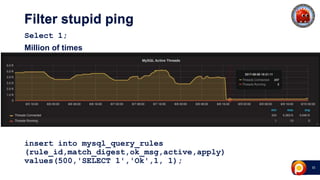
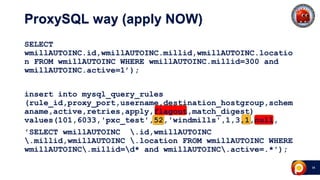
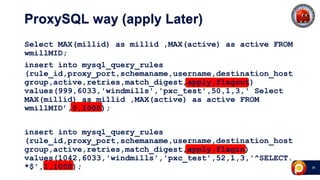
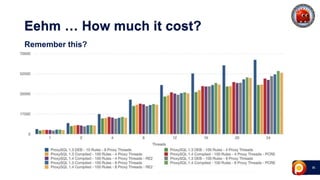
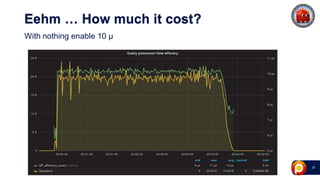
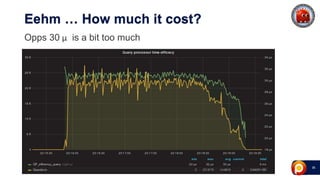
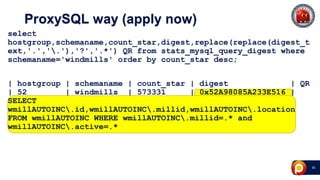
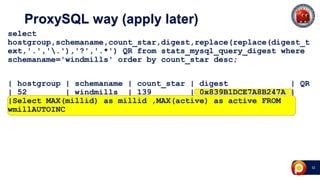
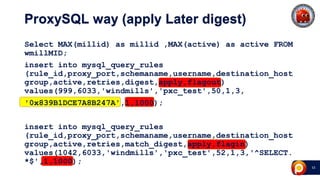
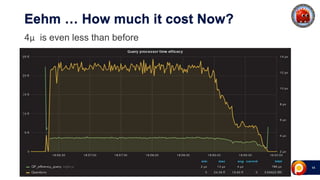
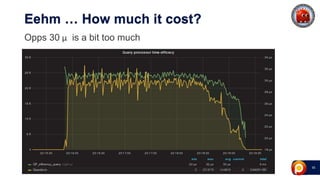
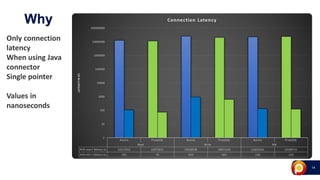
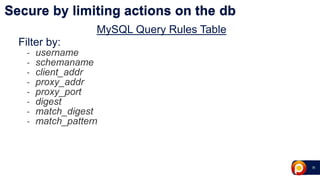
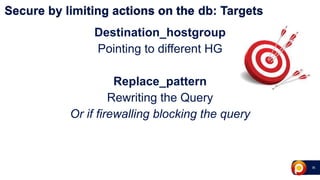
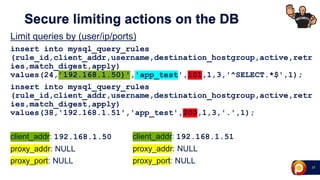
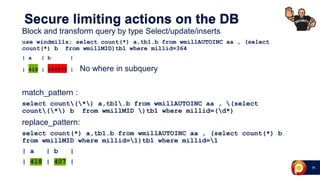
ProxySQL can be used with Amazon Aurora or other AWS solutions to improve security and performance. It can filter and redirect queries, caching results and load balancing connections across backend servers. Using ProxySQL's query rules, administrators can limit actions on the database by blocking or rewriting queries based on attributes of the client, query, or destination host group. This provides finer-grained control over queries than native AWS options alone. While ProxySQL has some performance overhead, using techniques like digest rules instead of regex matching can reduce this cost significantly.







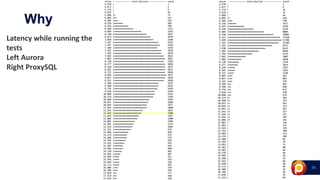





![31
IPtables
[root@galera1h1n5 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:mysql
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:tram
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:bmc-reporting
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:krb524
ACCEPT udp -- 10.0.0.0/24 anywhere udp dpt:tram
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:42000
ACCEPT tcp -- 192.168.1.0/24 anywhere tcp dpt:42002
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:6033
ACCEPT tcp -- 10.0.0.0/24 anywhere tcp dpt:6032
ACCEPT icmp -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:mysql
REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
Chain OUTPUT (policy ACCEPT)
target prot opt source destination](https://image.slidesharecdn.com/fortifyawsauroraproxy-190201150003/85/Fortify-aws-aurora_proxy-30-320.jpg)