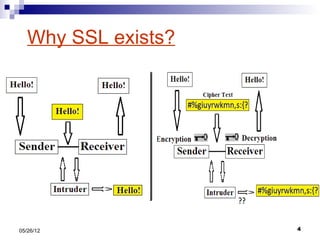
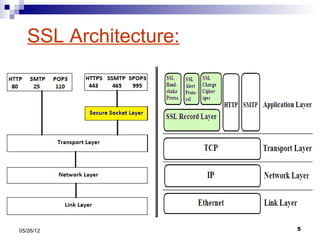
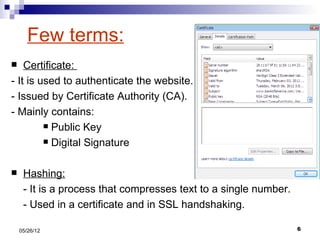
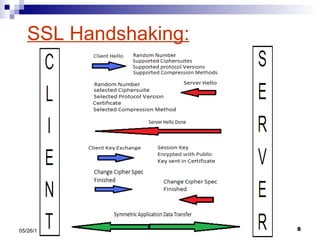
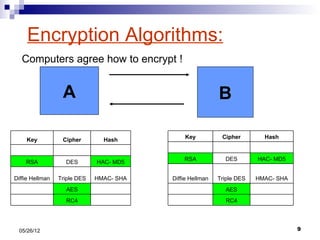
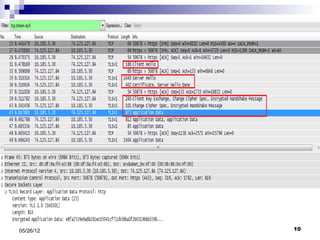
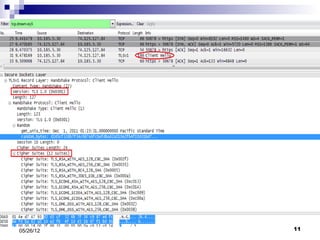
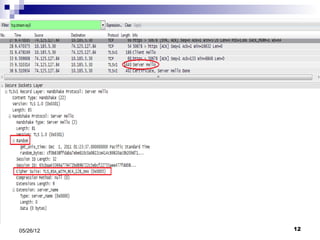
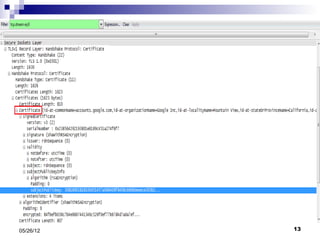
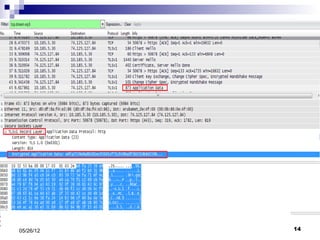
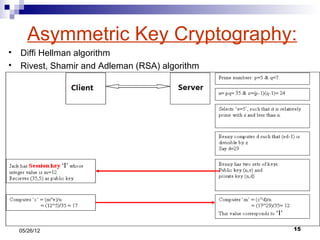
This presentation summarizes Secure Socket Layer (SSL) technology. It discusses how SSL uses encryption to provide security and integrity for data transmission. The presentation covers SSL architecture, including the certificate and hashing components. It also describes the SSL handshake process and how symmetric and asymmetric encryption algorithms are used to securely transfer data. Common algorithms like RSA, Diffie-Hellman, DES, and AES are also mentioned.