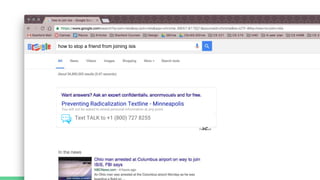
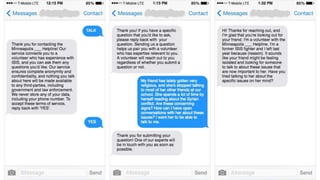
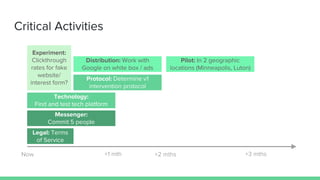
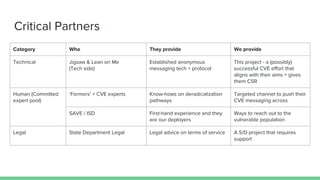
The document summarizes the work of HackingCT - Week 8. It discusses using technology, government, and at-risk communities to combat extremist messaging in a bottom-up manner. It details 12 interviews conducted so far with 90 total. The goal is to bring credible former extremists and family/friends of radicalized individuals together to provide help and information to those at risk of radicalization through an anonymous textline. The proposed MVP and mission model canvas are described.