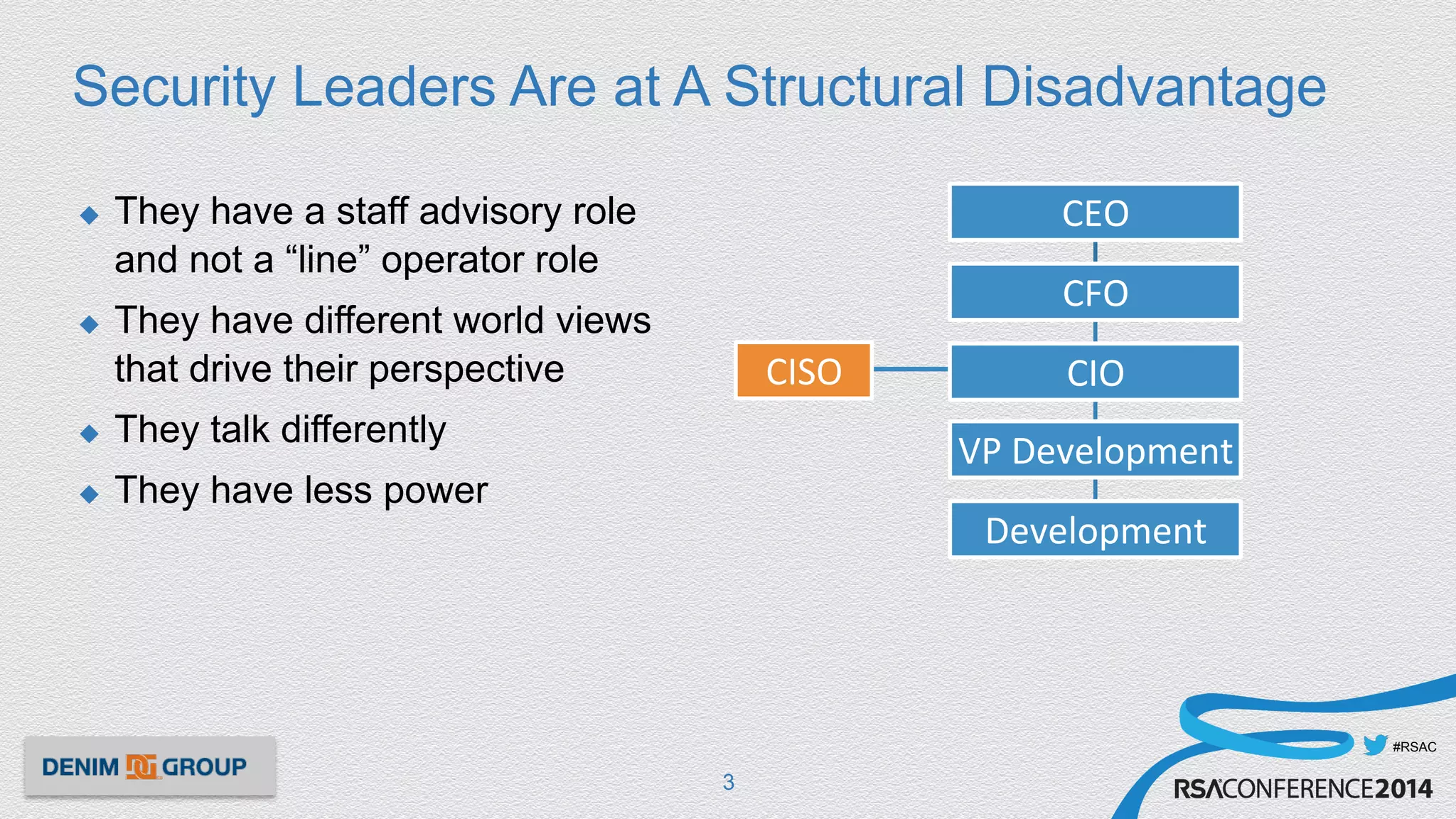
The document discusses strategies for security leaders to secure budget approval without relying on fear, uncertainty, and doubt (FUD). Key principles include exploiting key projects, adapting requests to organizational culture, tailoring communications to specific sectors, building credibility and relationships, leveraging timely events, and documenting successes. The conclusion emphasizes that successful security budget requests are grounded in proactive and strategic engagement rather than fear tactics.