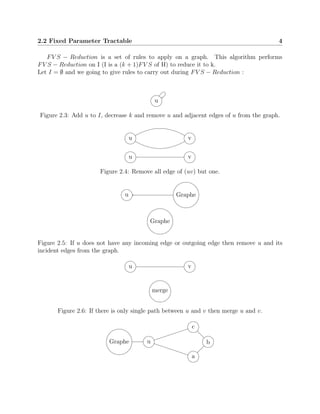
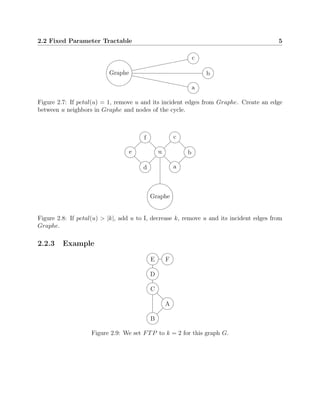
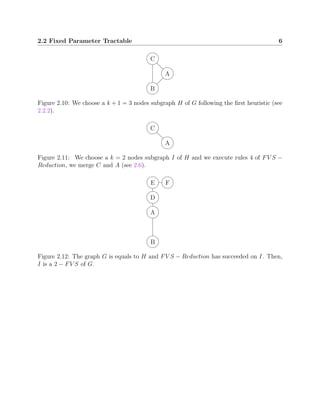
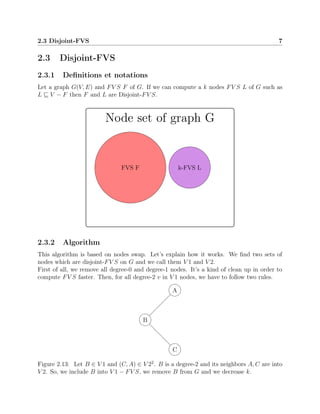
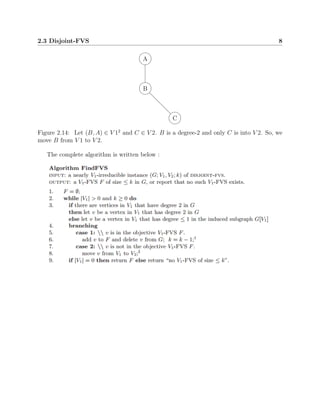
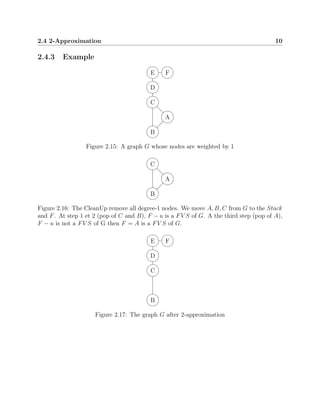
This document discusses algorithms for solving the feedback vertex set problem, which aims to find the minimum number of nodes that need to be removed from a graph to make it acyclic. It describes several algorithms including a naive algorithm, fixed parameter tractable algorithm, 2-approximation algorithm, disjoint feedback vertex set algorithm, and randomized algorithm. For each algorithm, it provides definitions, pseudocode, and an example to illustrate how it works. The document concludes that this problem remains an active area of research to develop more efficient algorithms.