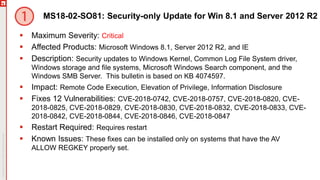
The document provides an overview of a webinar discussing the February 2018 patch Tuesday events, hosted by Chris Goettl and Todd Schell. It covers critical vulnerabilities across various Microsoft products including Windows, Office, and Internet Explorer, as well as updates on identified issues like the Meltdown and Spectre vulnerabilities. The document also outlines specific security updates, requirements for installations, and known issues related to antivirus software compatibility.