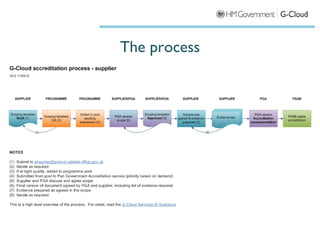
The document outlines the agenda and processes for the accreditation of services under the UK government's G-Cloud framework. It emphasizes the importance of security accreditation for protecting information systems, detailing the steps suppliers must take to achieve and maintain accreditation, and the role of the Public Sector Accreditation Board. Additionally, it addresses compliance requirements including data protection and offshoring considerations.