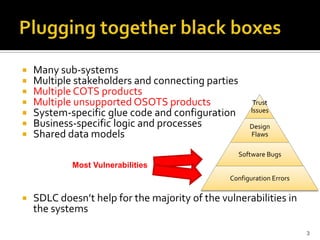
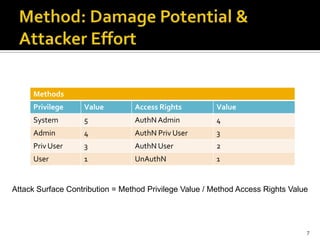
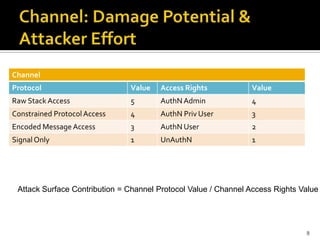
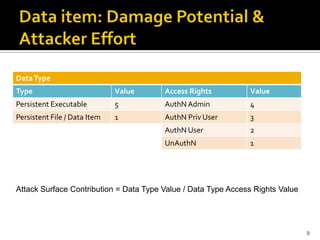
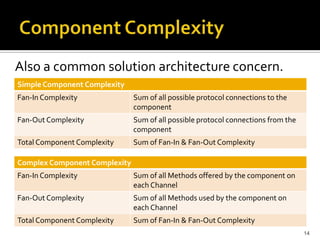
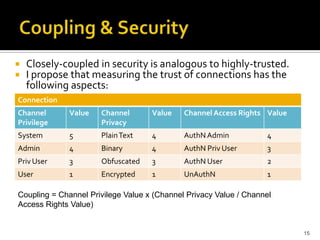
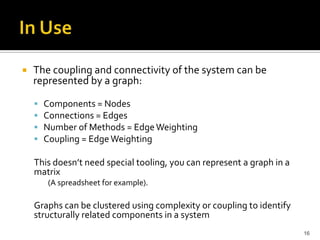
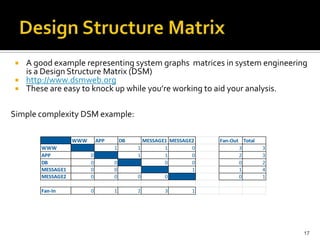
The document discusses the challenges of security architecture in large, complex systems involving multiple stakeholders and diverse projects. It emphasizes the importance of measuring attack surfaces and system complexity, as well as the risks associated with tightly-coupled components. The analysis introduces concepts like attack surface contributions, coupling, and connectivity to identify high-risk areas in such complex systems.