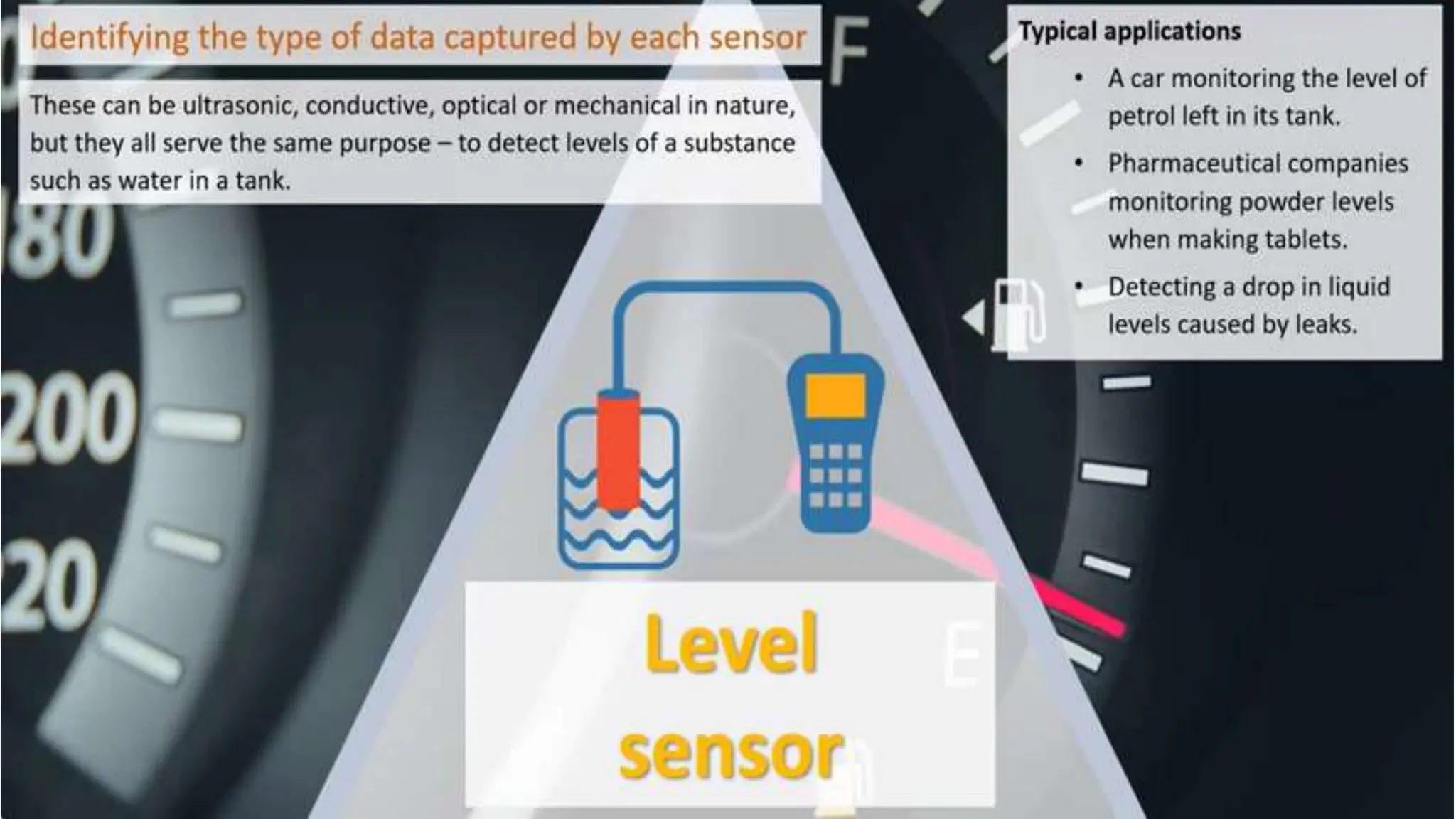
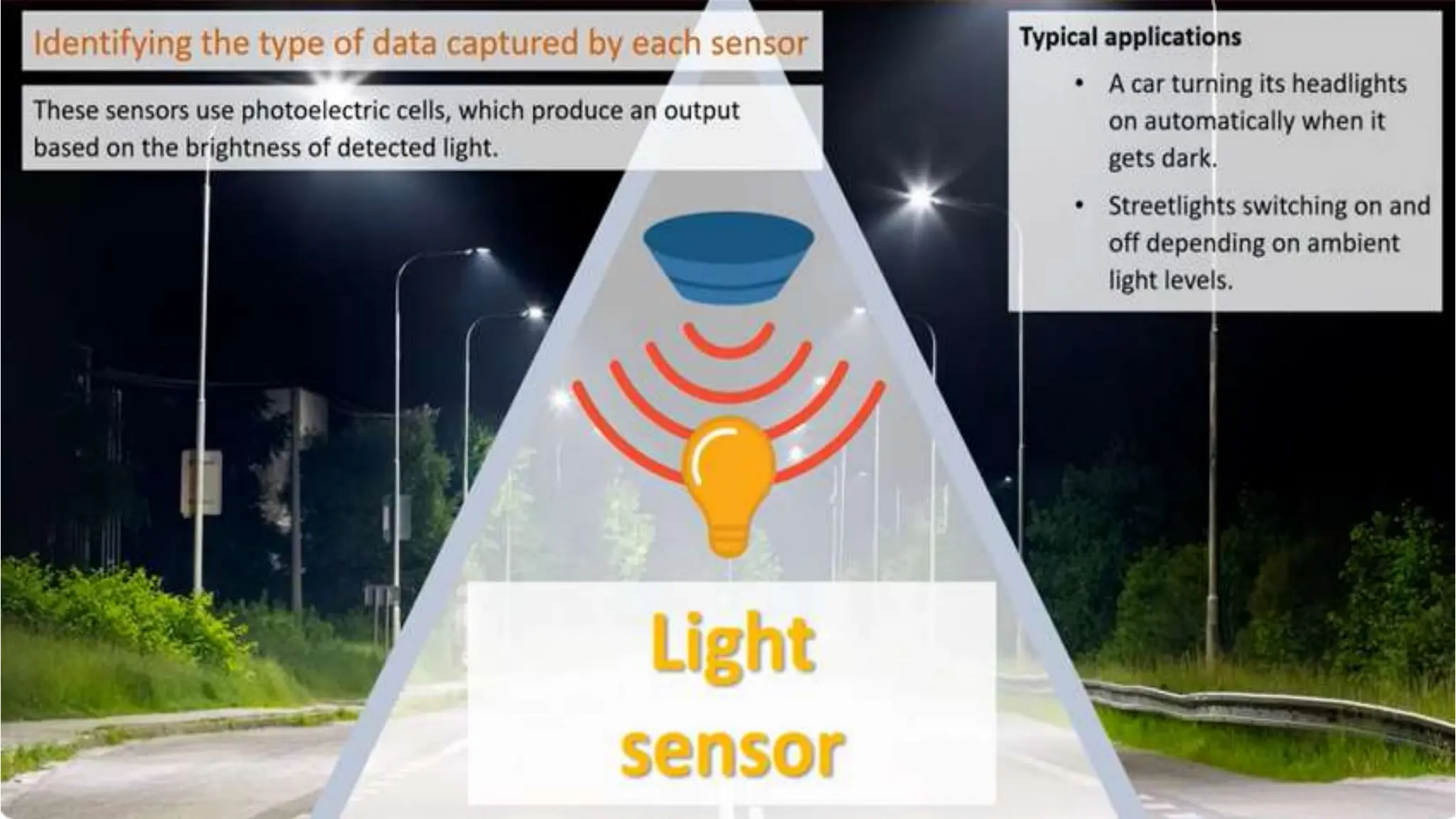
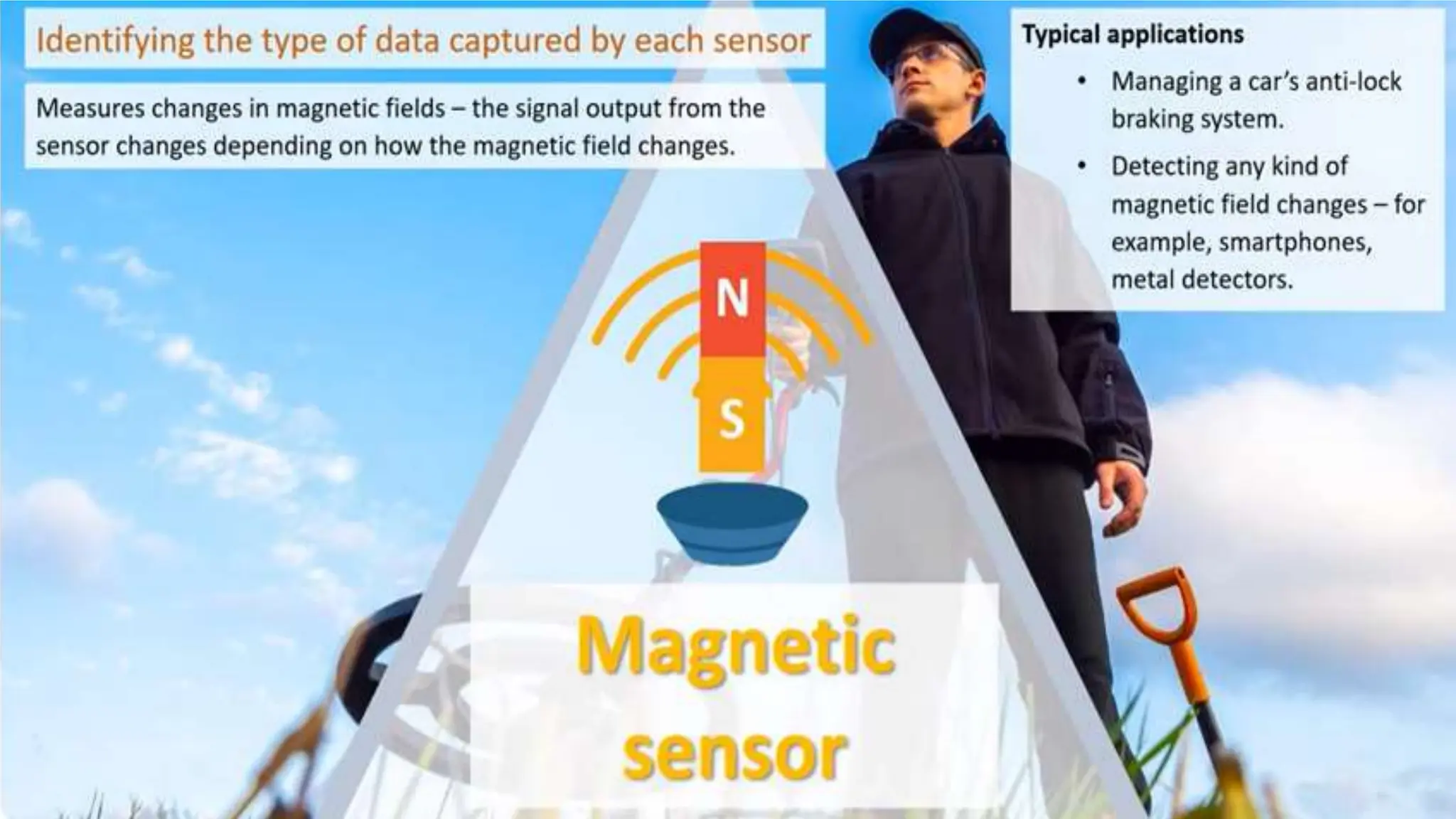
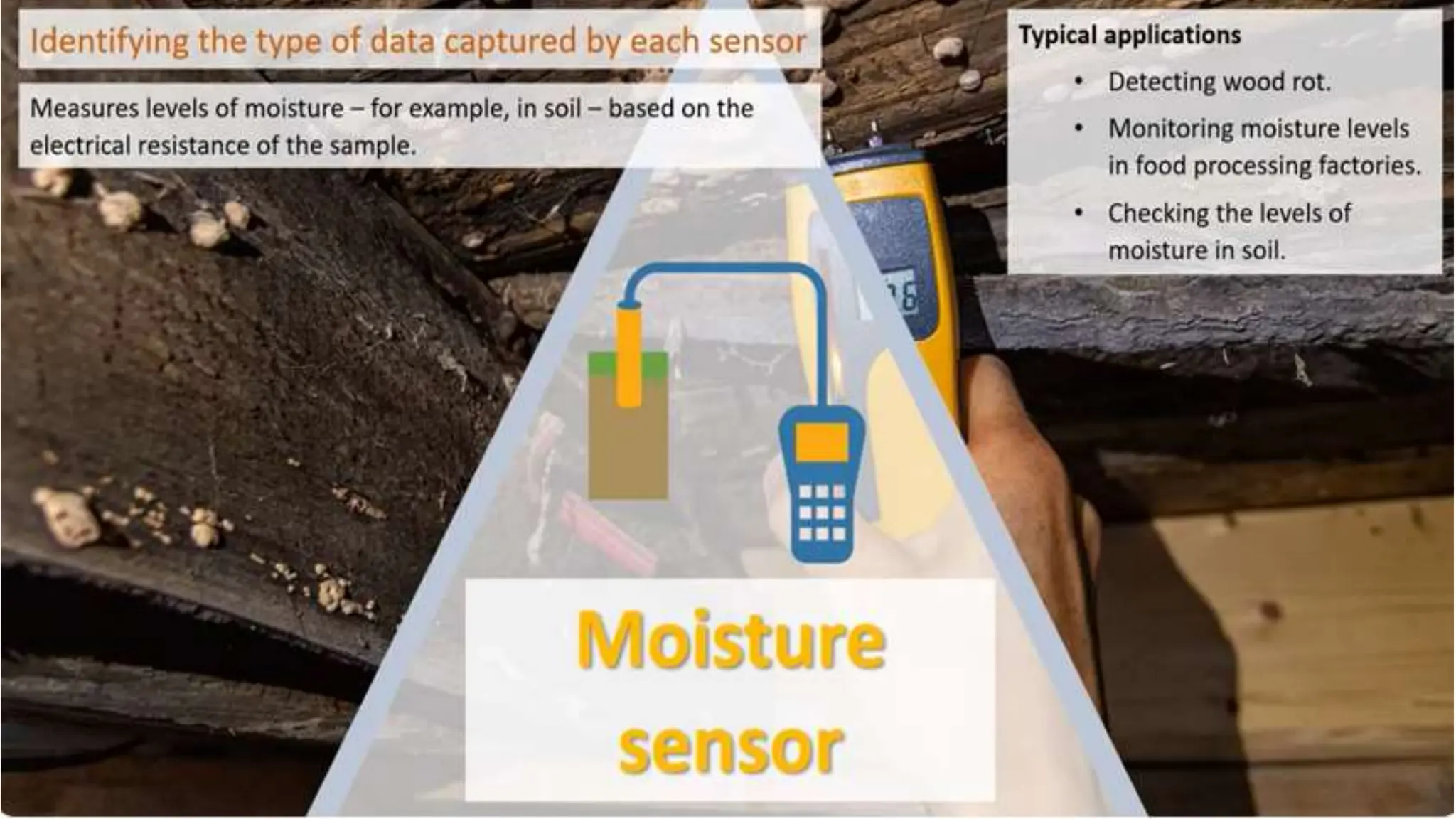
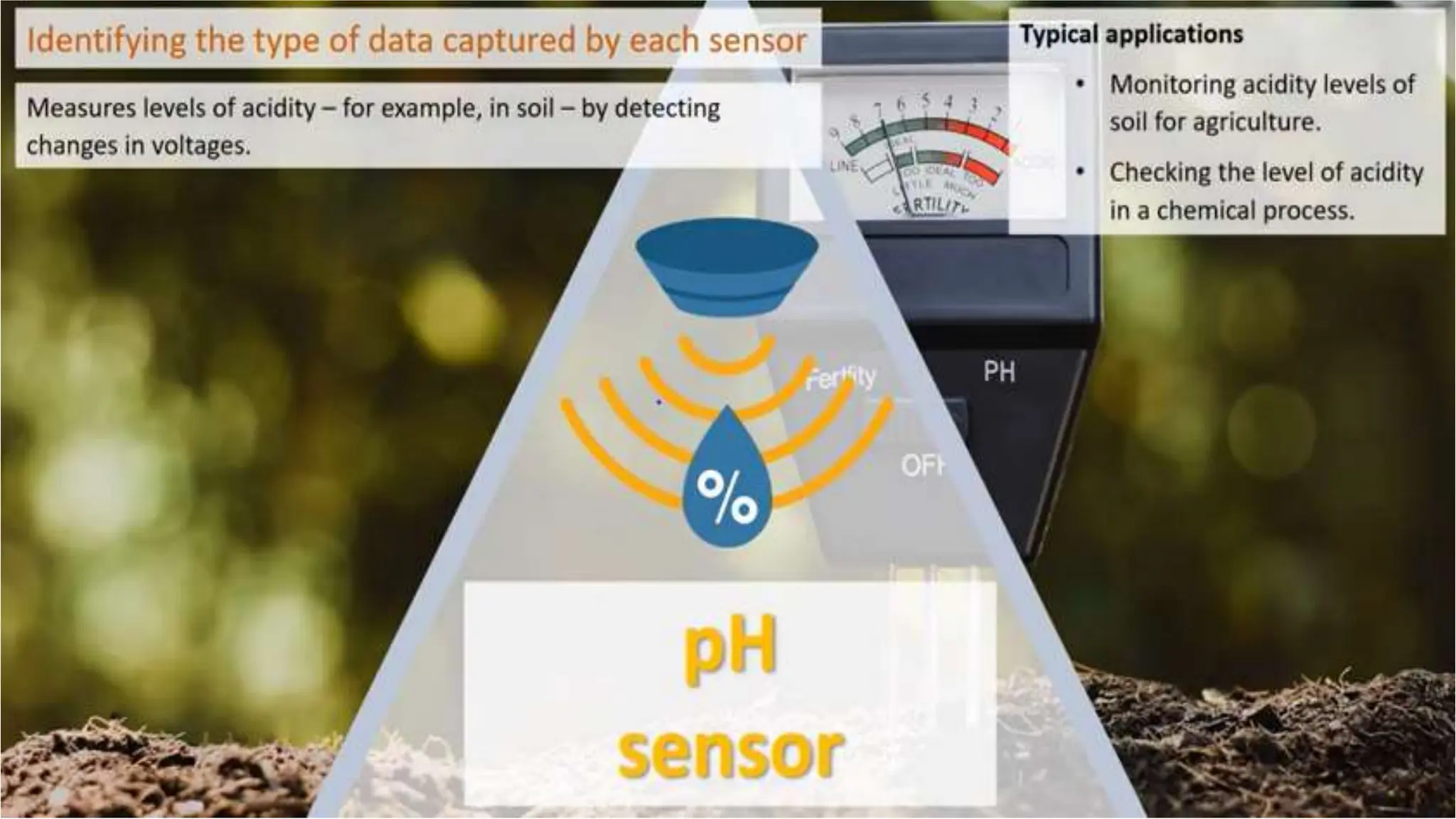
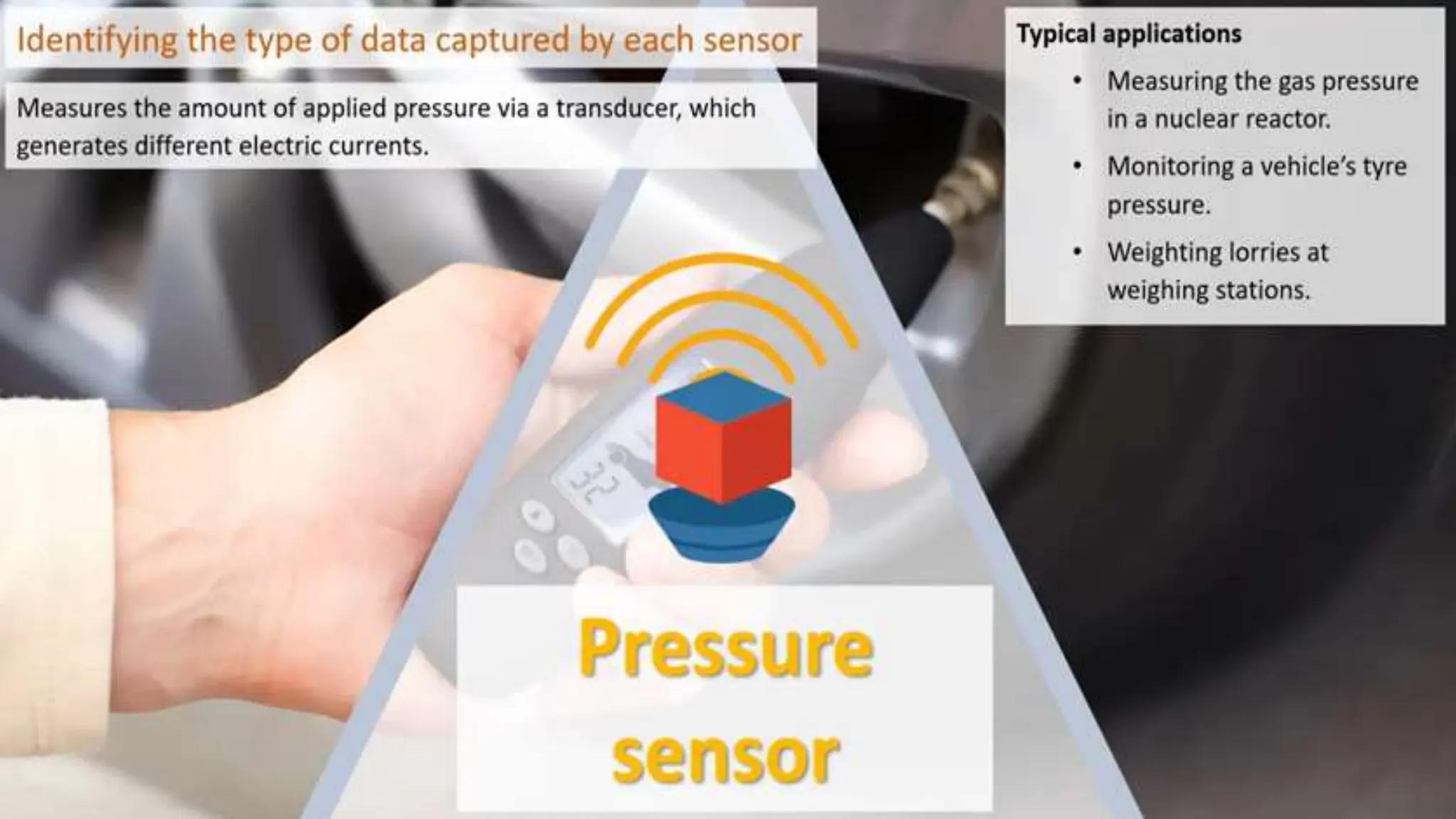
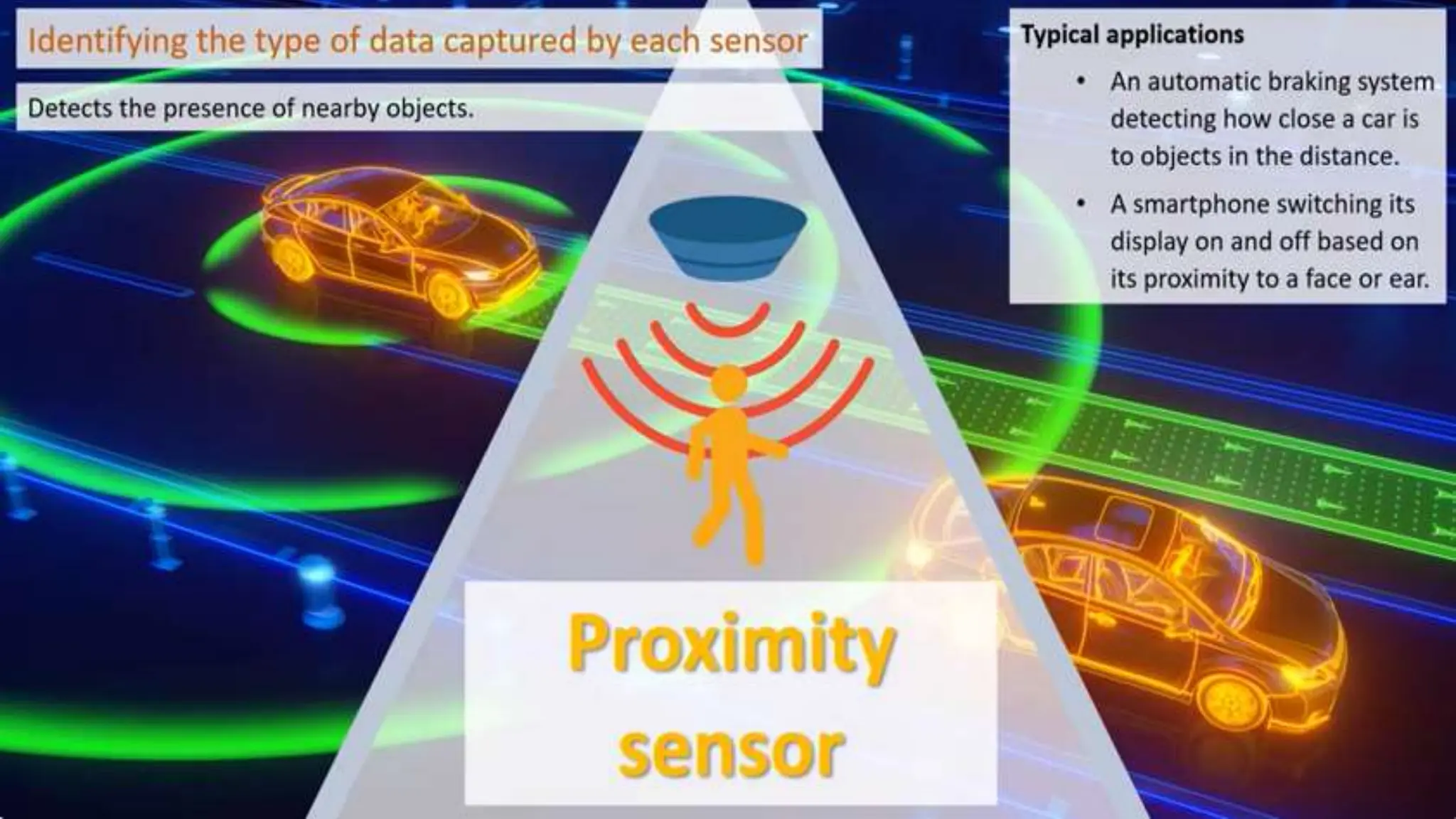
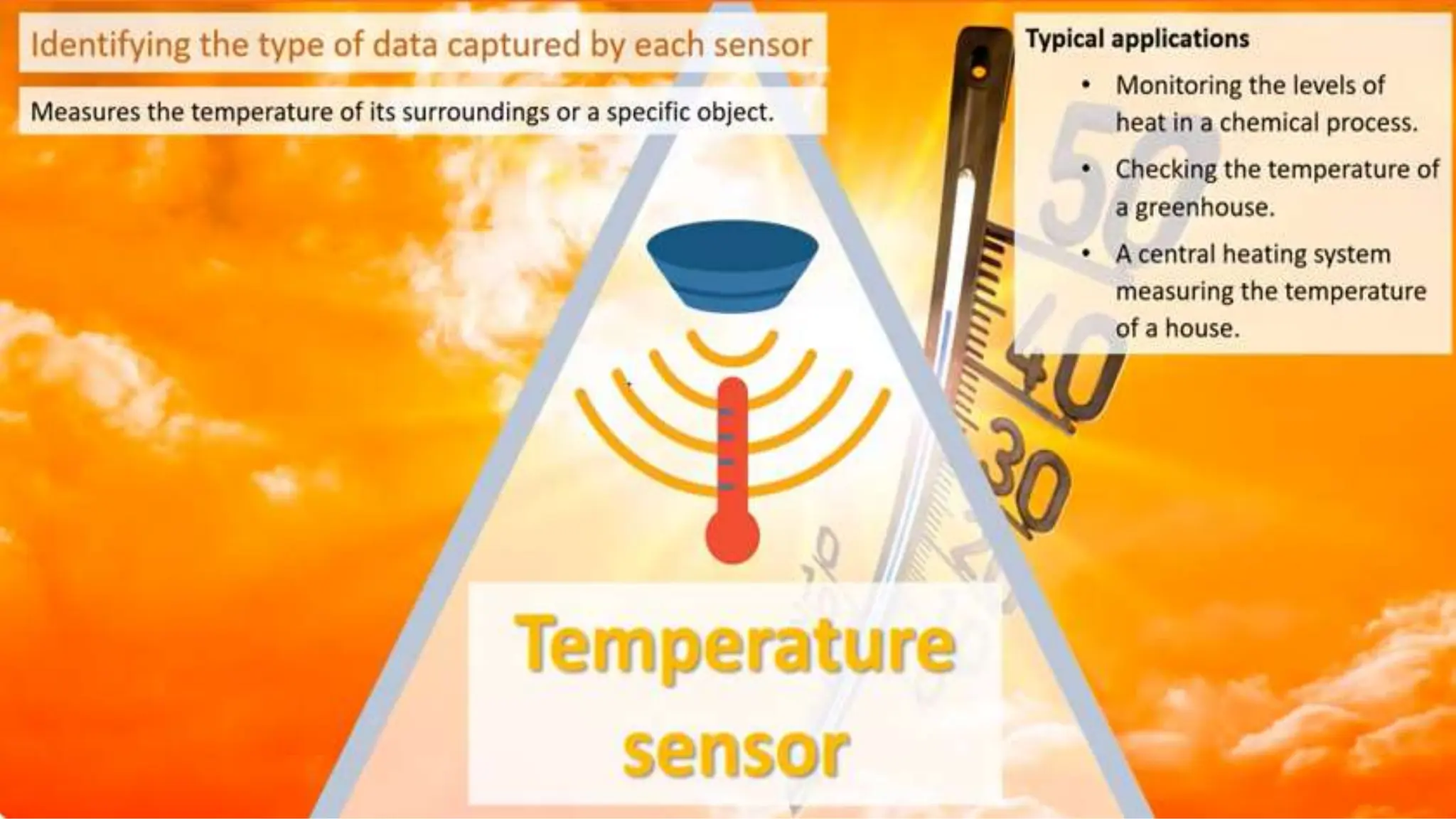
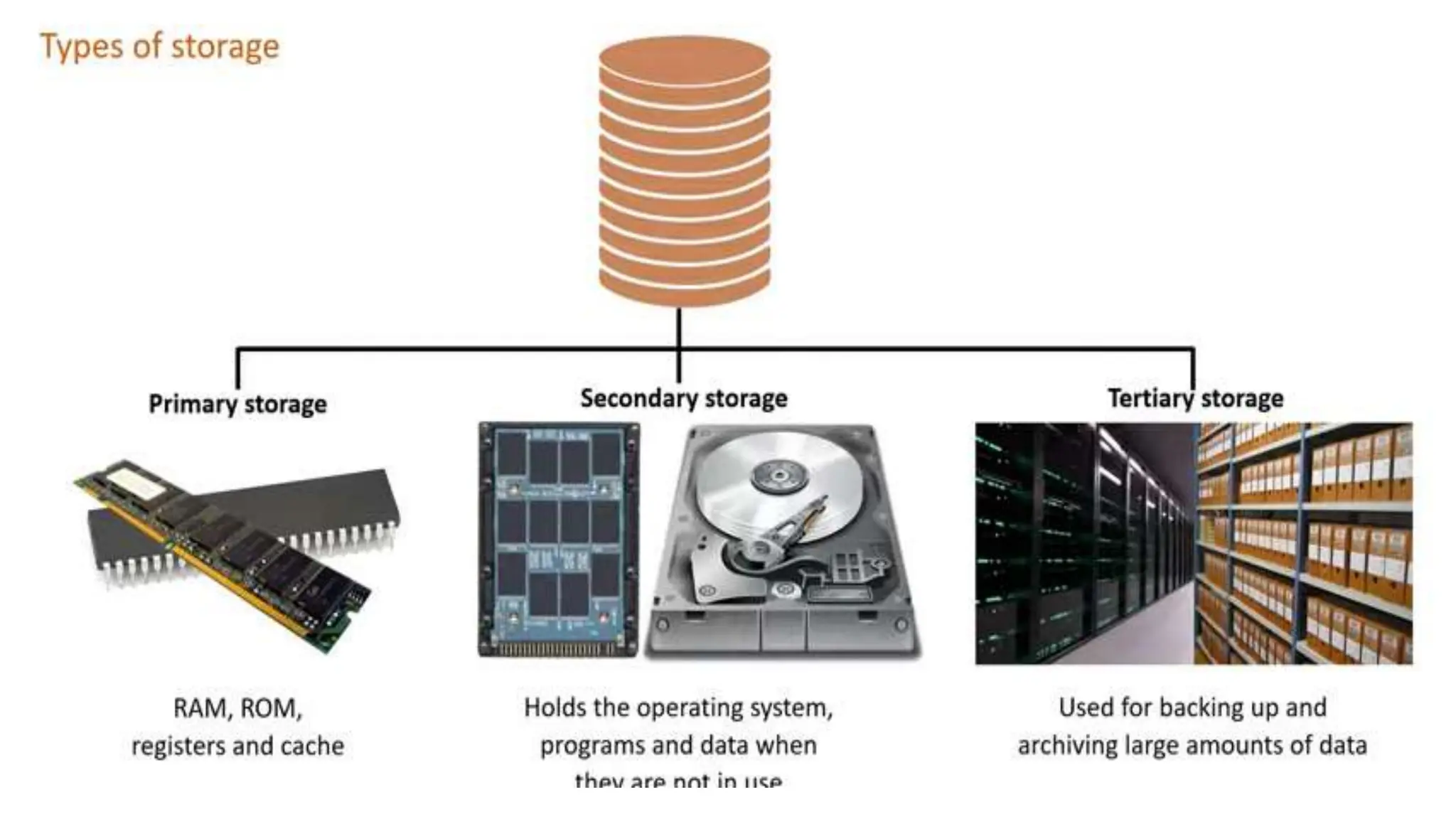
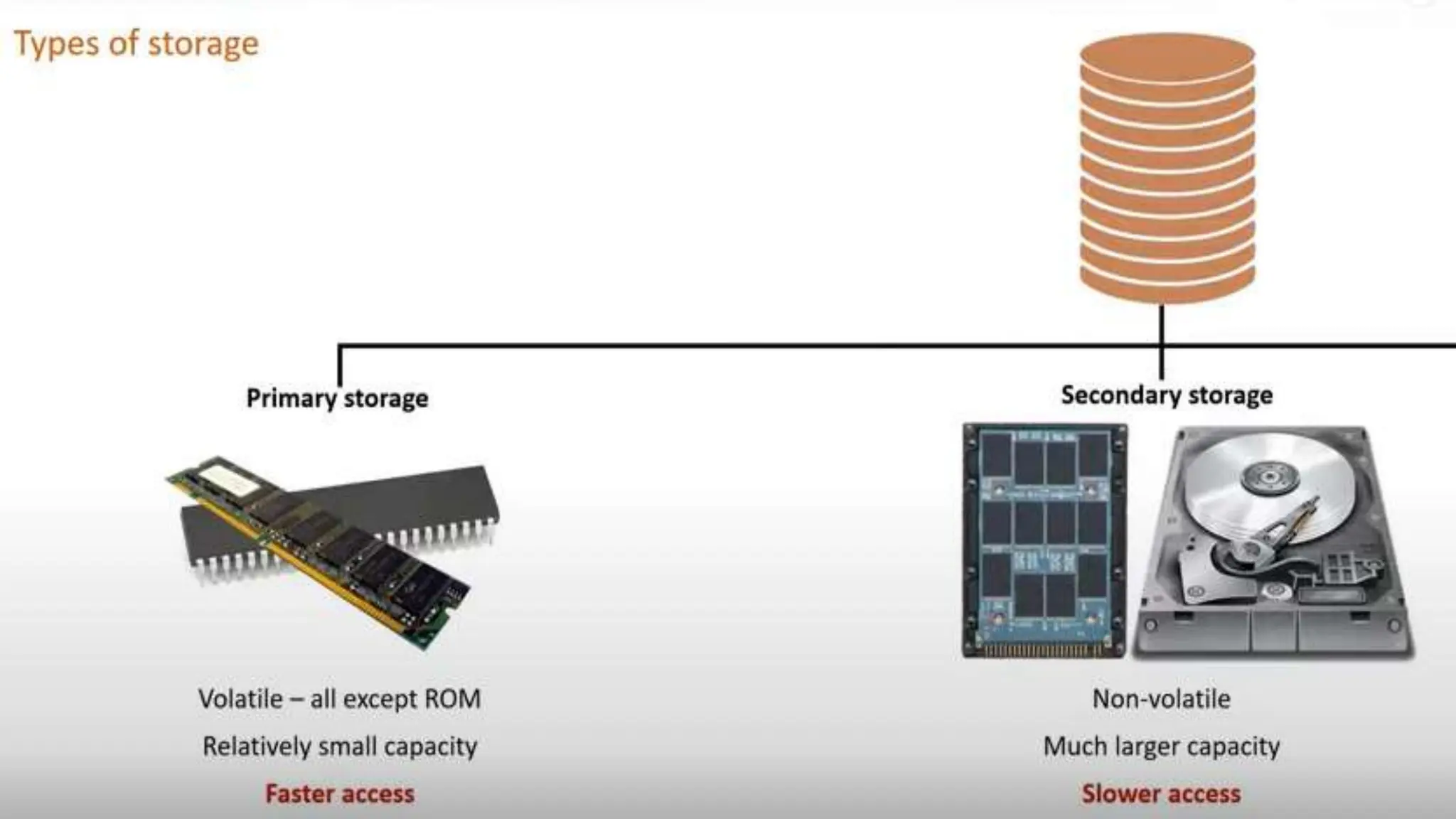
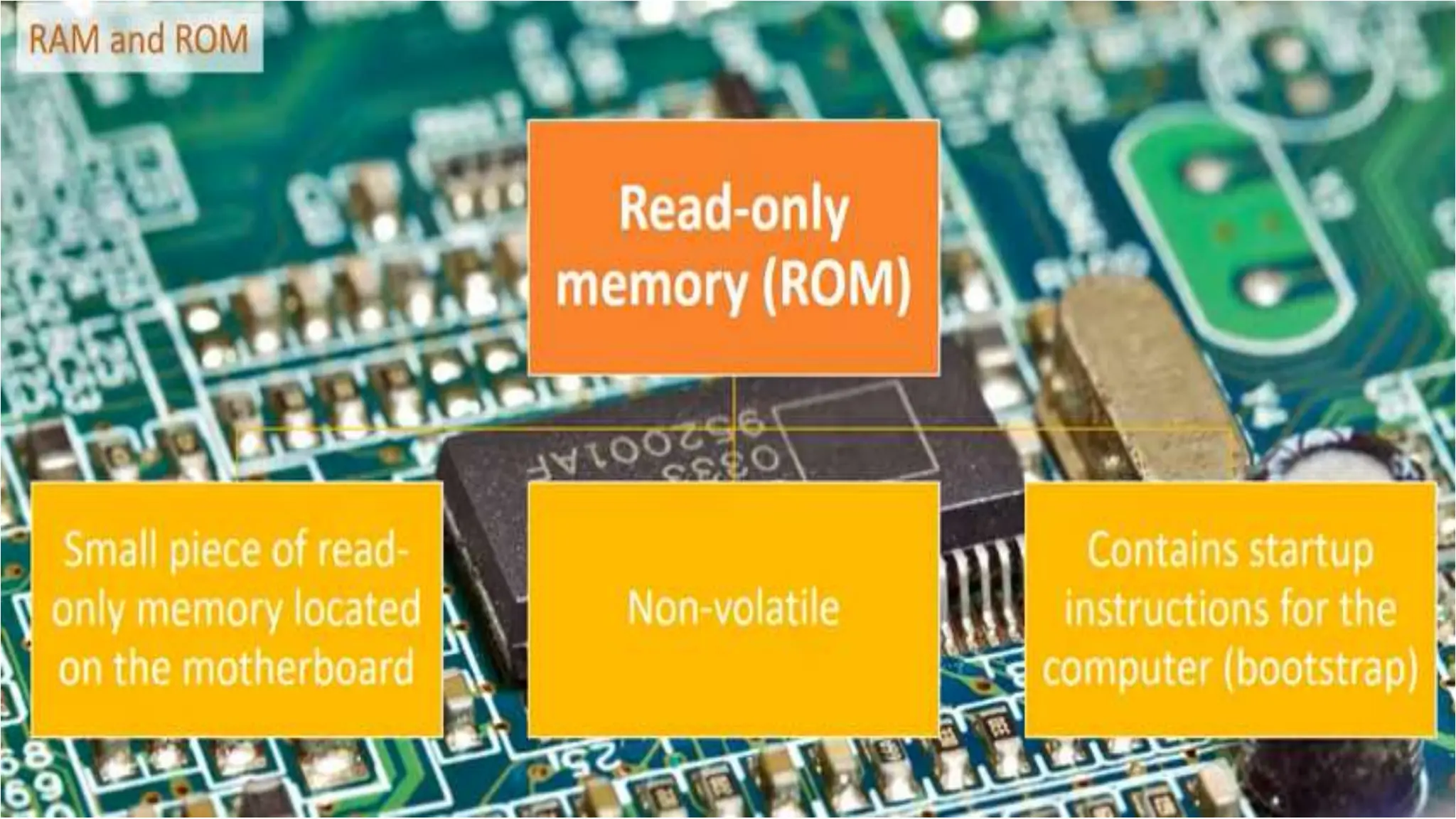
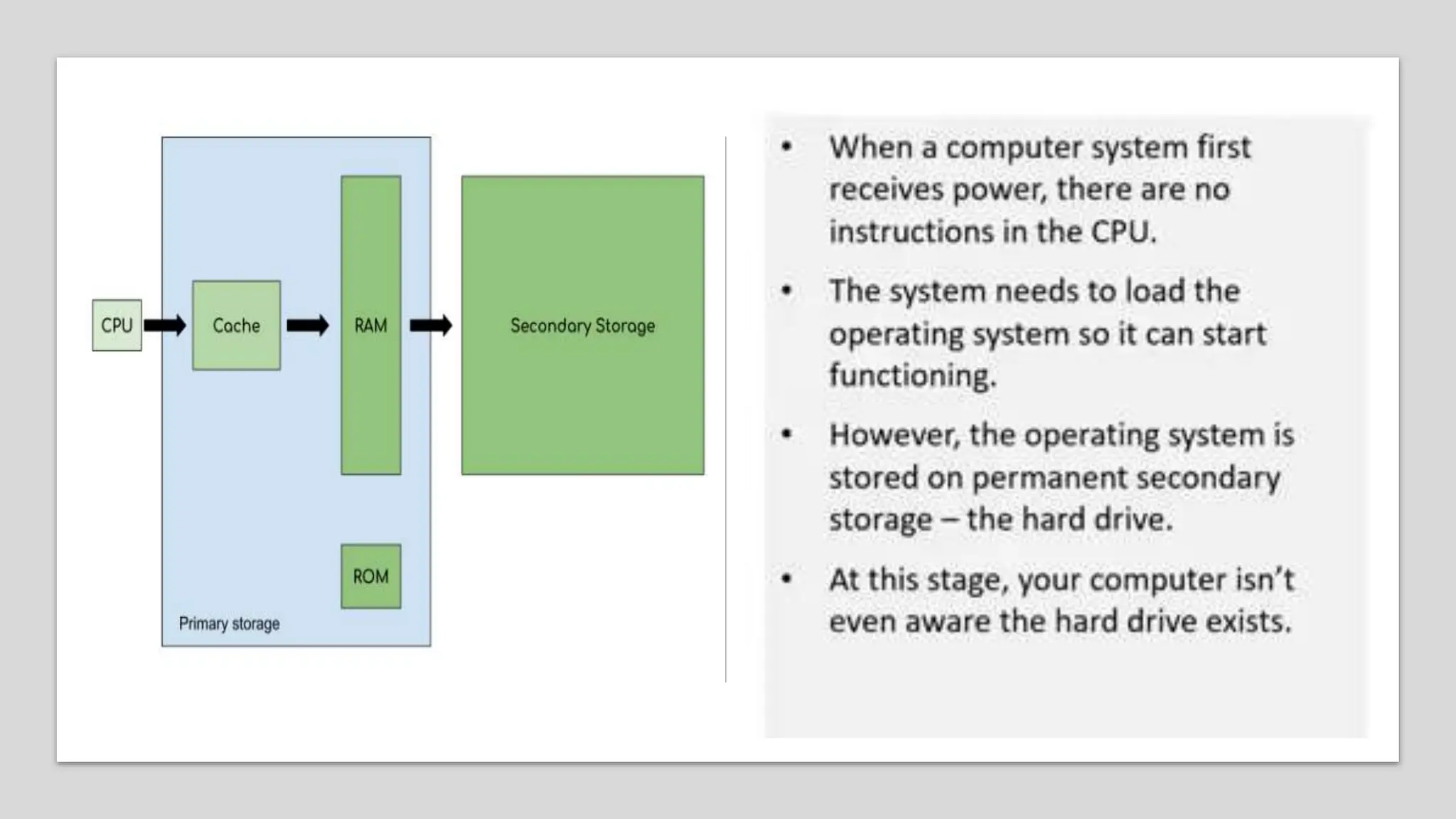
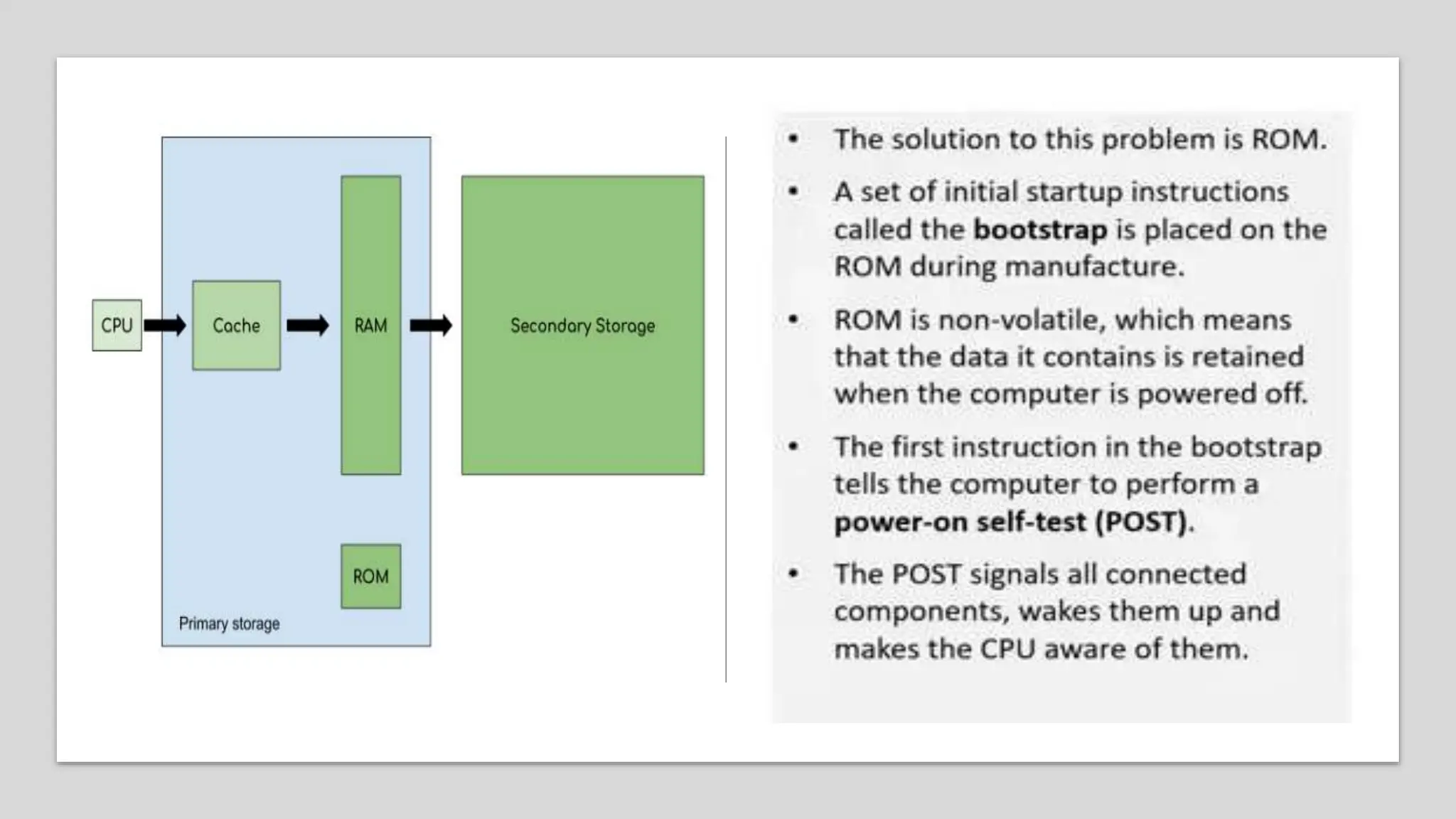
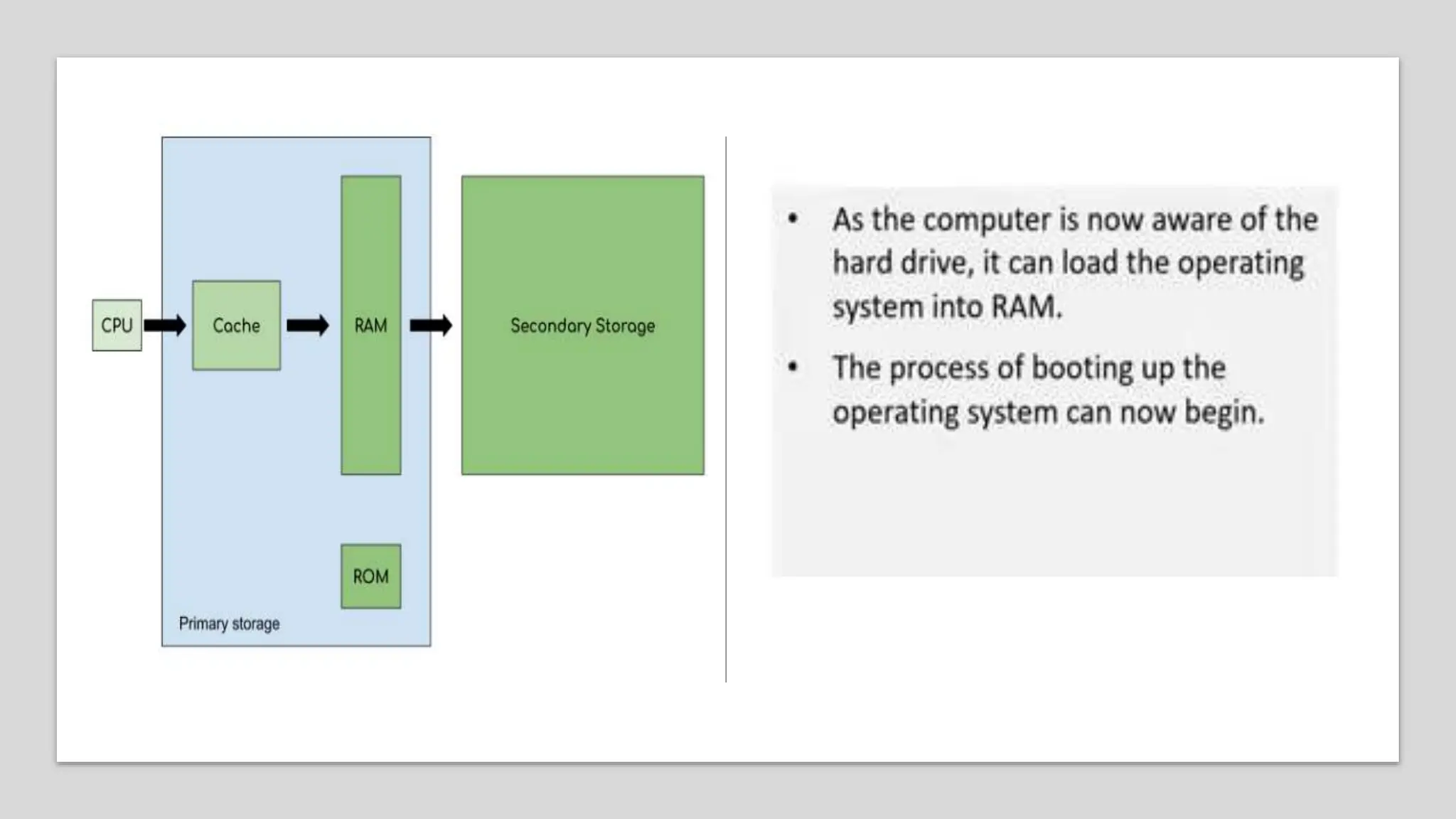
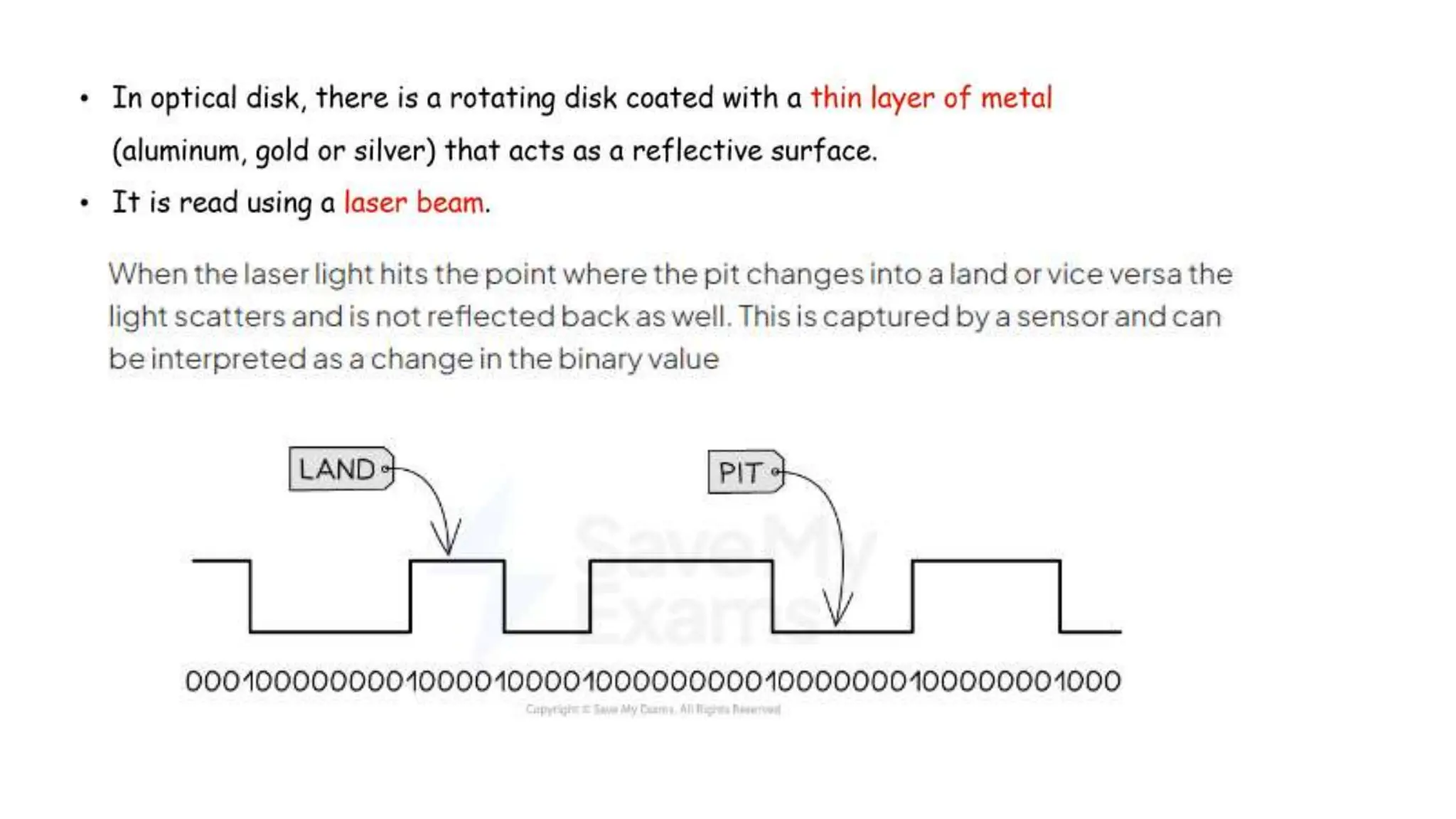
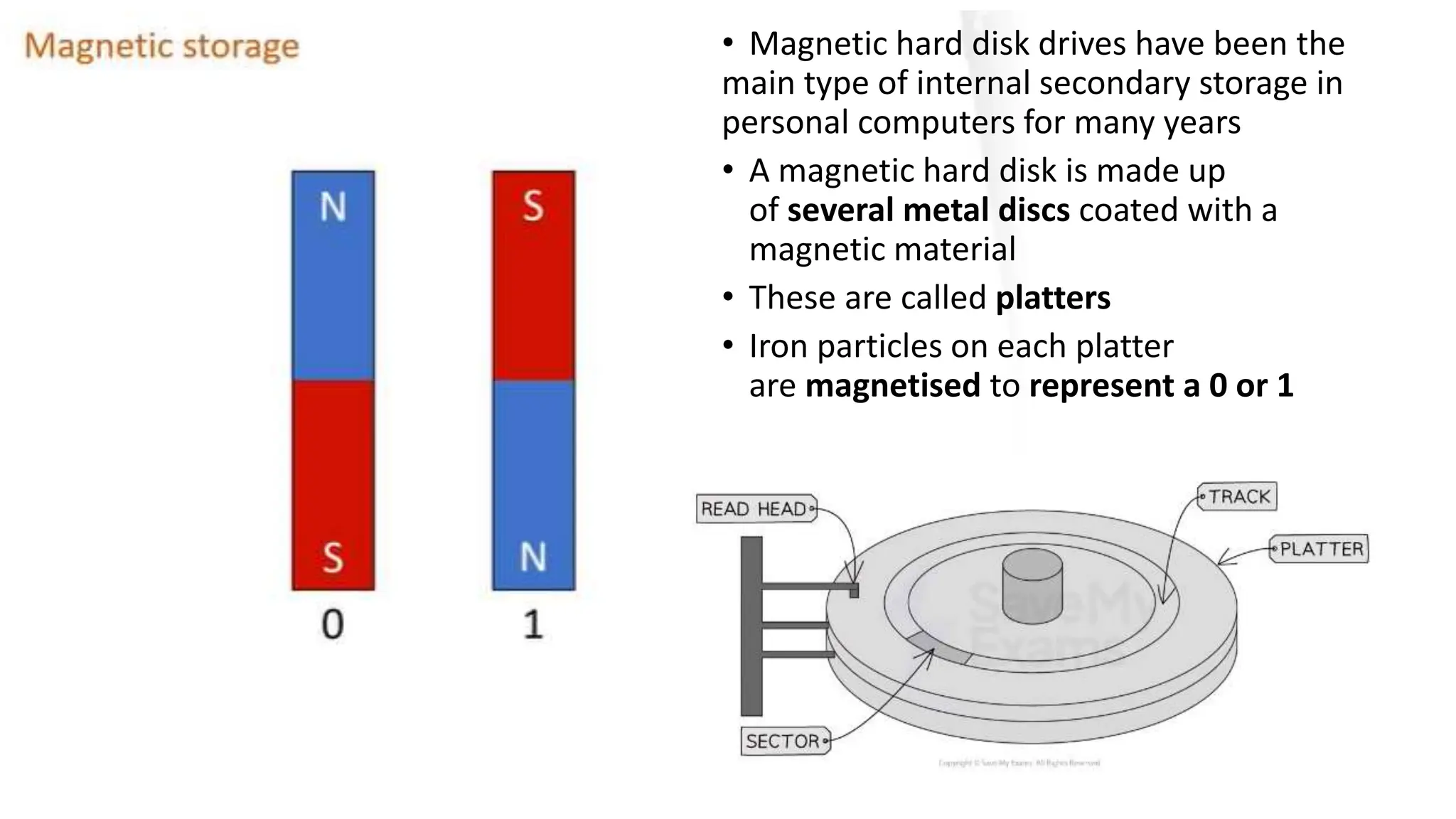
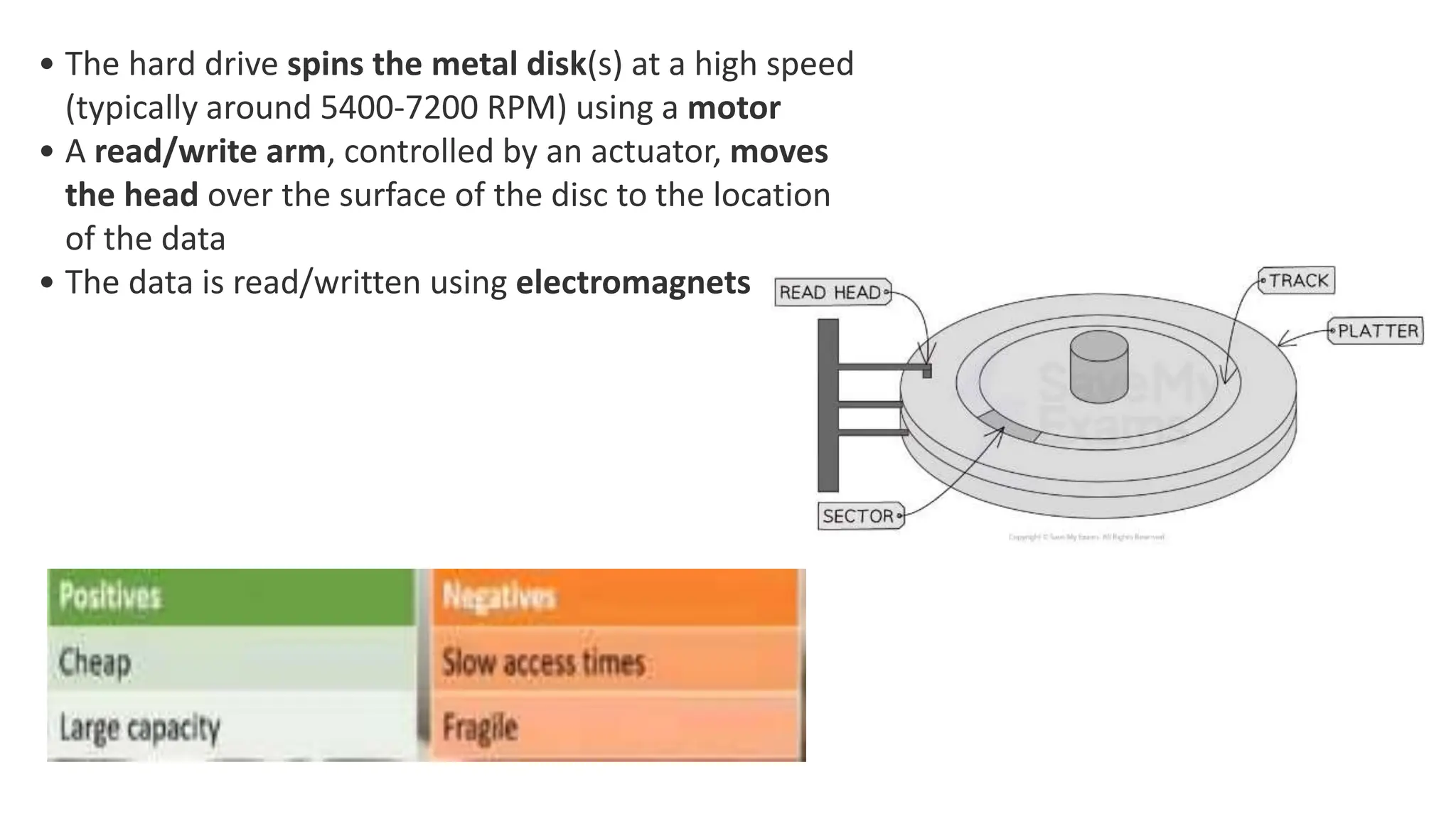
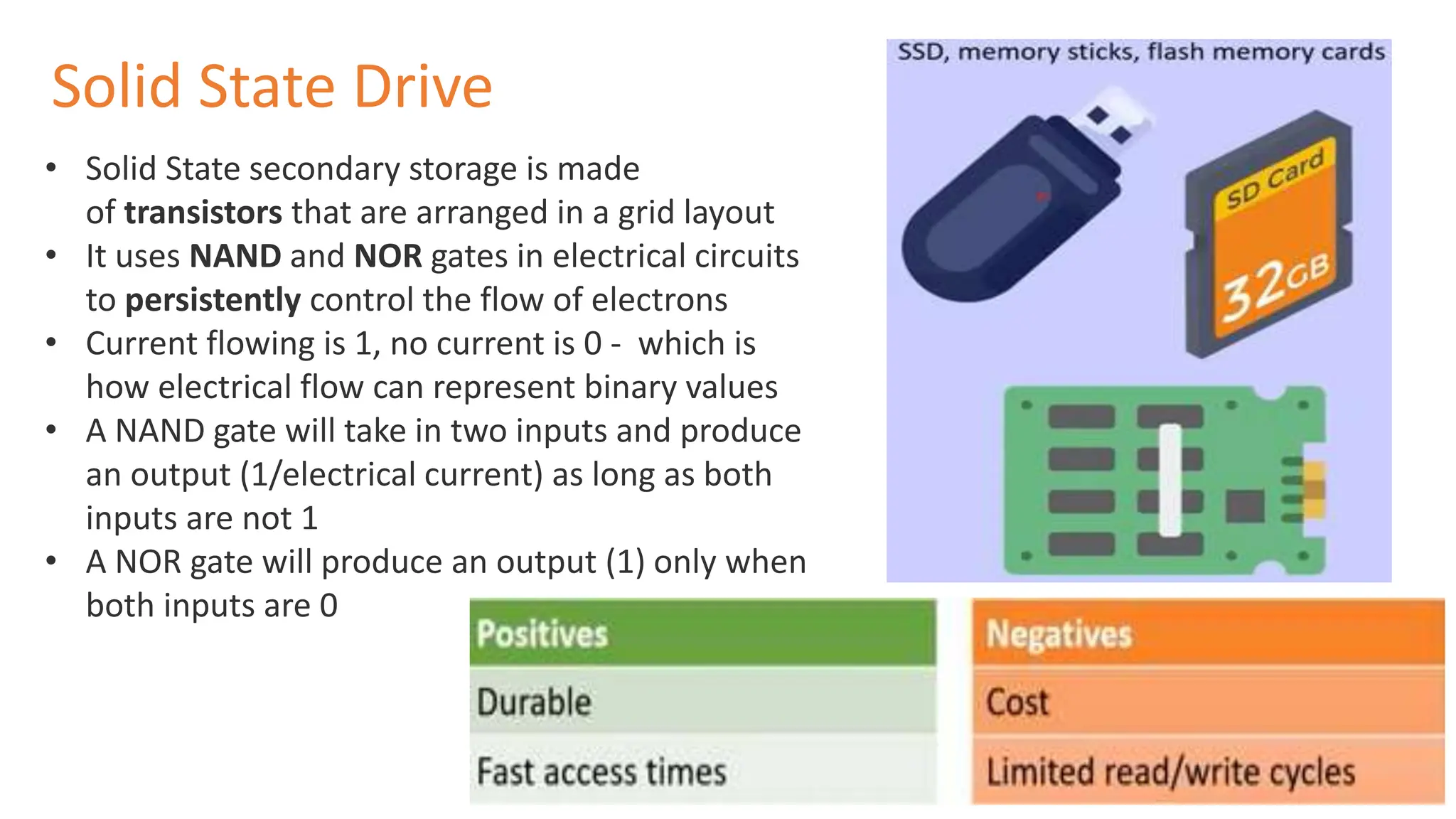
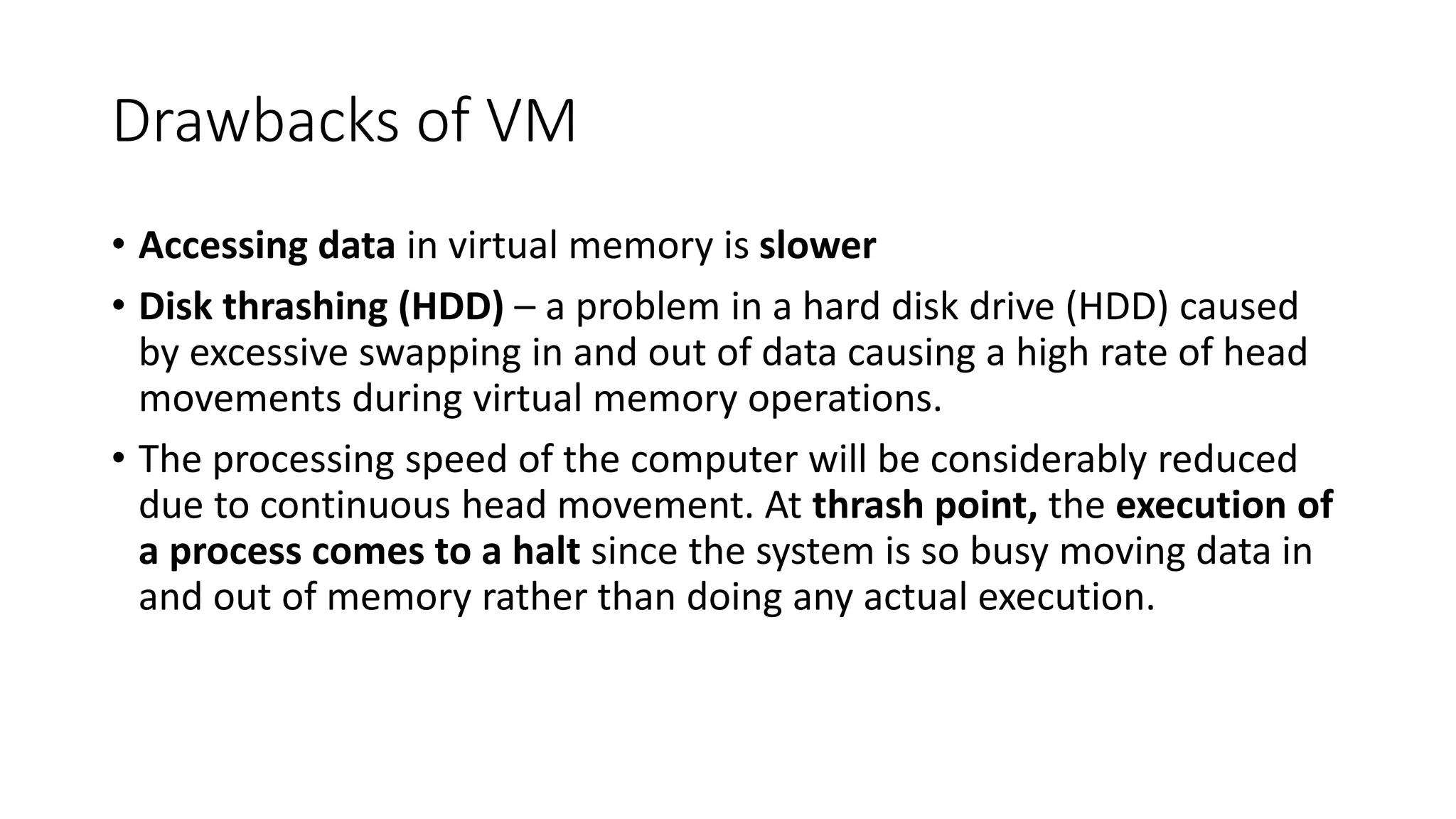
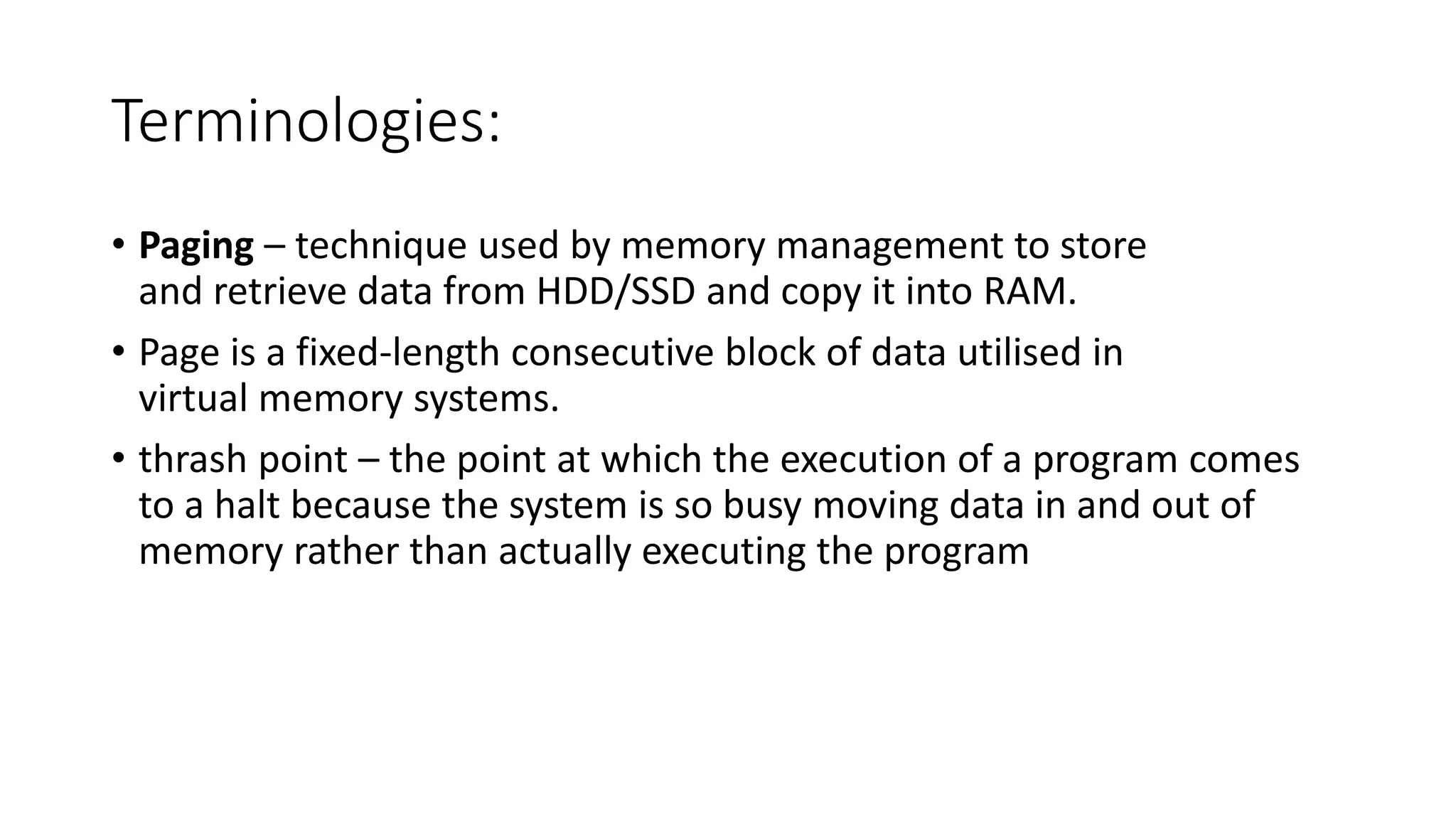
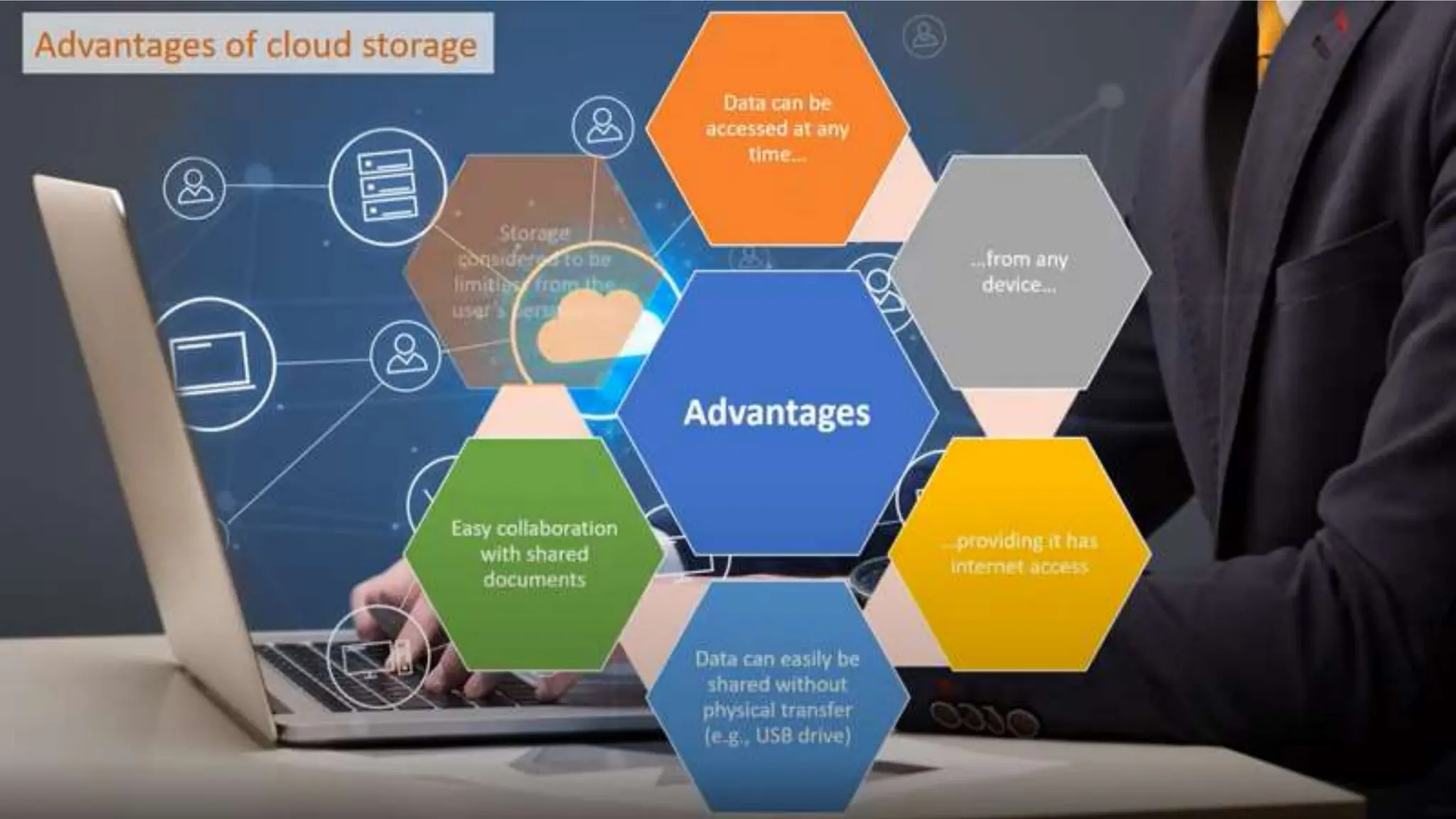
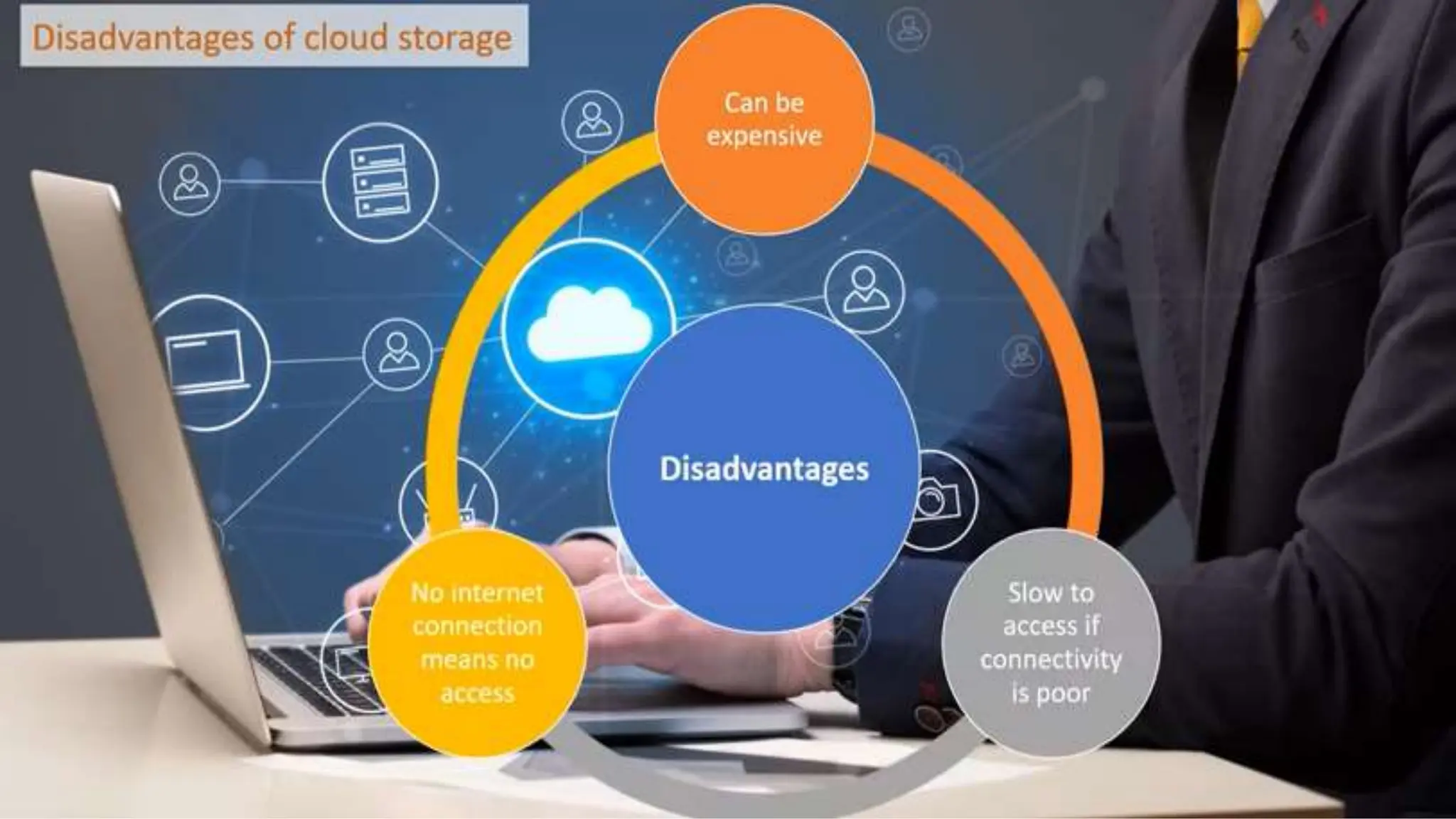
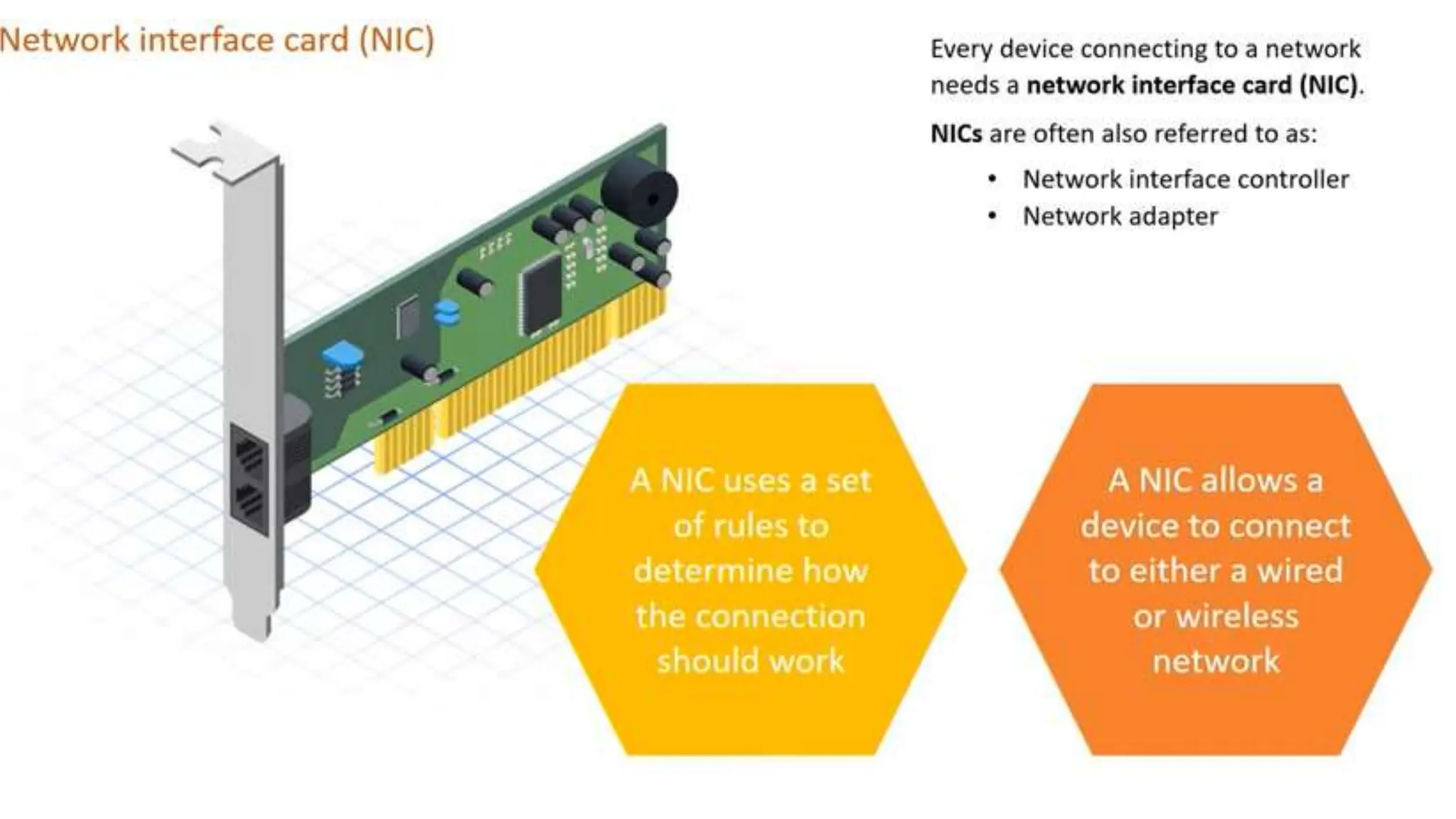
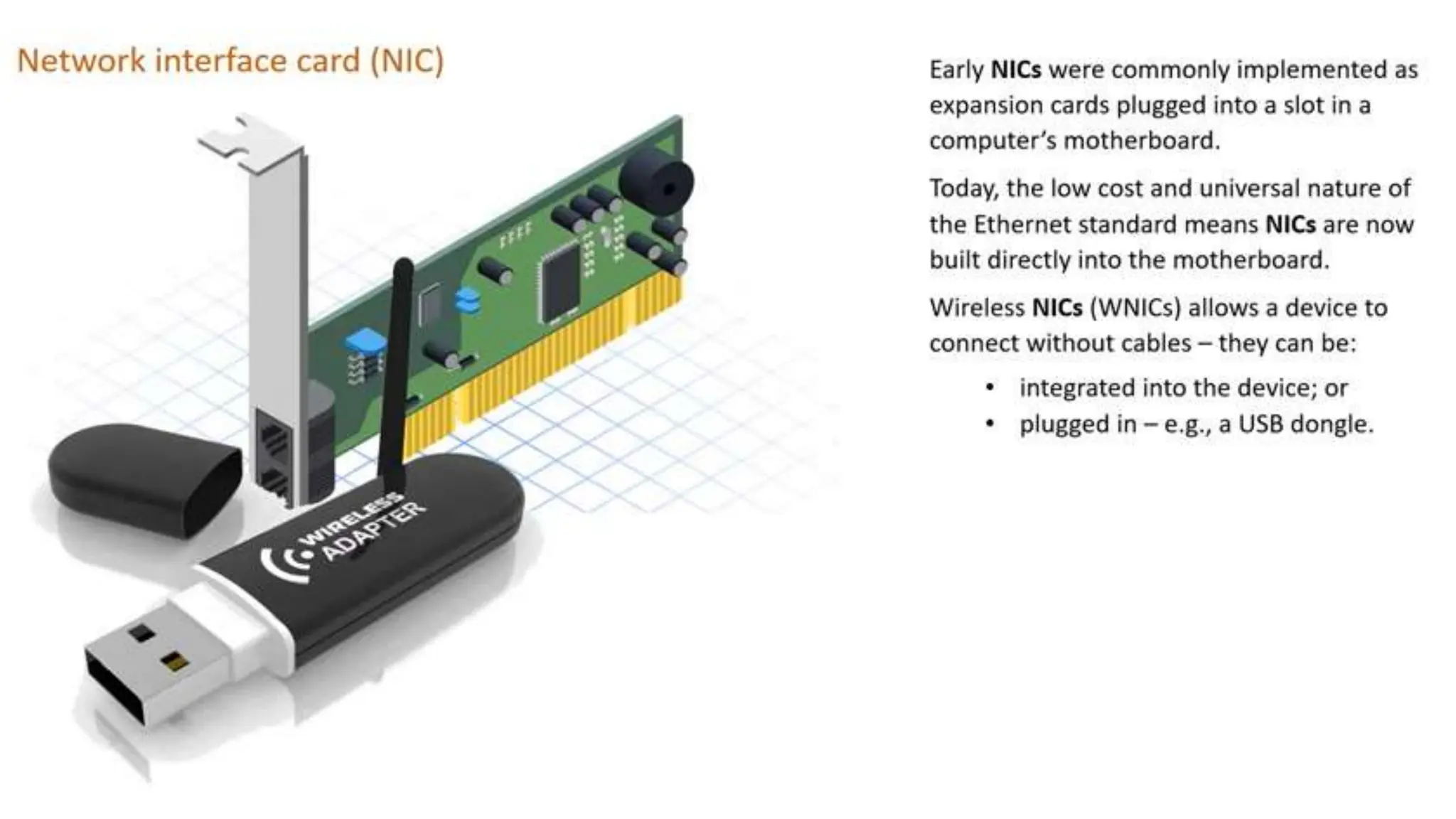
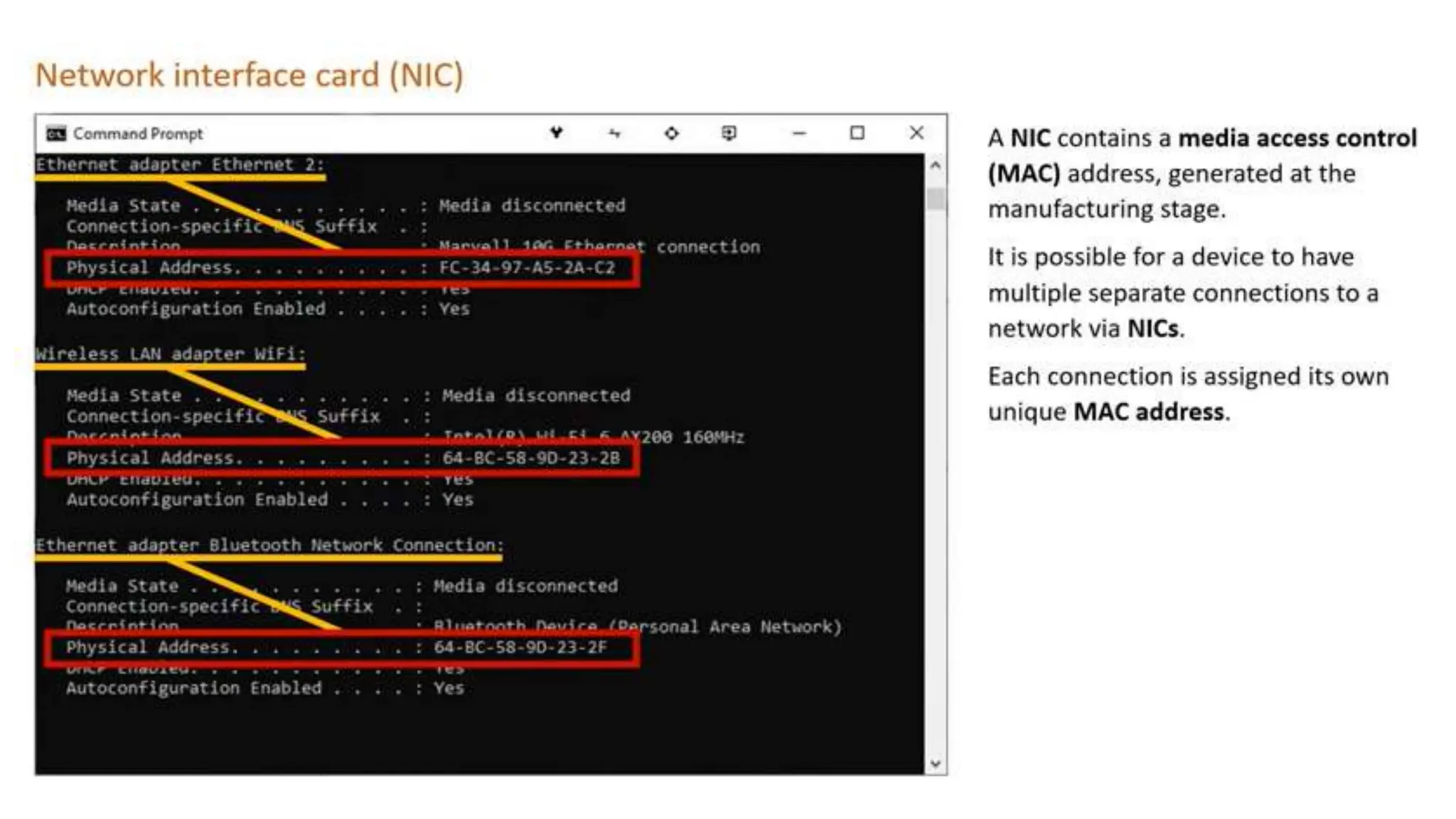
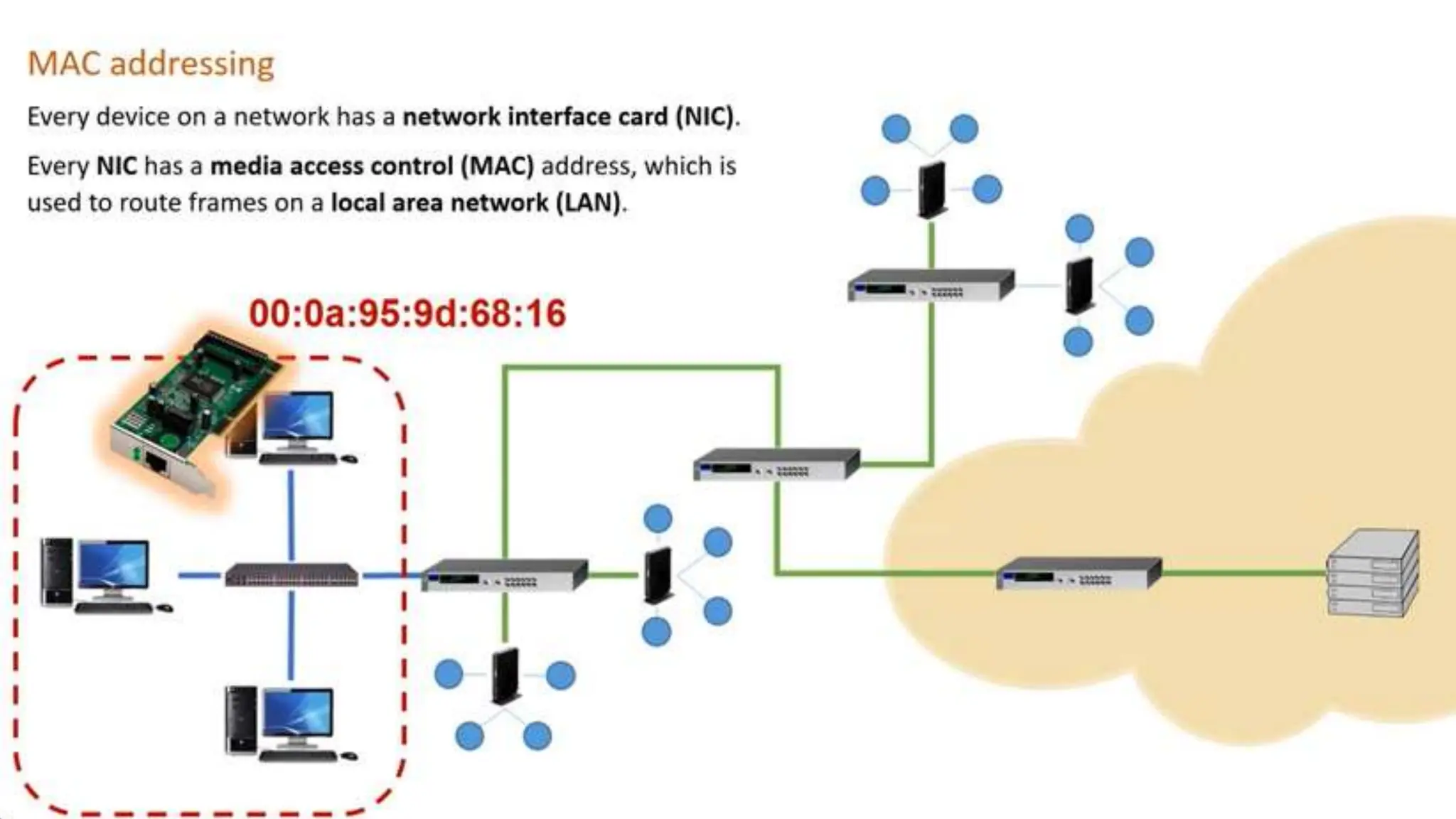
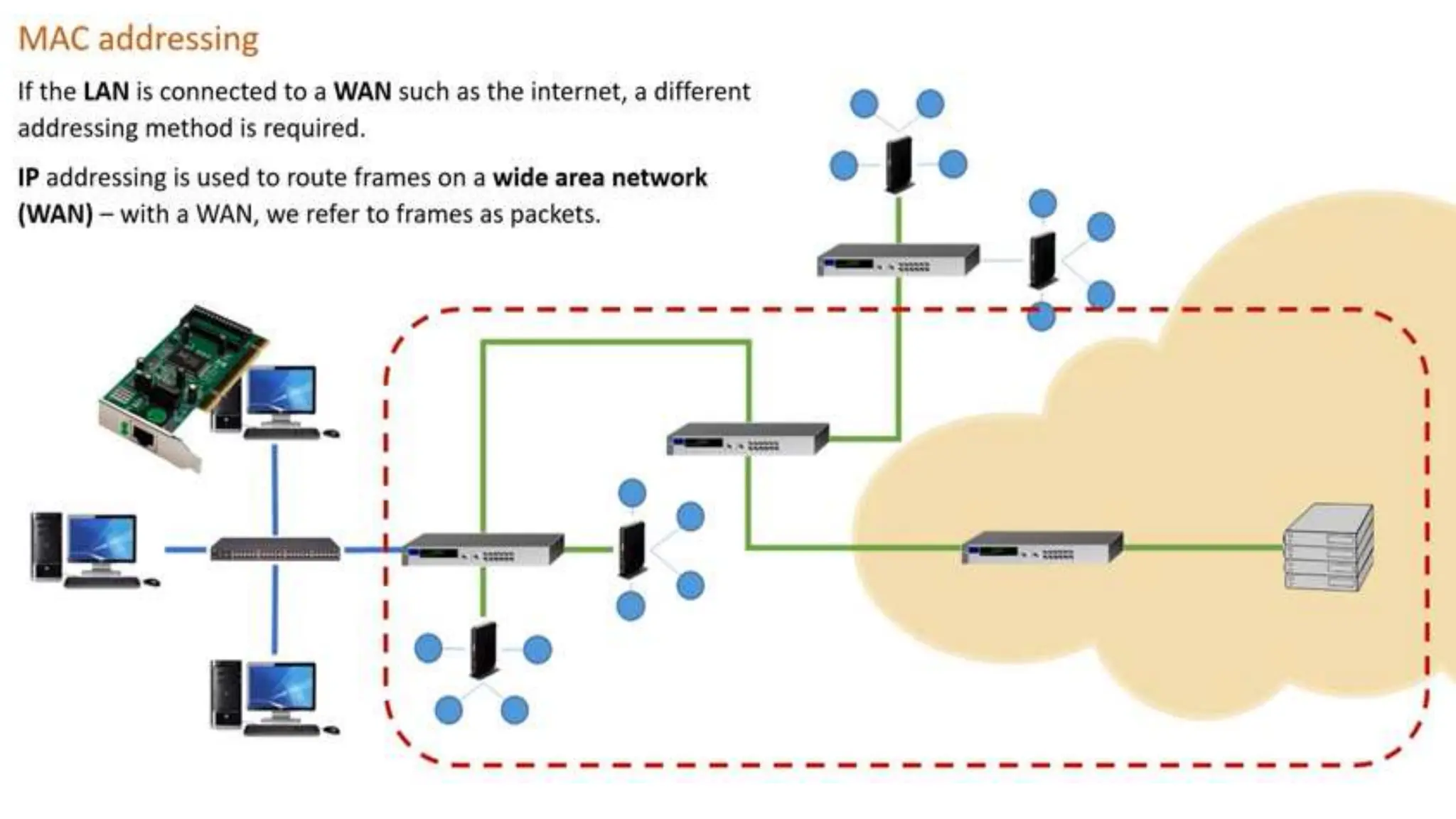
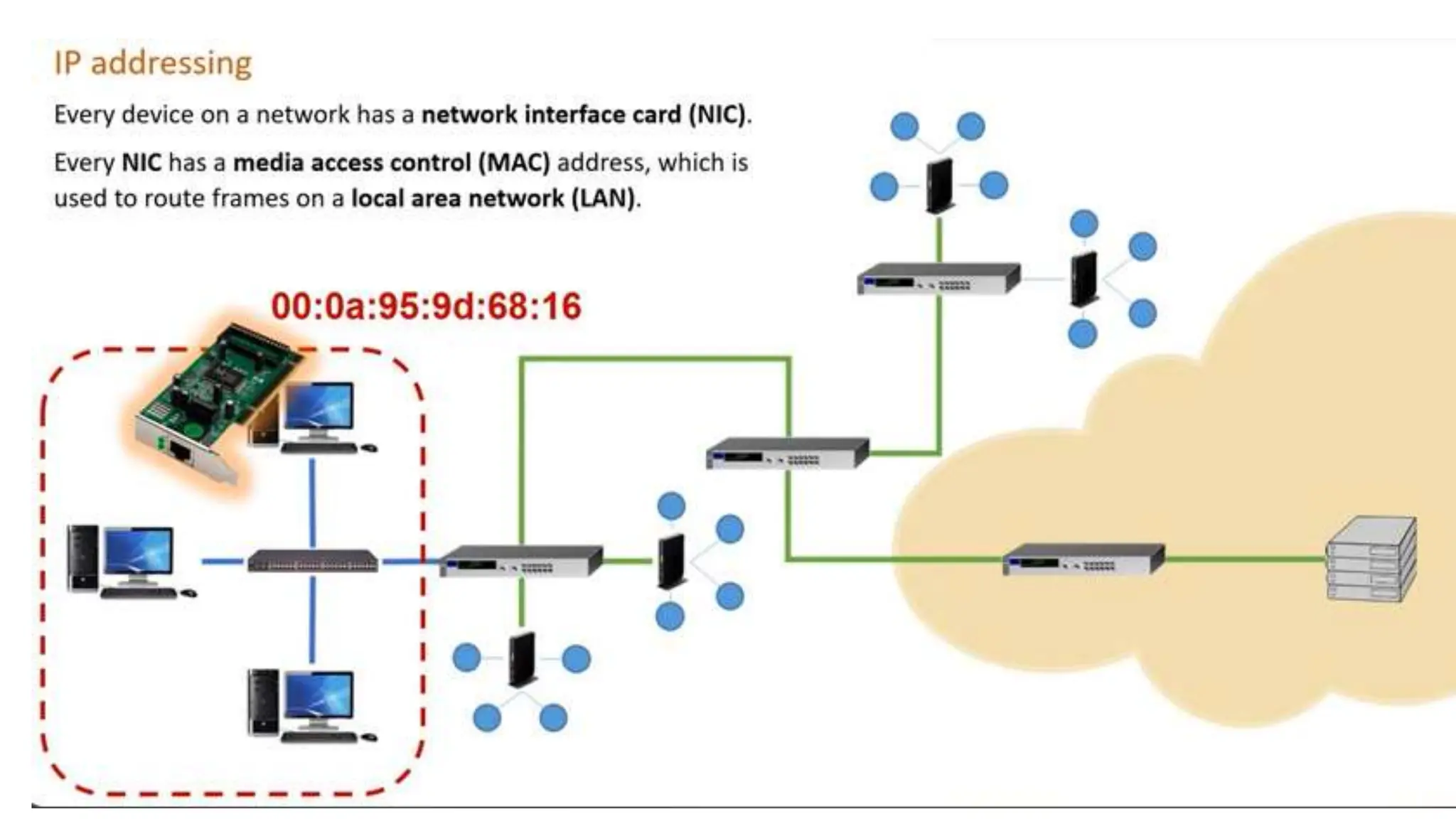
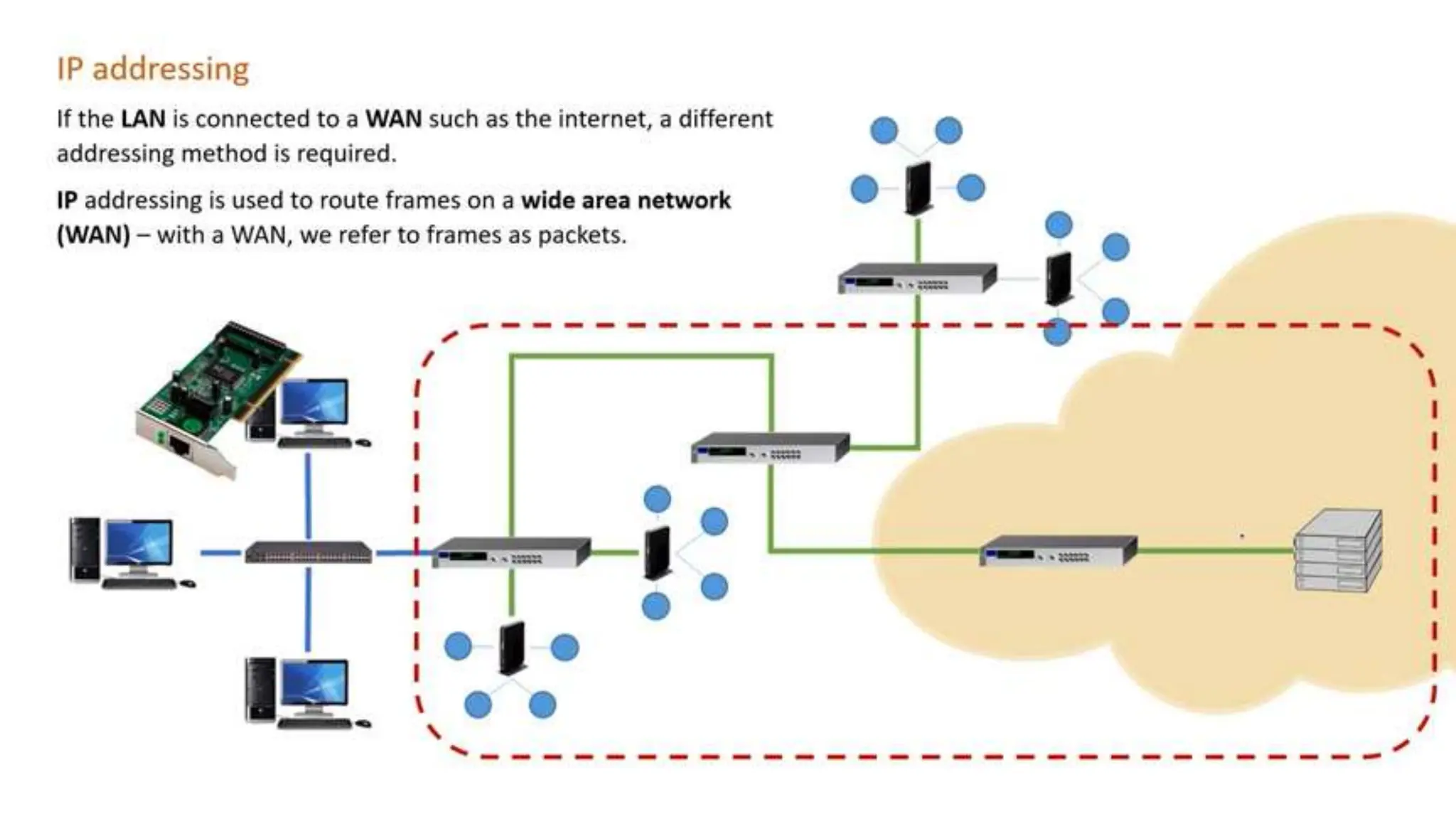
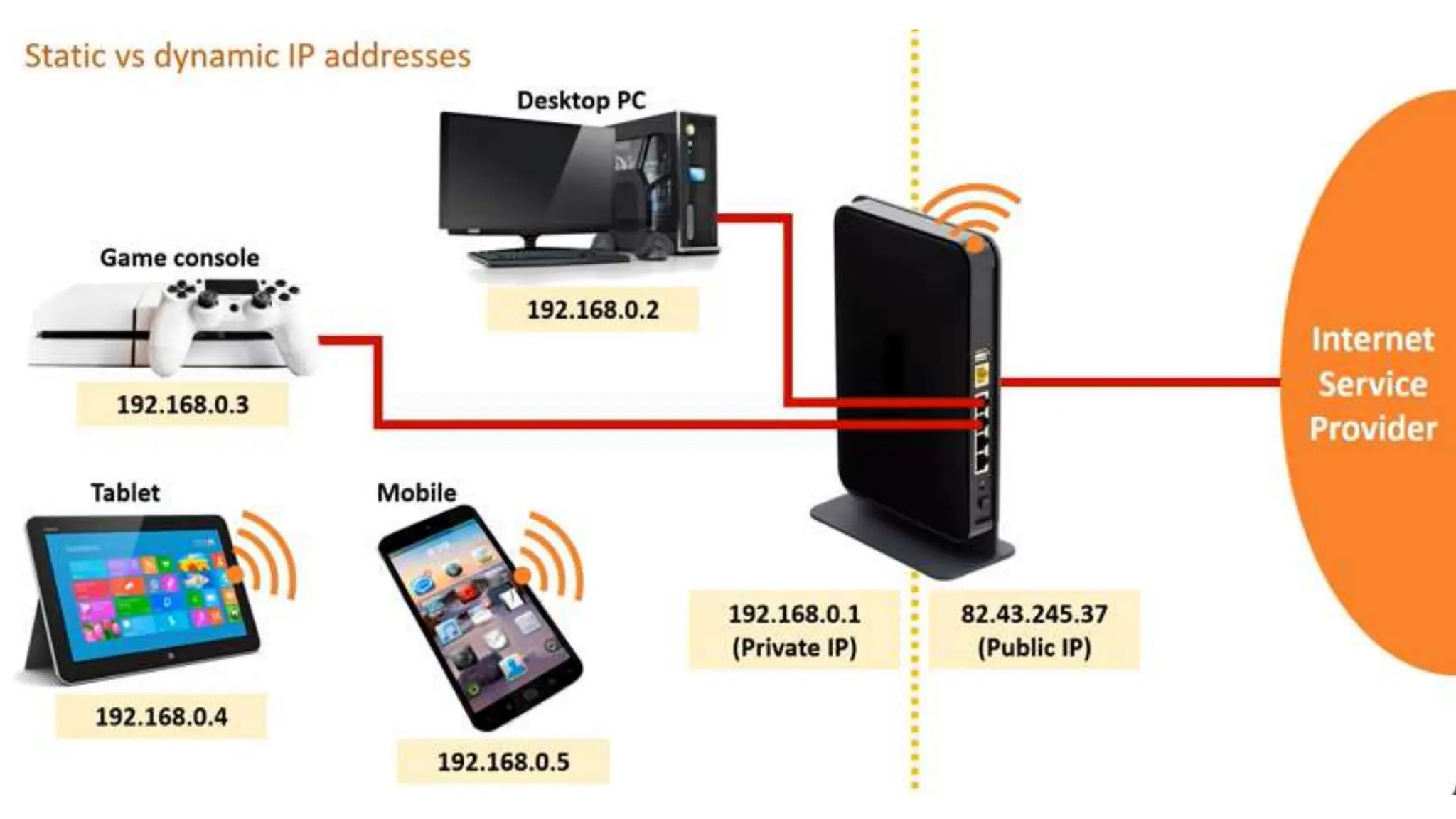
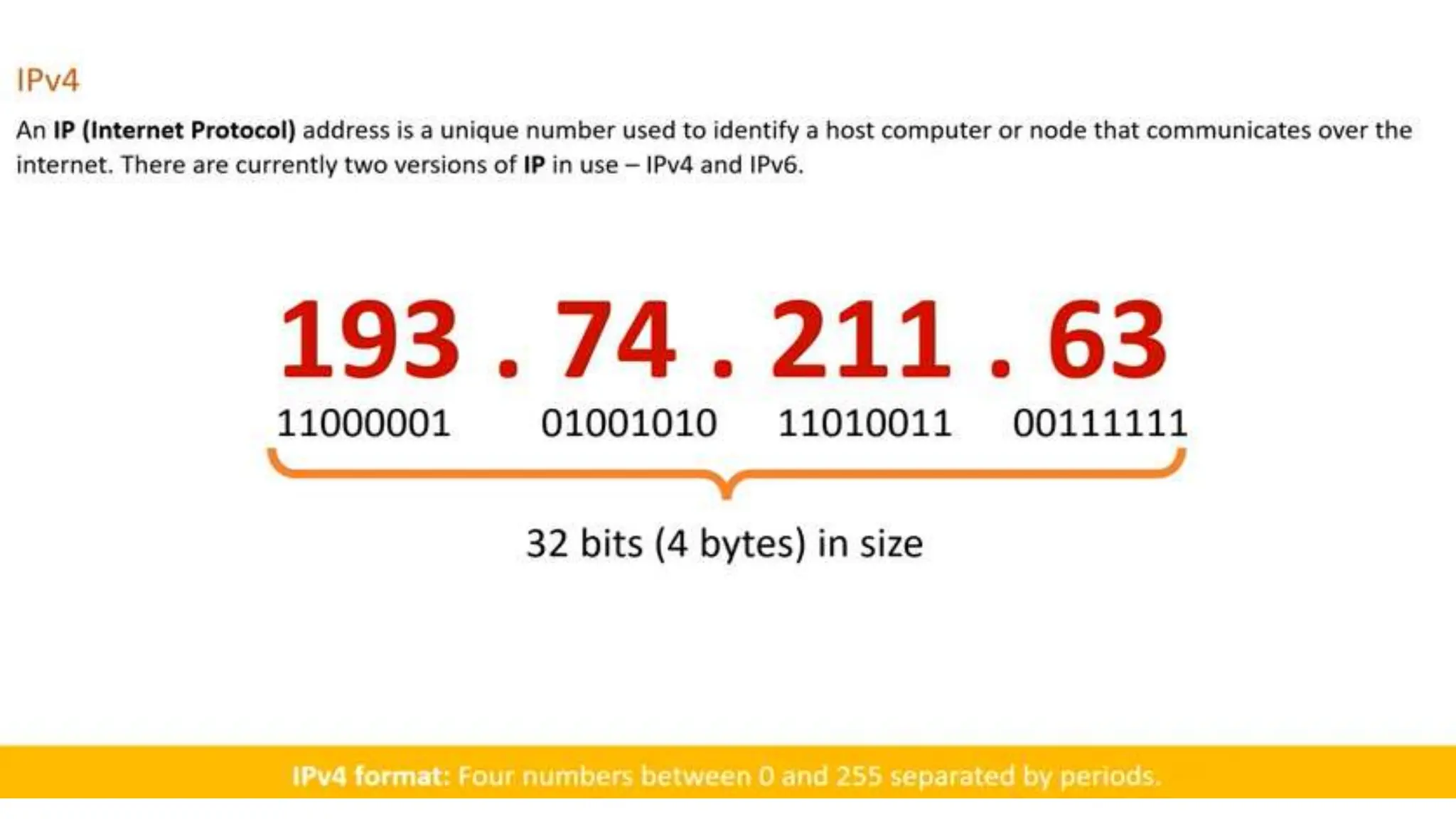
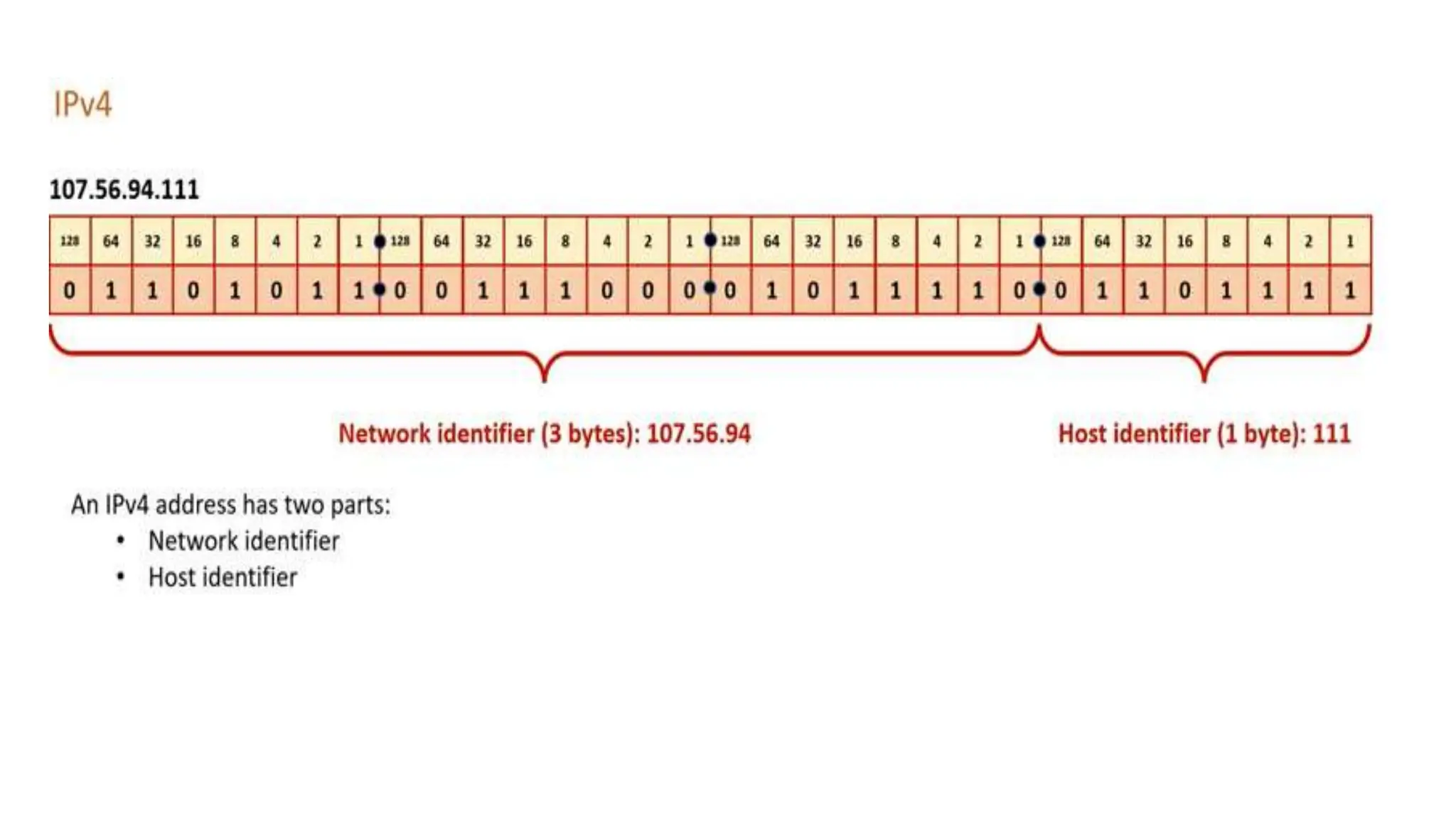
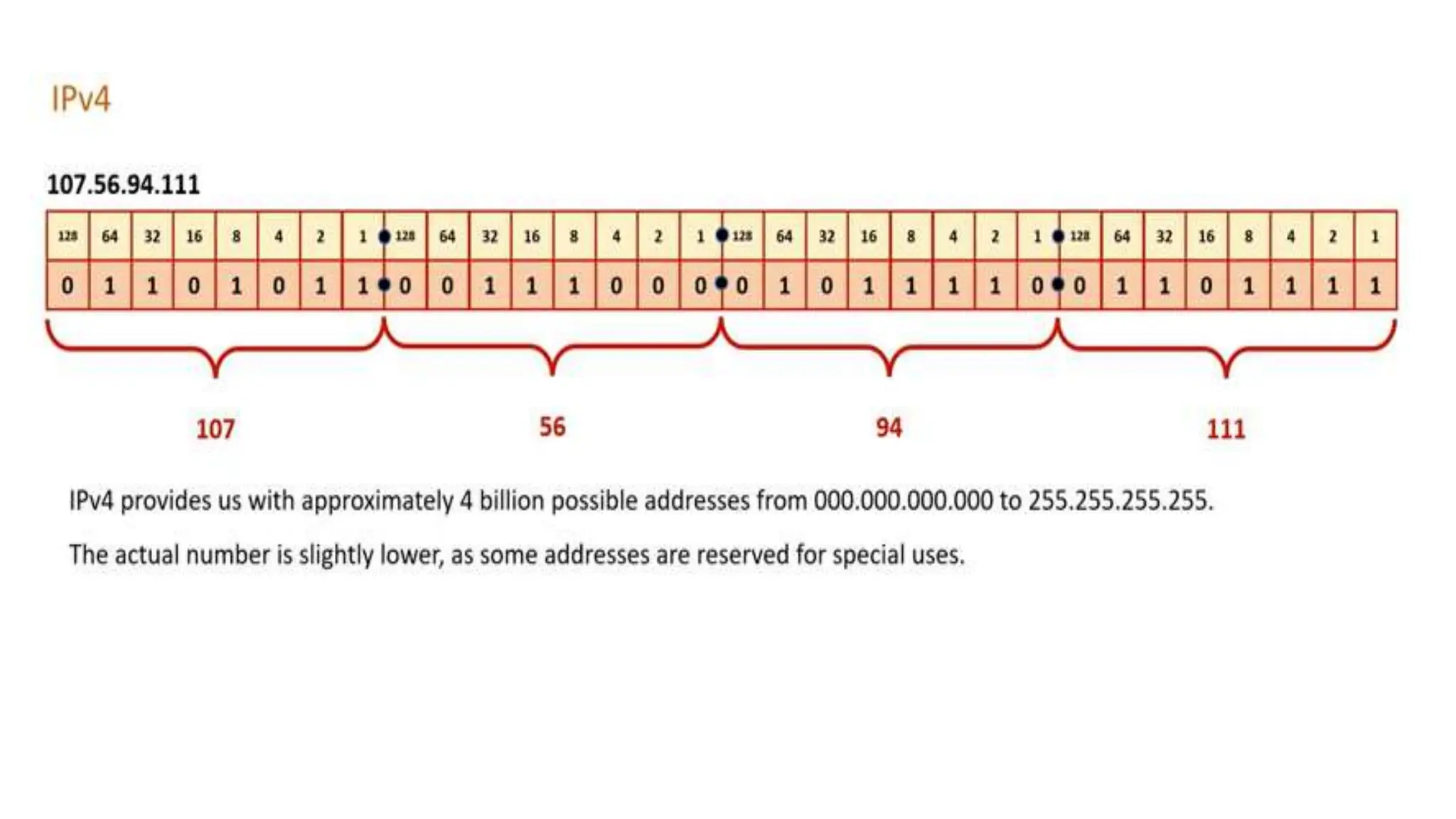
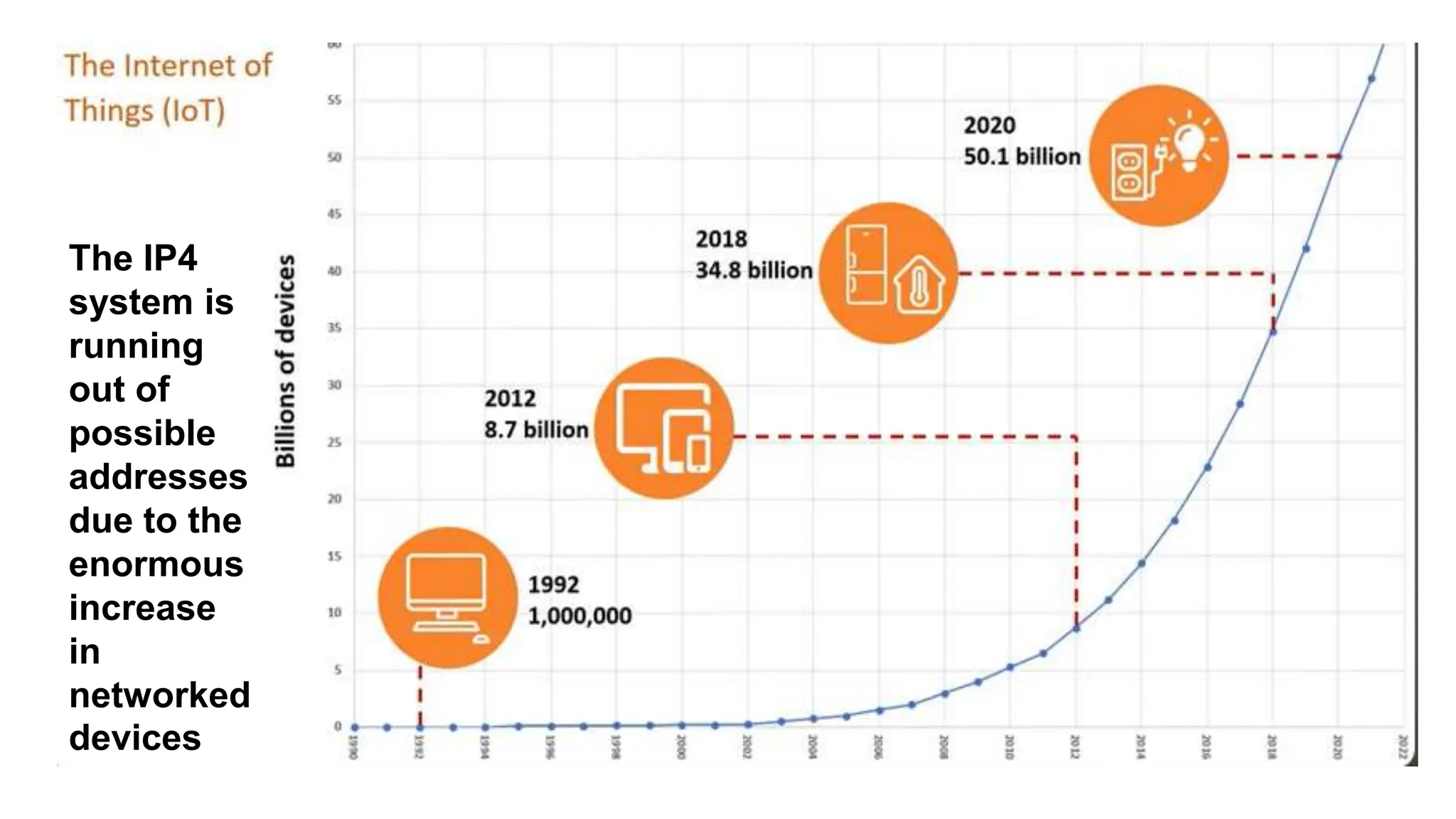
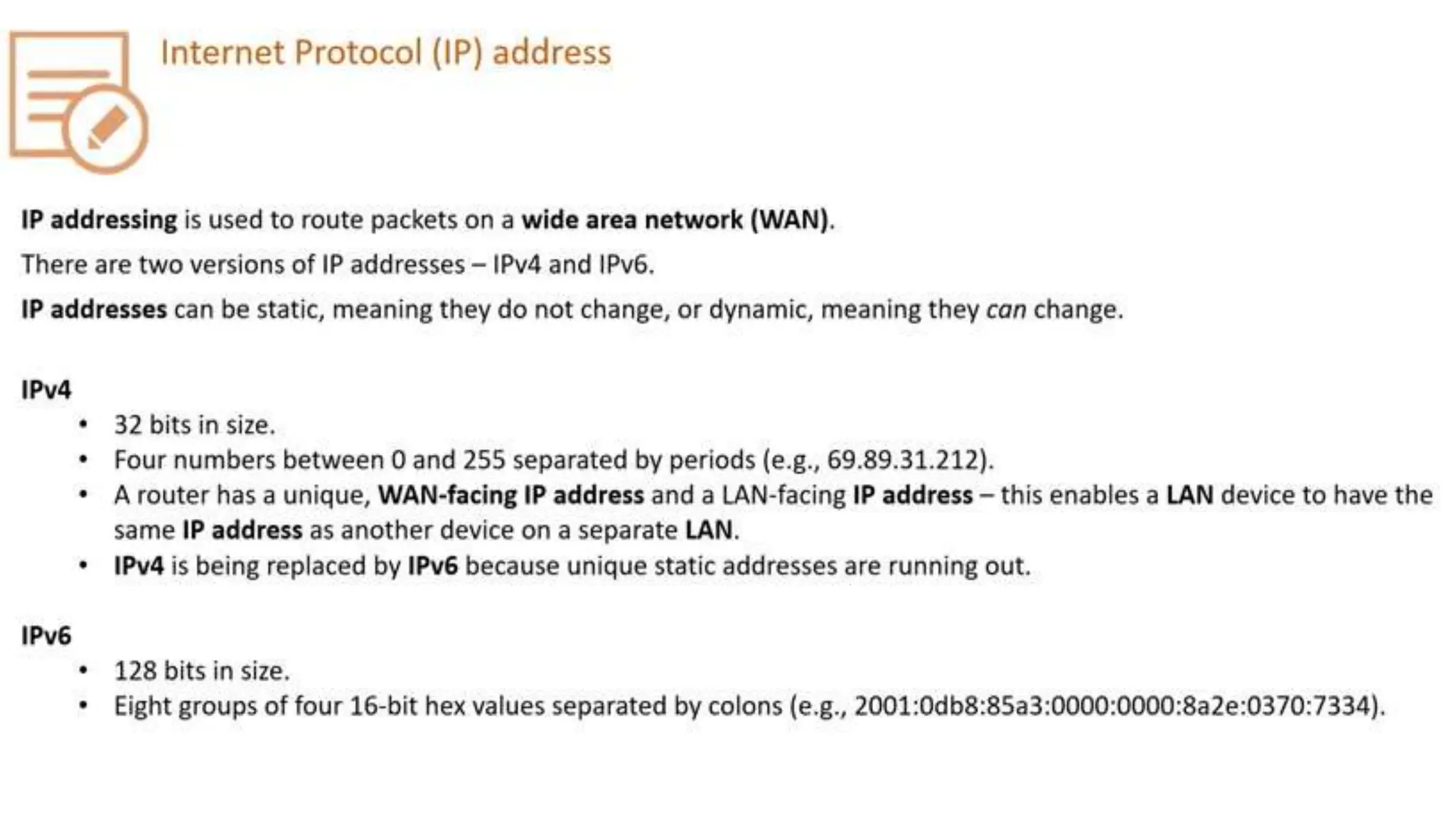
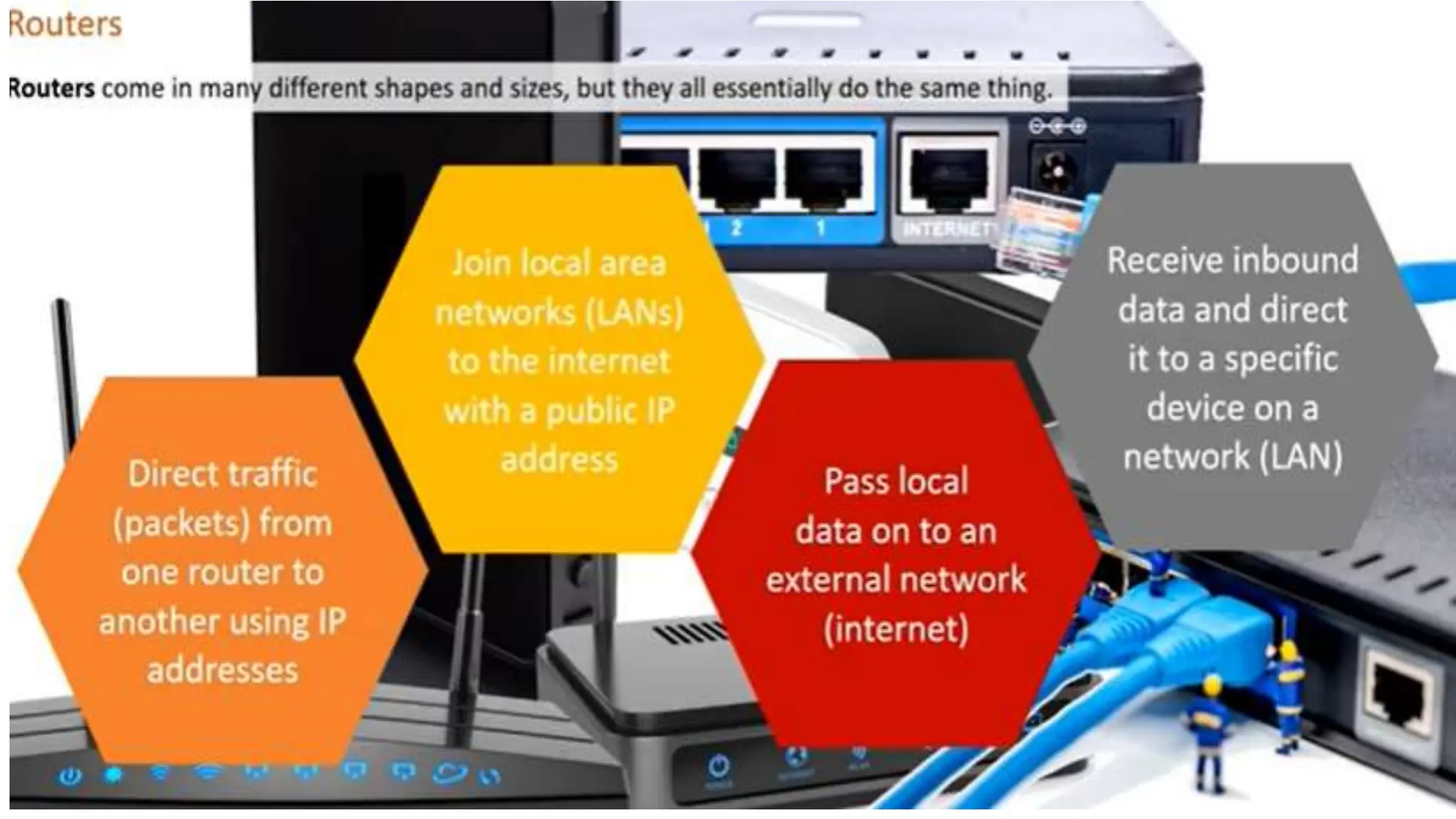
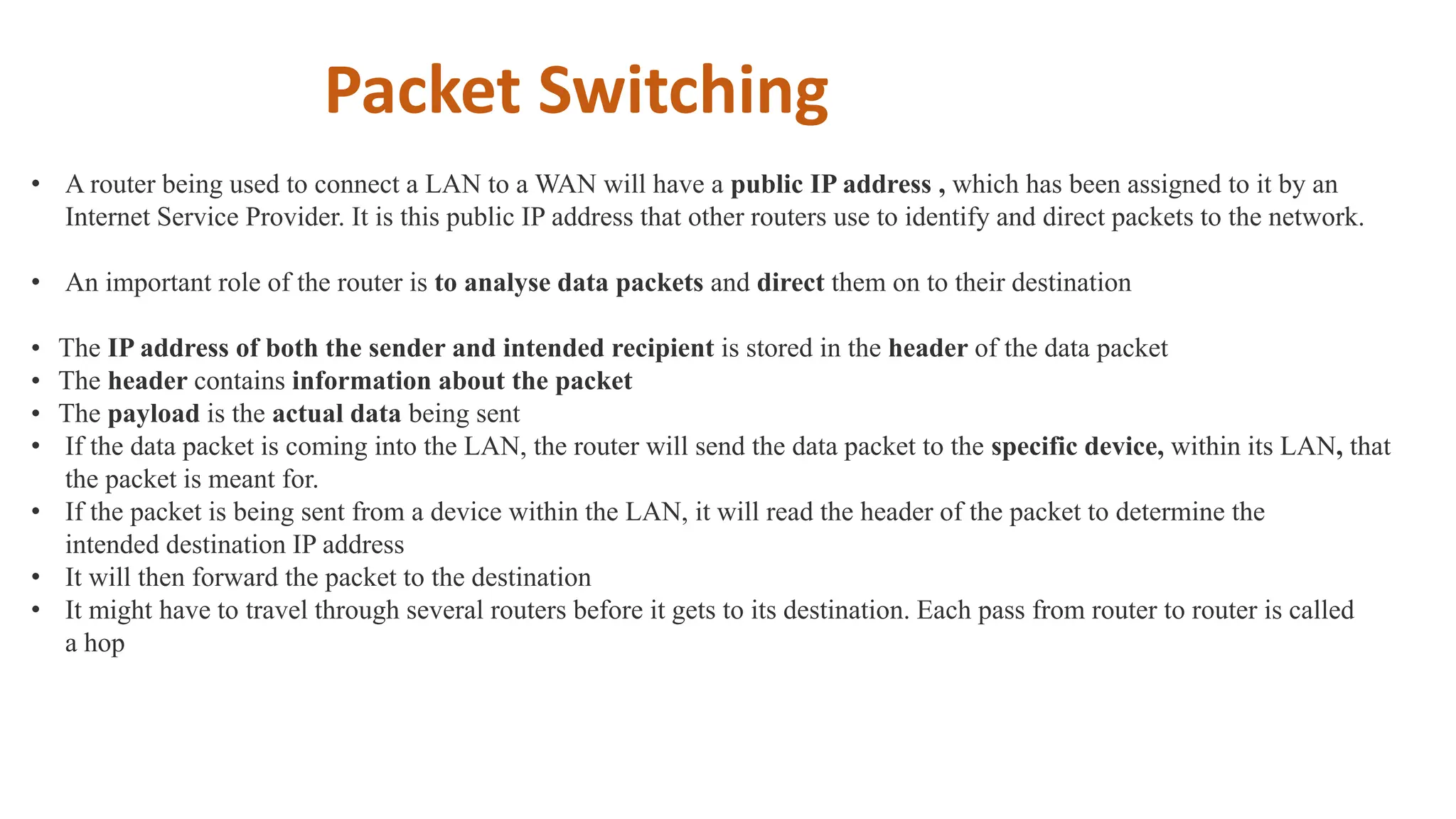
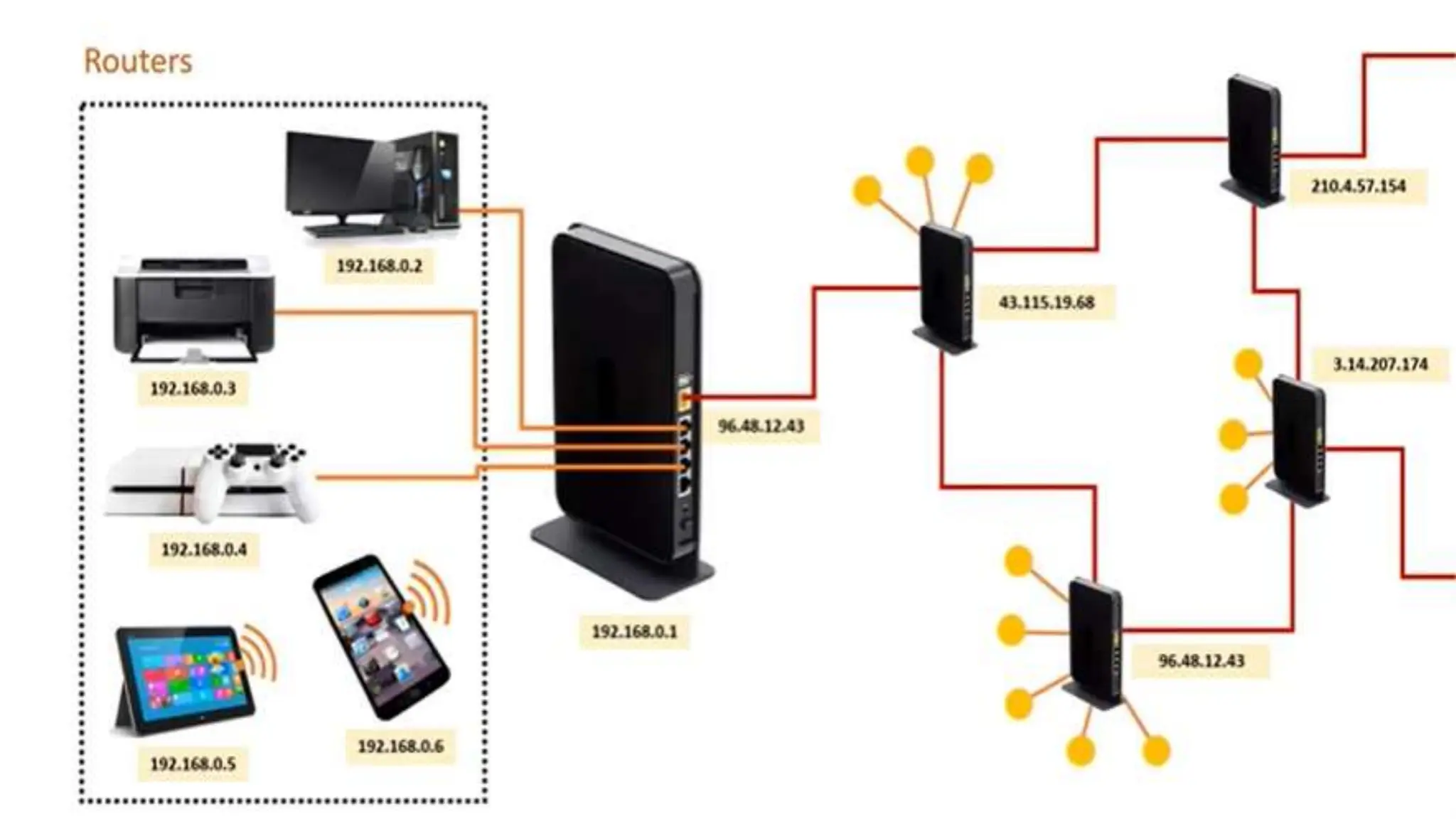
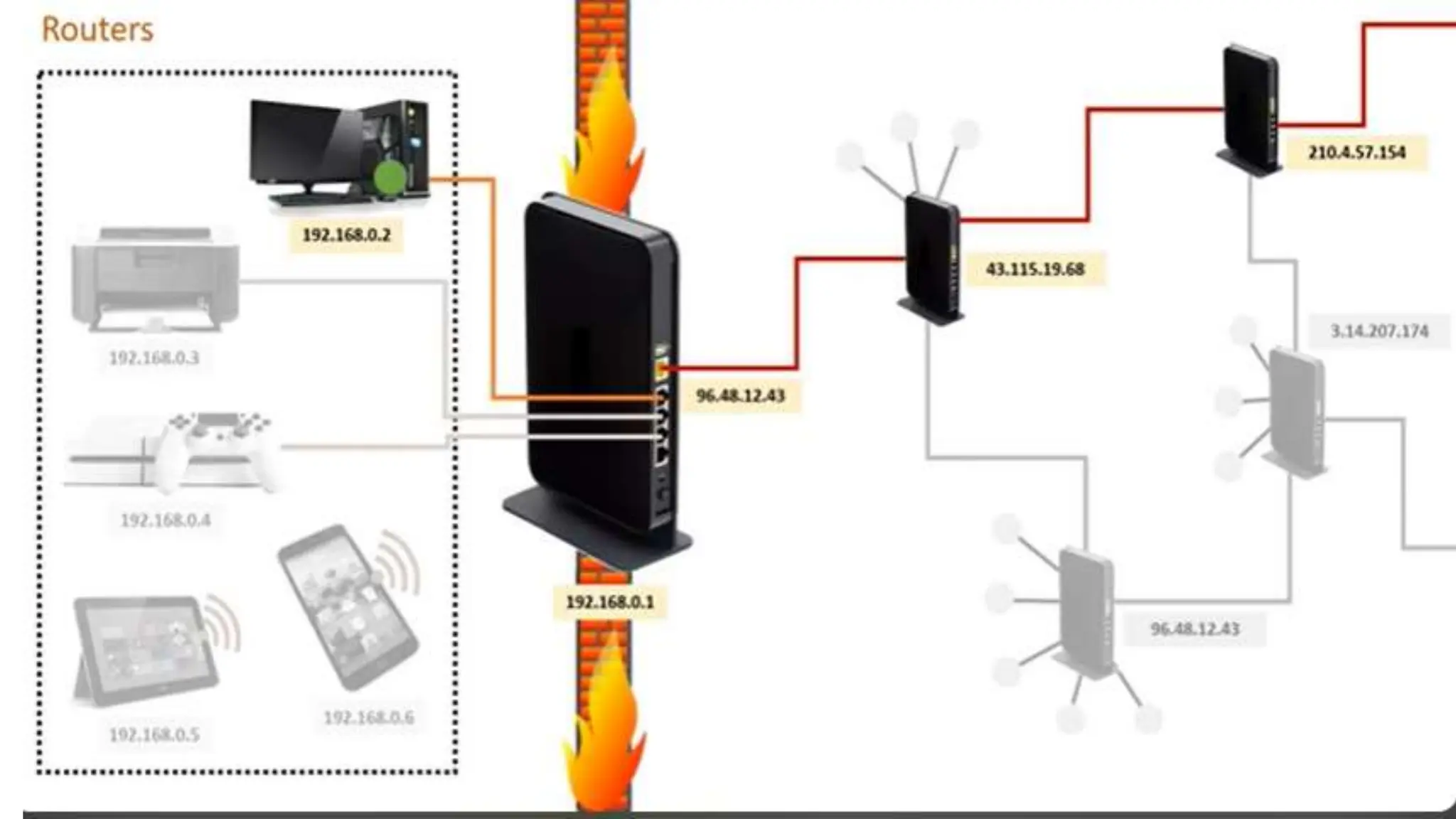
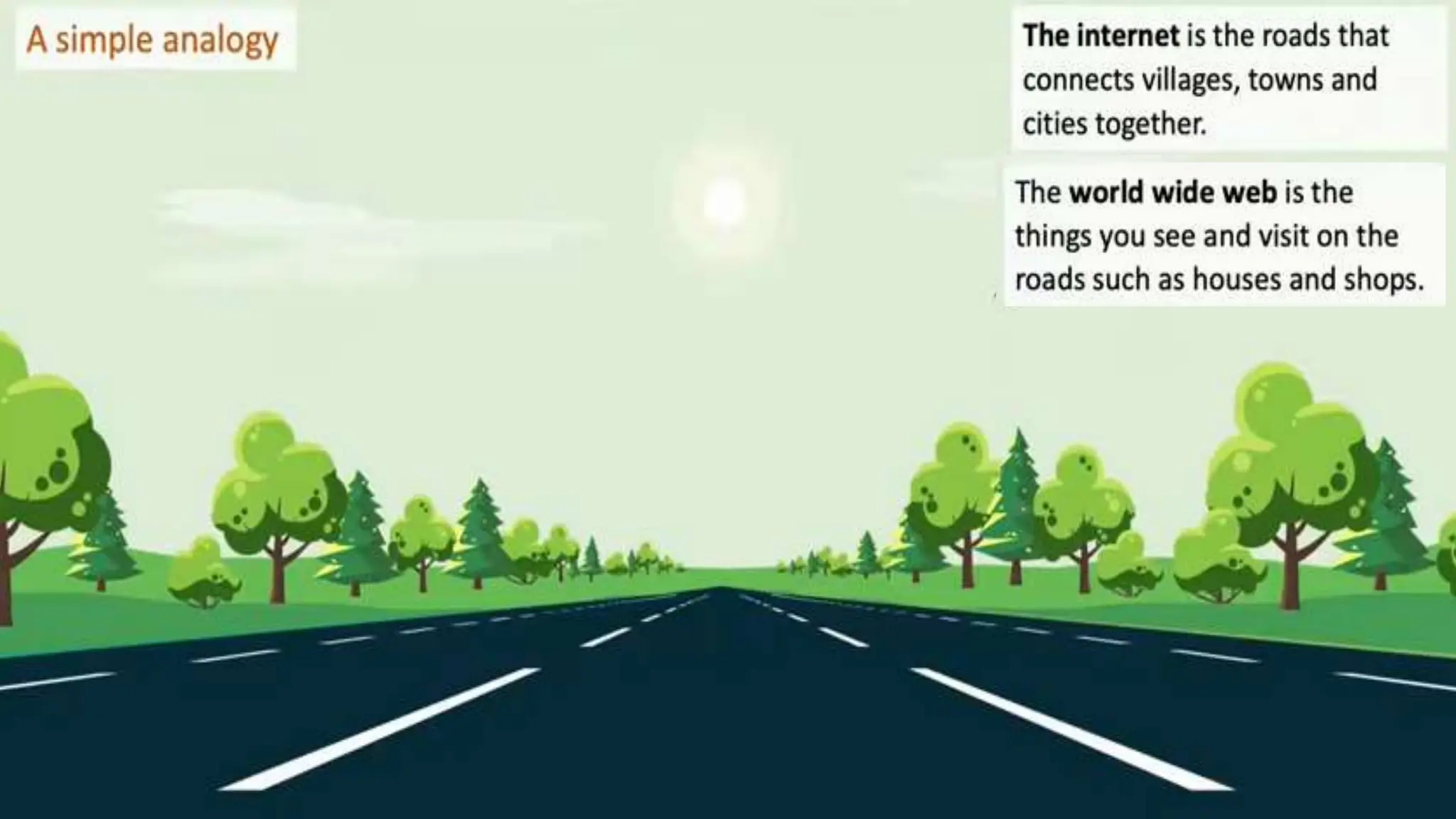
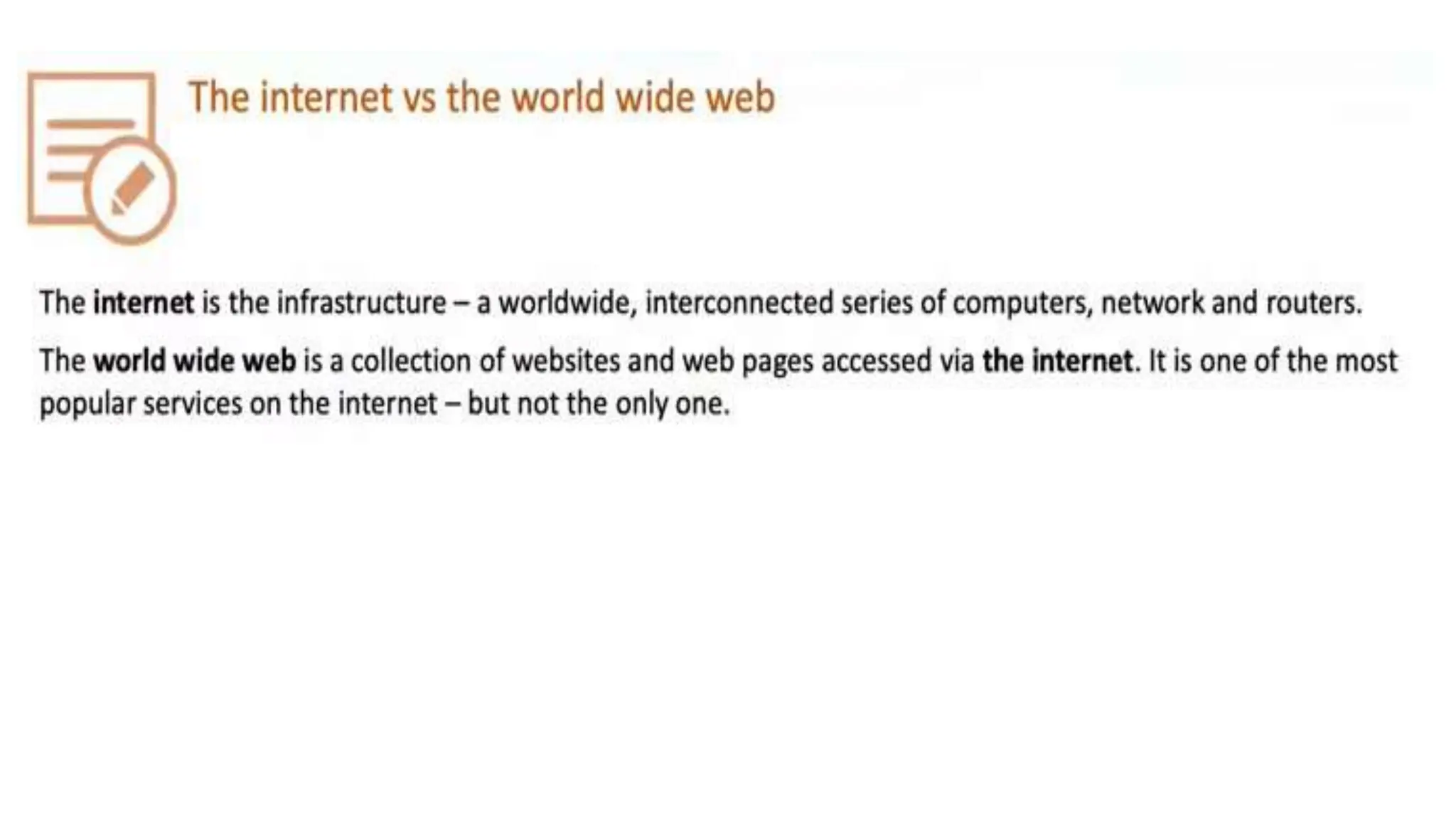
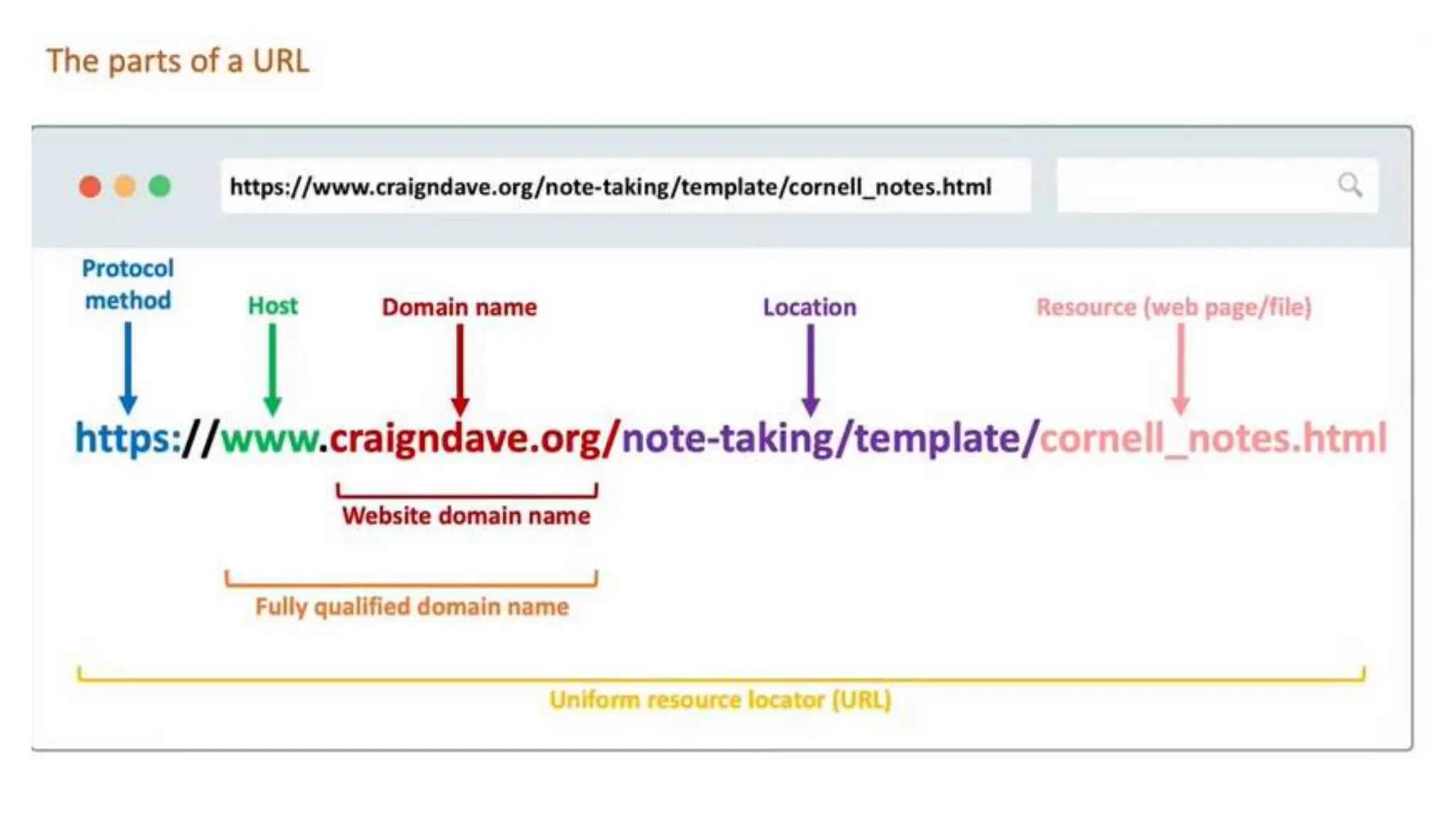
Input and output devices allow computers to receive and display information. Common input devices include keyboards, mice, and touchscreens which translate human actions into digital data. Output devices such as monitors, printers and speakers convey the processed data in a human understandable form. Data storage devices like hard disk drives, solid state drives and optical discs are used to permanently store large amounts of digital data in binary format using magnetic charges or physical marks. Networks allow computers to share and exchange information through connections and communication protocols. Network interface cards are used to connect devices to networks while routers direct data traffic between networks.