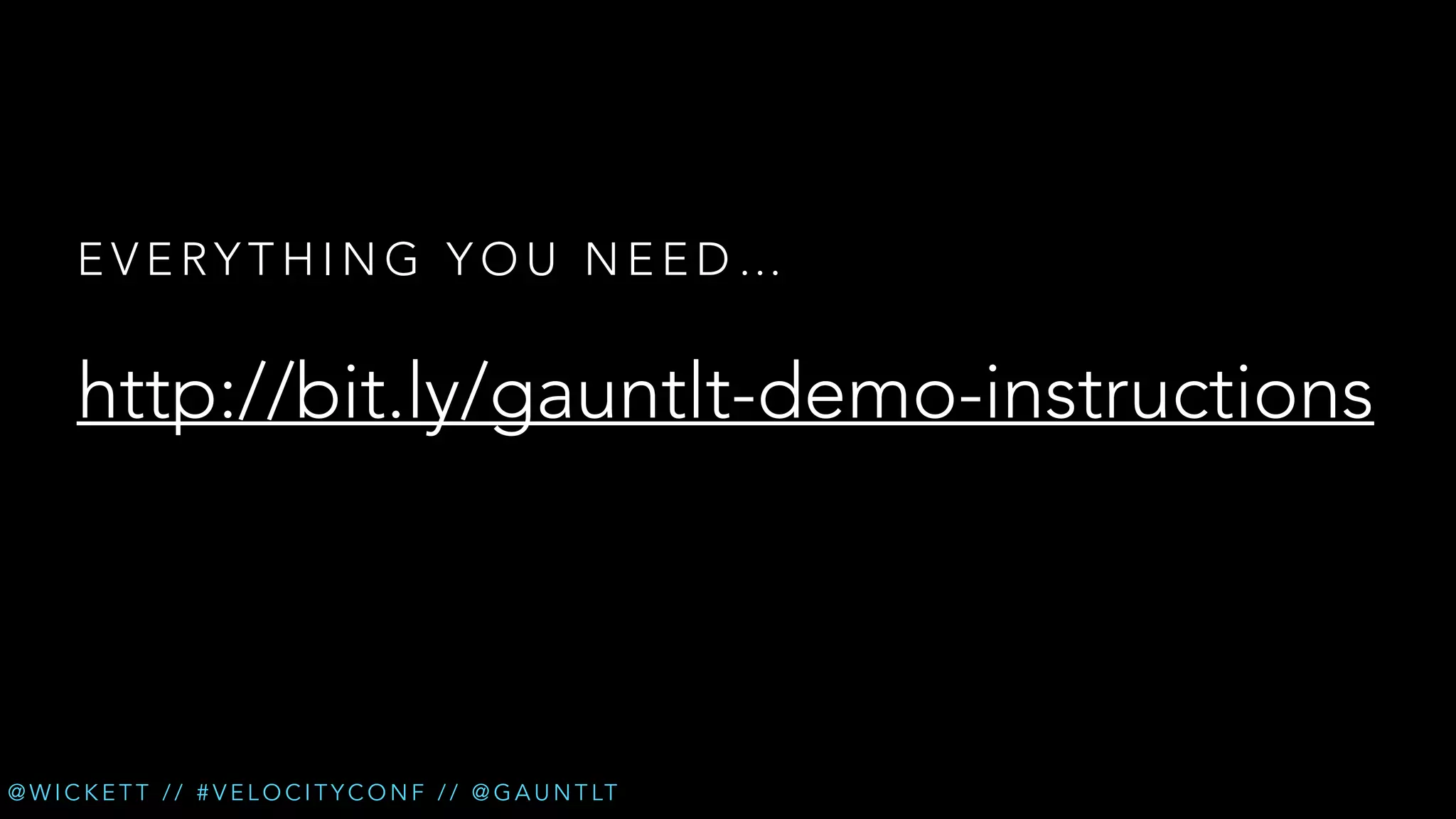
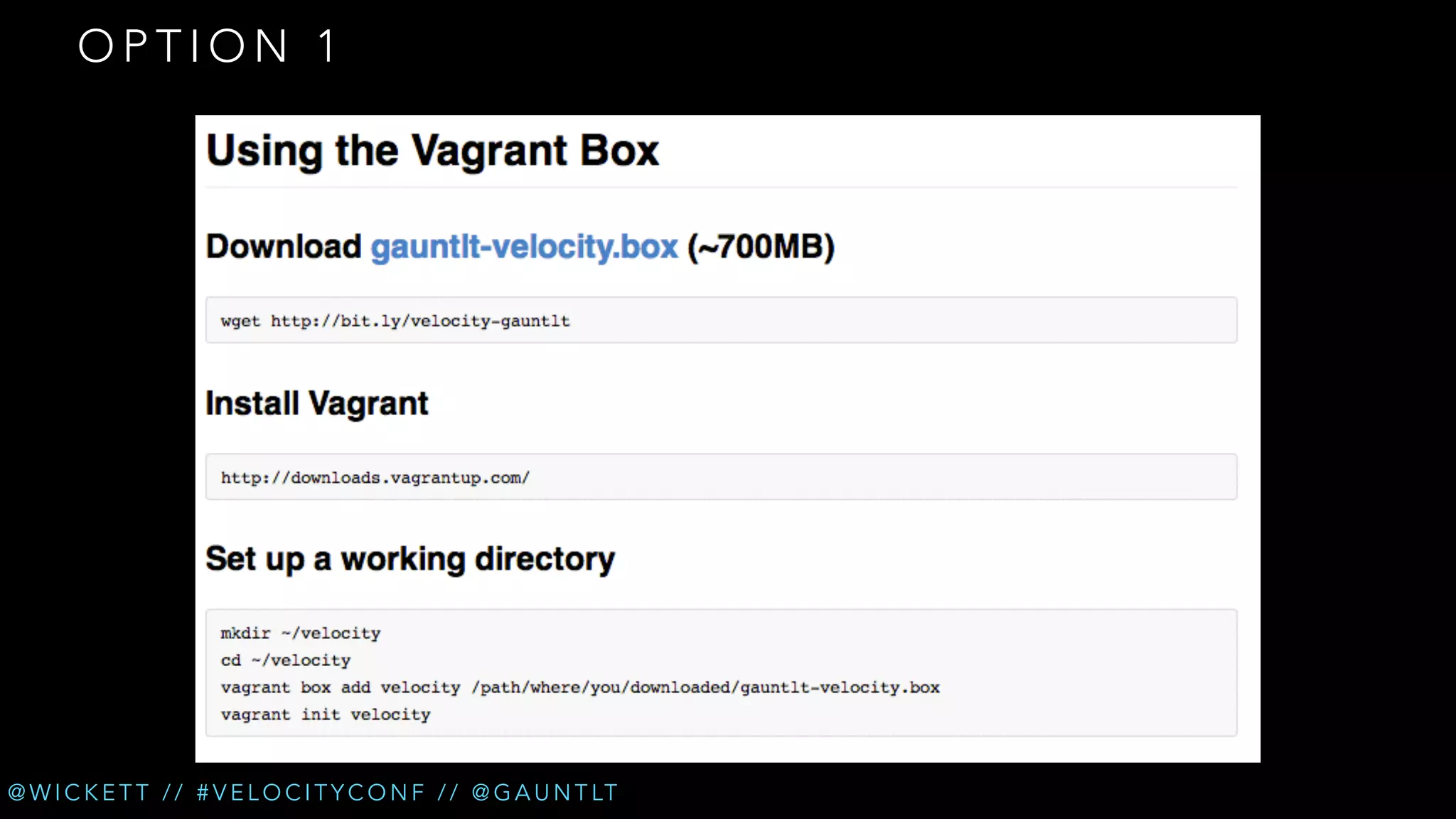
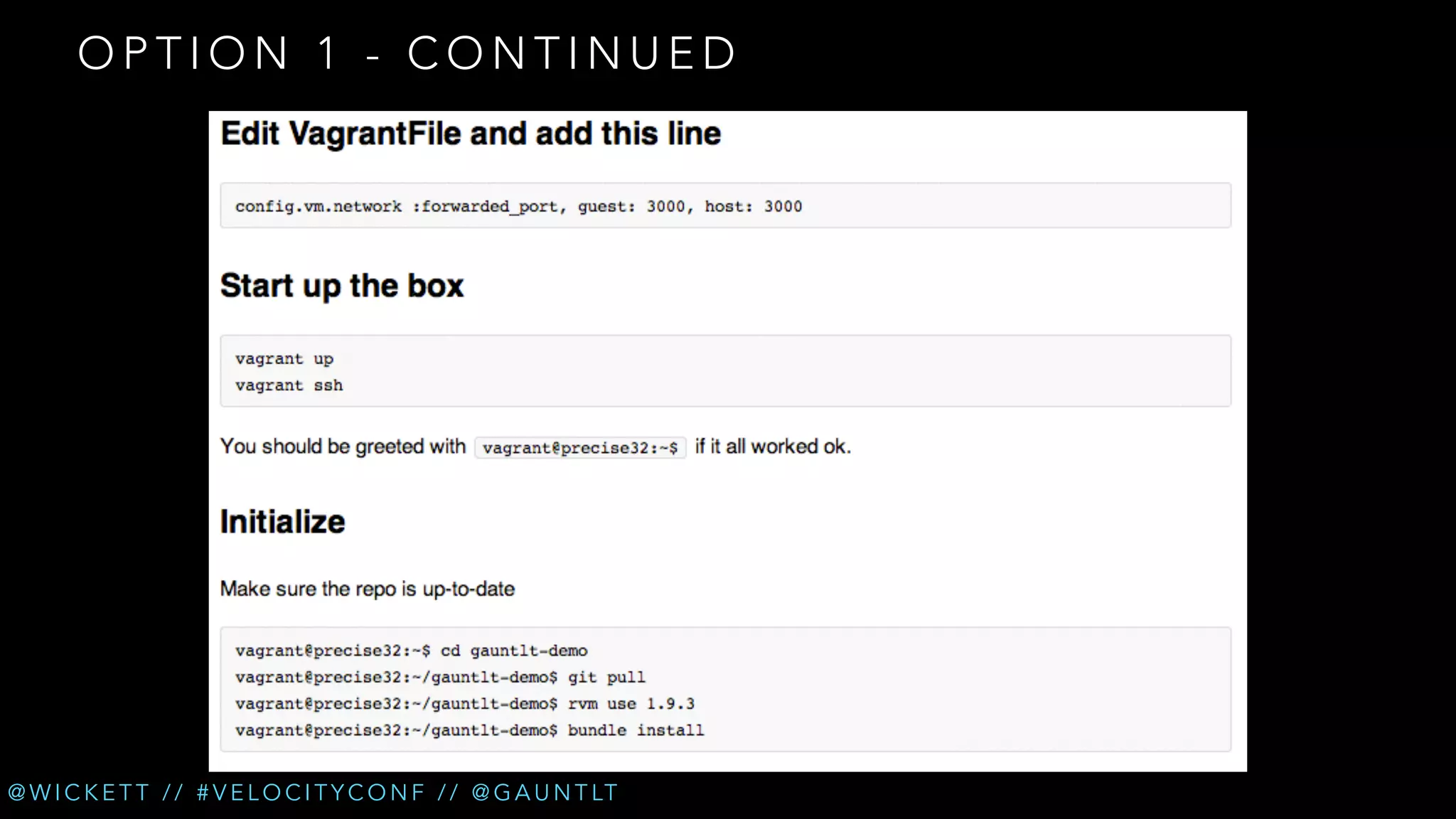
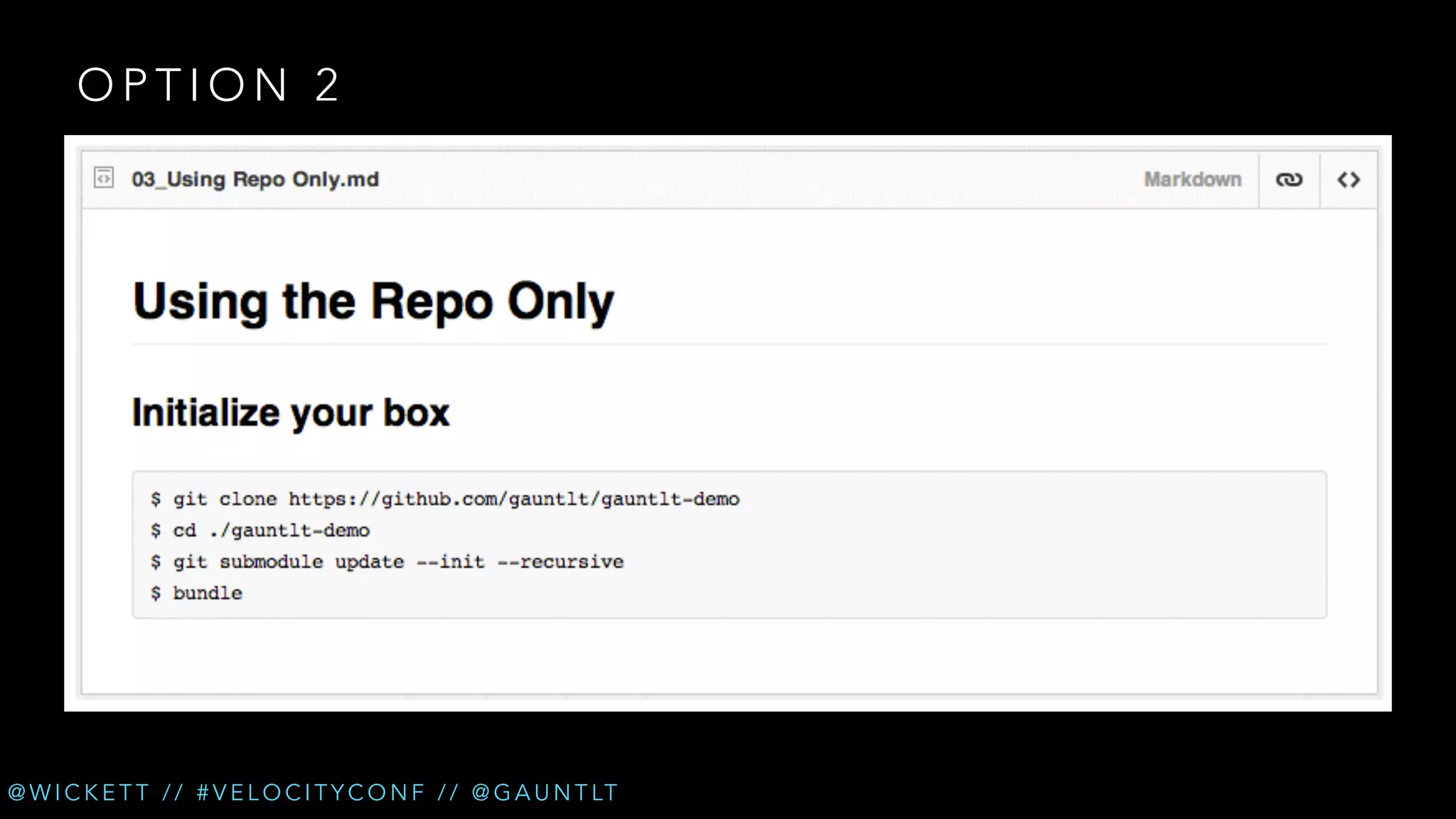
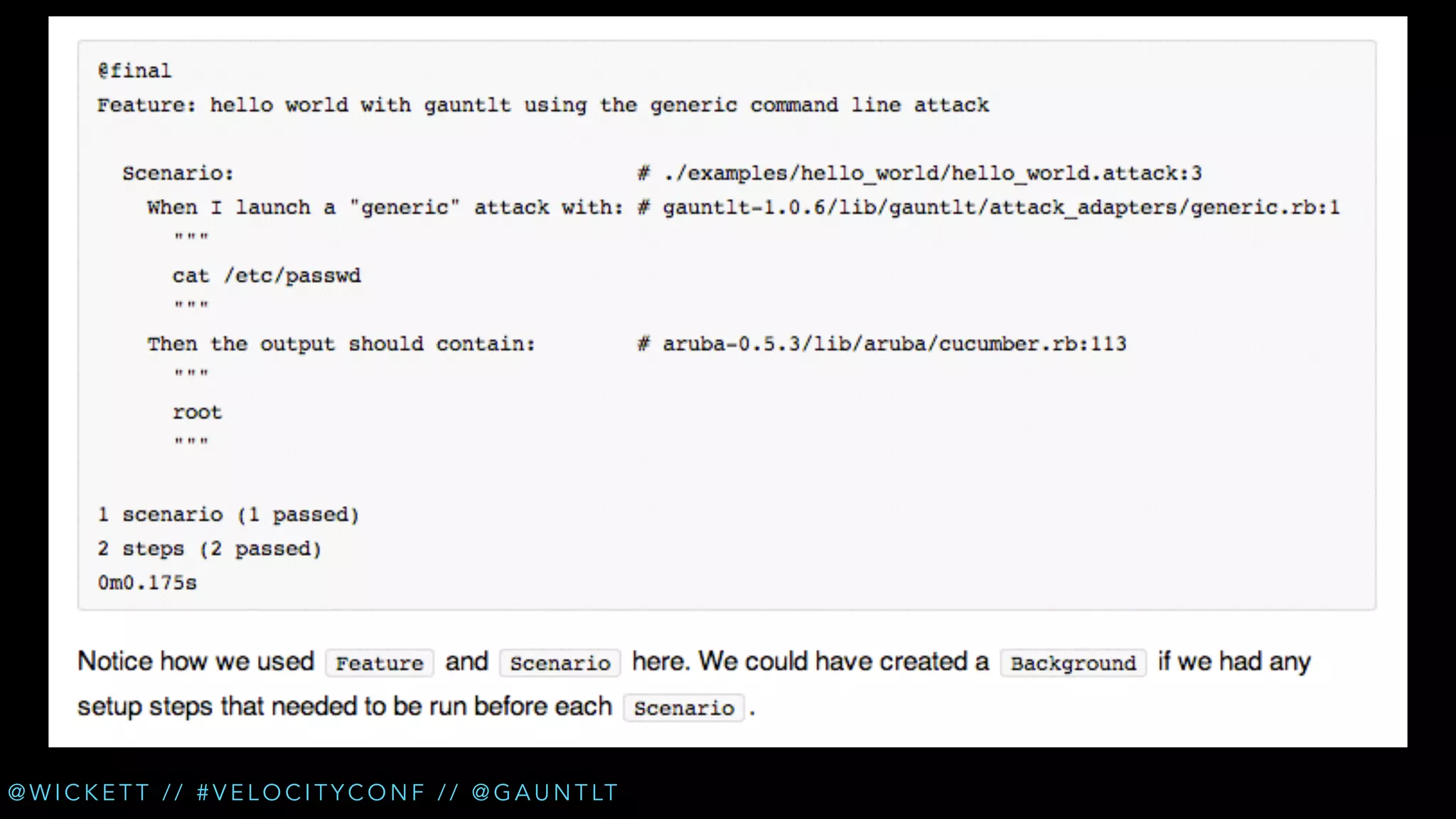
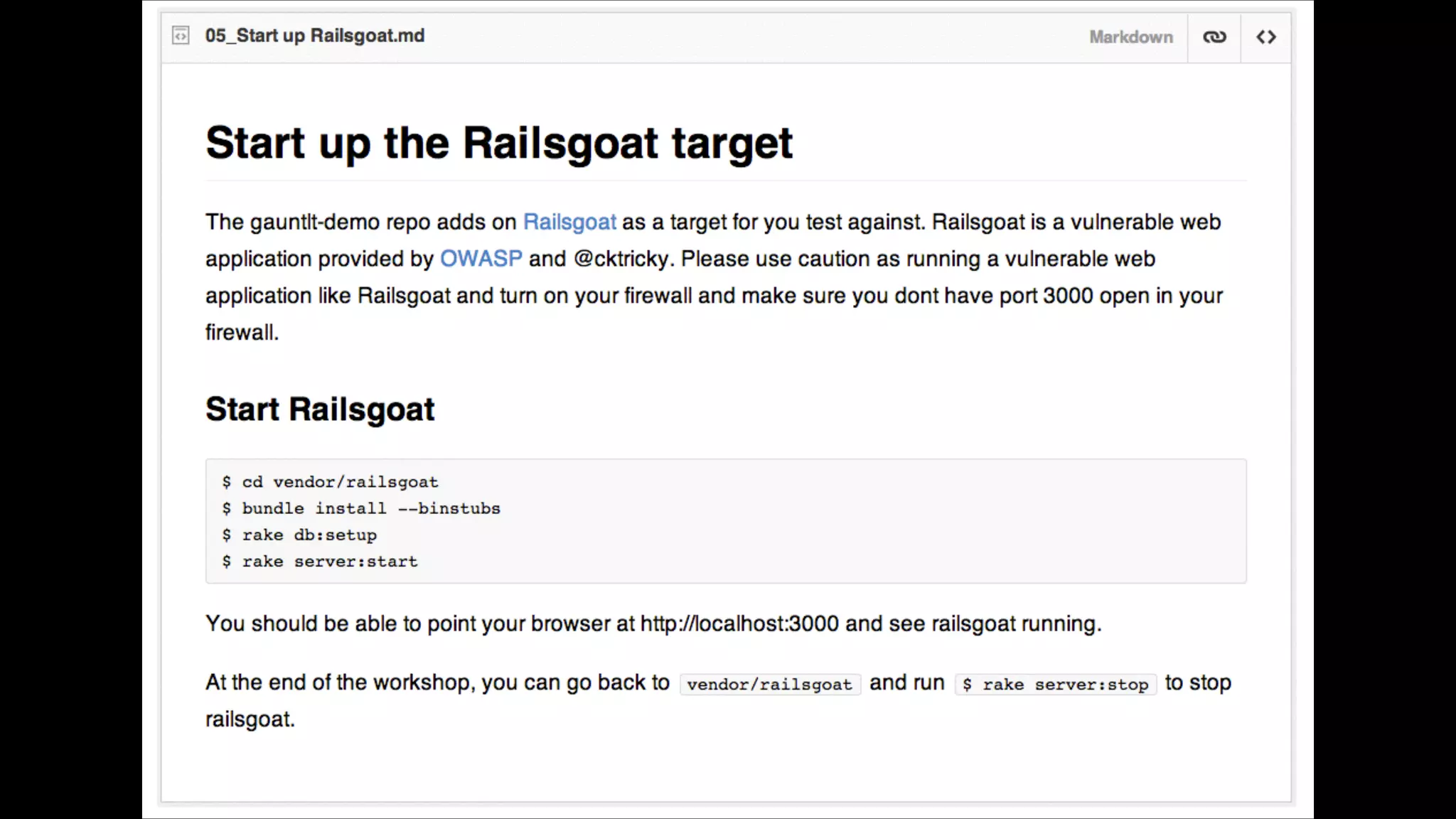
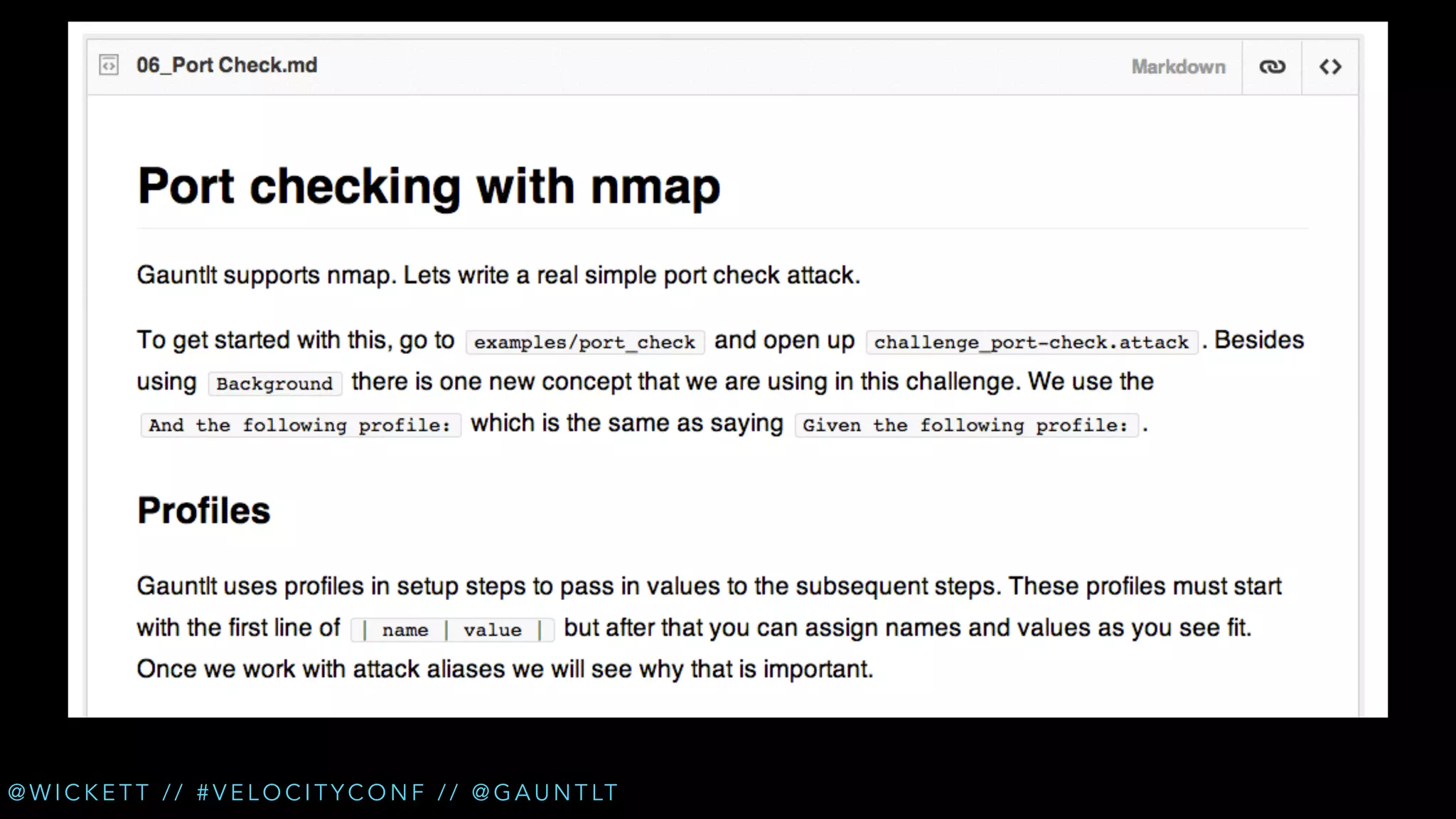
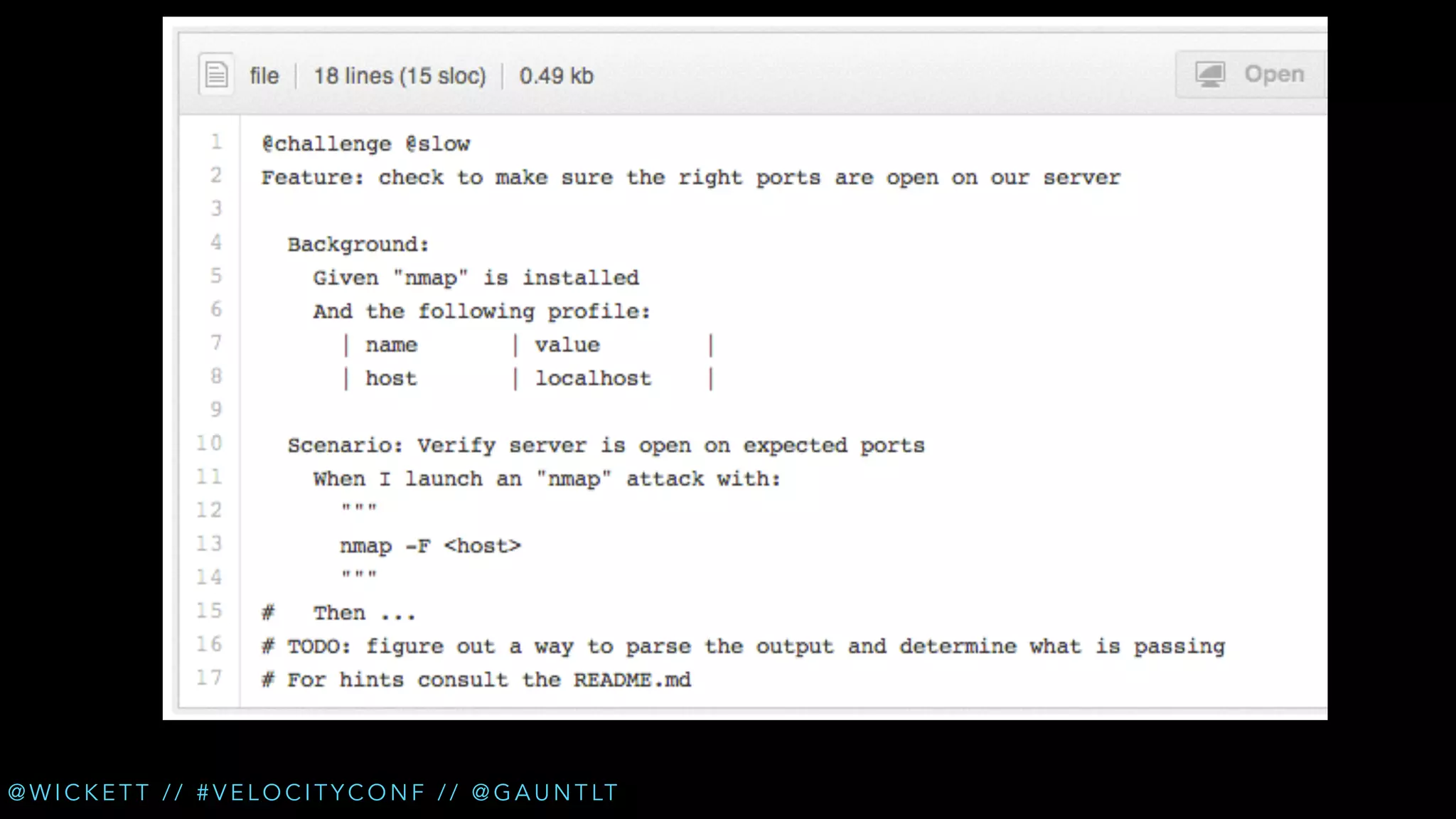
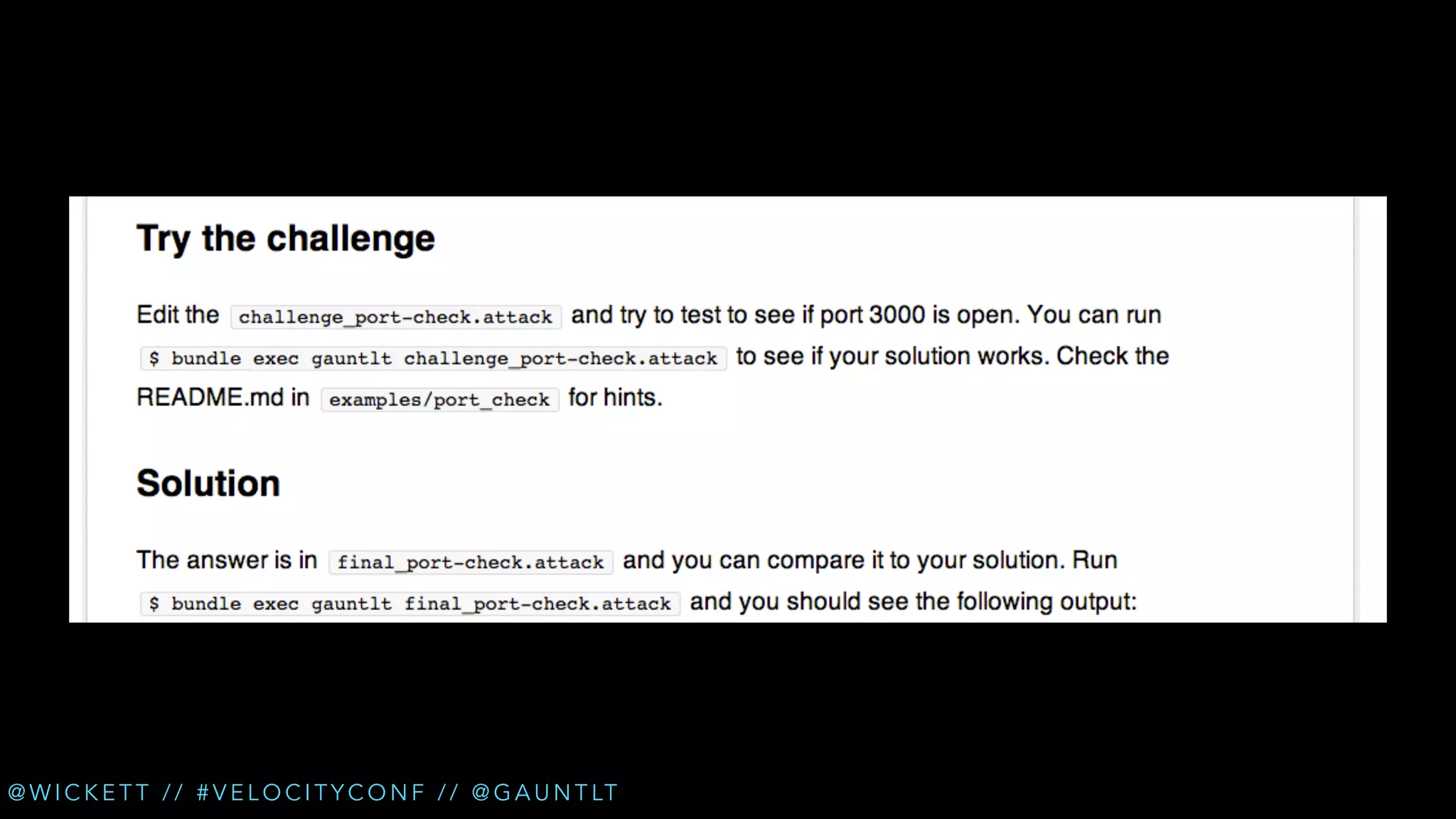
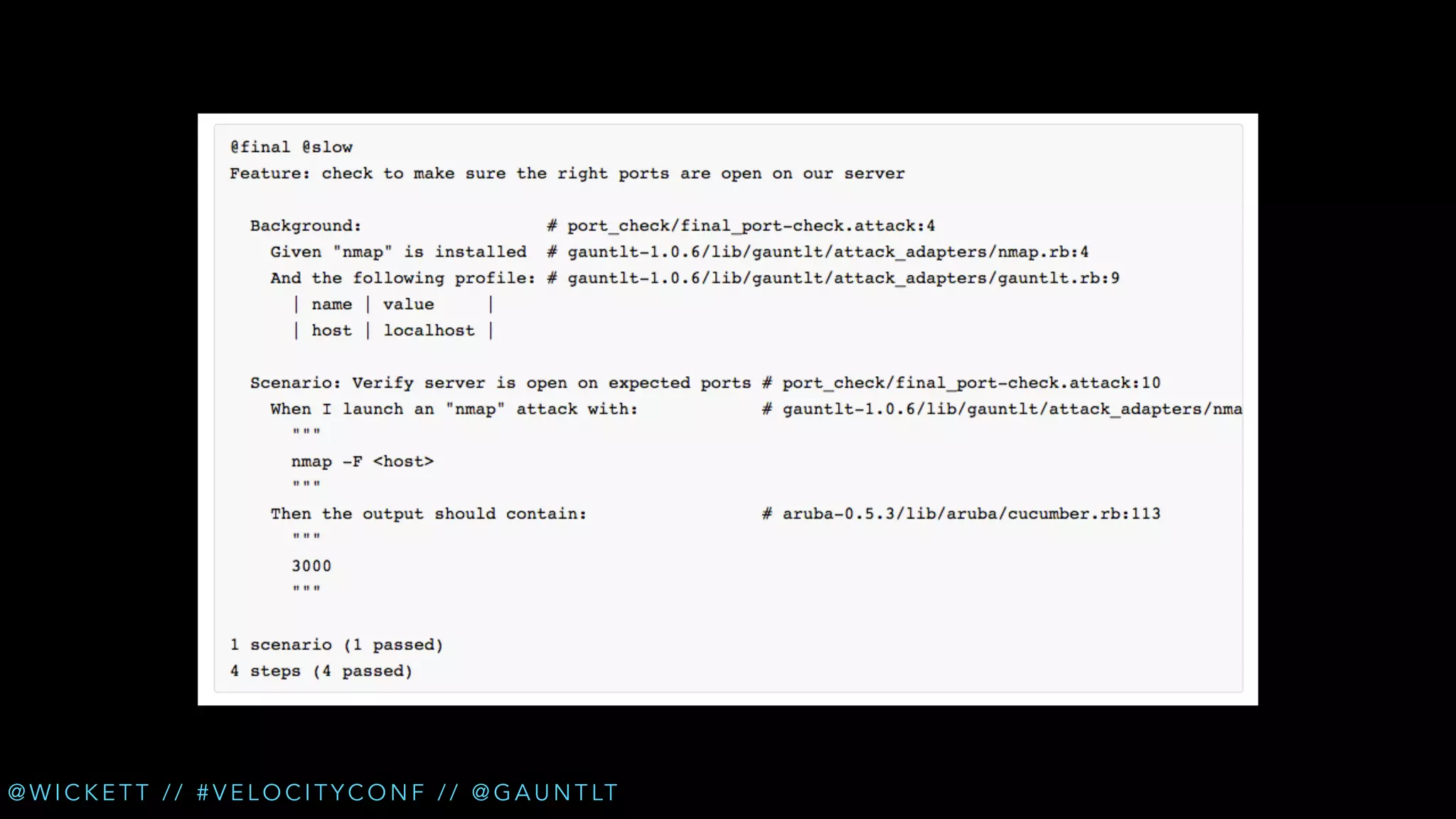
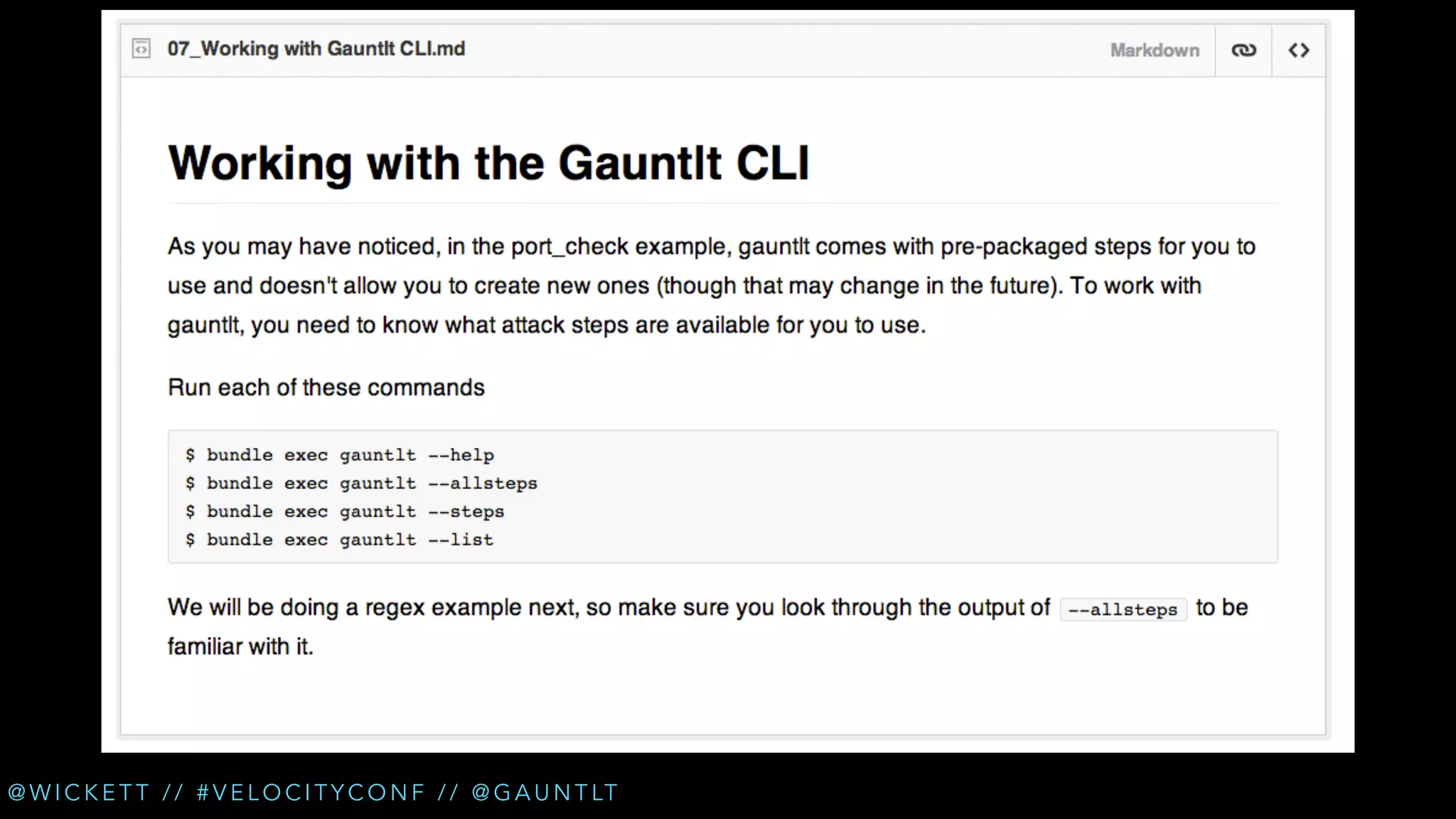
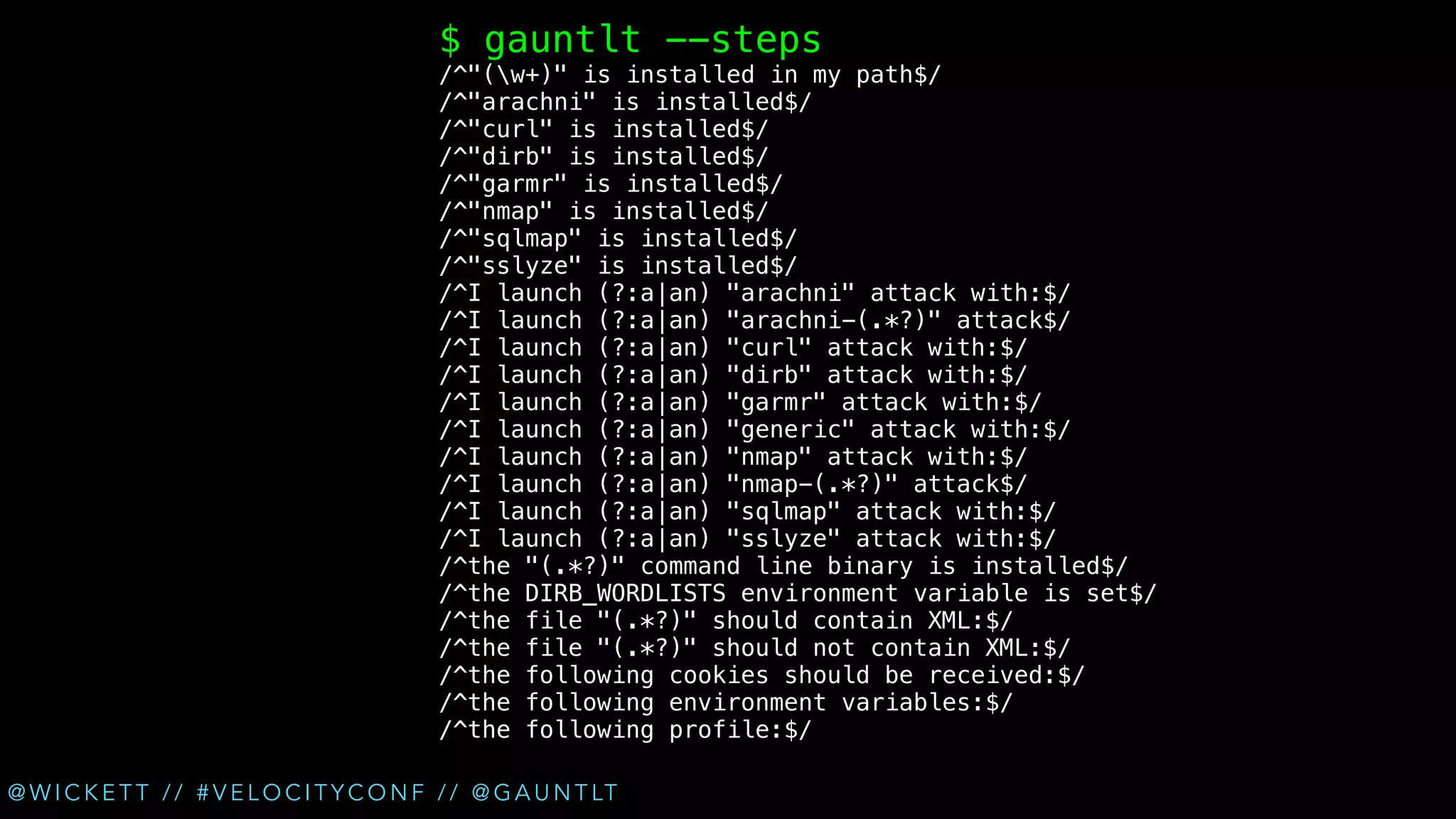
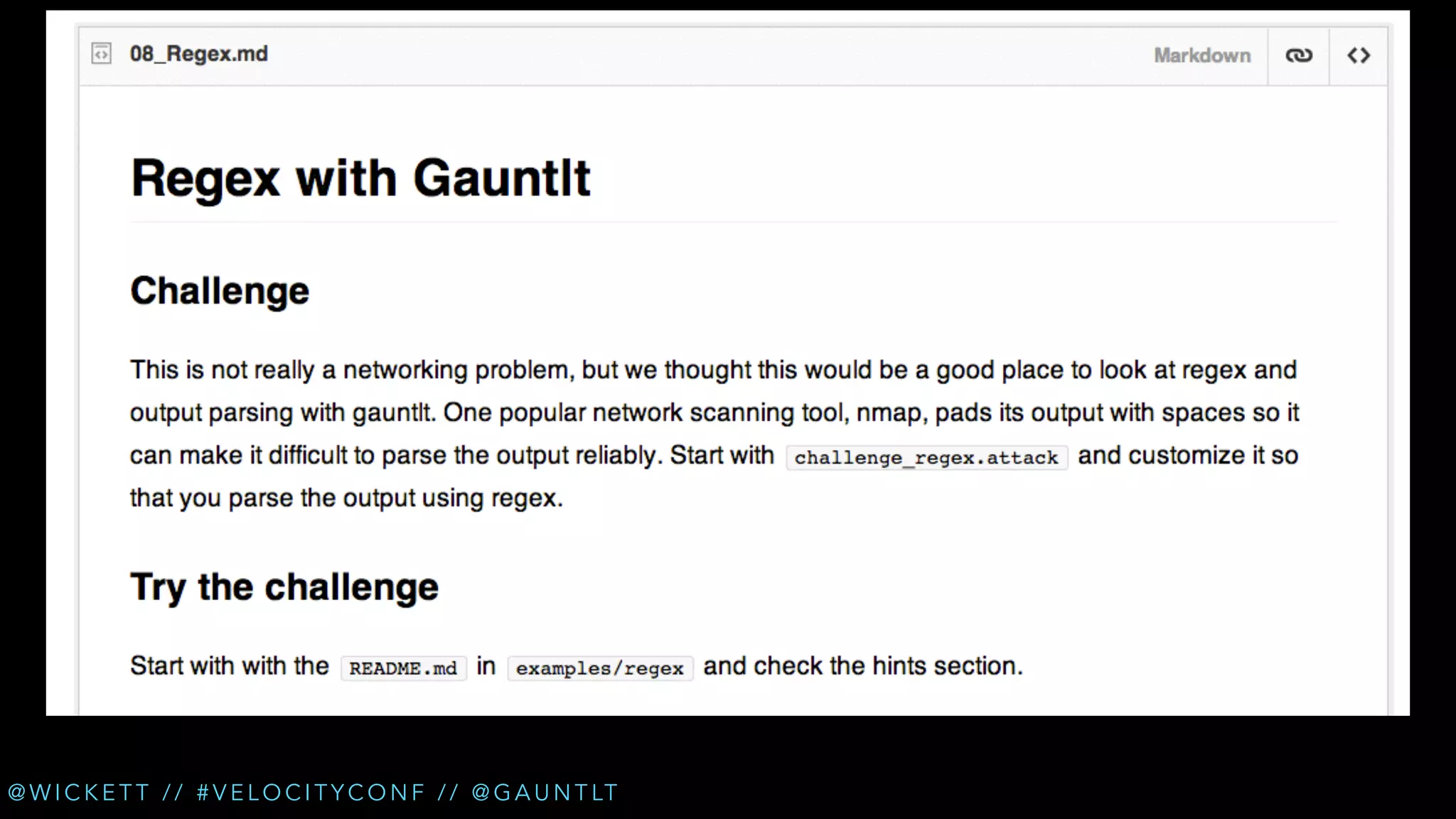
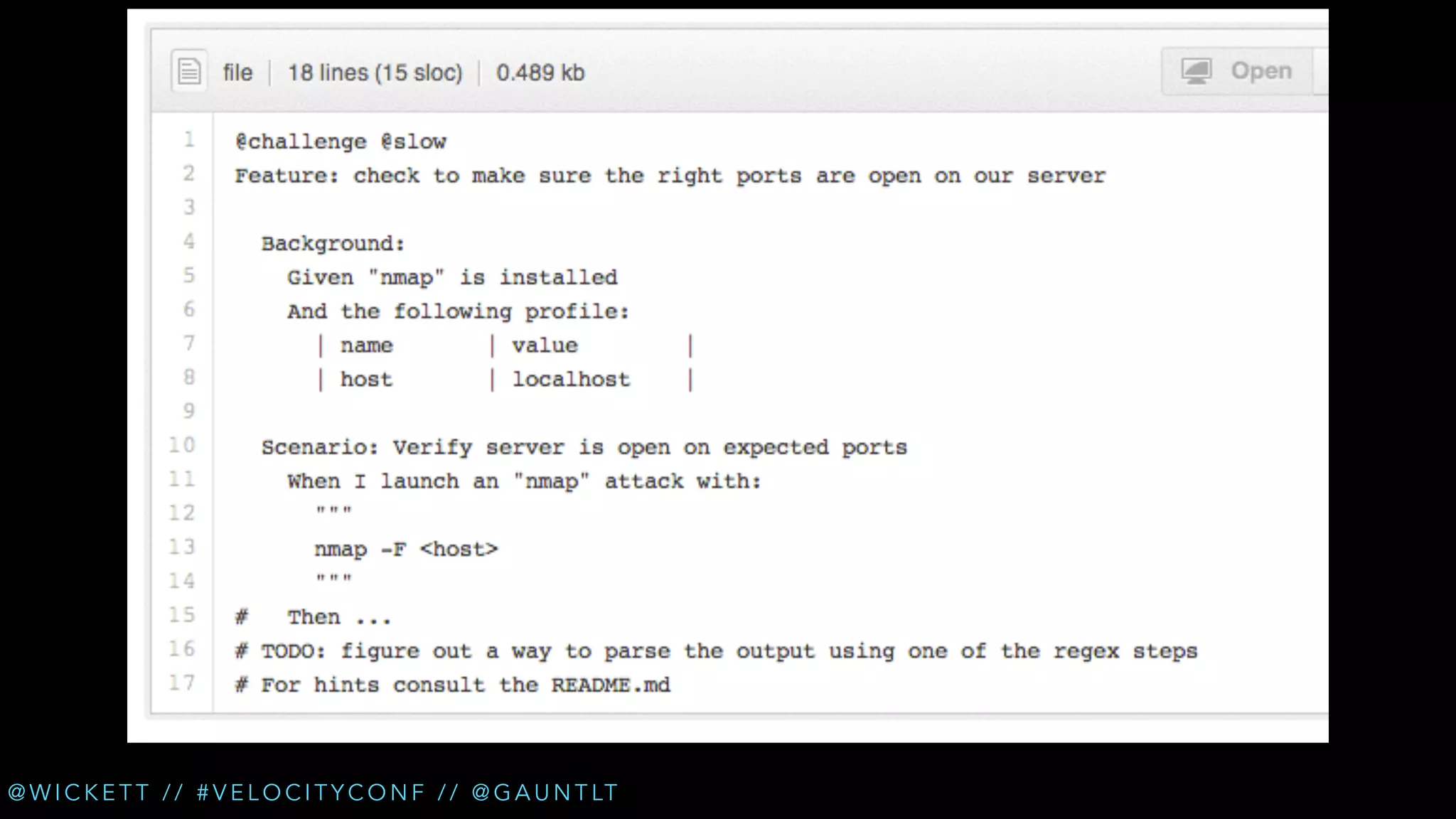
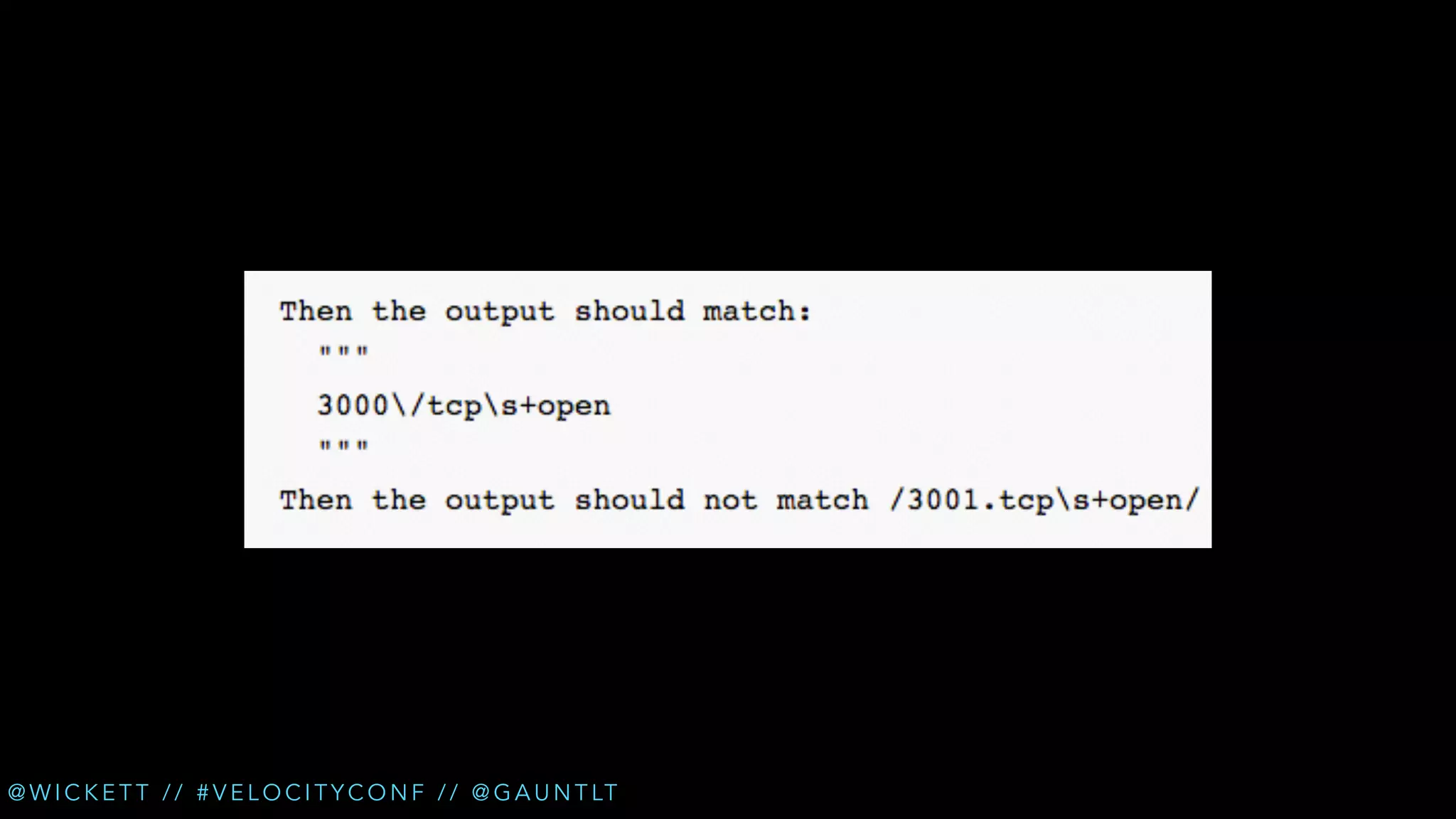
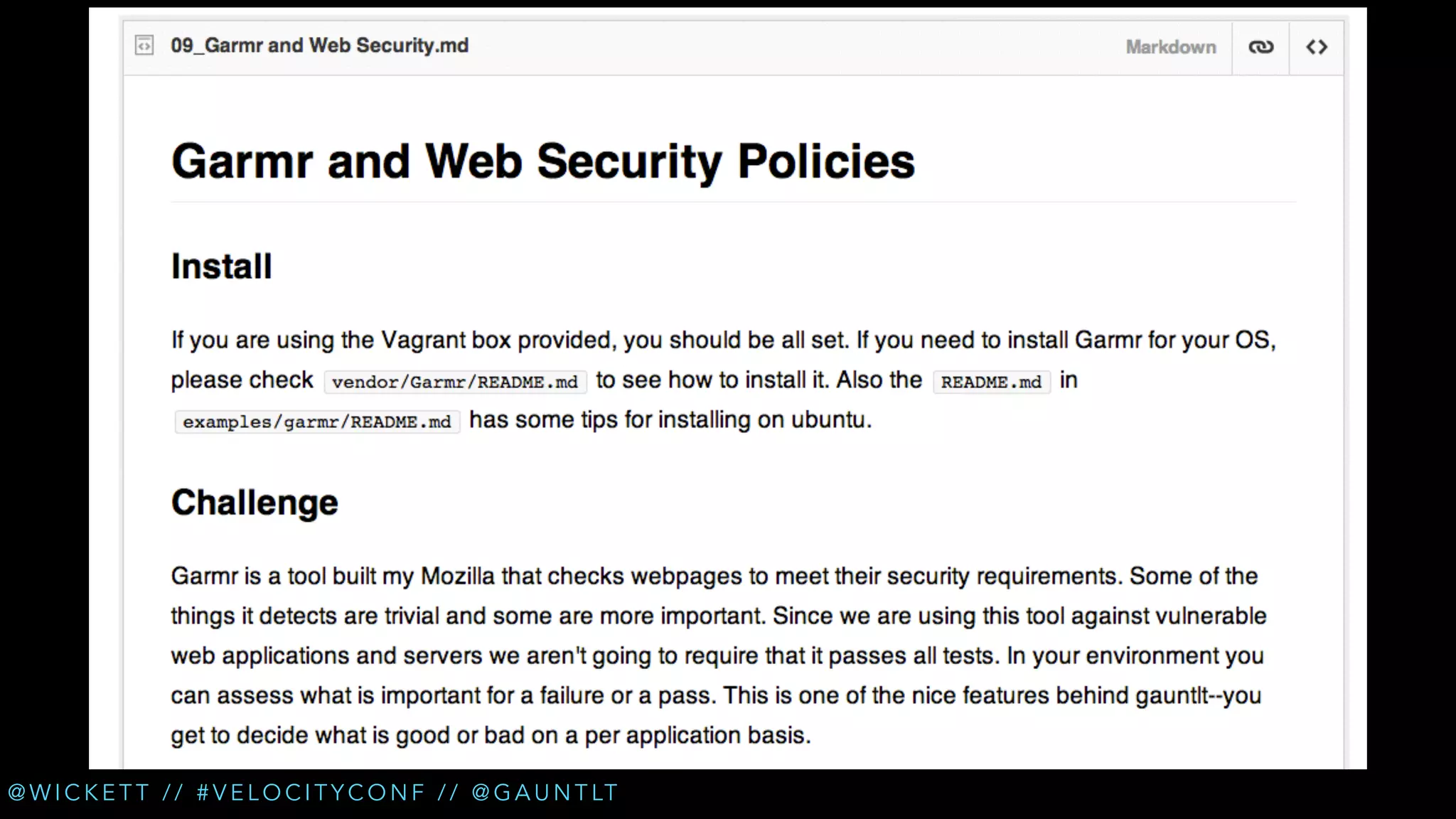
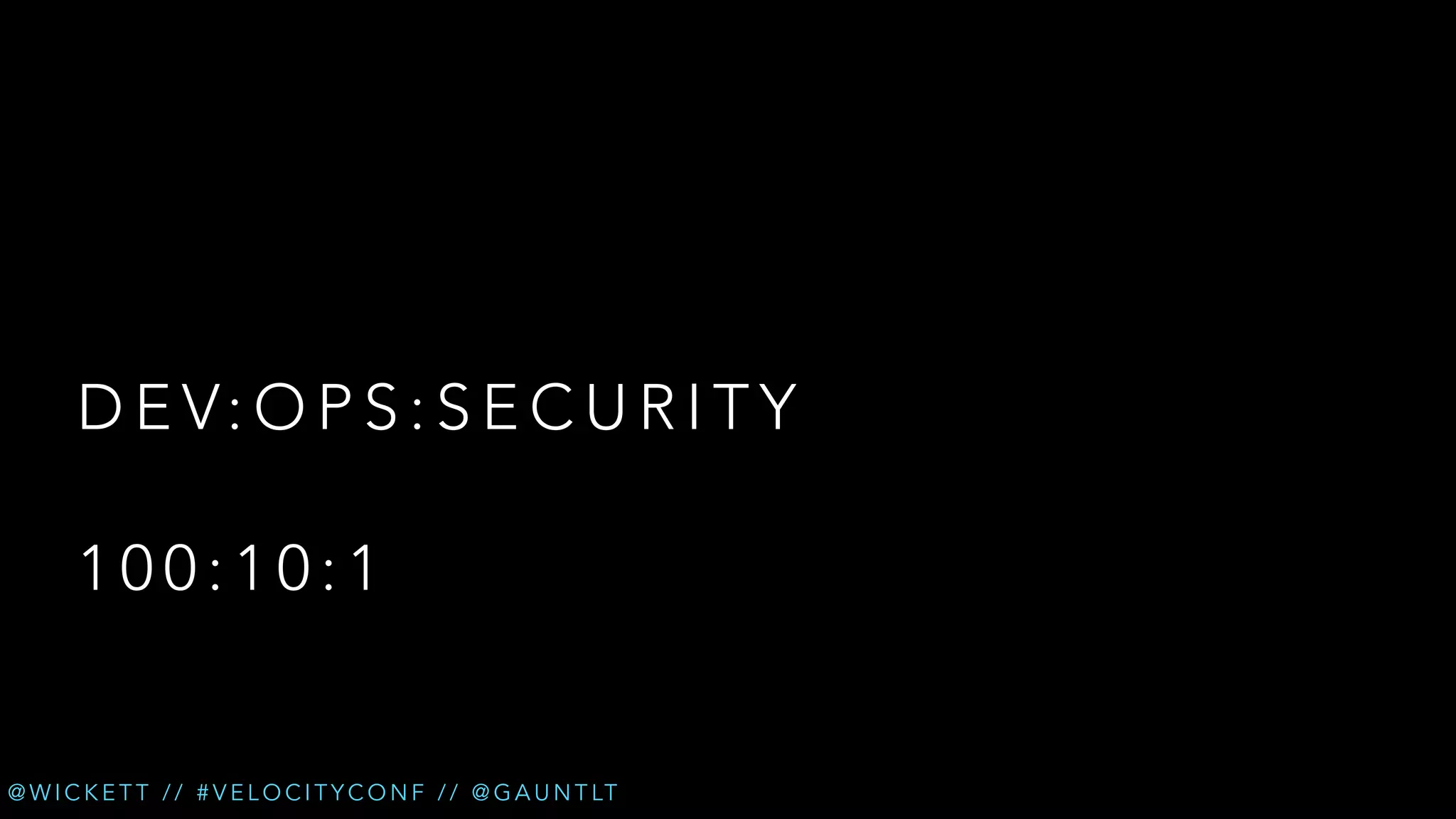
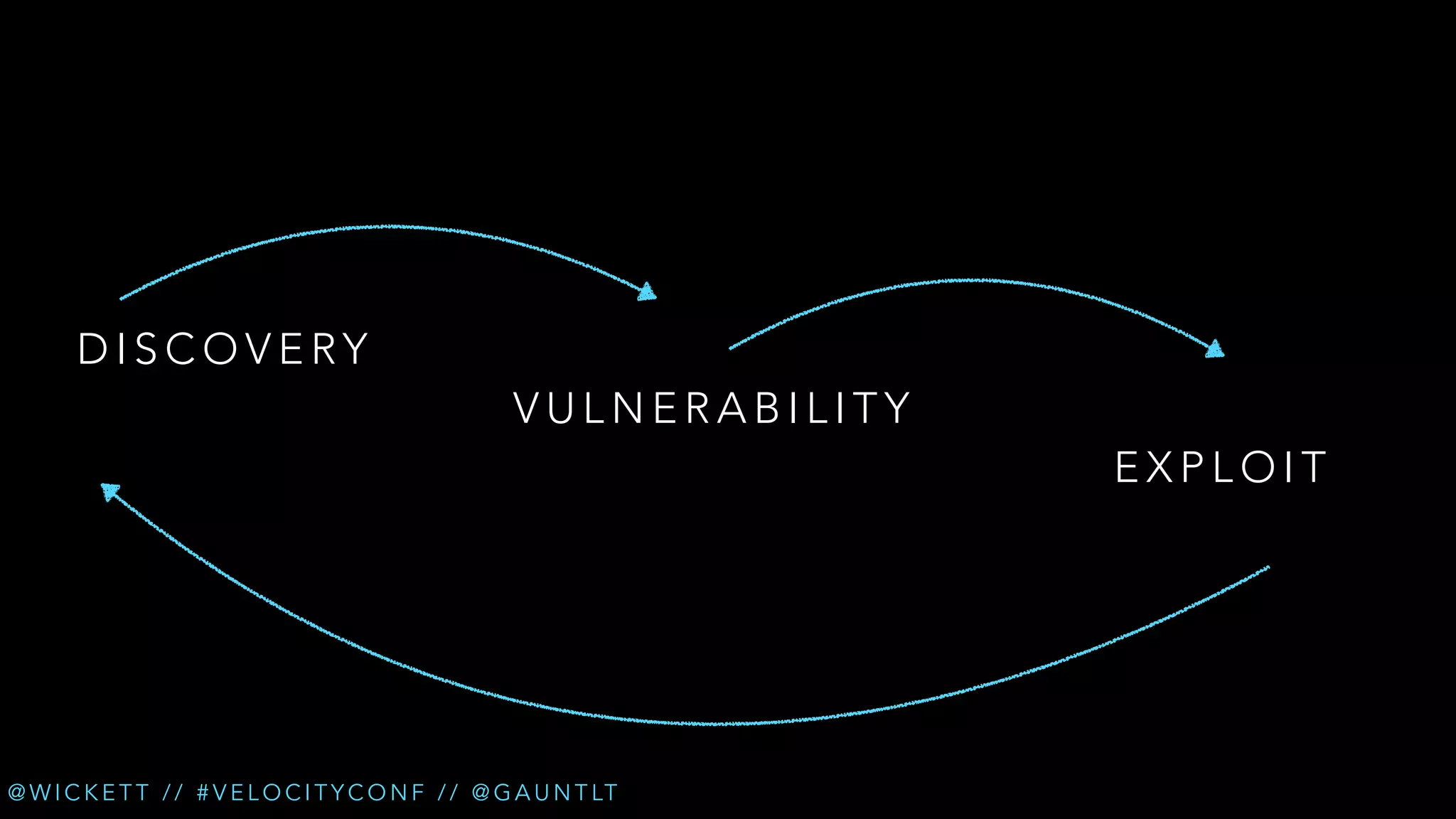
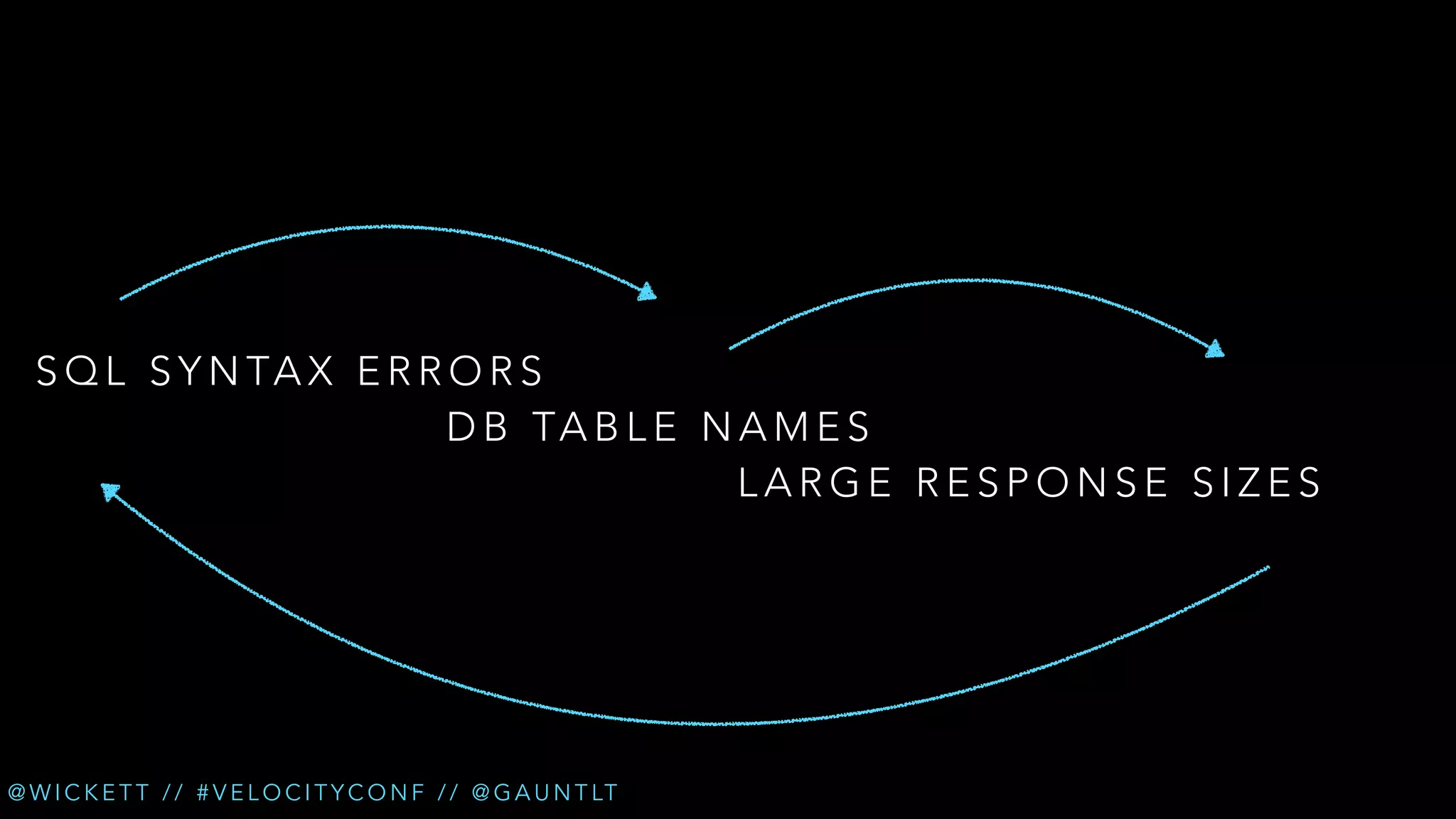
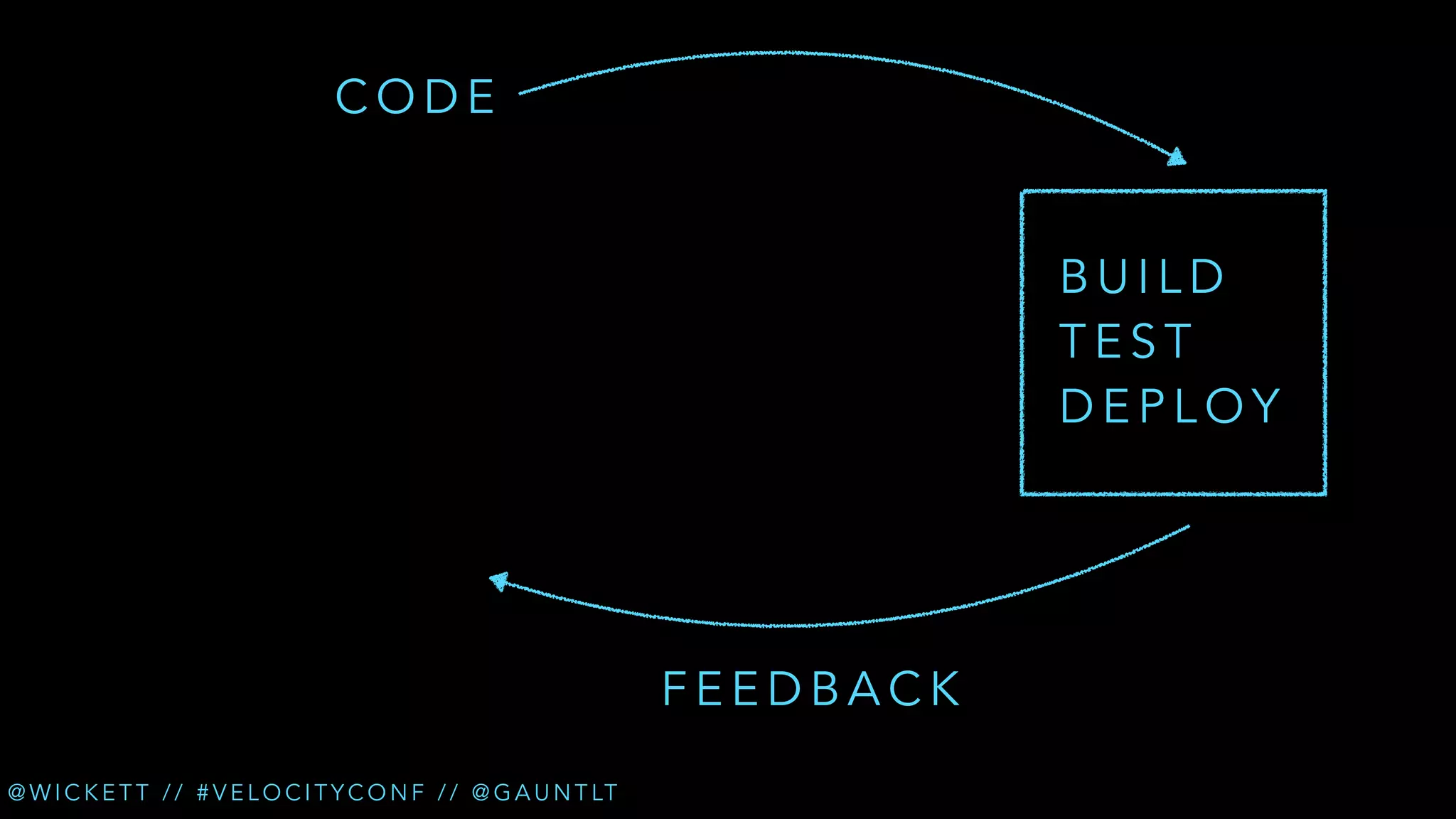
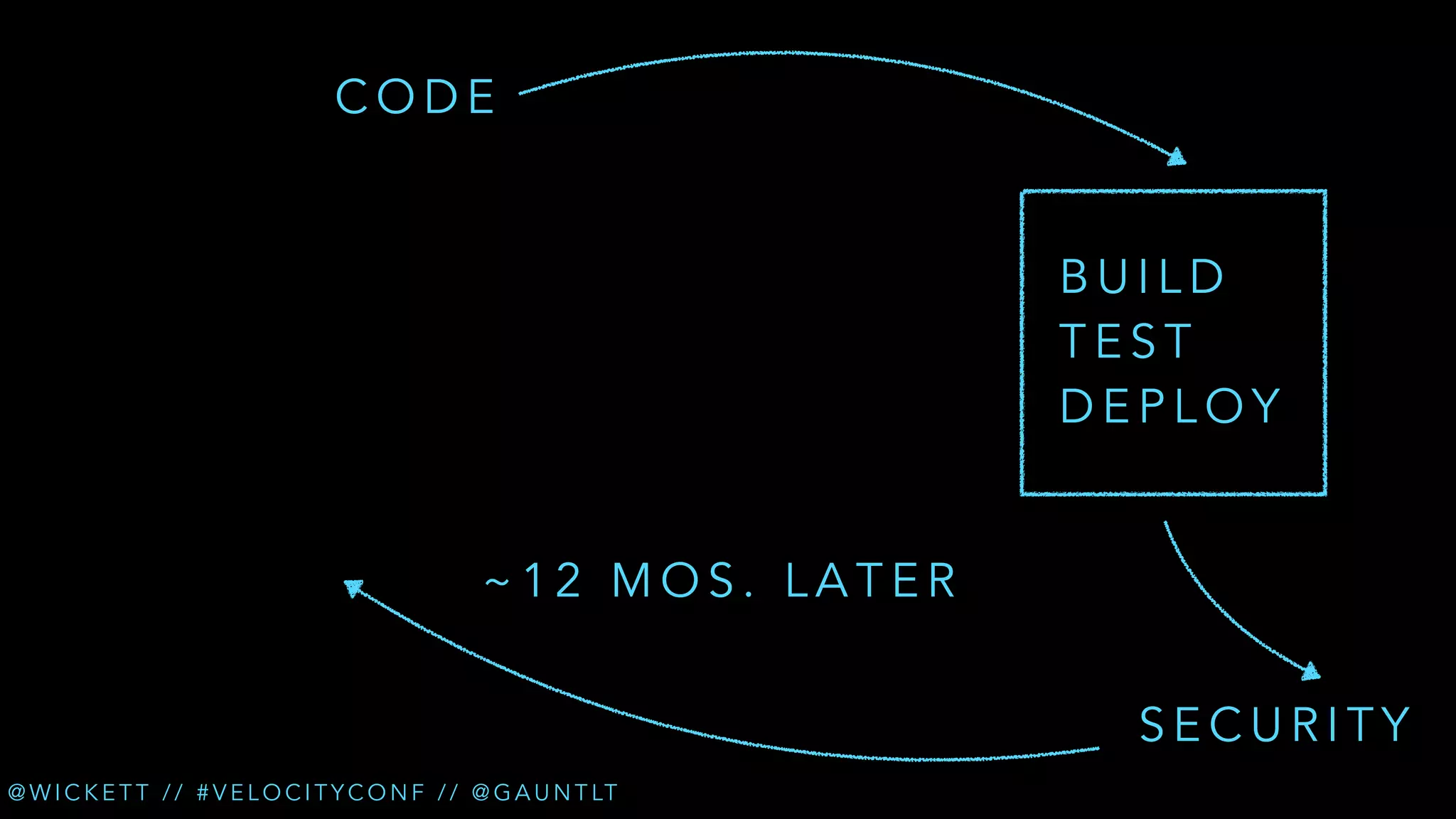
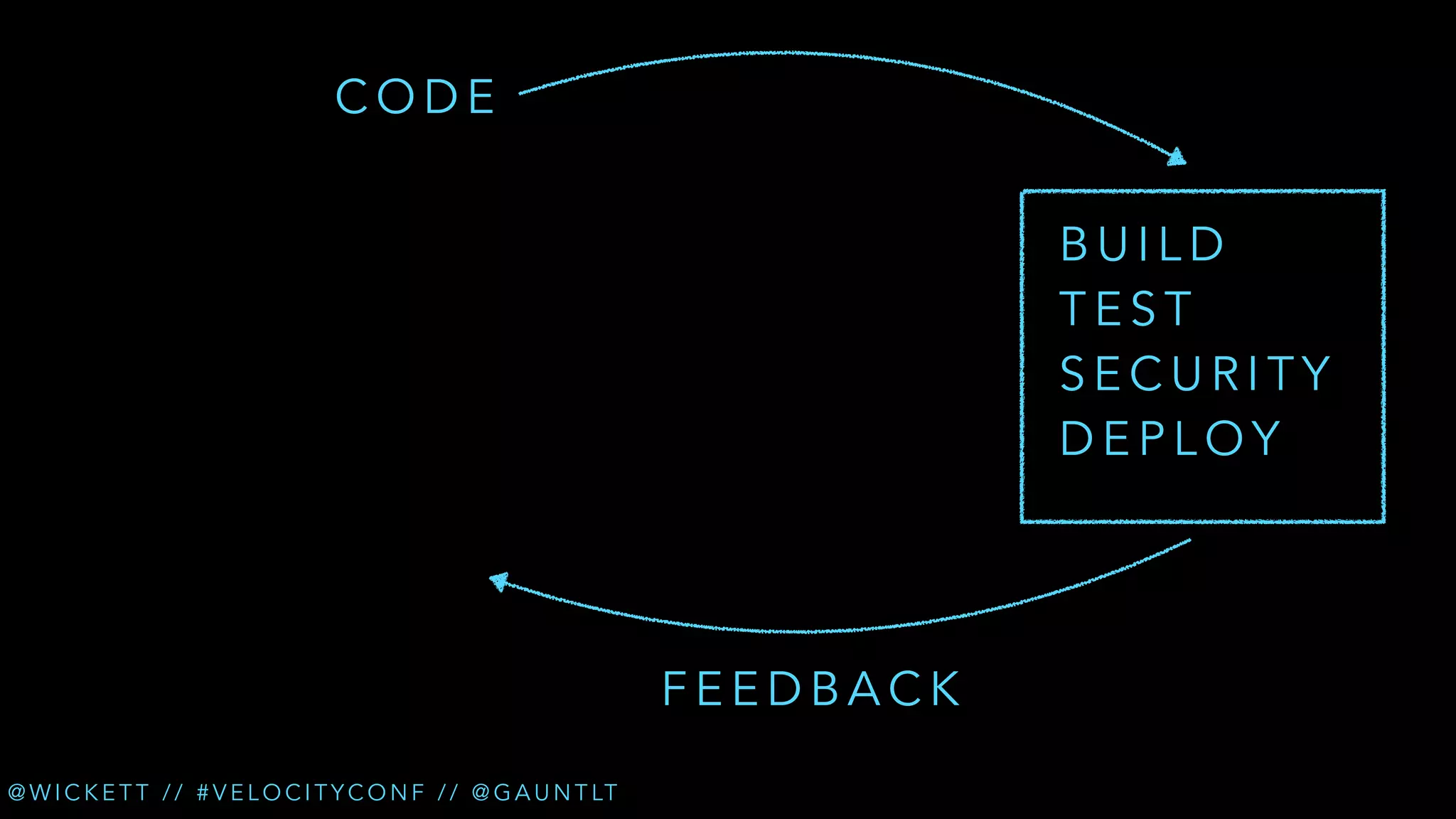
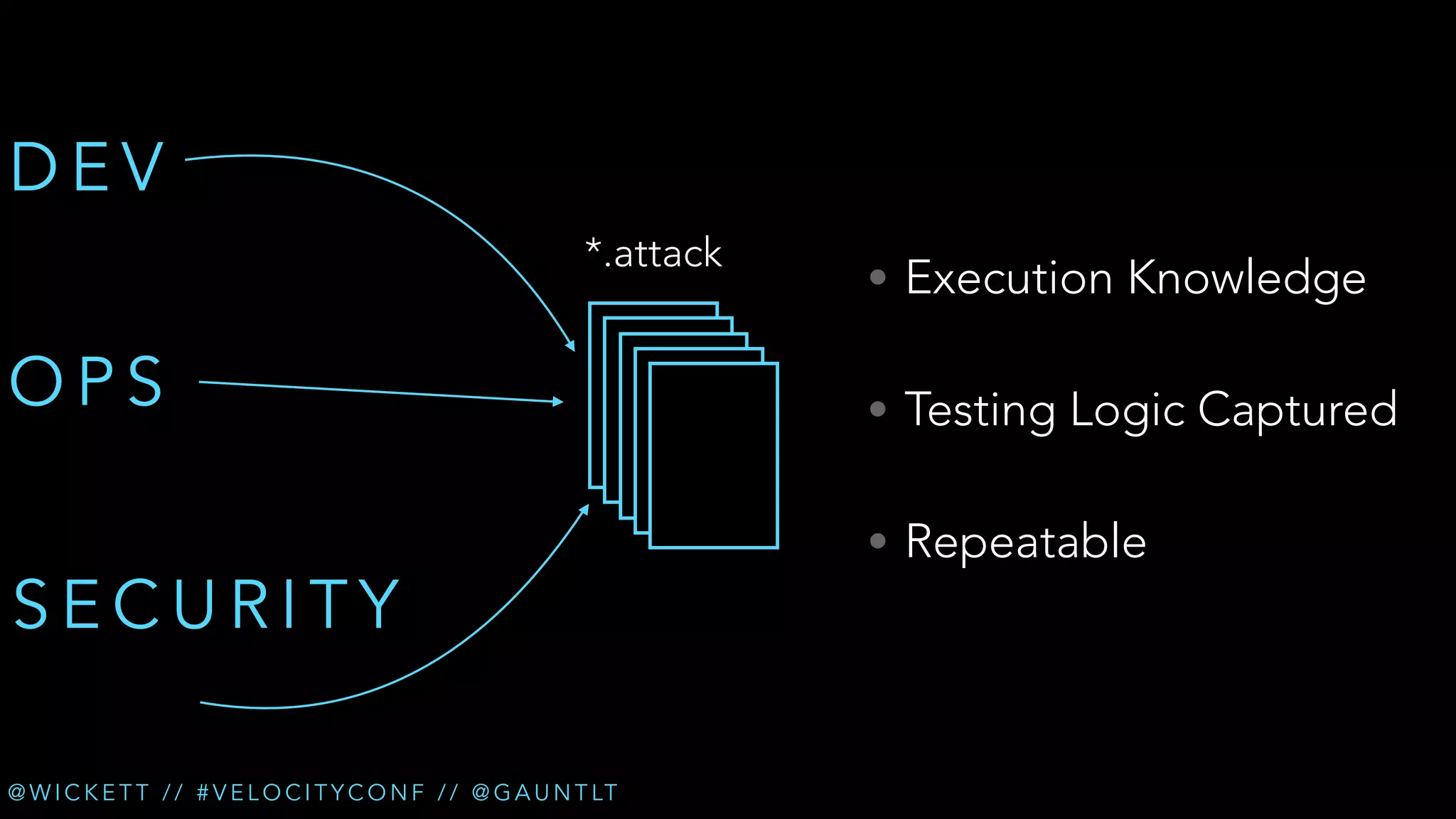
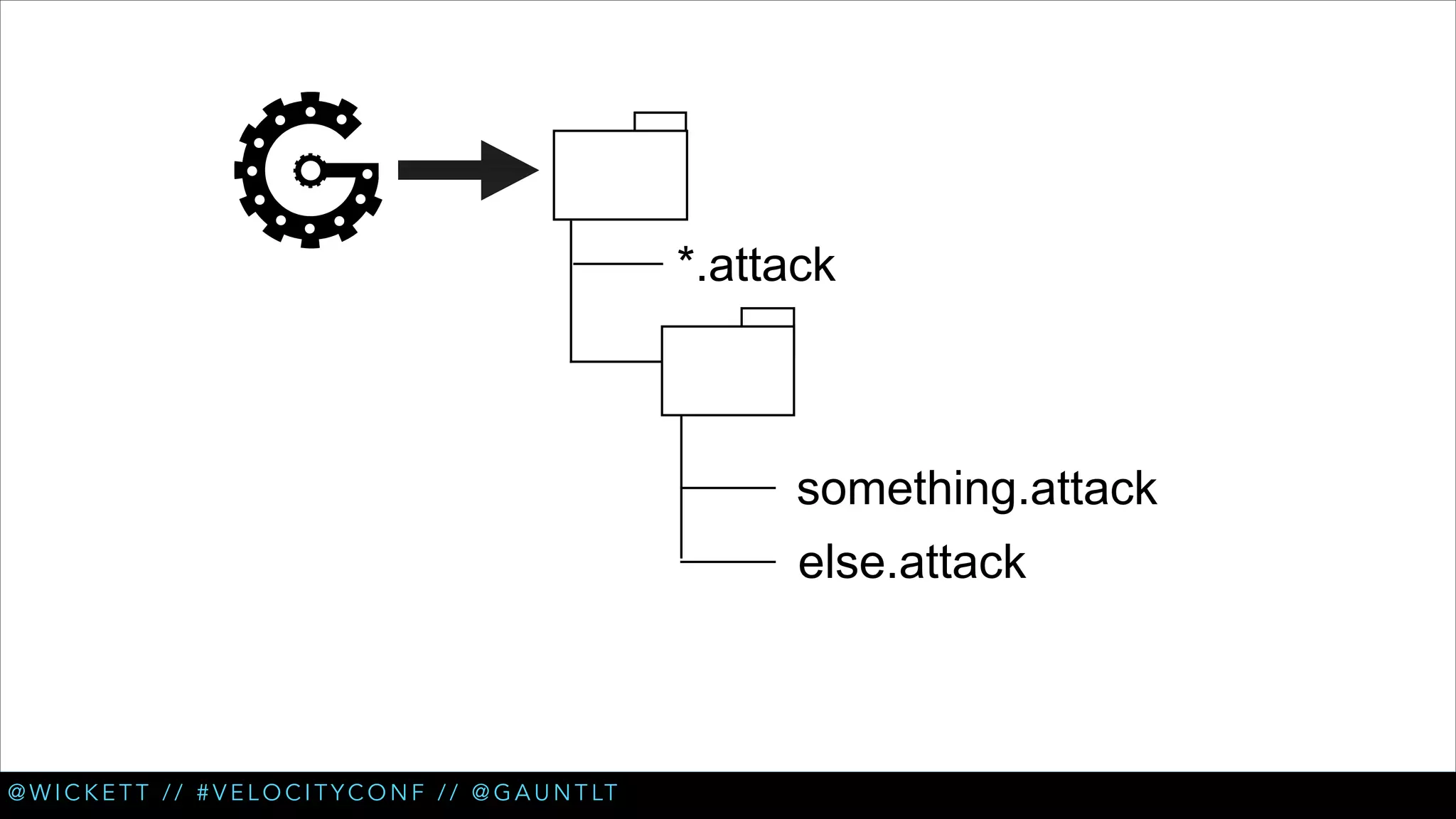
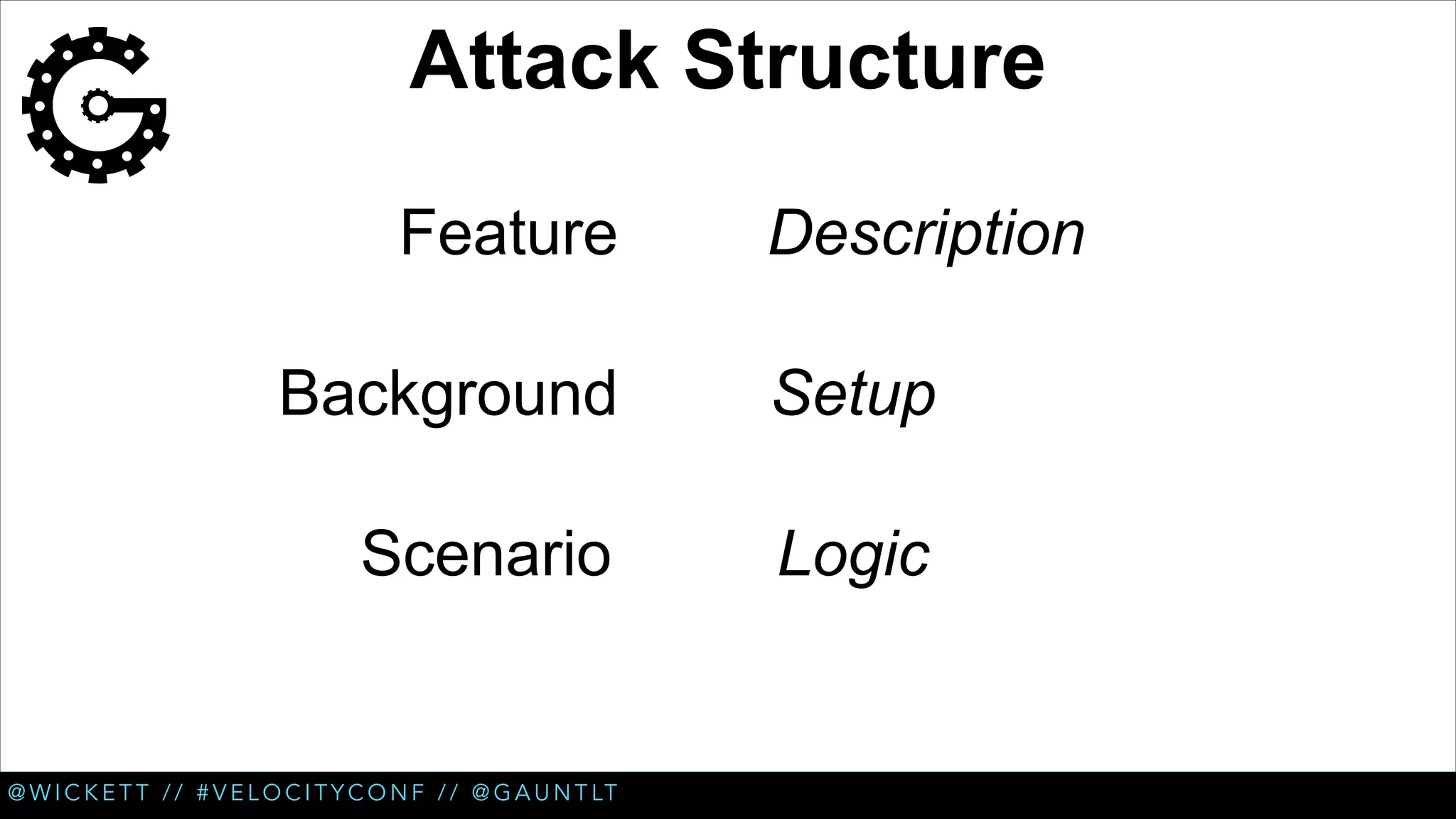
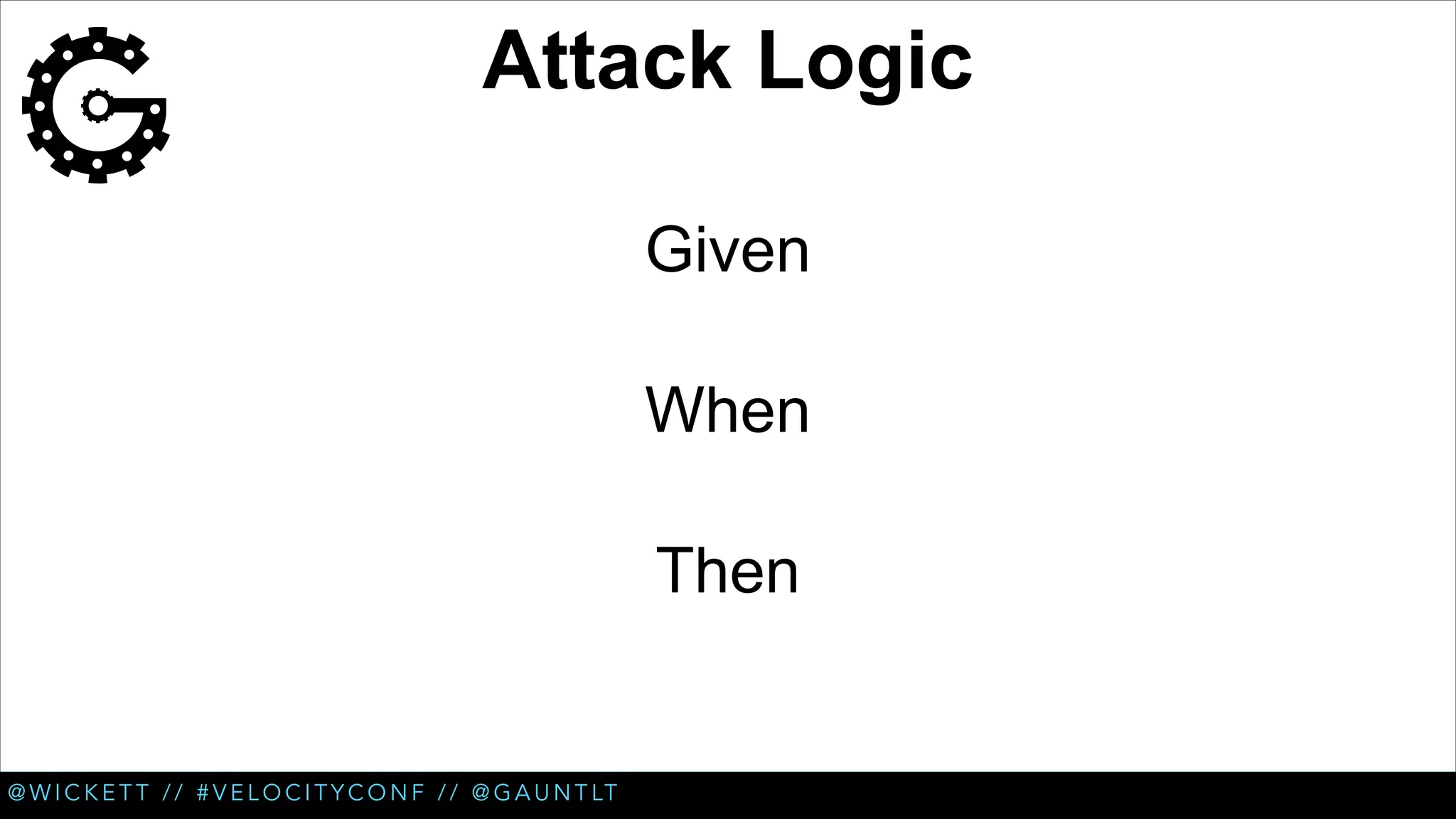
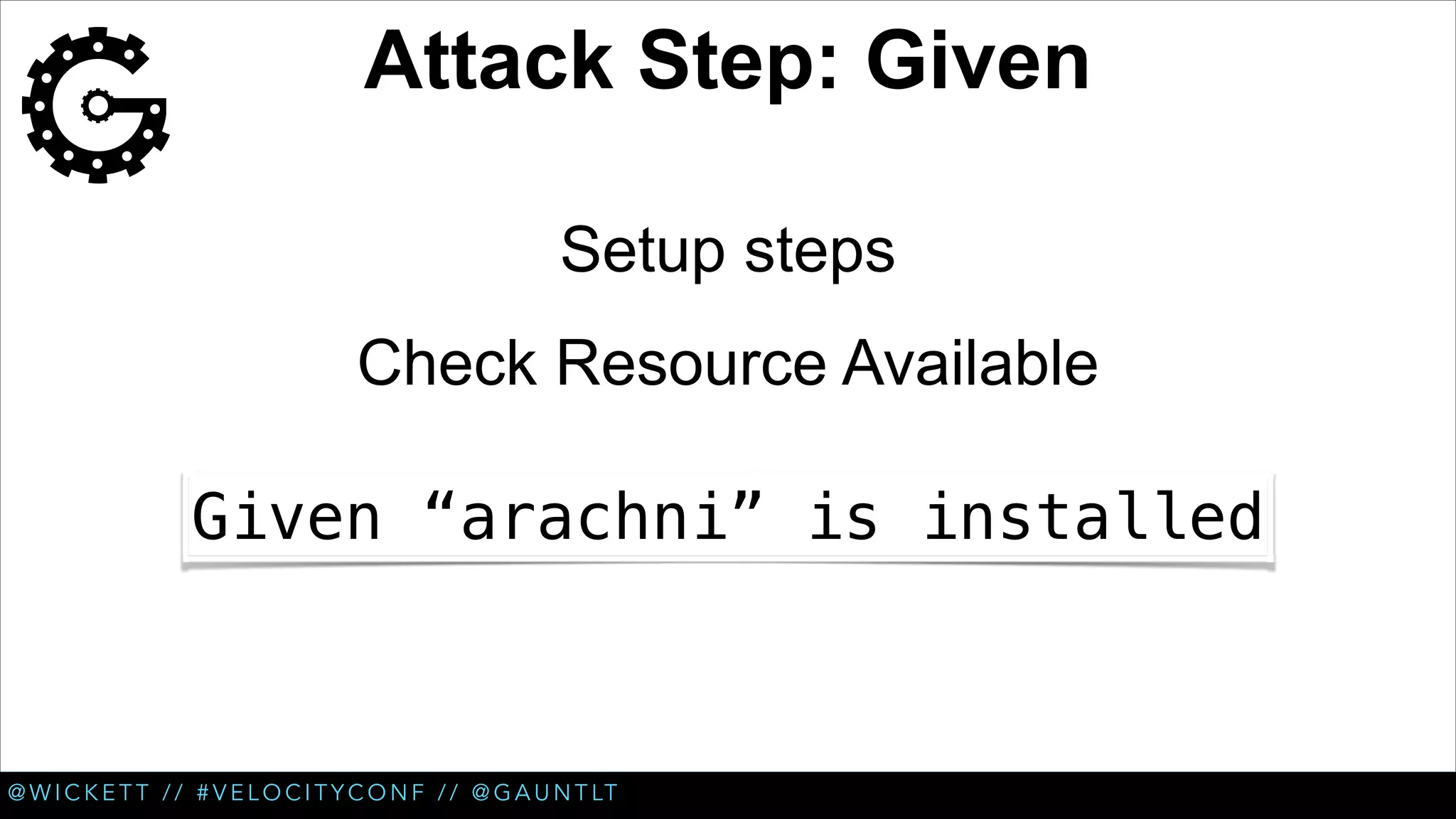
The document discusses the integration of security testing within the DevOps process through the use of a framework called Gauntlt. It emphasizes the need for collaboration between development, operations, and security teams to address vulnerabilities effectively. Key topics include the importance of automated testing, attack structures, and the evolving nature of security practices.





















































![AT A G A M E D E V S H O P
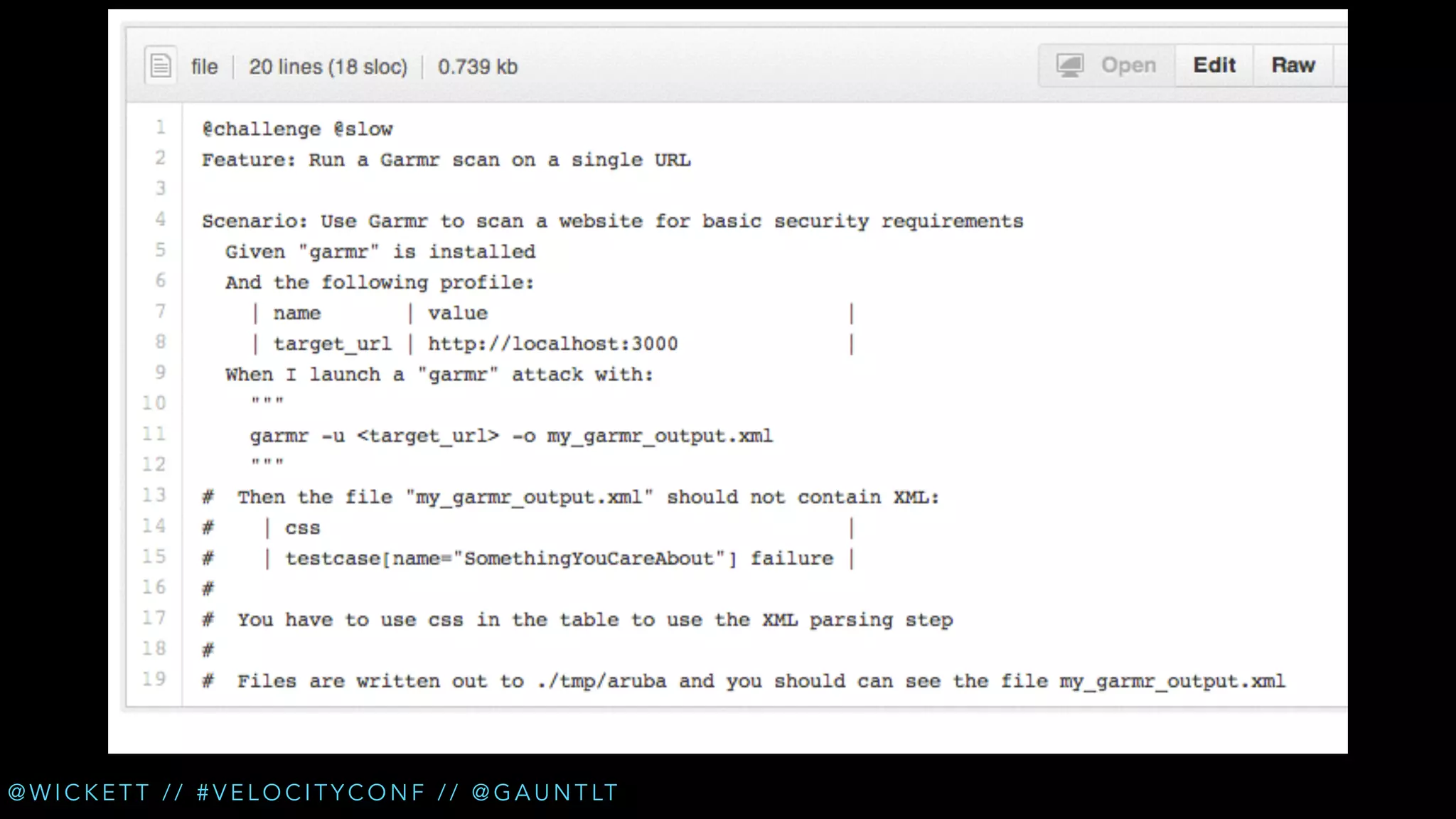
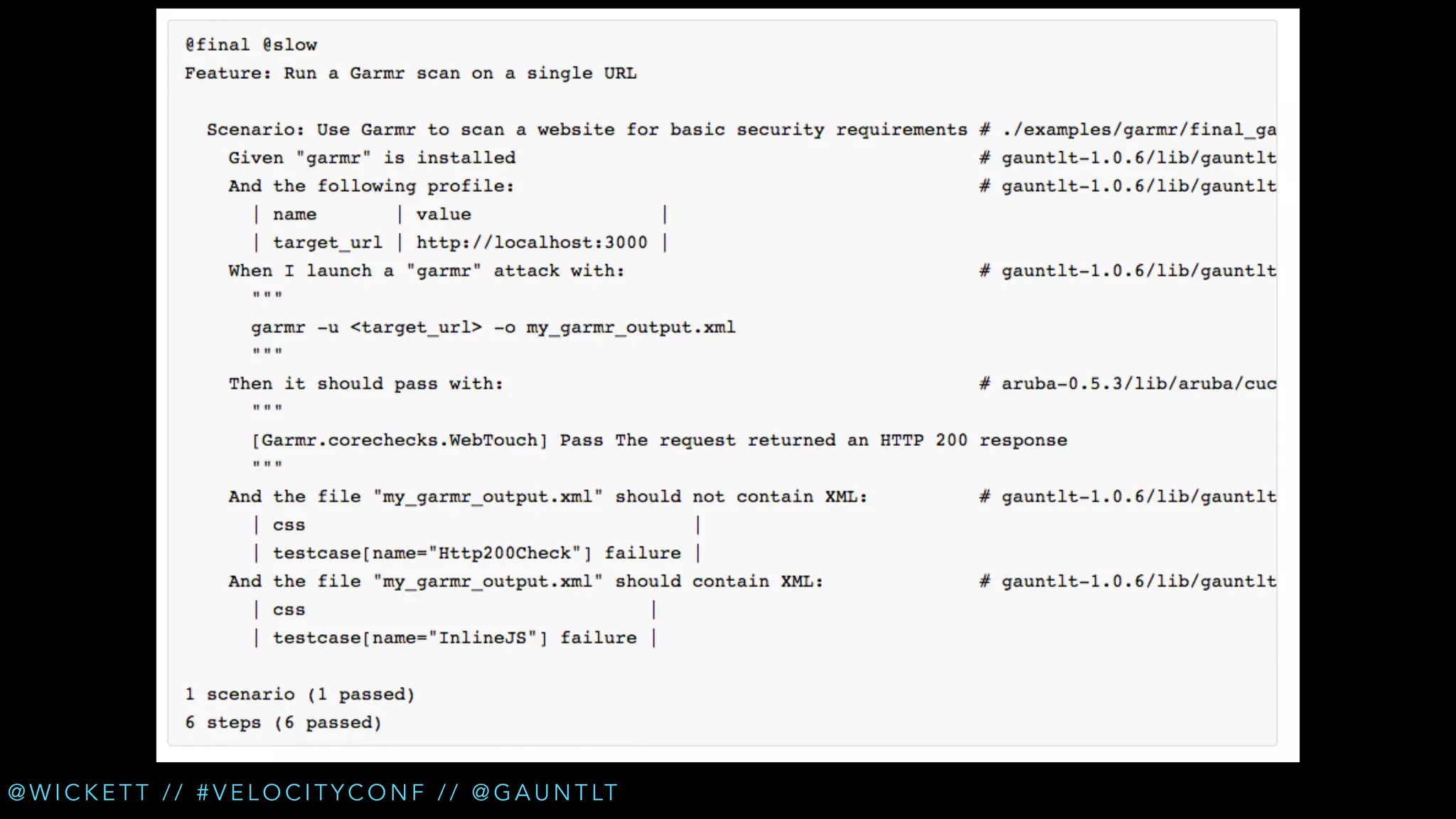
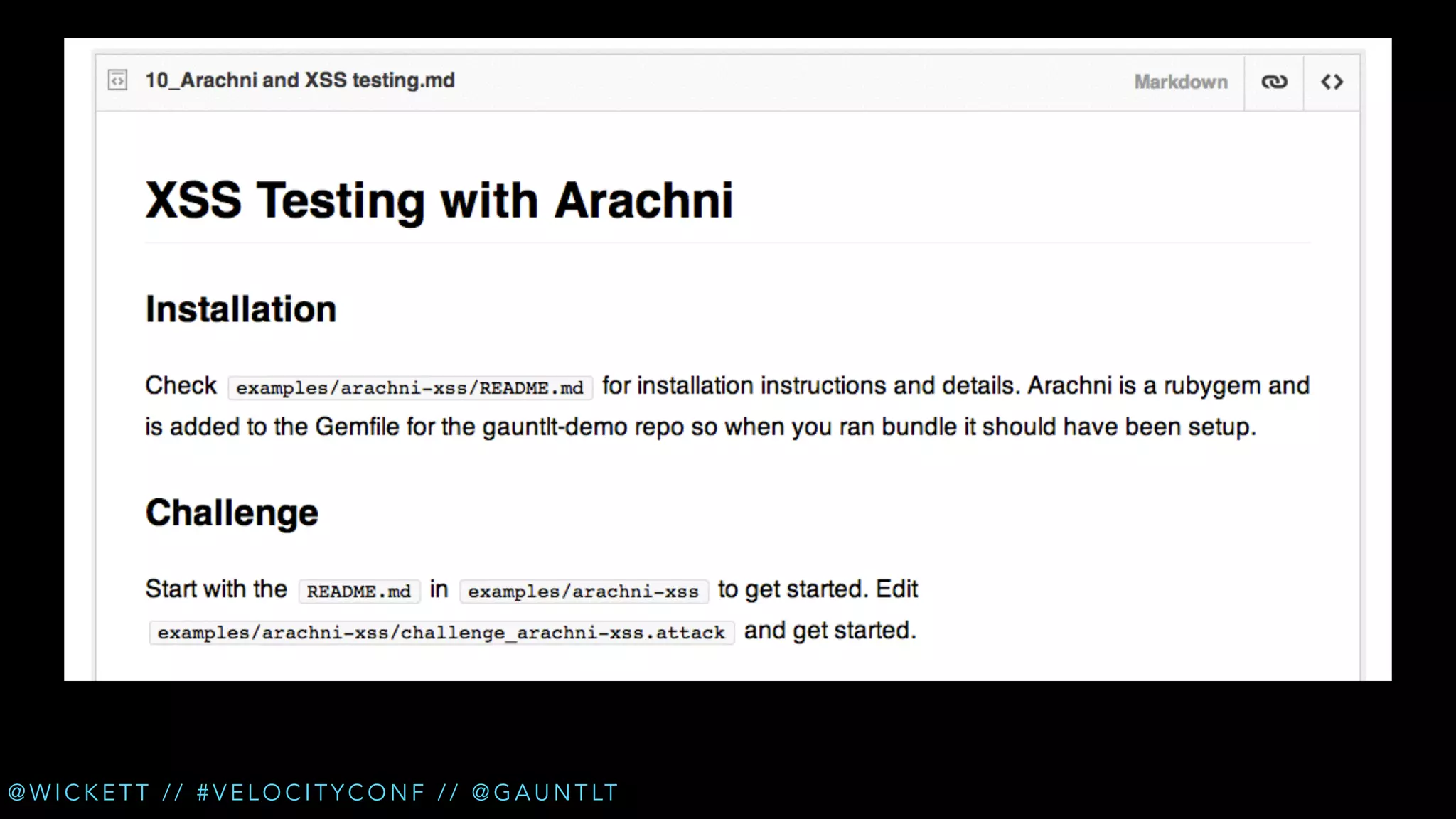
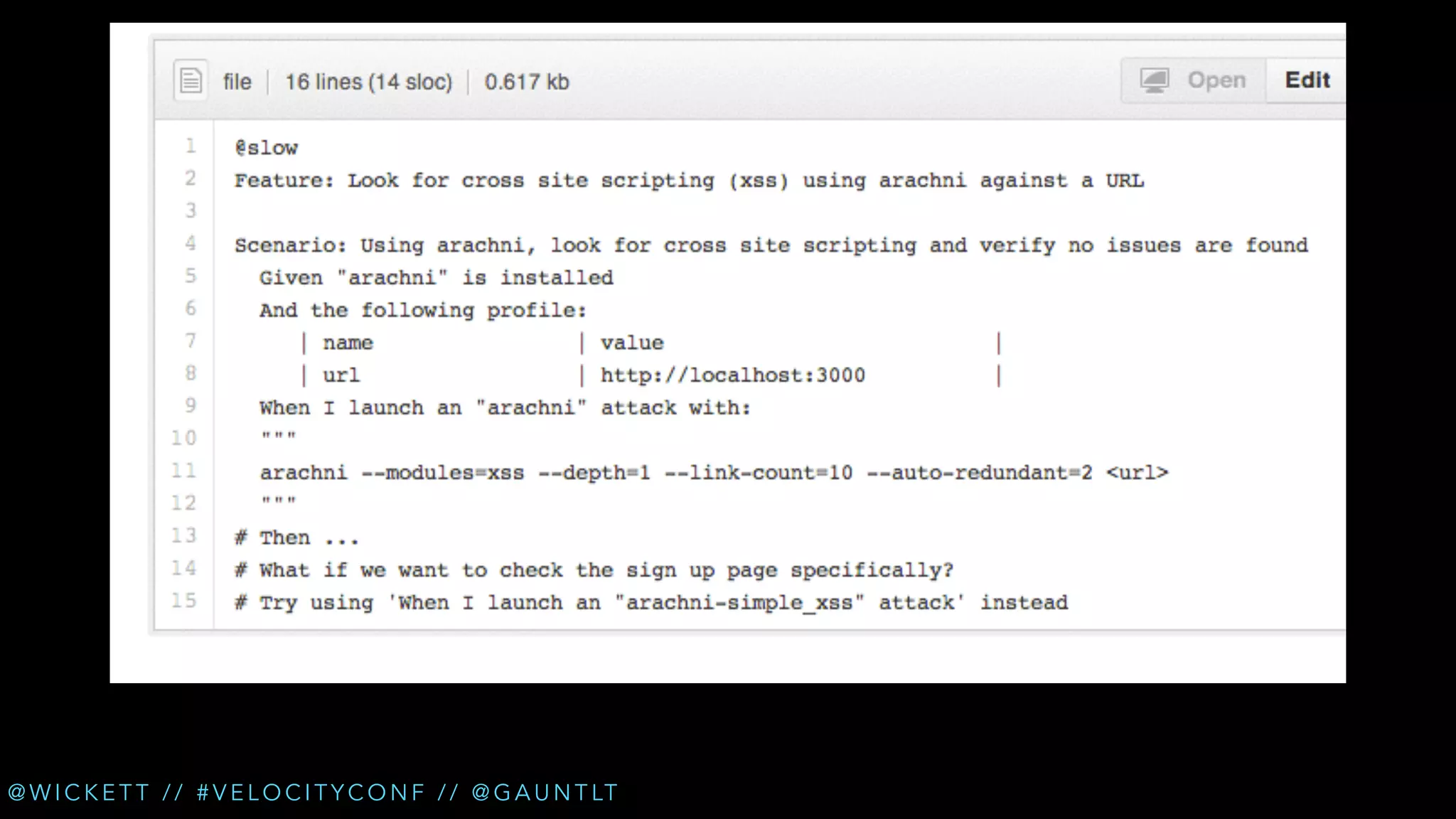
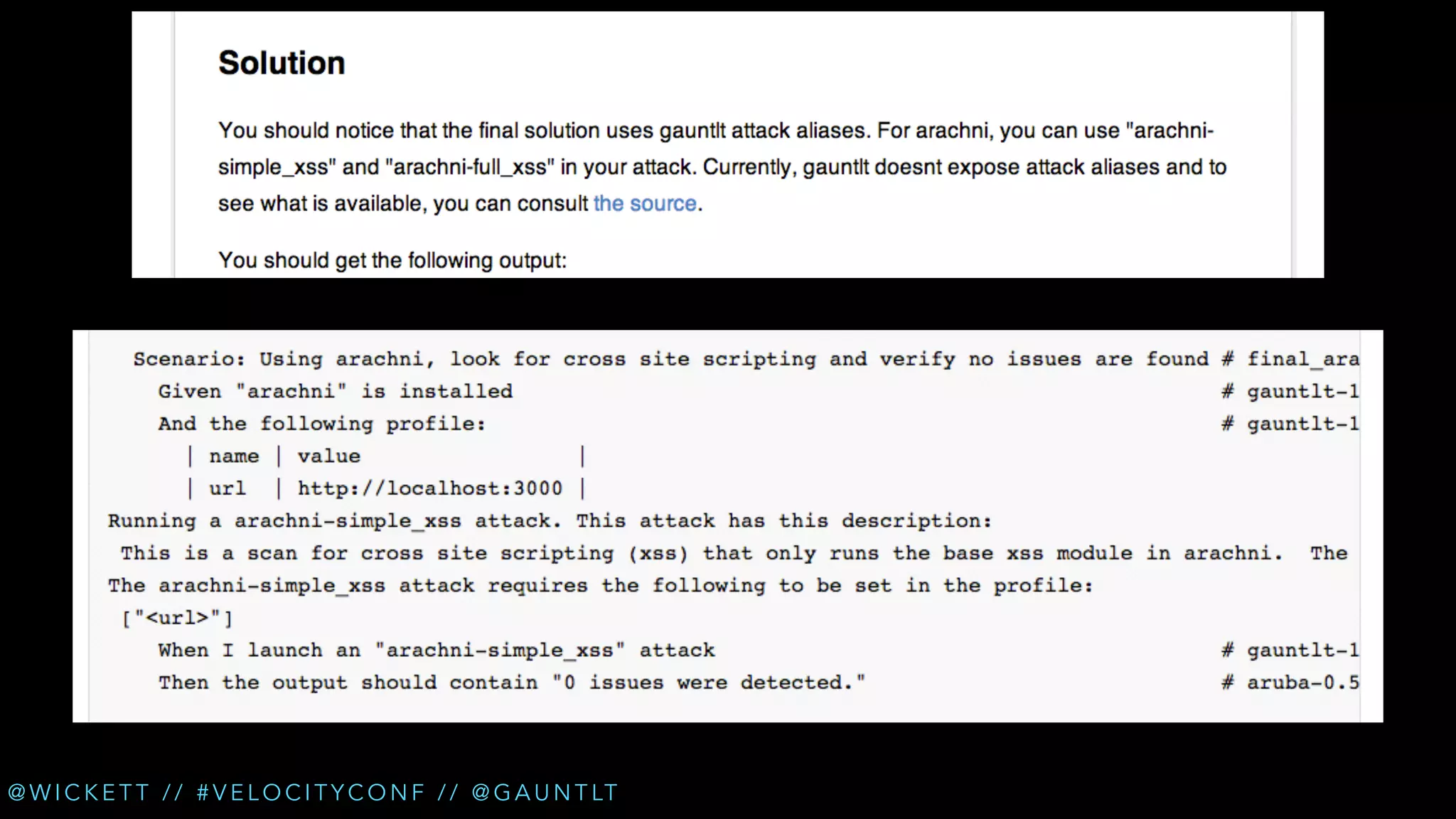
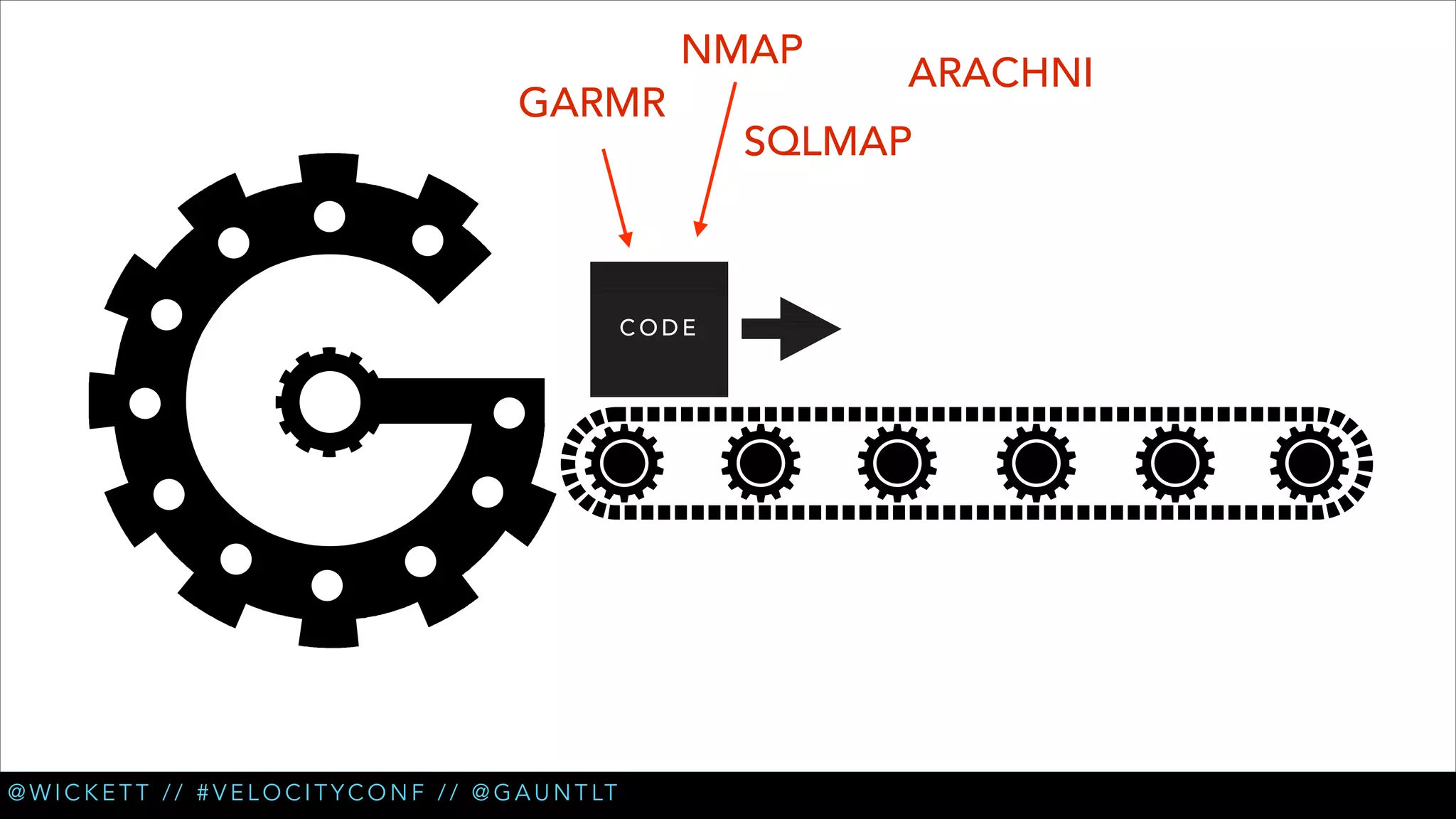
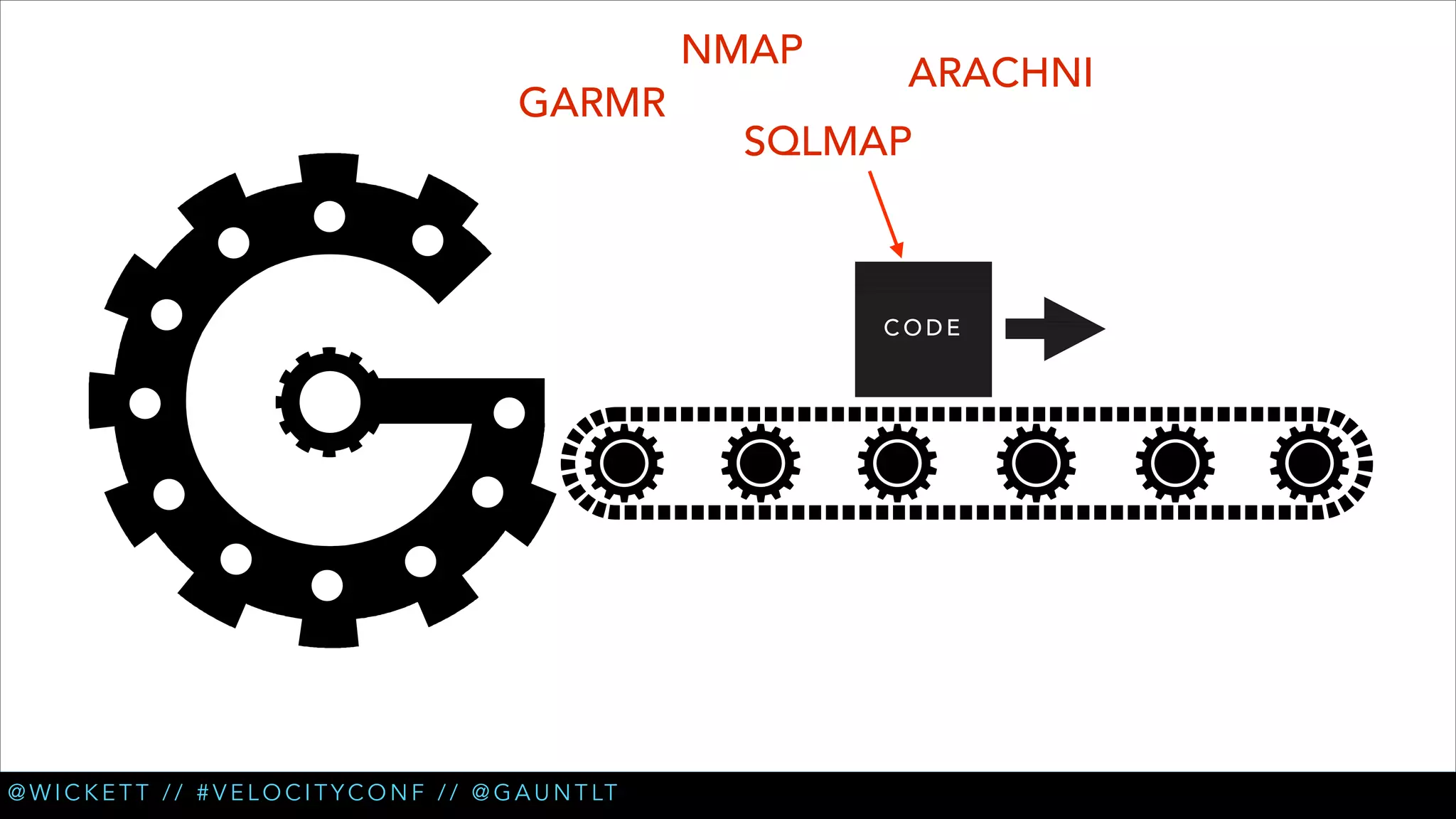
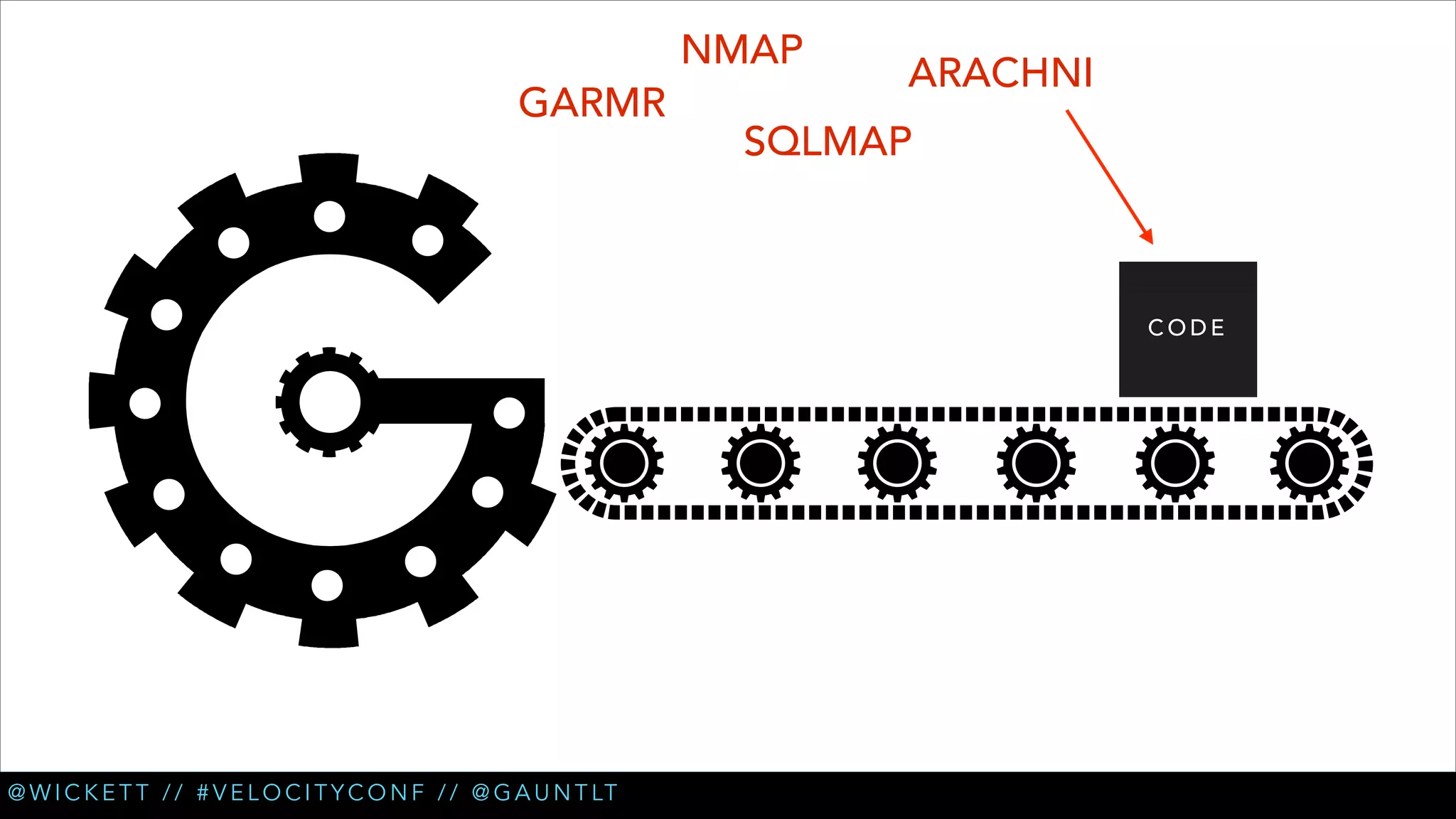
• Check for XSS (cross site scripting) [Arachni]
• Check for new login pages [Garmr]
• Check for insecure refs in login flows [Garmr]
• Extended XSS testing [Custom Arachni] (PR coming soon)
@ W I C K E T T / / # V E L O C I T Y C O N F / / @ G A U N T LT](https://image.slidesharecdn.com/gauntlt-velocityeu-2013-131113094126-phpapp02/75/Be-Mean-to-Your-Code-with-Gauntlt-and-the-Rugged-Way-Velocity-EU-2013-Workshop-86-2048.jpg)
![MENTOR GRAPHICS
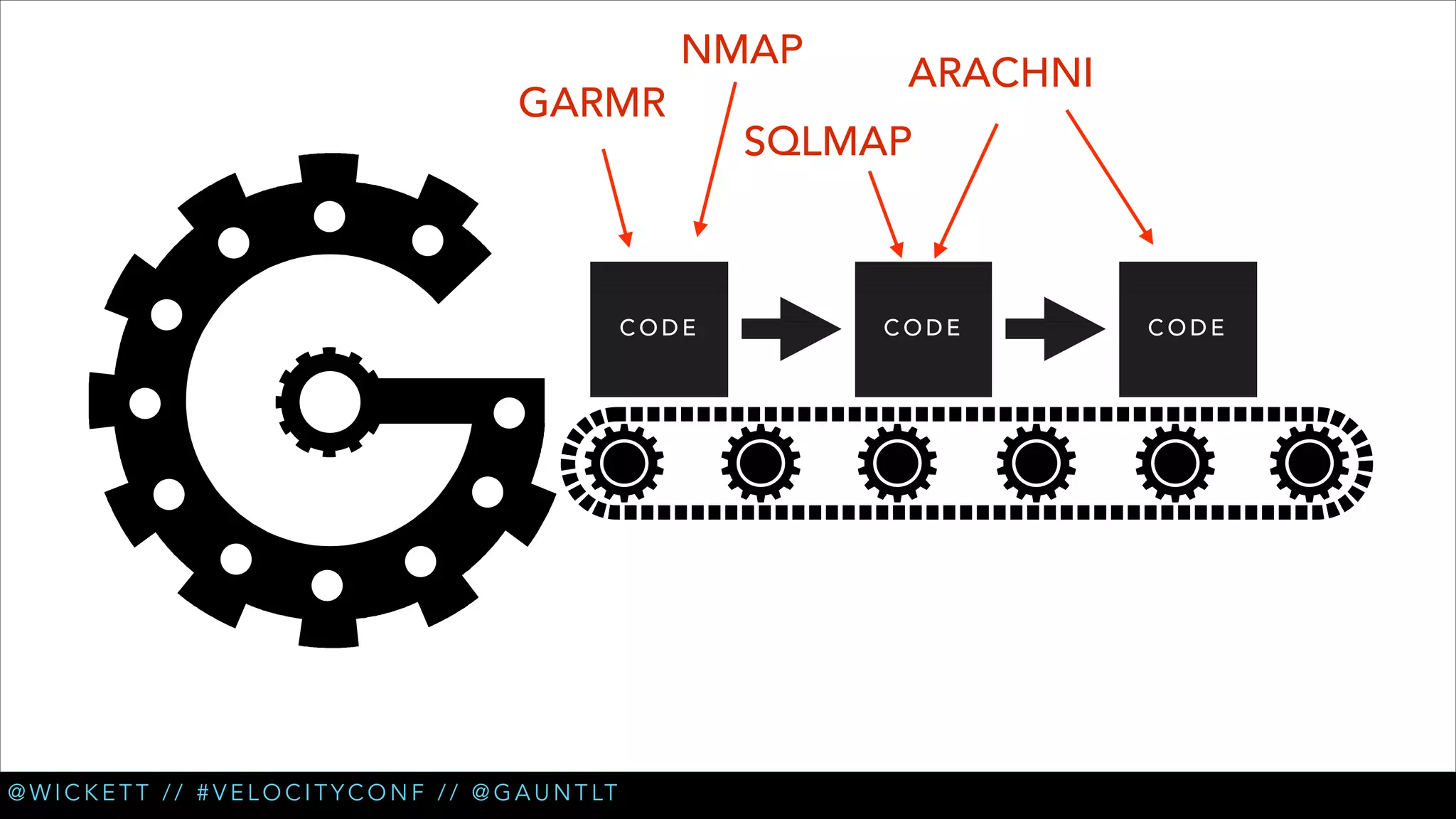
• Smoke Test integration on environment build
• Checks REST services [curl]
• Tests for XSS [arachni]
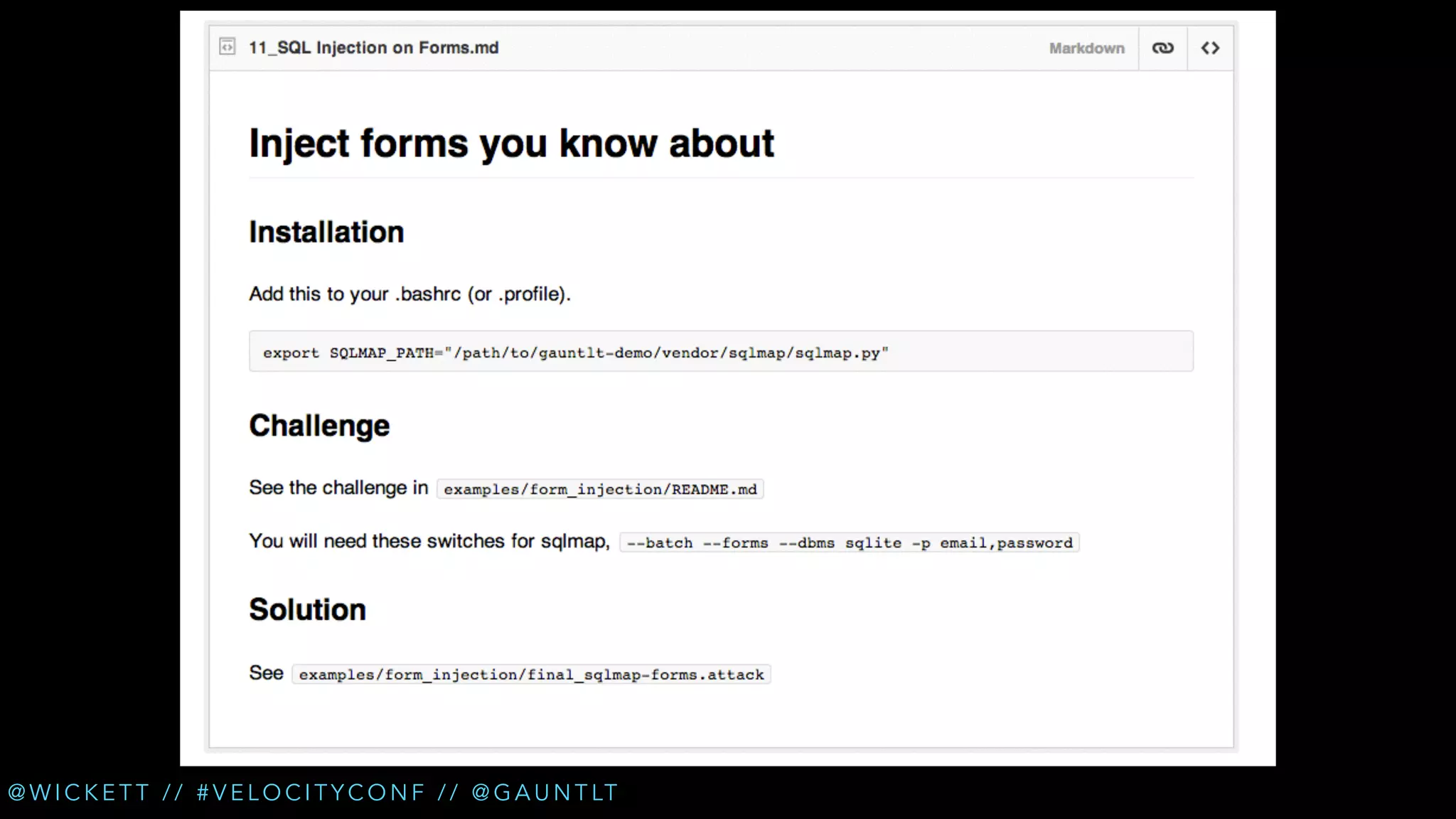
• Injection attacks [sqlmap, dirb]
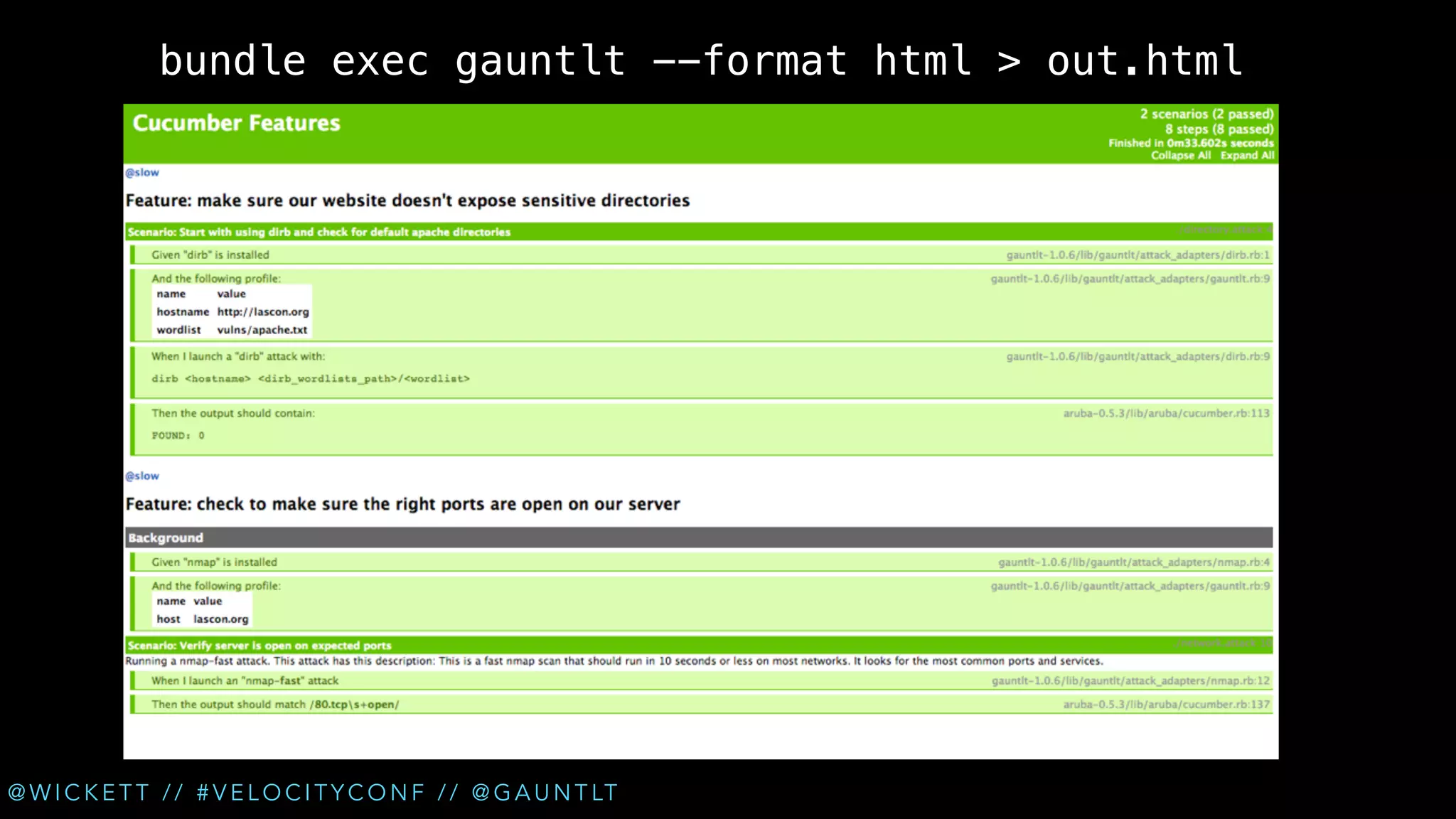
• Misconfiguration [dirb]
• SSL checks [sslyze]
@ W I C K E T T / / # V E L O C I T Y C O N F / / @ G A U N T LT](https://image.slidesharecdn.com/gauntlt-velocityeu-2013-131113094126-phpapp02/75/Be-Mean-to-Your-Code-with-Gauntlt-and-the-Rugged-Way-Velocity-EU-2013-Workshop-87-2048.jpg)