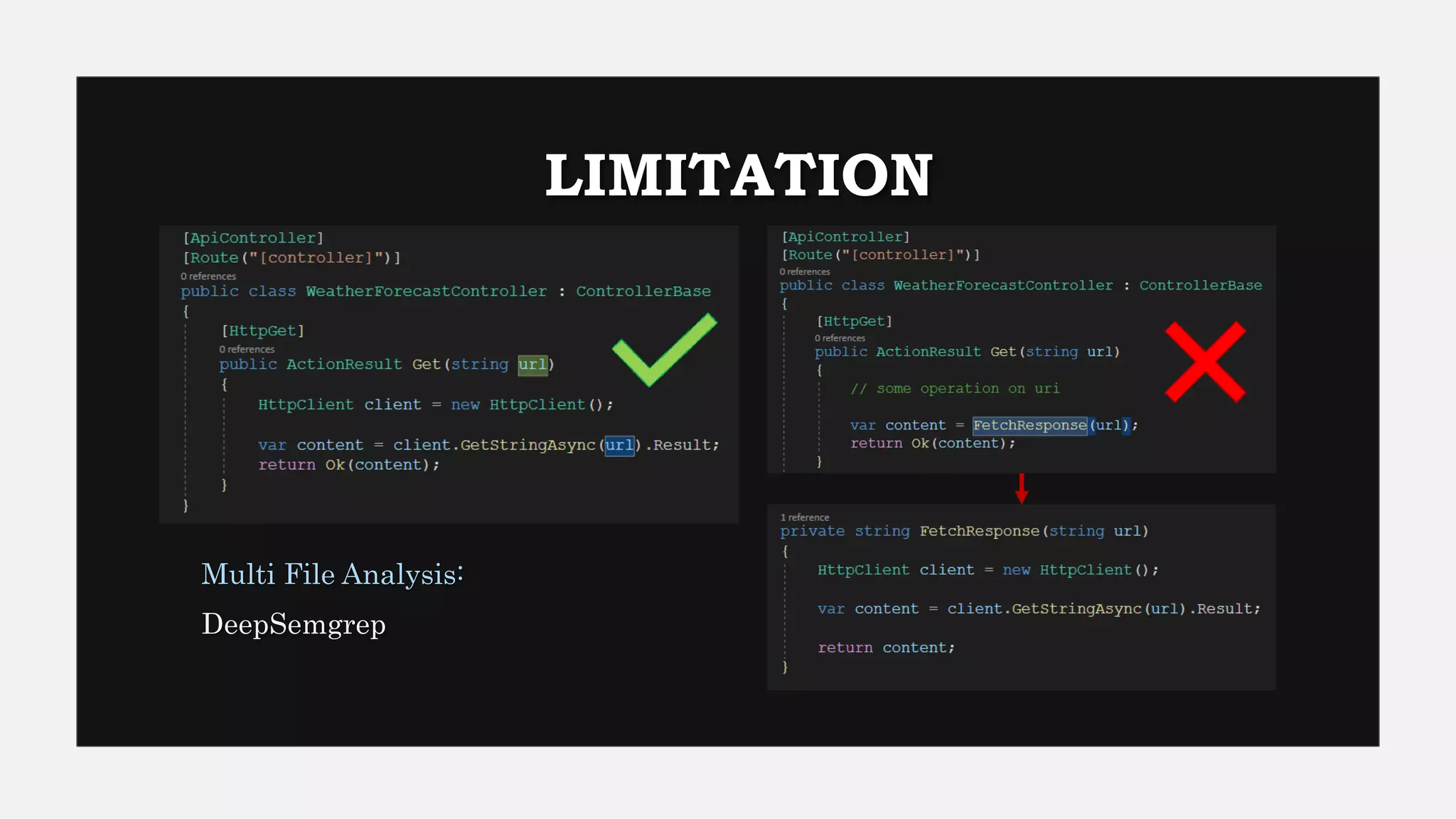
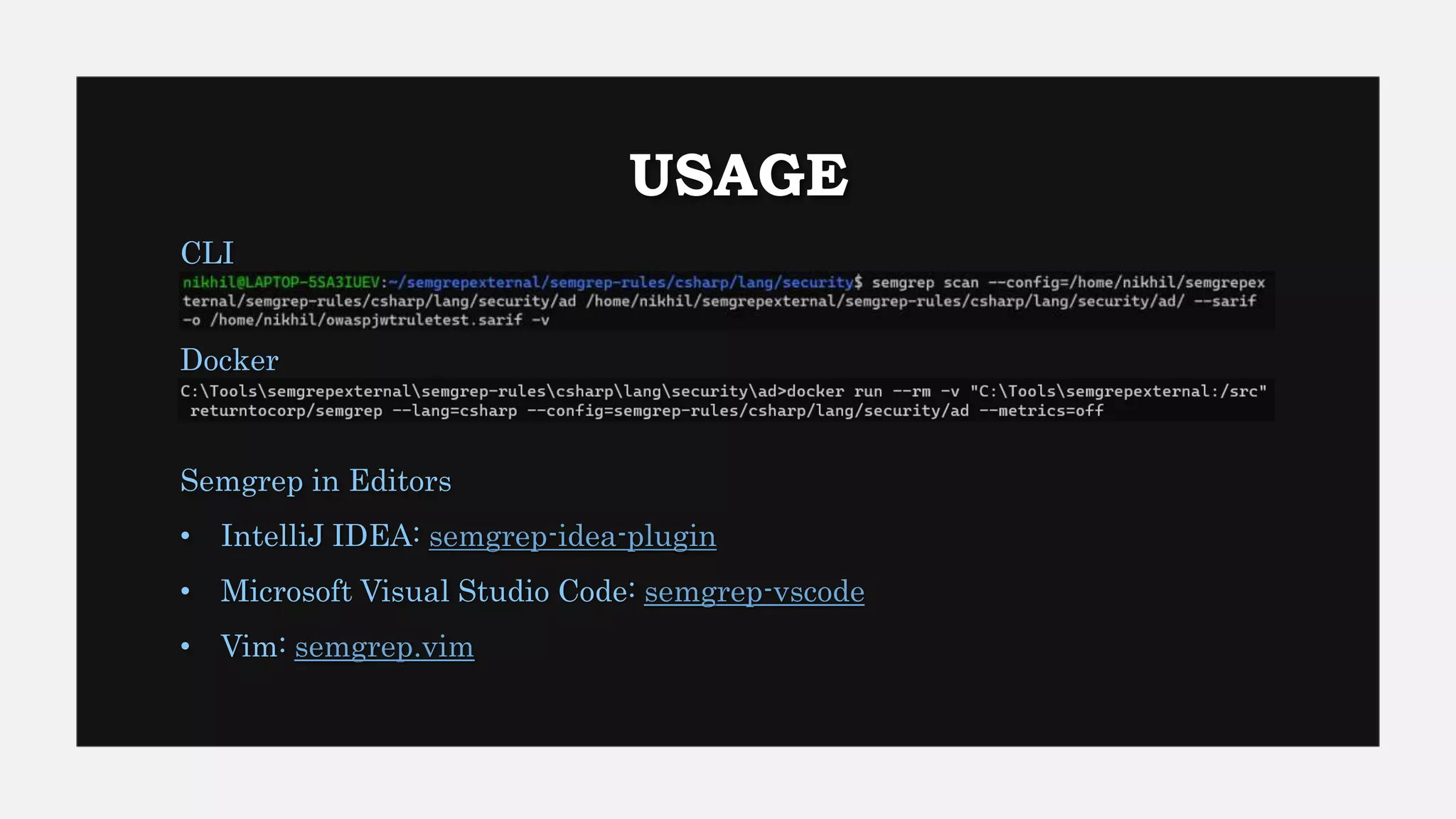
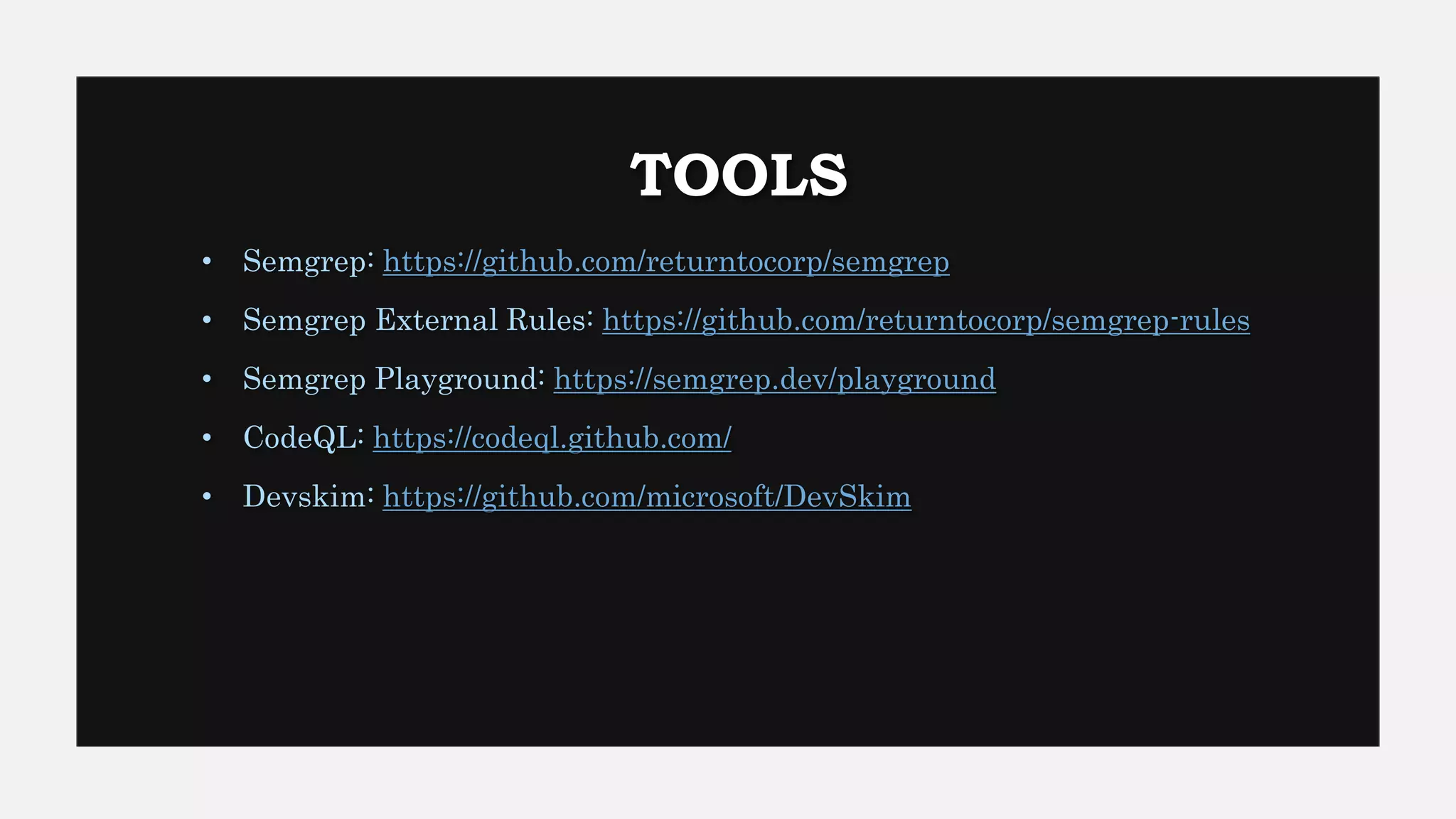
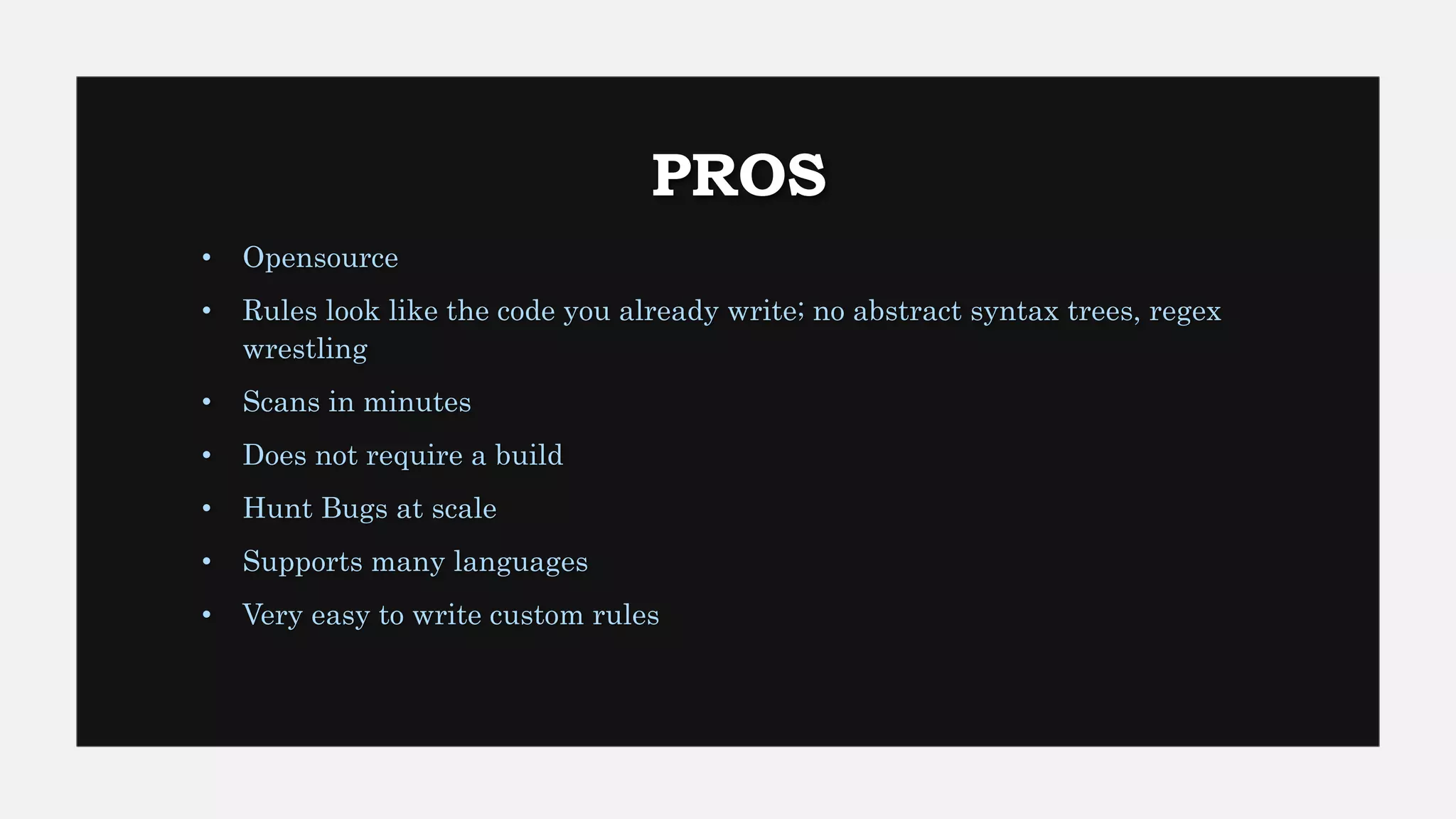
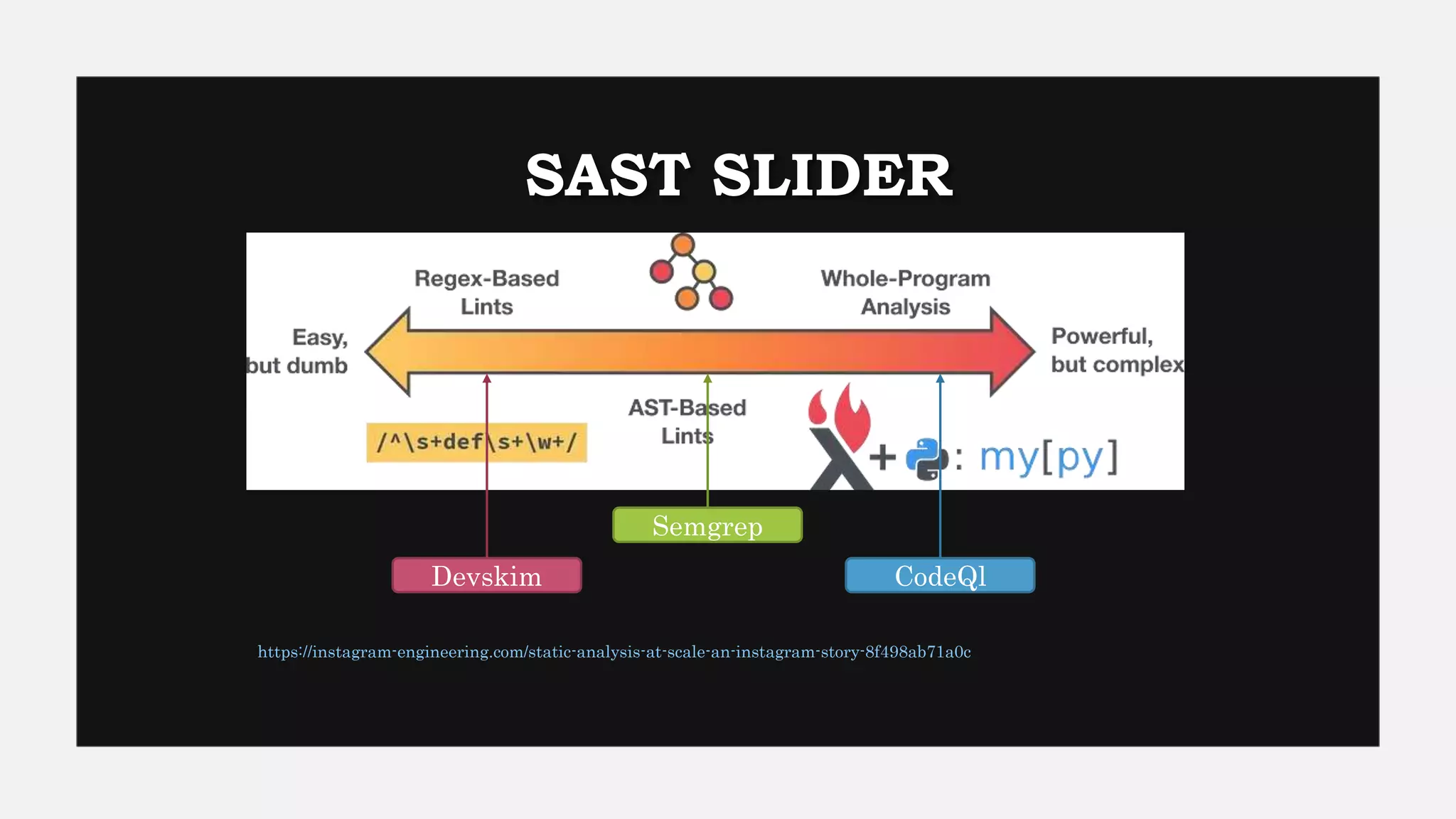
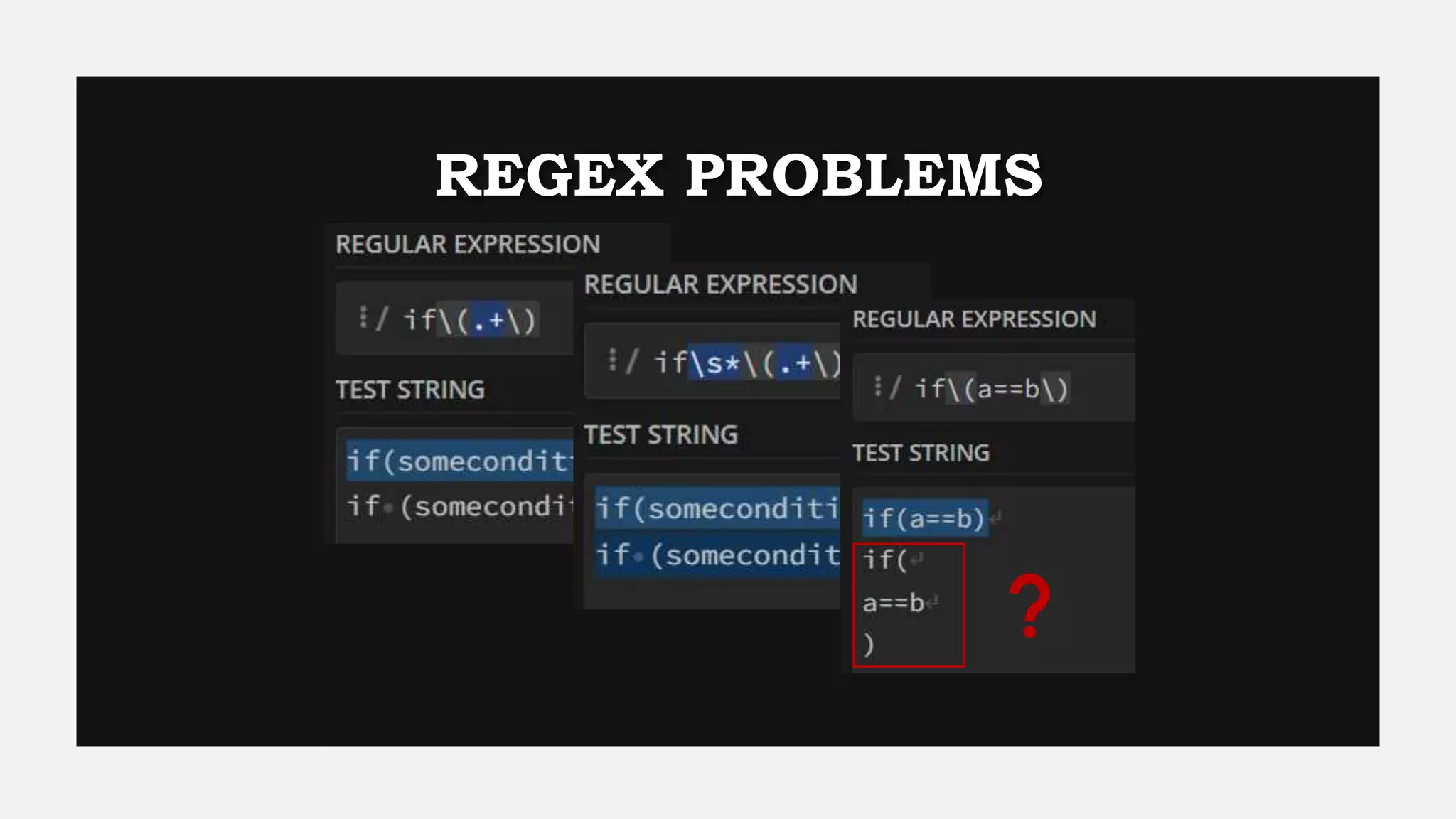
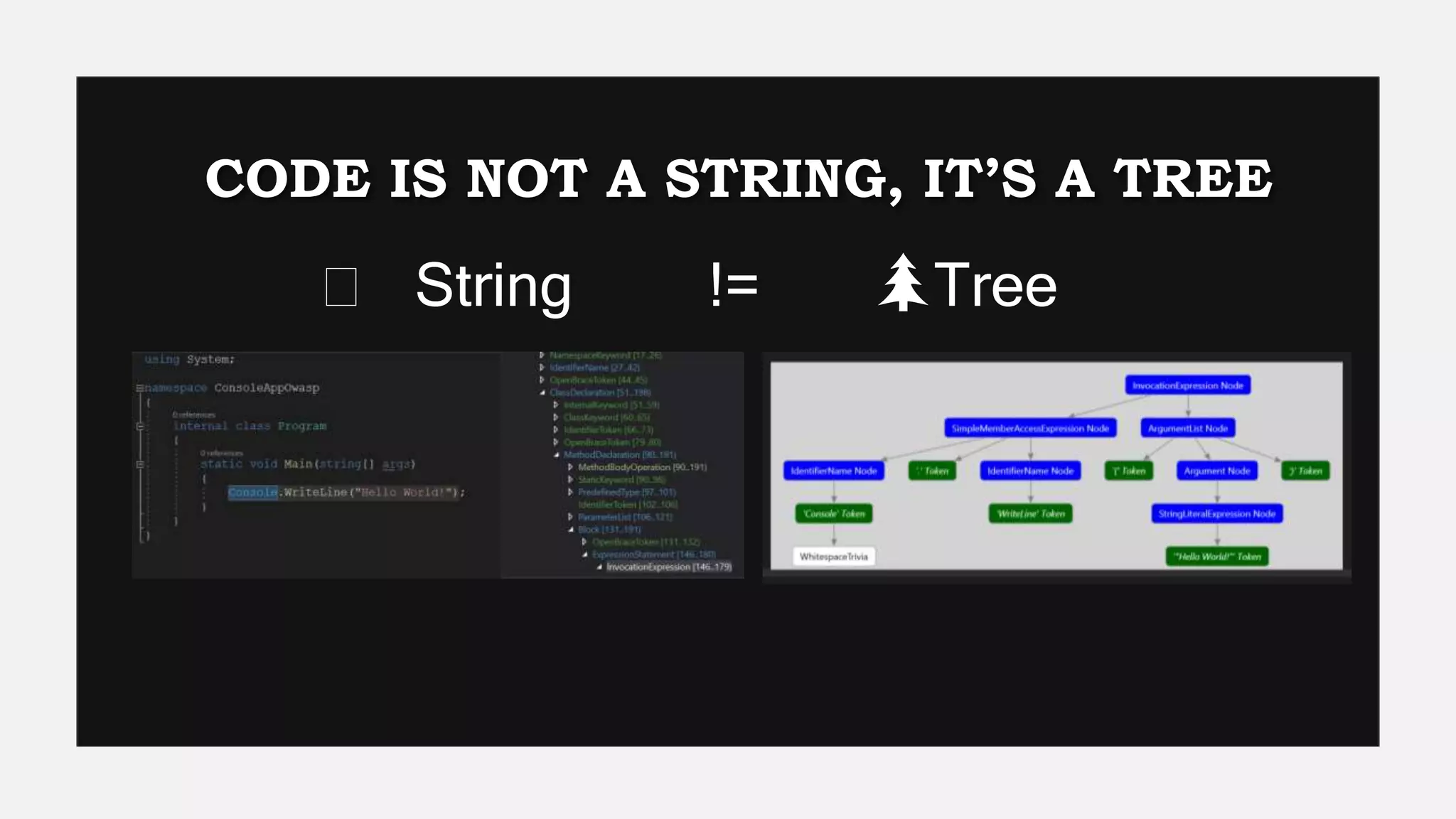
This document provides an overview of Semgrep, a lightweight static code analysis tool. It discusses Semgrep's history and key features like fast scanning, easy to write rules syntax resembling code, and support for many languages. The document demonstrates writing Semgrep rules through examples and references external rule sets. It also covers limitations like lack of multi-file analysis and how Semgrep can be used via editors, CLI and CI/CD integration.





![DEEP EXPRESSION
• Deep Expression Operator: “<… [your pattern]…>”
• Scenario: XML Parser allows resolving external resources
• Solution:
https://semgrep.dev/orgs/nikhil1232/editor/s/nikhil1232:owasp-
xmltextreader
• Reference: https://rules.sonarsource.com/csharp/RSPEC-2755,
https://pvs-studio.com/en/blog/posts/csharp/0918/](https://image.slidesharecdn.com/null25feblightweightstaticcodeanalysiswithsemgrep-230301082827-9017ad59/75/Lightweight-static-code-analysis-with-semgrep-17-2048.jpg)