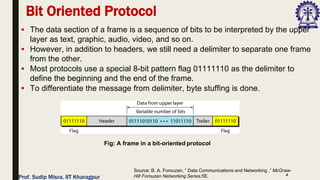
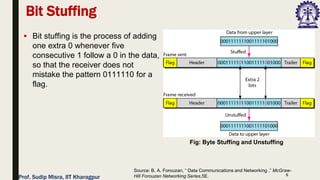
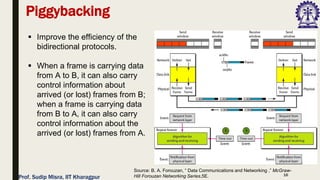
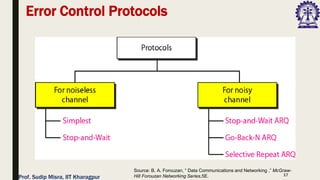
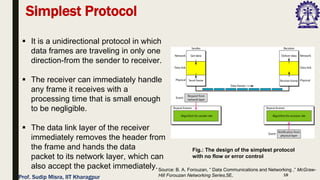
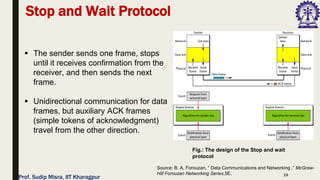
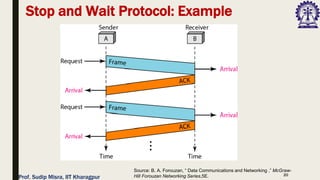
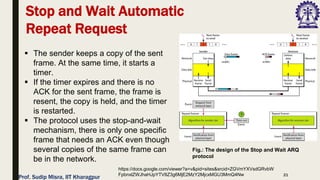
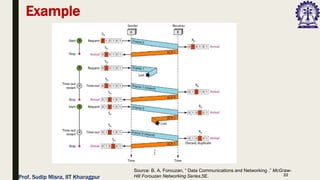
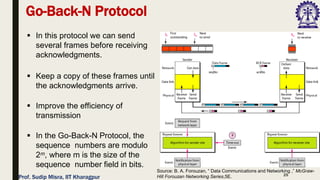
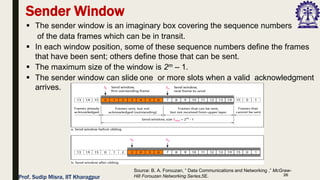
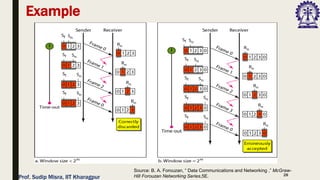
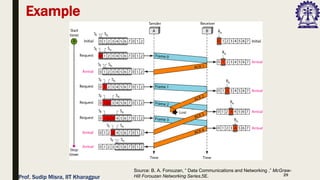
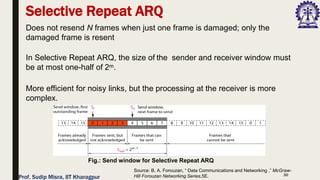
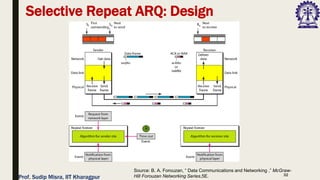
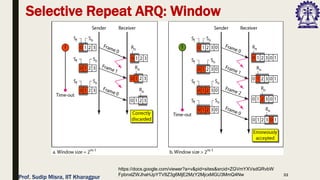
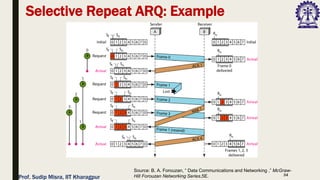
The document outlines data link control functions in computer networks, emphasizing framing, flow control, and error control protocols implemented to ensure efficient and reliable data transmission. It covers techniques like bit and byte stuffing, and various protocols such as stop-and-wait, go-back-N, and selective repeat for managing data flow and error detection. Additionally, it discusses the importance of sequence numbers and acknowledgment mechanisms in maintaining communication integrity between sender and receiver.