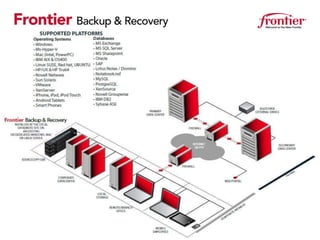
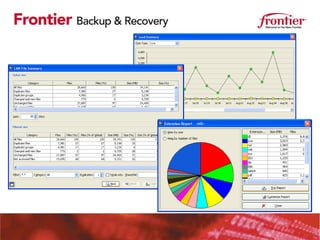
Frontier Backup & Recovery provides a managed backup and recovery service to address common business challenges. Data is critical for all industries but is at risk from hardware failures, human errors, and other issues. Regulations require stringent data security and compliance. Frontier's solution automates backups, allows fast recovery of files and servers, protects remote offices and laptops, and ensures security, compliance, and reduced costs through its managed service model. It aims to free up IT resources and provide expertise, automation, and validation to better protect critical business data.