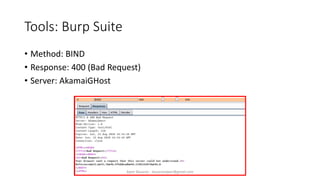
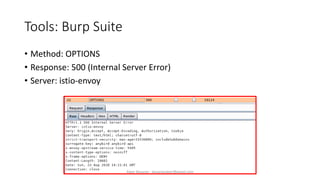
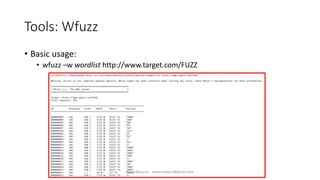
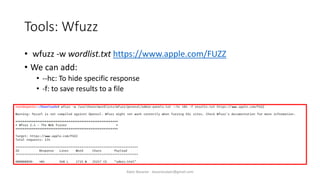
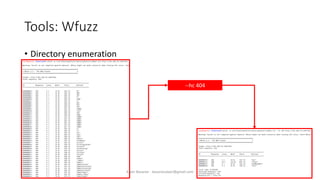
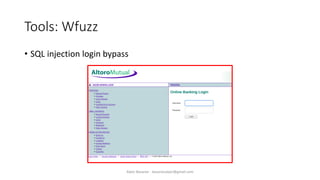
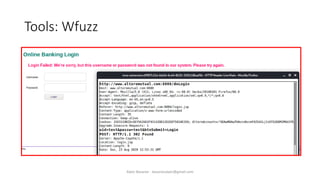
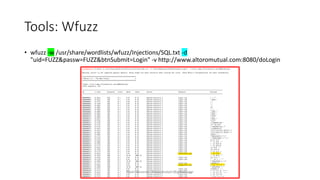
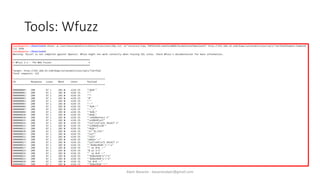
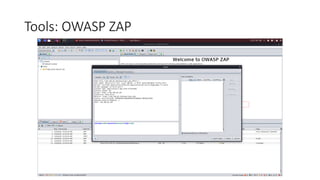
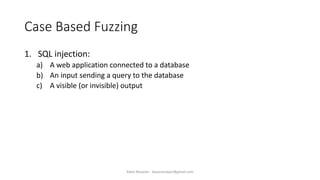
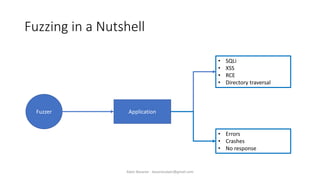
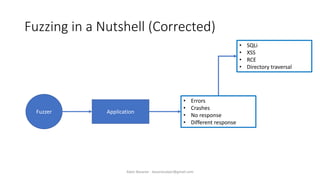
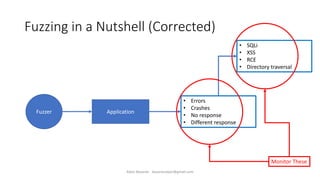
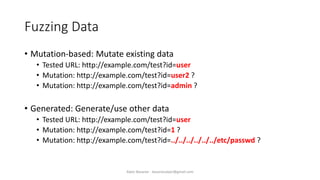
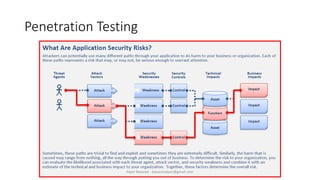
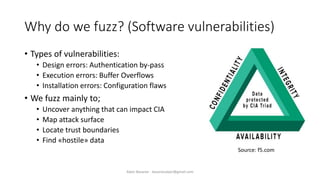
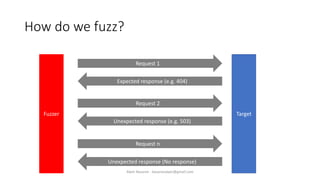
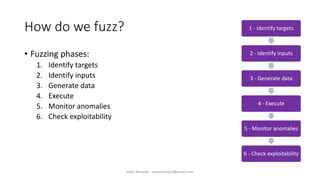
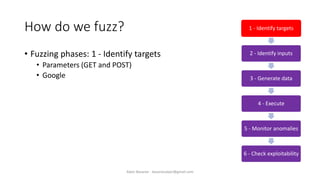
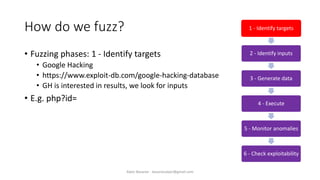
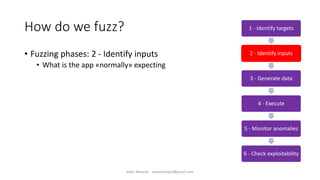
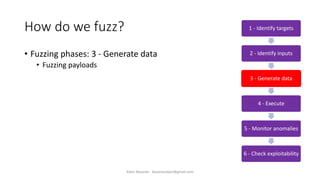
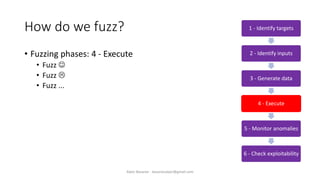
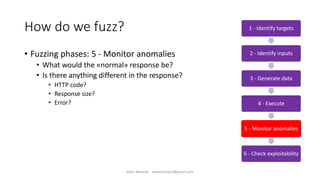
The document discusses fuzzing as a software testing technique aimed at discovering vulnerabilities by inputting unexpected or random data. It outlines fuzzing phases, types of vulnerabilities, and tools used in the process, emphasizing its importance in quality assurance and vulnerability assessment. Limitations of fuzzing are also addressed, including its inability to understand application logic and potentially missing complex vulnerabilities.





















![Hostile Data
• Mostly characters but also any data that can make the app do
something it shouldn’t
• Special characters would mainly be:
~ $ * _ } / '
! % ( + ] ` ? "
@ ^ ) = [ , ; <
# & _ { | . : >
Alper Basaran - basaranalper@gmail.com](https://image.slidesharecdn.com/fuzzingtelaviv-201029122346/85/Finding-Bugs-FASTER-with-Fuzzing-30-320.jpg)
![Hostile Data
• Mostly characters but also any data that can make the app do
something it shouldn’t
• Special characters would mainly be:
~ $ * _ } / '
! % ( + ] ` ? "
@ ^ ) = [ , ; <
# & _ { | . : >
Breaks SQL
Adds Command
Comments
Alper Basaran - basaranalper@gmail.com](https://image.slidesharecdn.com/fuzzingtelaviv-201029122346/85/Finding-Bugs-FASTER-with-Fuzzing-31-320.jpg)






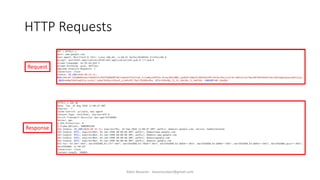



![Input / Output Validation
• Two main approaches:
• Blacklist:
• Don’t accept these:
• <script>
• ‘ or ‘1’=‘1
• Whitelist:
• Only accept these
• [a-z]
• [0-9]
Alper Basaran - basaranalper@gmail.com
Client
Side
Server
Side
Input
Validation](https://image.slidesharecdn.com/fuzzingtelaviv-201029122346/85/Finding-Bugs-FASTER-with-Fuzzing-53-320.jpg)