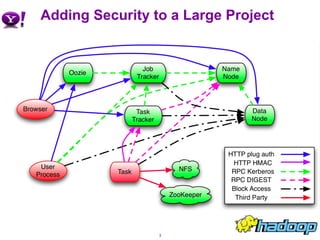
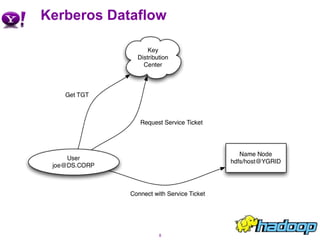
The document outlines the security challenges and improvements in Hadoop, particularly focusing on user authentication and authorization using Kerberos. It highlights the need for secure configurations, changes in permissions, and enhancements to the web UIs to ensure user accountability. Key changes include controller permissions, token management for jobs, and the establishment of proxy users, while mentioning ongoing issues such as the lack of encryption on wire and disk.
![Preview of Hadoop Security Owen O’Malley Yahoo Hadoop Development [email_address]](https://image.slidesharecdn.com/hadoopsecuritypreview-100325134432-phpapp02/75/Hadoop-Security-Preview-1-2048.jpg)