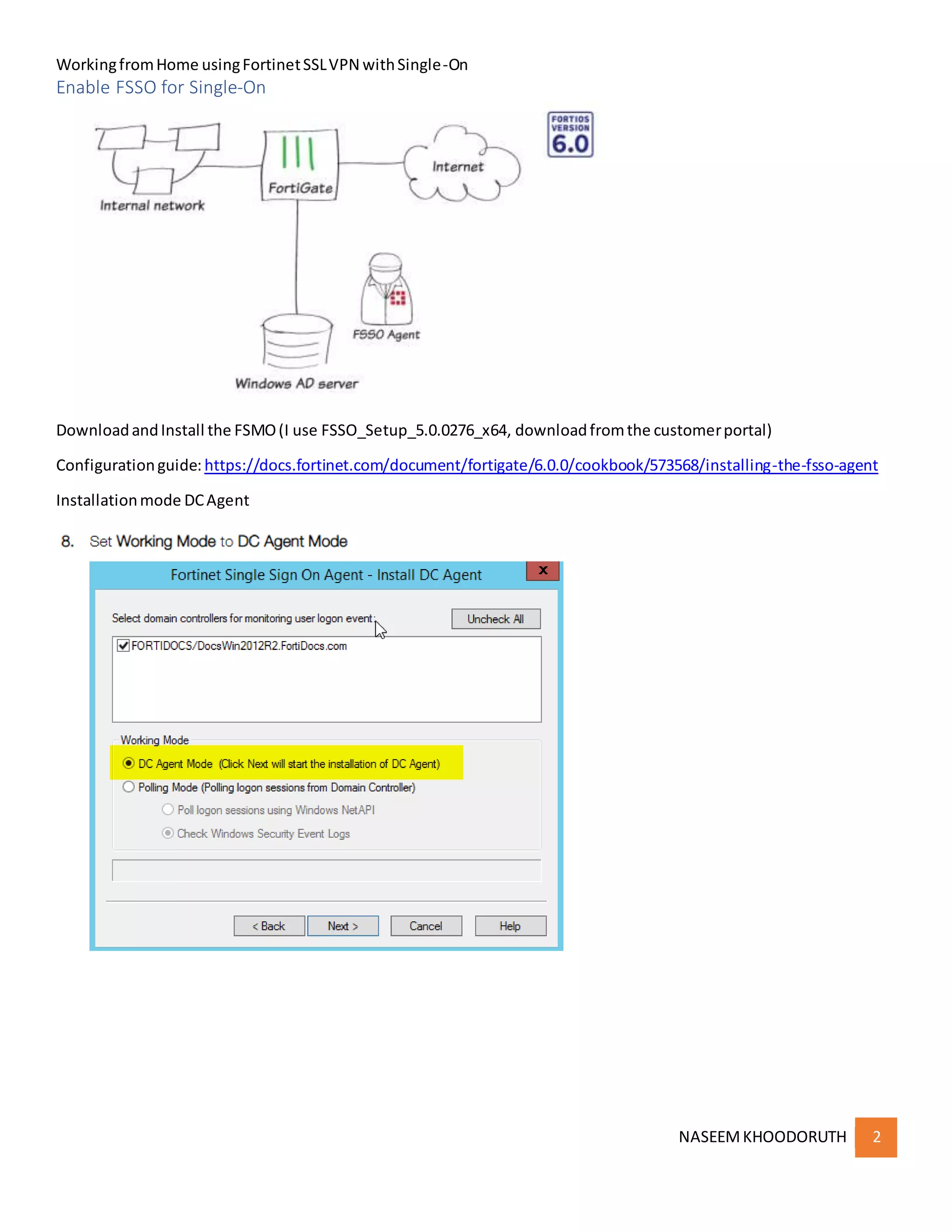
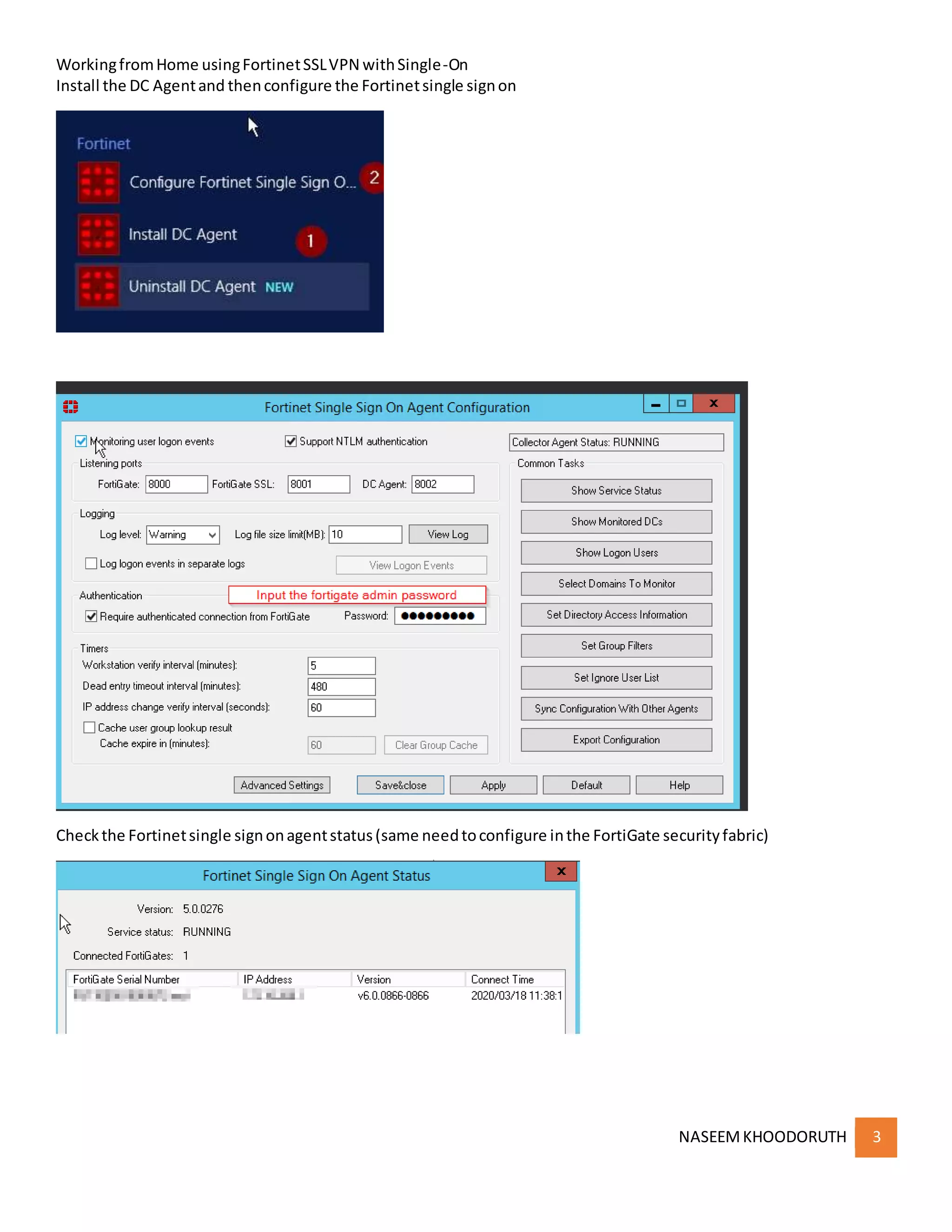
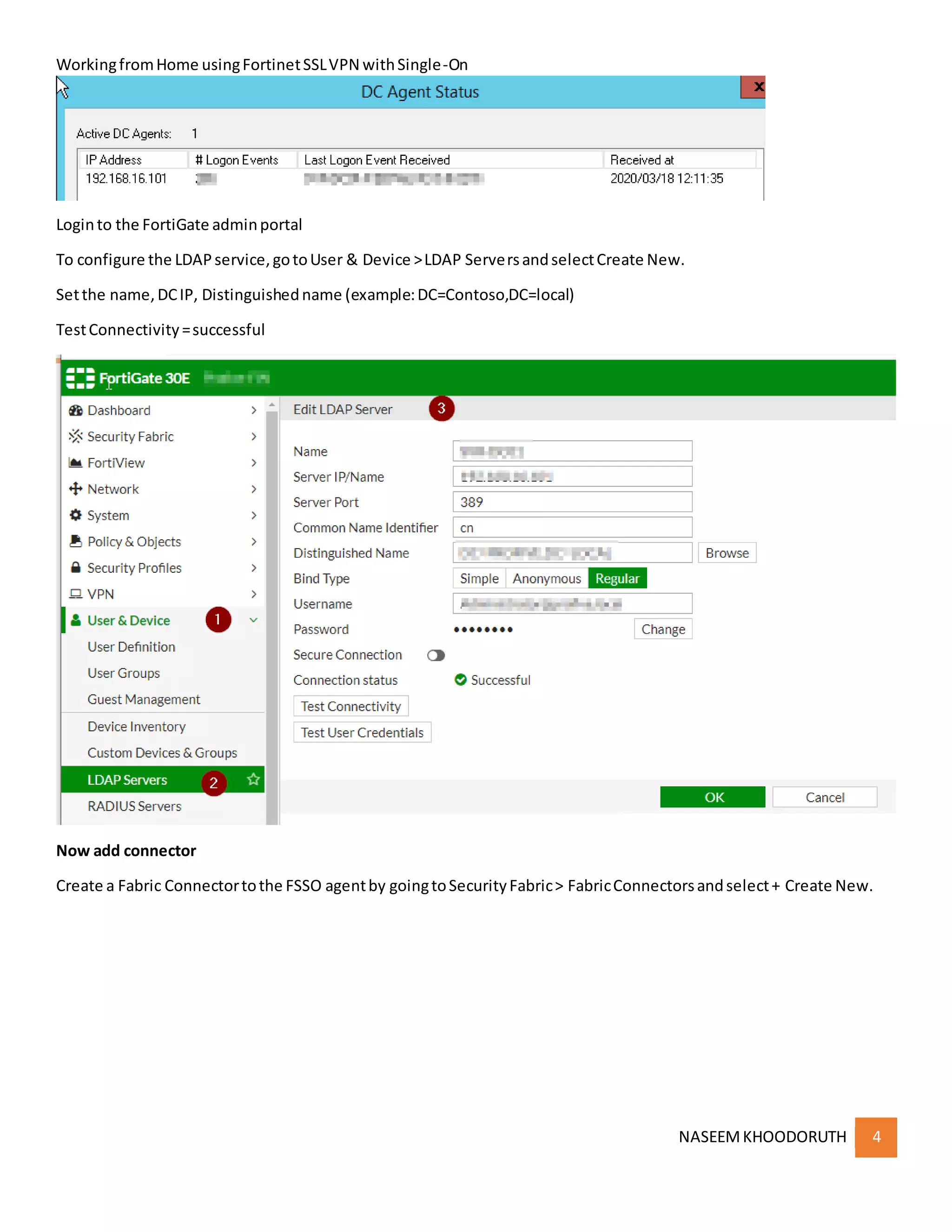
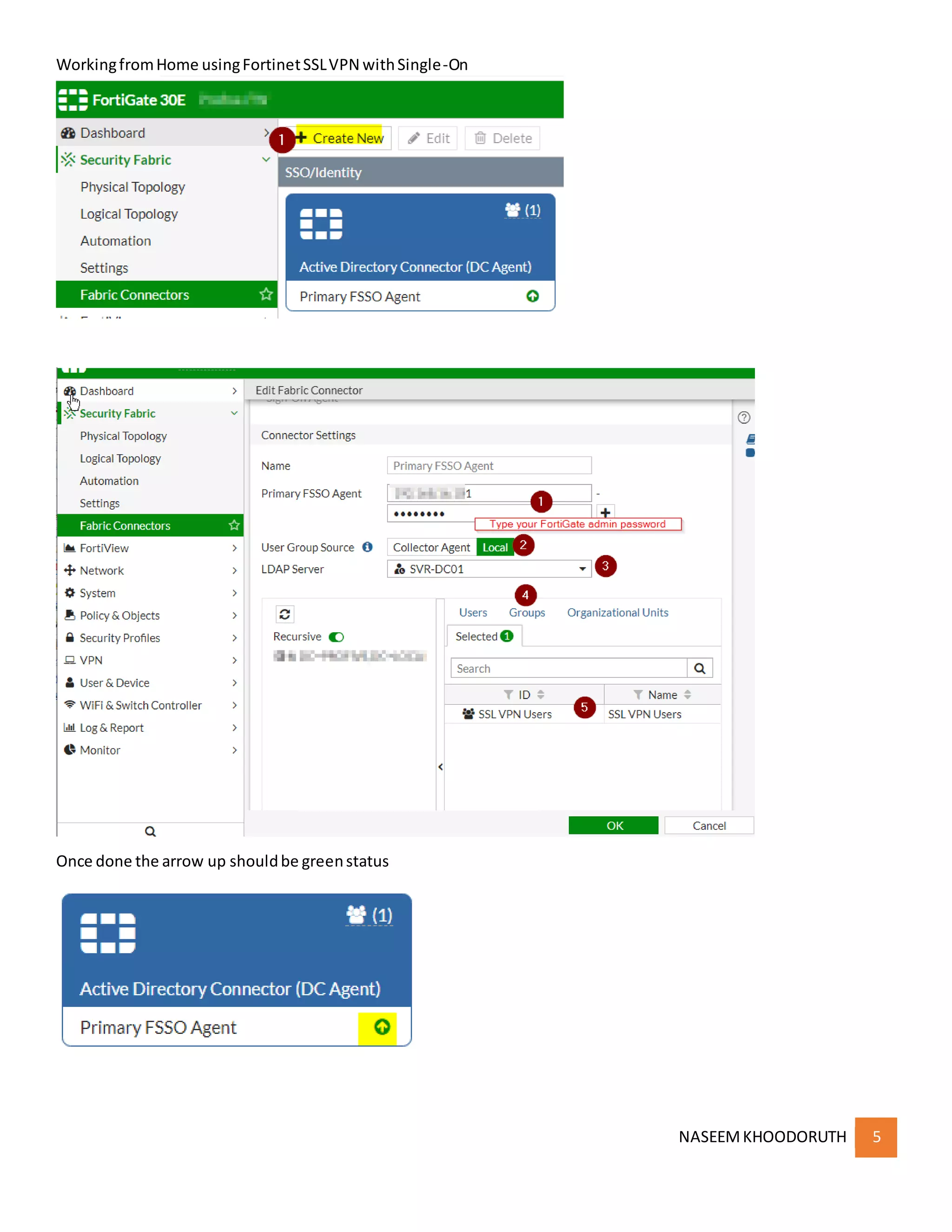
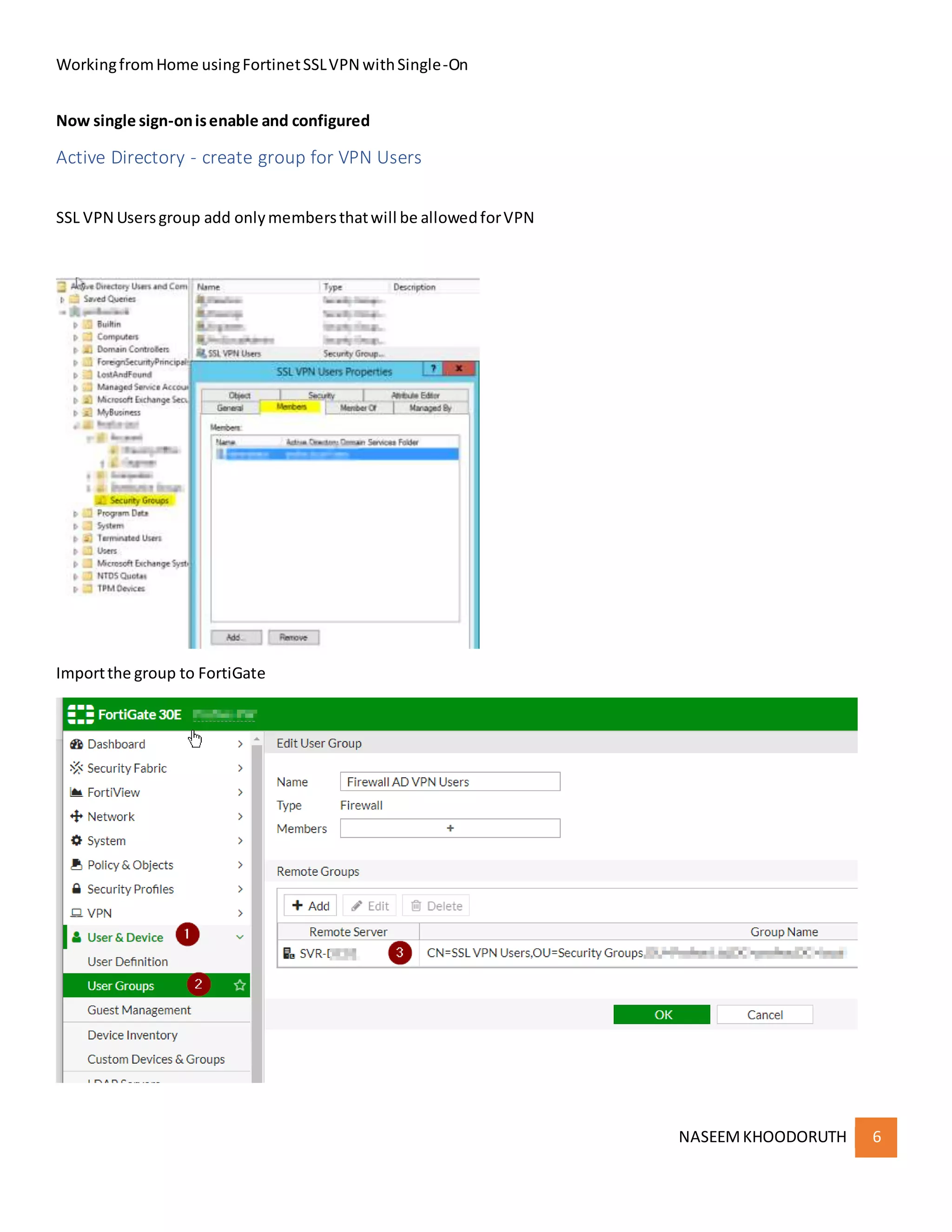
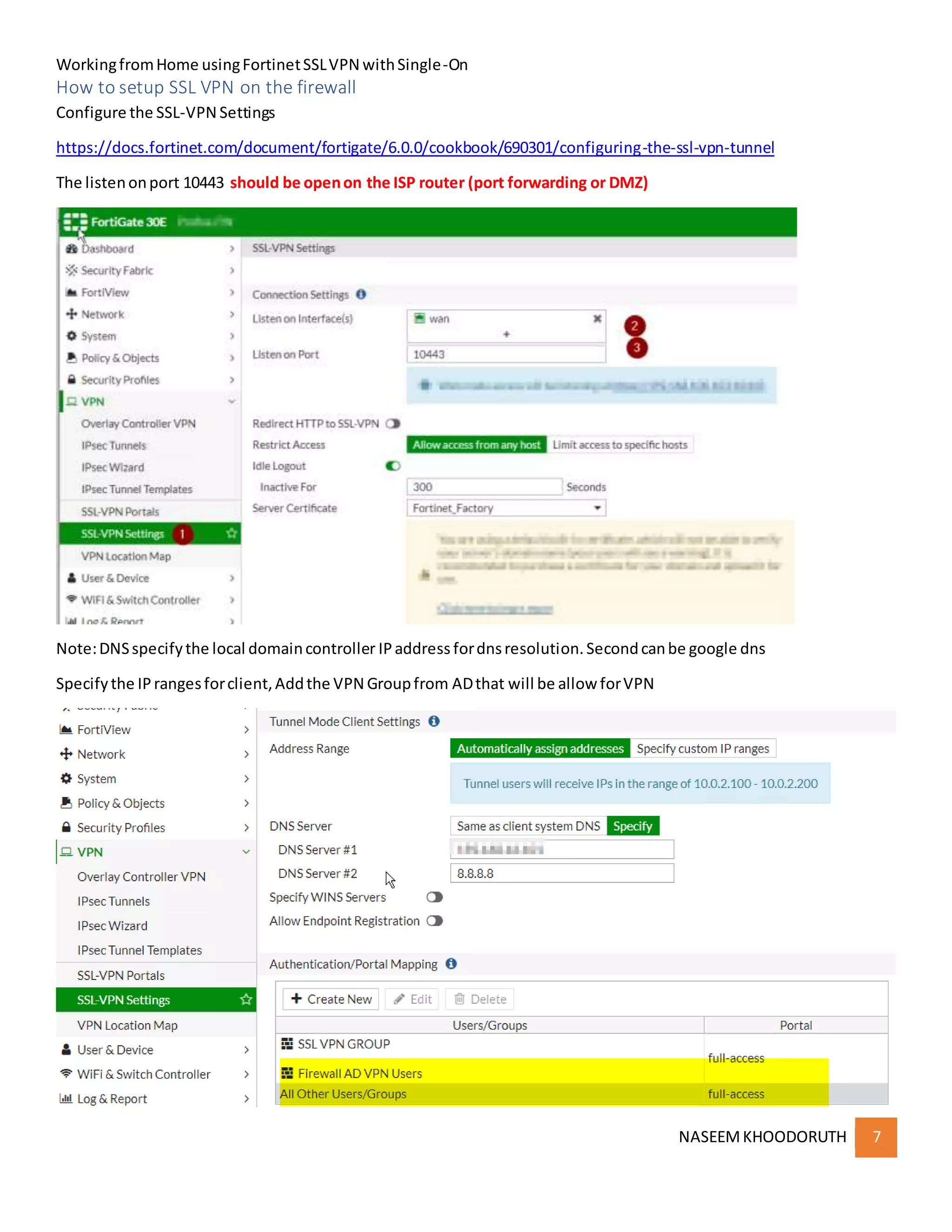
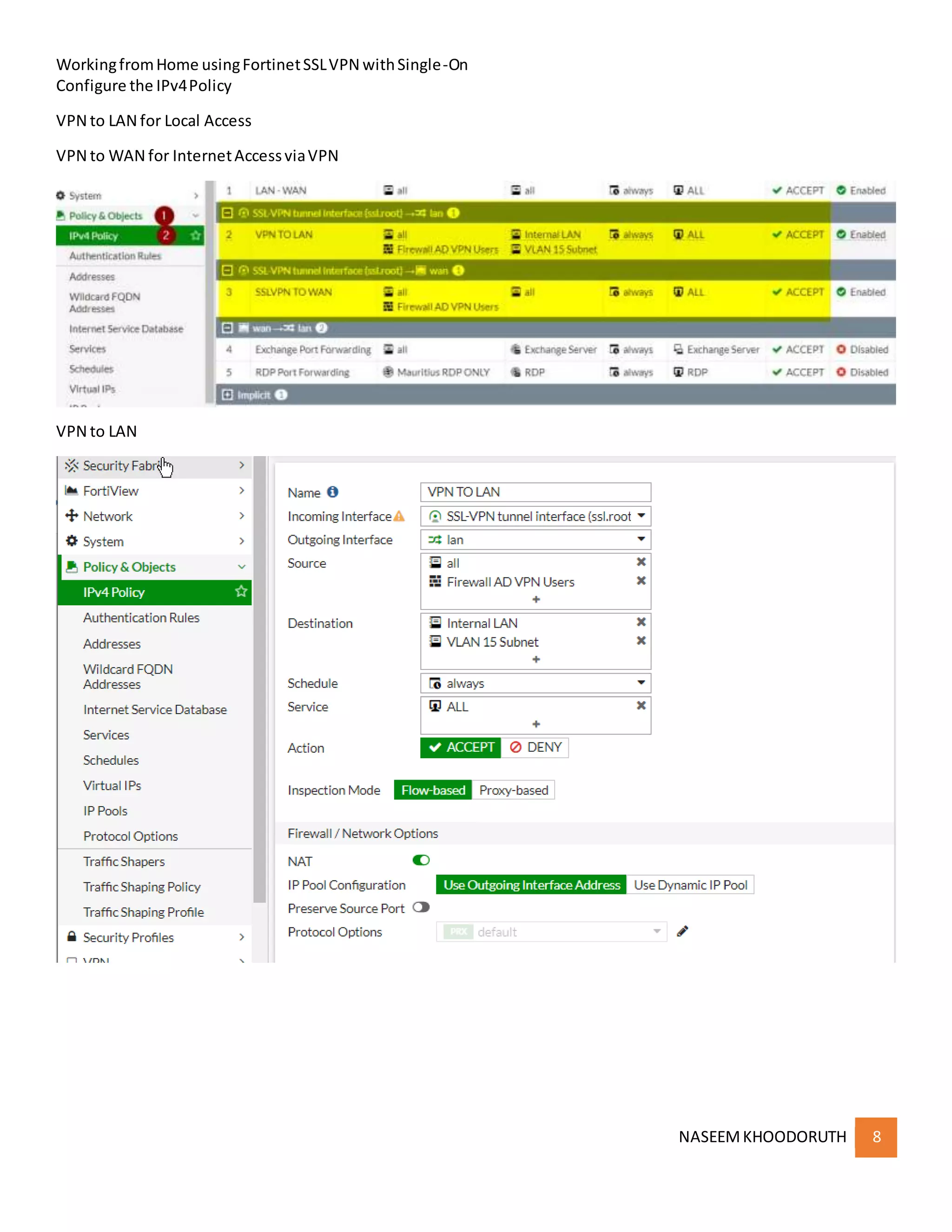
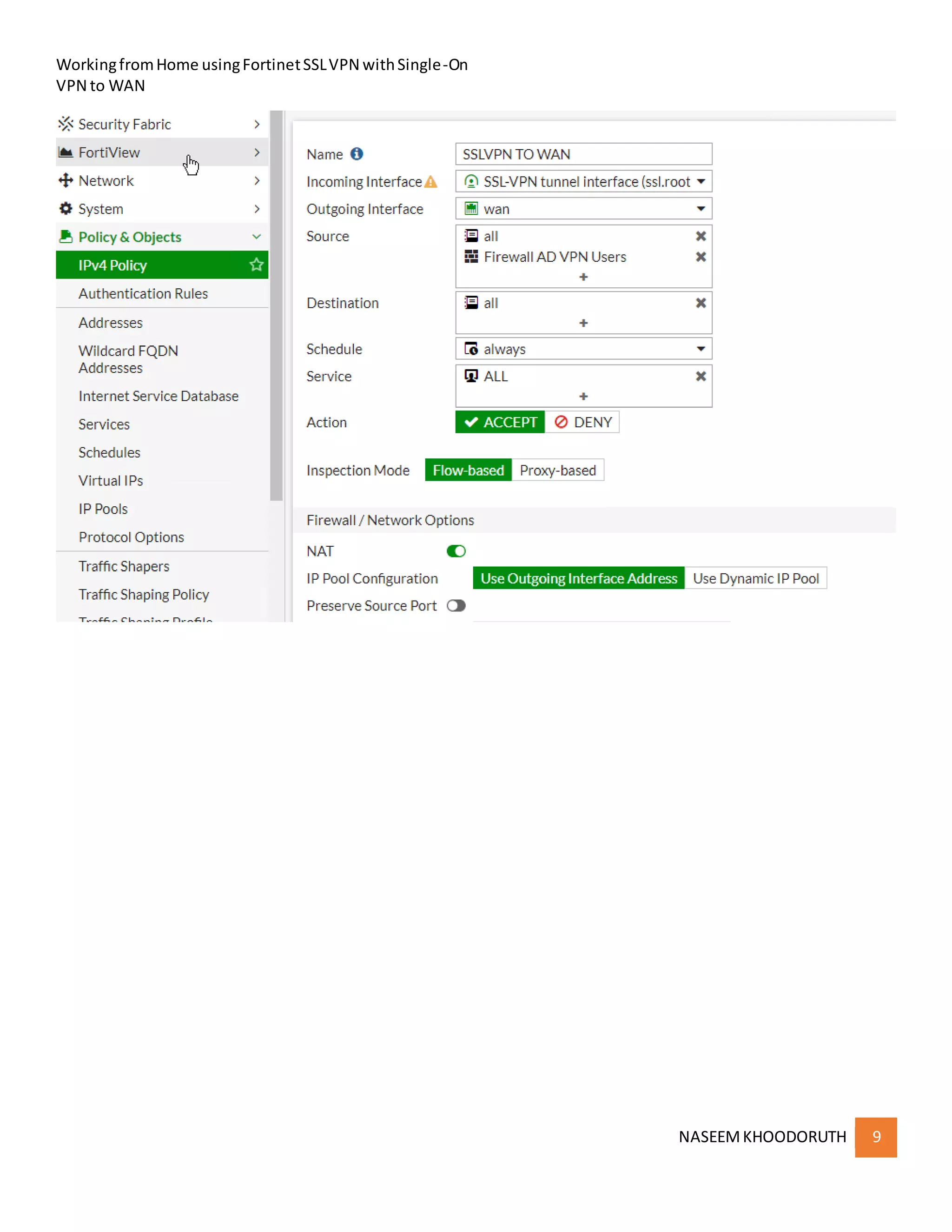
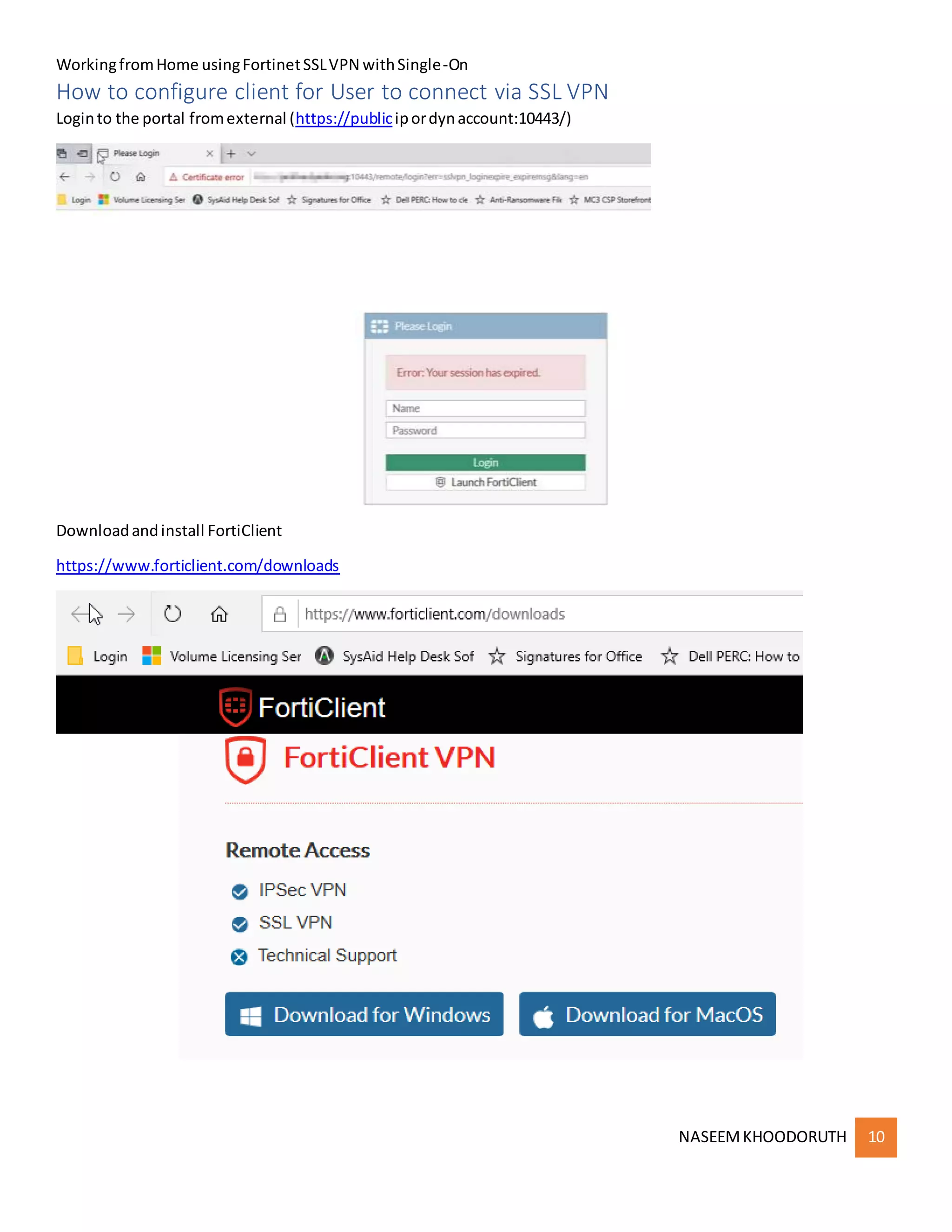
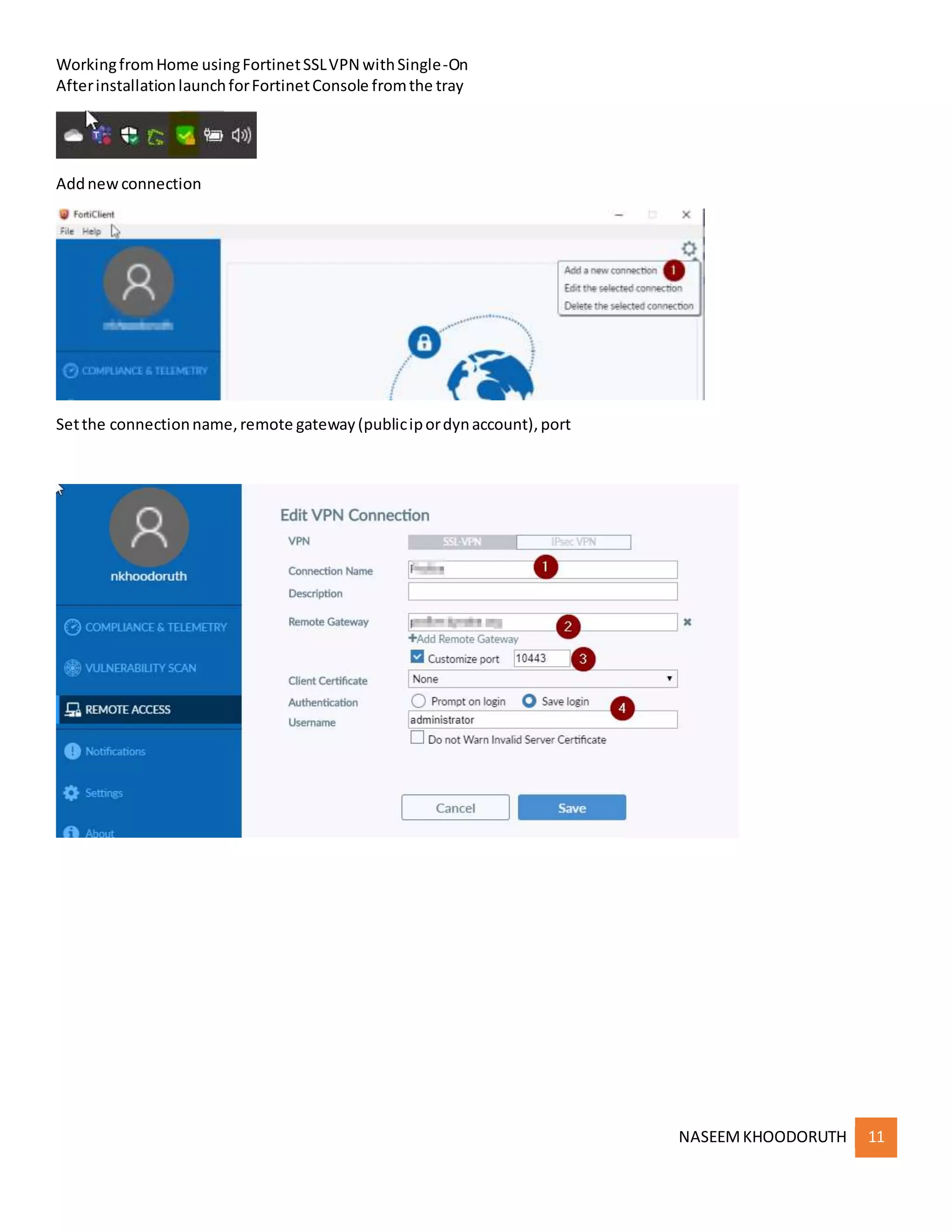
This document provides instructions for configuring single sign-on authentication for remote access to a network using Fortinet SSL VPN. It describes installing the FSSO agent, configuring the FortiGate for LDAP authentication and single sign-on, creating a VPN user group in Active Directory, setting up the SSL VPN interface and policies on the FortiGate, and configuring the FortiClient VPN client for remote users.