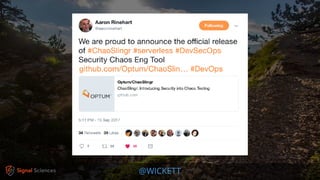
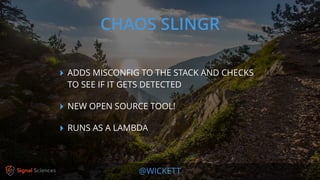
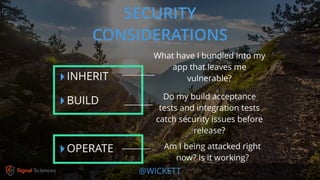
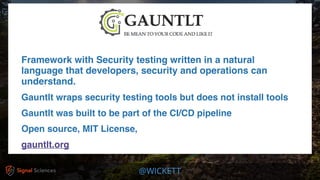
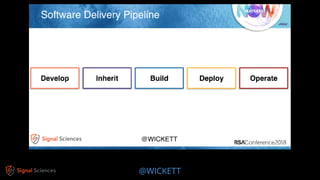
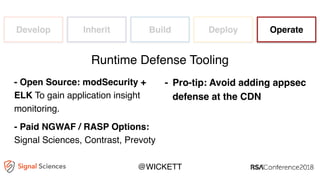
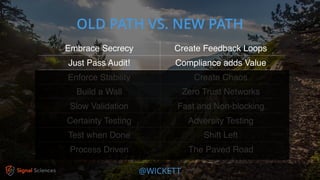
James Wickett discusses the evolving role of security within the DevOps culture, emphasizing the need for a shift from traditional security practices to more integrated and collaborative approaches. He highlights the importance of feedback loops, continuous testing, and empathy between development, operations, and security teams to enhance productivity and security outcomes. Wickett advocates for a DevSecOps culture that supports rapid deployment and addresses the current crisis in security by embracing openness and proactive measures.




























![@WICKETT
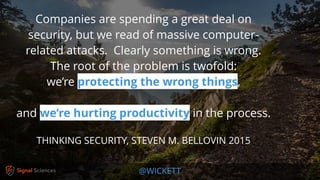
[Security by risk assessment]
introduces a dangerous fallacy: that
structured inadequacy is almost as
good as adequacy and that
underfunded security efforts plus risk
management are about as good as
properly funded security work](https://image.slidesharecdn.com/devsecopsandthenewpathforward-180424182203/85/DevSecOps-and-the-New-Path-Forward-30-320.jpg)





















![@WICKETT
[Deploys] can be treated as
standard or routine changes
that have been pre-approved
by management, and that
don’t require a heavyweight
change review meeting.](https://image.slidesharecdn.com/devsecopsandthenewpathforward-180424182203/85/DevSecOps-and-the-New-Path-Forward-59-320.jpg)