Hacking Team Presented By: Tushar Moolya Rocky Kalal Yash Dixit
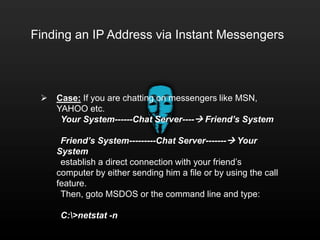
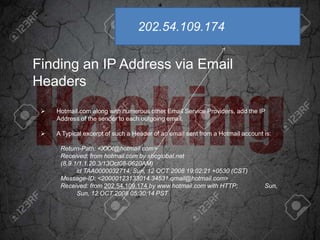
Hacking refers to intruding on someone's personal information without permission for malicious purposes. The history of hacking includes arrests in the 1980s and 1990s, with famous hackers like Ian Murphy, Kevin Mitnick, and Johan Helsinguis. Basic hacking skills include learning to program, using open-source operating systems, and using the web and HTML. Hackers must hide their real identity and IP address to avoid being caught. An IP address can be found through instant messaging, internet relay chat, email headers, or visiting someone's website.