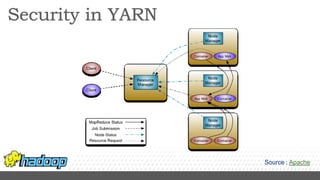
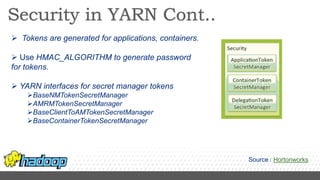
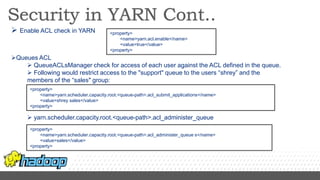
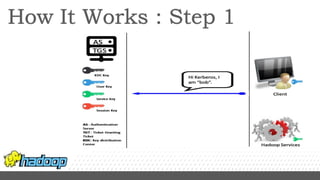
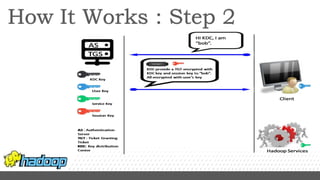
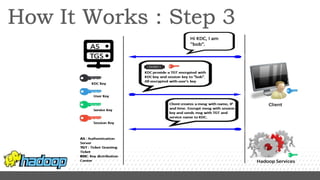
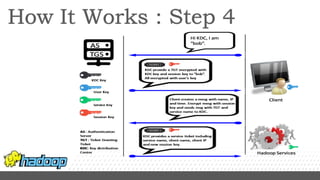
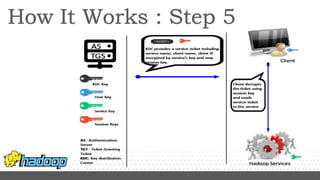
- Kerberos is used to authenticate Hadoop services and clients running on different nodes communicating over a non-secure network. It uses tickets for authentication.
- Key configuration changes are required to enable Kerberos authentication in Hadoop including setting hadoop.security.authentication to kerberos and generating keytabs containing principal keys for HDFS services.
- Services are associated with Kerberos principles using keytabs which are then configured for use by the relevant Hadoop processes and services.











![ Shell Operations
• hadoop fs -chmod [-R] mode file
• hadoop fs -chgrp [-R] group file
• chown [-R] [owner][:[group]] file
The Super-User
The super-user is the user with the same identity as name node process itself.
Permissions checks never fail for the super-user.
There is no persistent notion of who was the super-user
When the name node is started the process identity determines who is the super-user for now.
WebHDFS
Uses Kerberos (SPNEGO) and Hadoop delegation tokens for authentication.](https://image.slidesharecdn.com/hadoopsecurity-150501123011-conversion-gate01/85/Hadoop-security-13-320.jpg)

![ACLs Shell Commands
hdfs dfs -getfacl [-R] <path>
hdfs dfs -setfacl [-R] [-b|-k -m|-x <acl_spec> <path>]|[--set <acl_spec> <path>]
-R : Recursive
-m : Modify ACL.
-b : Remove all but the base ACL entries. The entries for user, group and others are retained for compatibility
with permission bits.
-k : Remove the default ACL.
-x : Remove specified ACL entries.
<acl_spec> : Comma separated list of ACL entries.
--set : Fully replace the ACL, discarding all existing entries.
hdfs dfs -ls <args>
ls will append a '+' character to the permissions string of any file or directory that has an ACL.](https://image.slidesharecdn.com/hadoopsecurity-150501123011-conversion-gate01/85/Hadoop-security-15-320.jpg)