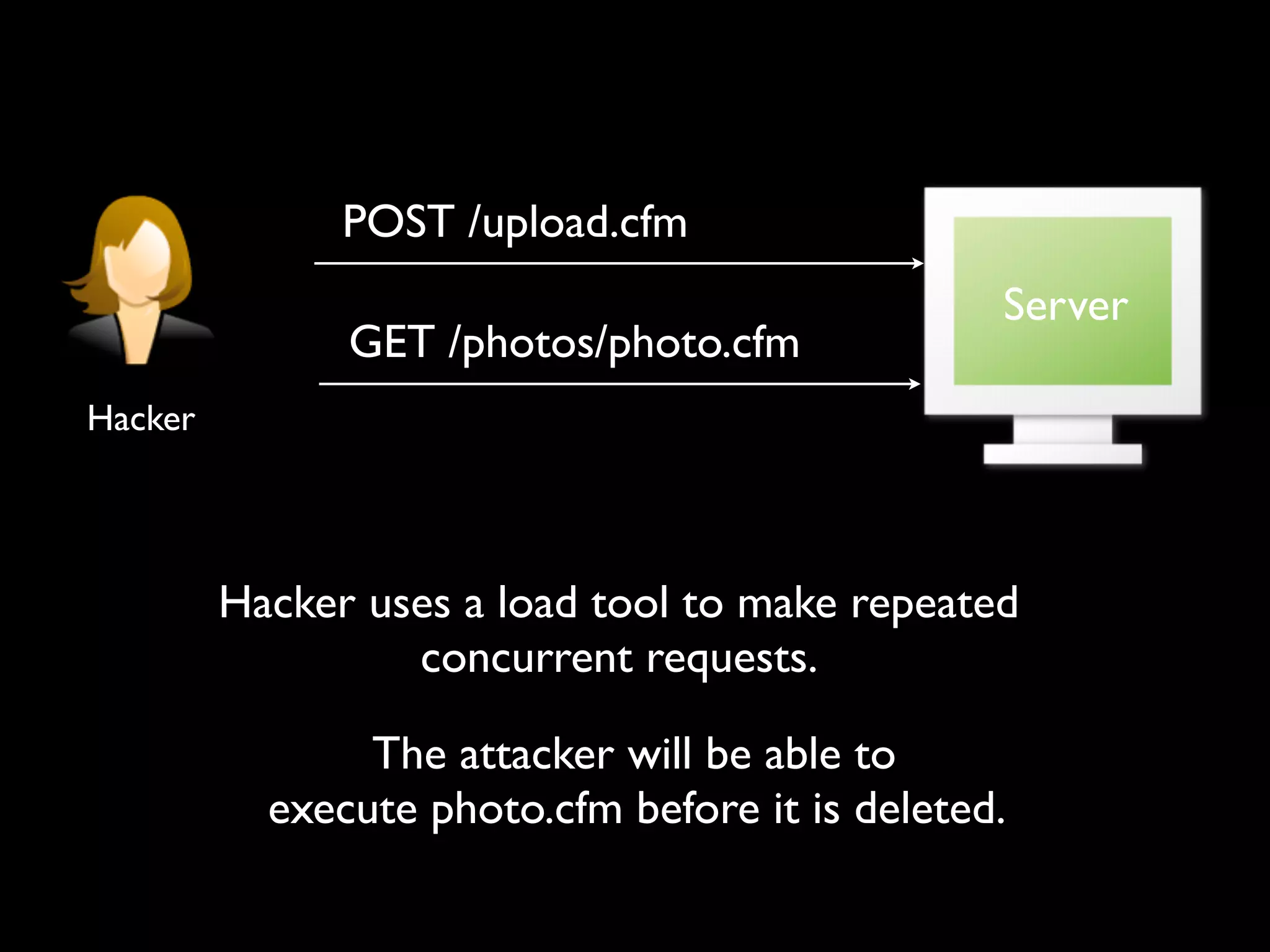
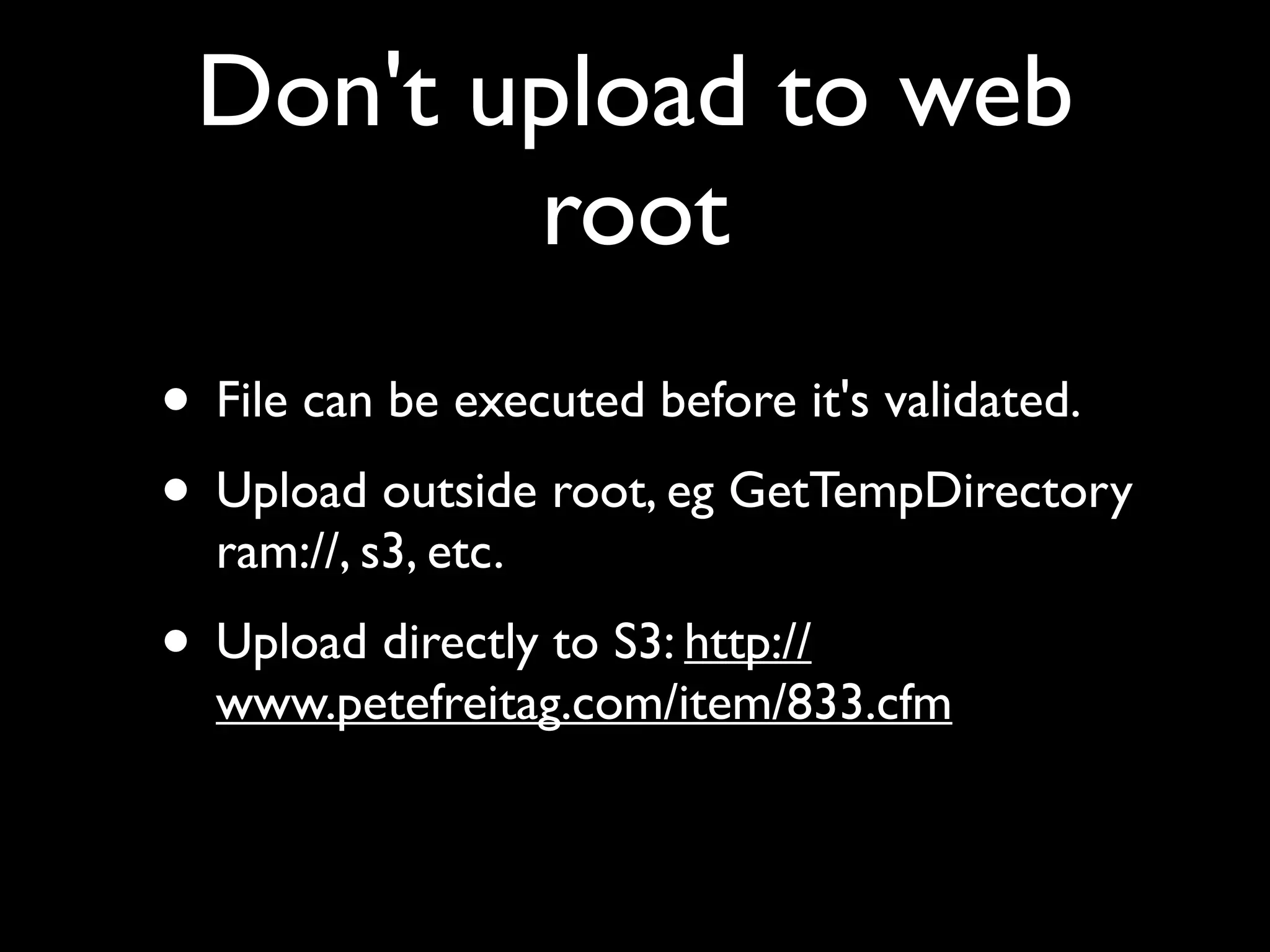
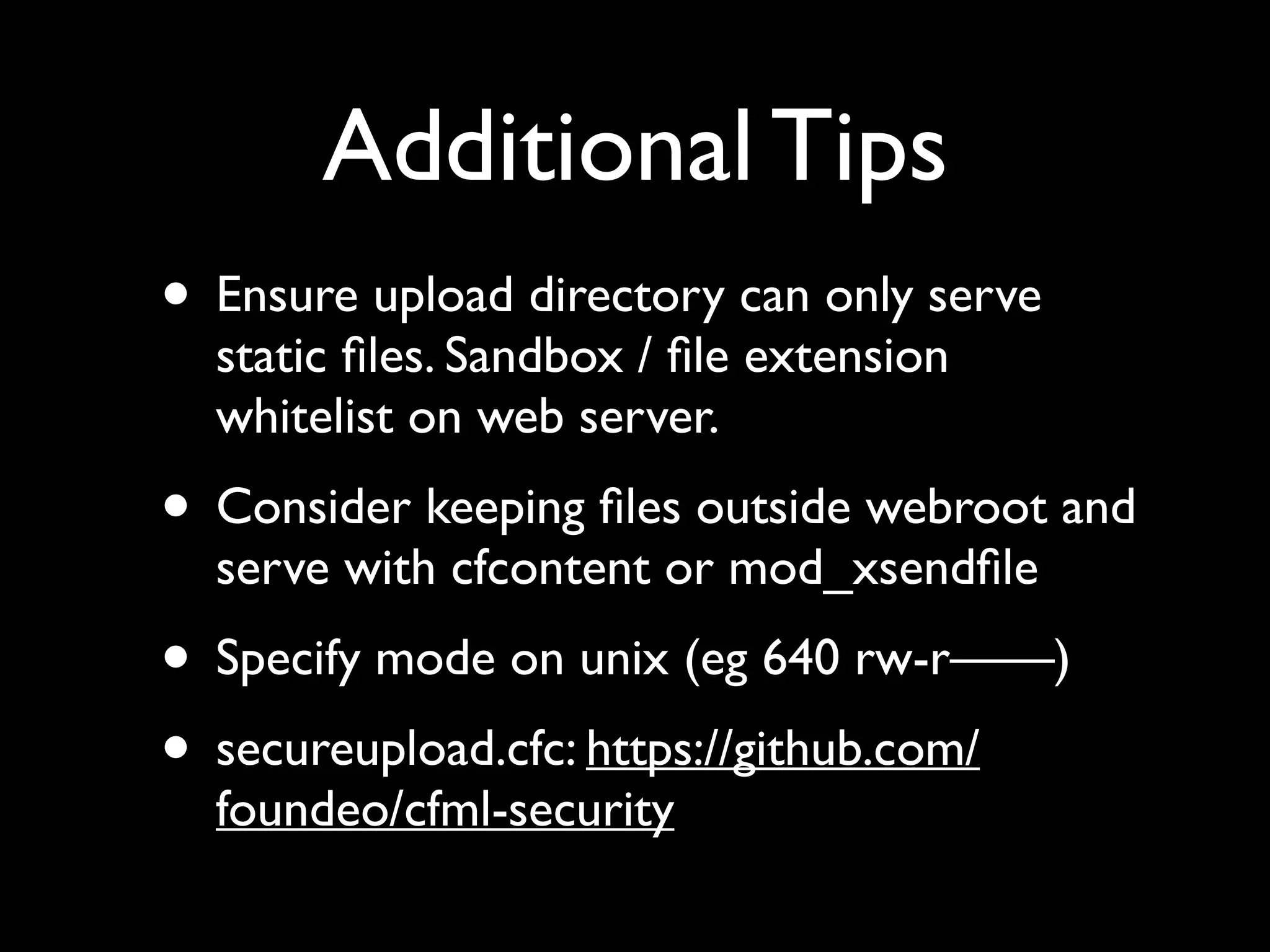
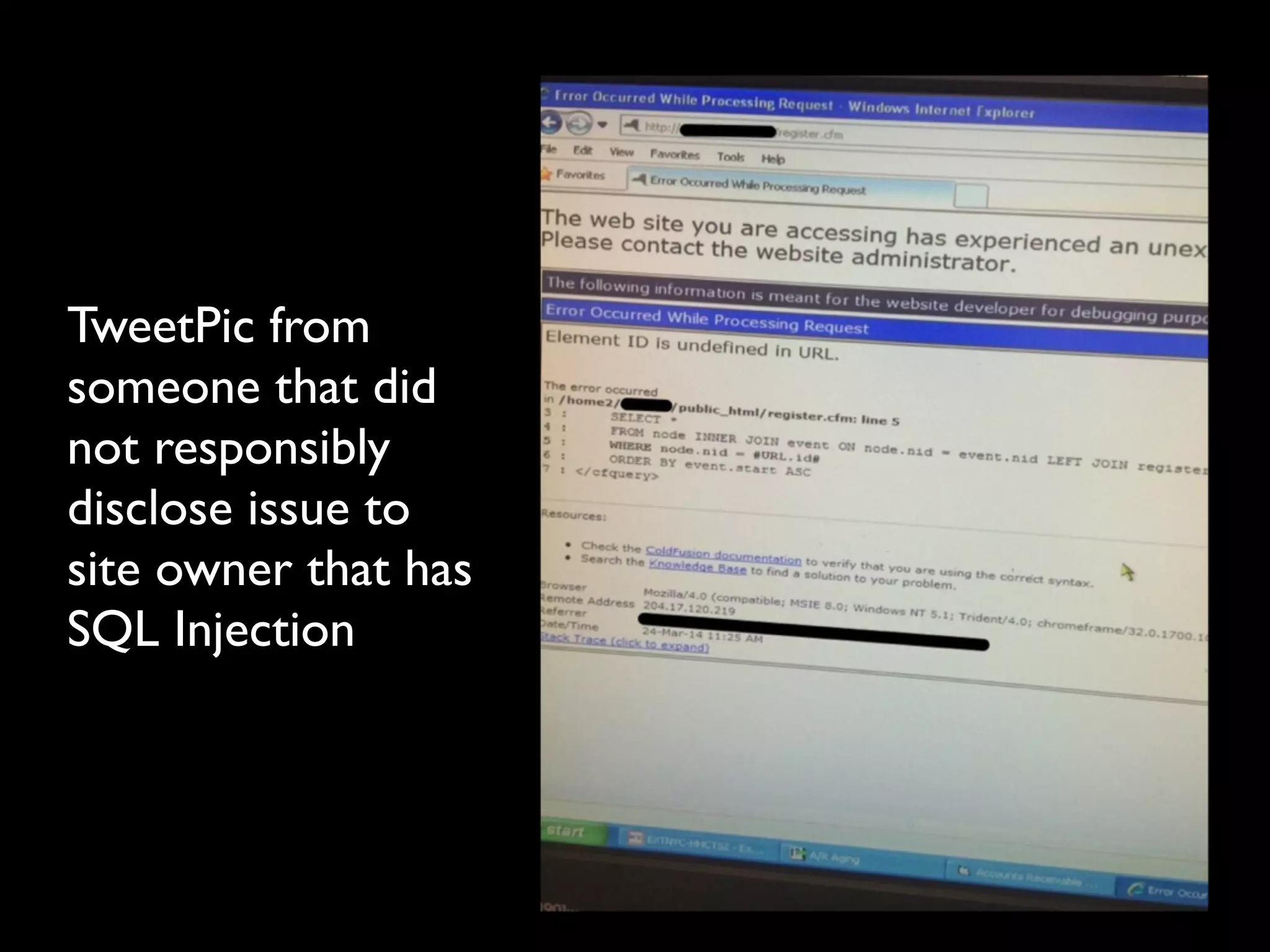
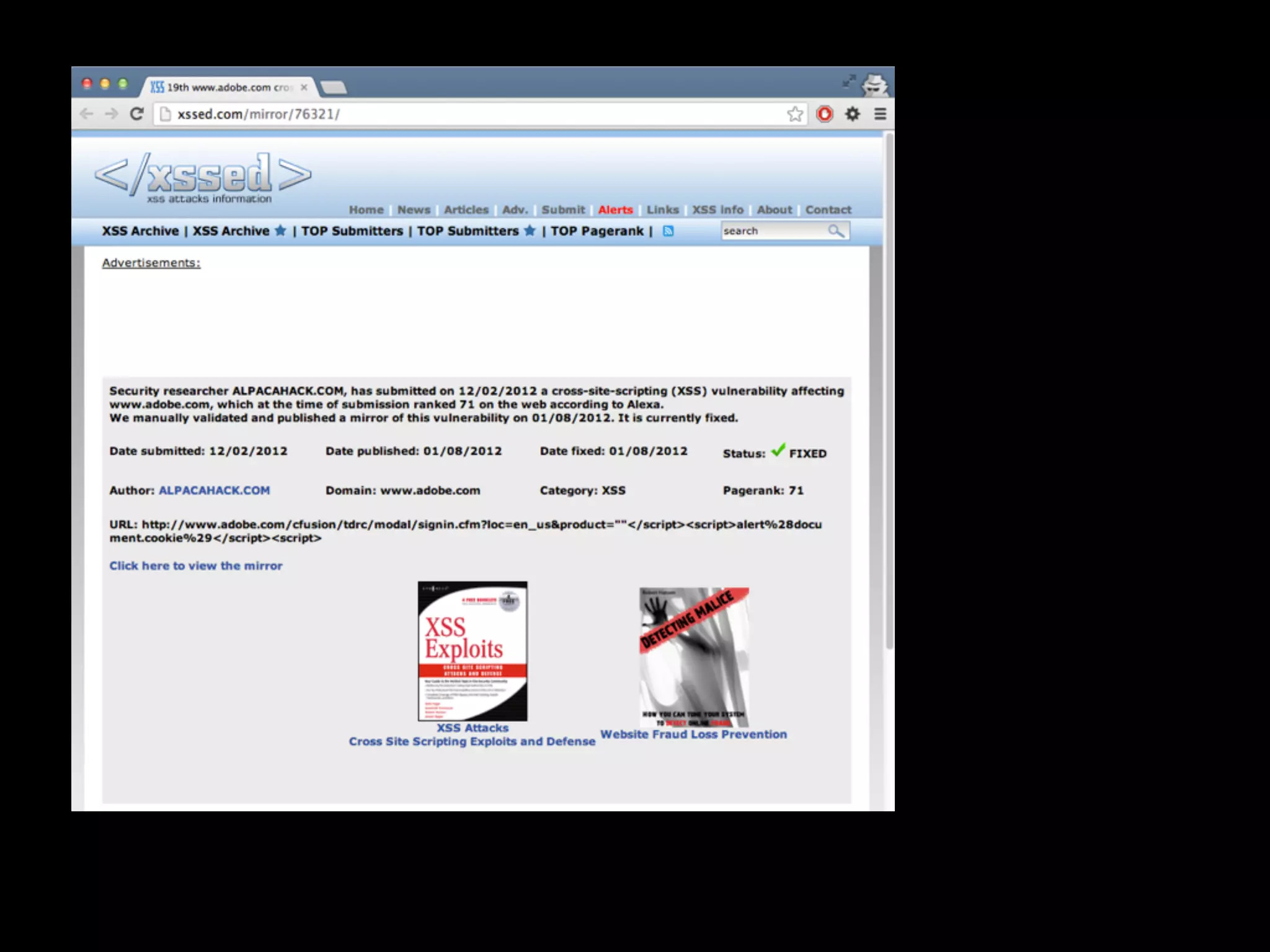
This document provides an agenda for a ColdFusion security training session presented by Pete Freitag and David Epler. It includes introductions to the presenters and their backgrounds in ColdFusion and security. The agenda covers common ColdFusion vulnerabilities like file uploads, SQL injection, path traversals, and cross-site scripting. It also demonstrates the OWASP ZAP security tool and provides a sneak peek at a new ColdFusion security analyzer called Raijin/Blizzard. Hands-on lessons are included to allow participants to try exploiting vulnerabilities.